SEC595: Applied Data Science and AI/Machine Learning for Cybersecurity Professionals


Experience SANS training through course previews.
Learn MoreLet us help.
Contact usBecome a member for instant access to our free resources.
Sign UpWe're here to help.
Contact UsHumans remain the number one driver of breaches today, demonstrating that cybersecurity is no longer just a technical challenge but a human one also.

The 2022 Verizon Data Breach Incident Report has been released and I could not be more excited. First, what is the report and why should anyone care? For the past 15 years, this report, informally known as the VZ DBIR, has provided insights on the most common drivers of incidents and breaches today. The goal of the report is to enable leaders to make data-driven decisions on their greatest risks and manage them most effectively. Several reasons why this report is so highly respected include:
Enough about the why this report is useful, let’s dig into what this year’s report tells us — especially from a human risk perspective. The big take away (similar to the past three years) is that the human remains the number one driver of breaches today, demonstrating that cybersecurity is no longer just a technical challenge but a human one also. As long as organizations continue to perceive and treat cybersecurity as a technical challenge, we will continue to lose this battle. Okay, let’s take a look at some of the specific findings.
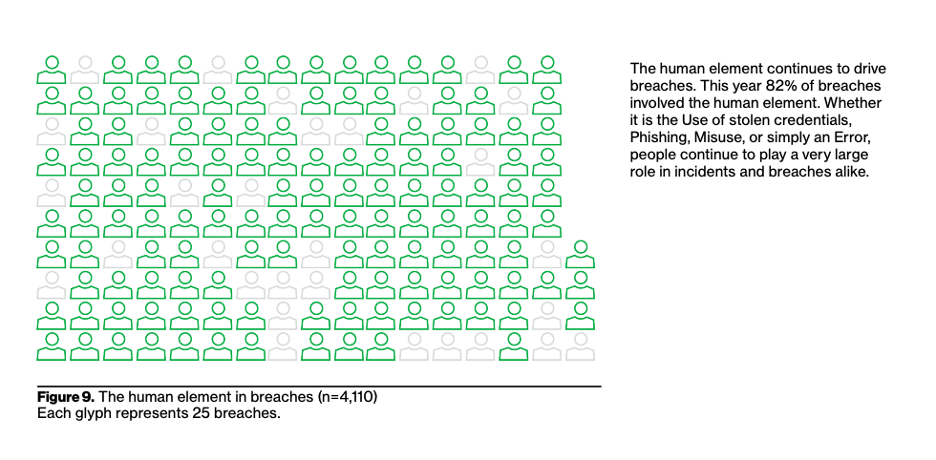
It's the Human - Figure 09: This finding is most likely the one garnering the greatest attention, clearly calling out that once again people are involved in breaches over 80% of the time. "By people" could mean a breach due to someone clicking on a link in a phishing email, someone reusing a weak password that is compromised, or an IT admin misconfiguring their cloud account and accidentally sharing sensitive data with the entire world. Use this number to help your leadership understand and create a sense of urgency that people, and not just technology, need to be addressed.
