SEC595: Applied Data Science and AI/Machine Learning for Cybersecurity Professionals


Experience SANS training through course previews.
Learn MoreLet us help.
Contact usBecome a member for instant access to our free resources.
Sign UpWe're here to help.
Contact Us
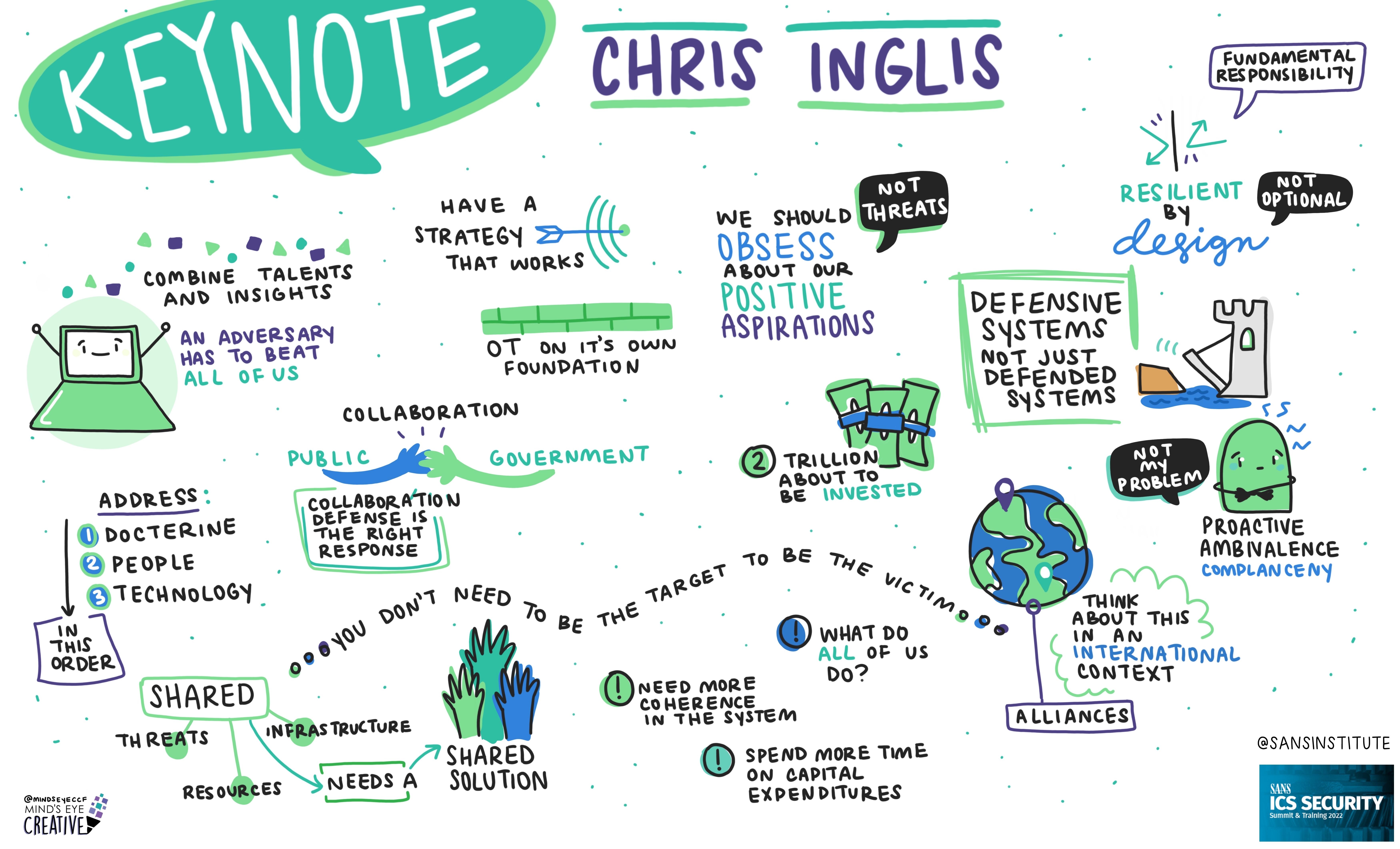