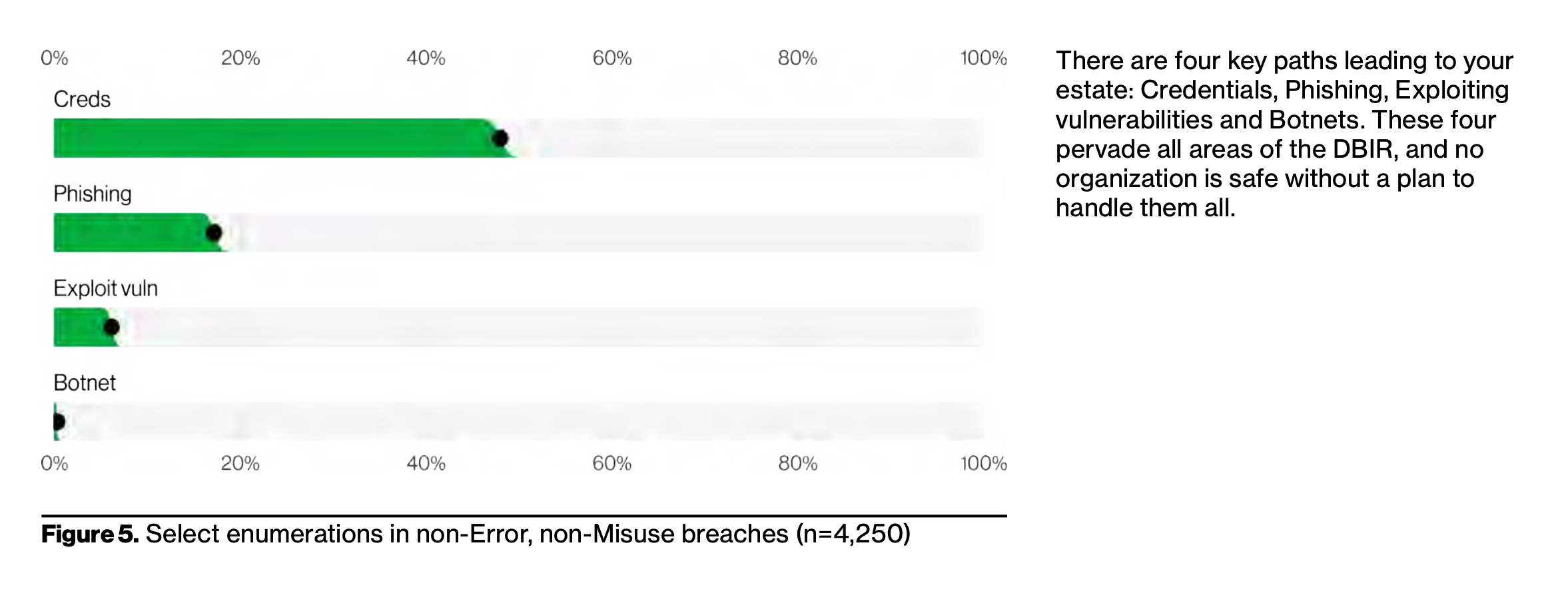
Phishing & Passwords — Figure 5: Similar to the last several years, phishing attacks and compromised credentials (passwords) are the top two methods by which cyber attackers are gaining access to an organization. This data point is key because it shows us which secure behaviors to focus on for improvement. Managing a security awareness or culture program can feel complex and overwhelming. Not sure where to start or what topics to prioritize? Phishing and passwords. Want to know the two most common ways Ransomware gets into an organization? Phishing and passwords.
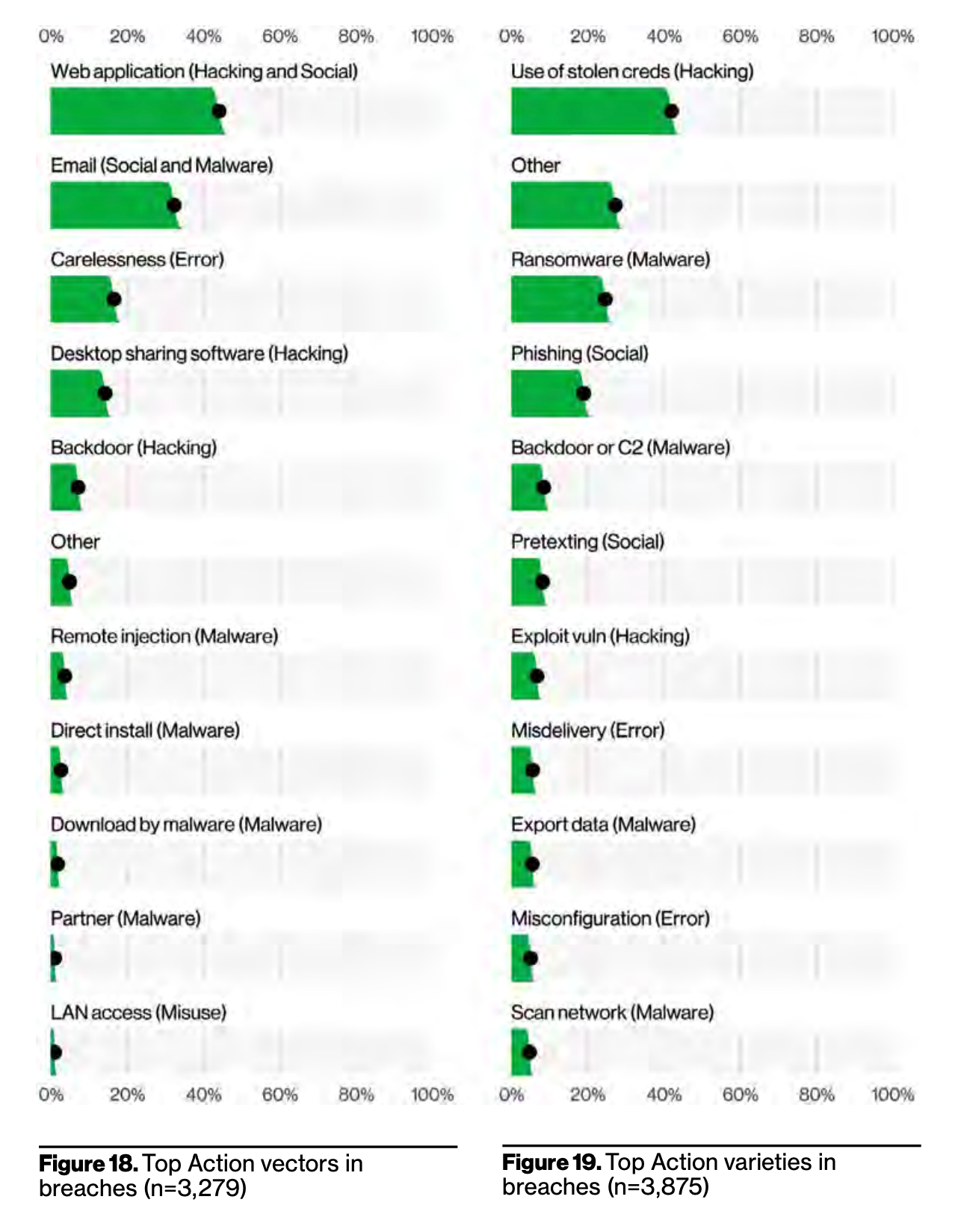
Human Mistakes — Figure 18: While we tend to focus on deliberate threats (cyber criminal or nation state actors) the VZ DBIR also identified almost 20% of breaches are caused by simple mistakes, either staff emailing the wrong person with sensitive data or IT admins misconfiguring their cloud accounts. A key here is make both your technologies and security policies as simple as possible to work with. The simpler you make security the less likely your staff will make mistakes.
To be honest none of these findings from a human perspective are shocking, as they are very similar to the same findings that the VZ DBIR has found for the past three years. People are now the primary attack vector, the largest drivers for breaches. Until we start effectively managing human risk, we will continue to lose this battle.
If you want to learn more about how to manage and measure human risk, consider taking SANS two-day MGT433 Security Awareness course or for more experienced security leaders the SANS five-day MGT521 Security Culture course.


Lance revolutionized cyber defense by founding the Honeynet Project. At SANS, he has empowered over 350 organizations worldwide to build resilient security cultures, transforming human risk management into a cornerstone of modern cybersecurity.
Read more about Lance Spitzner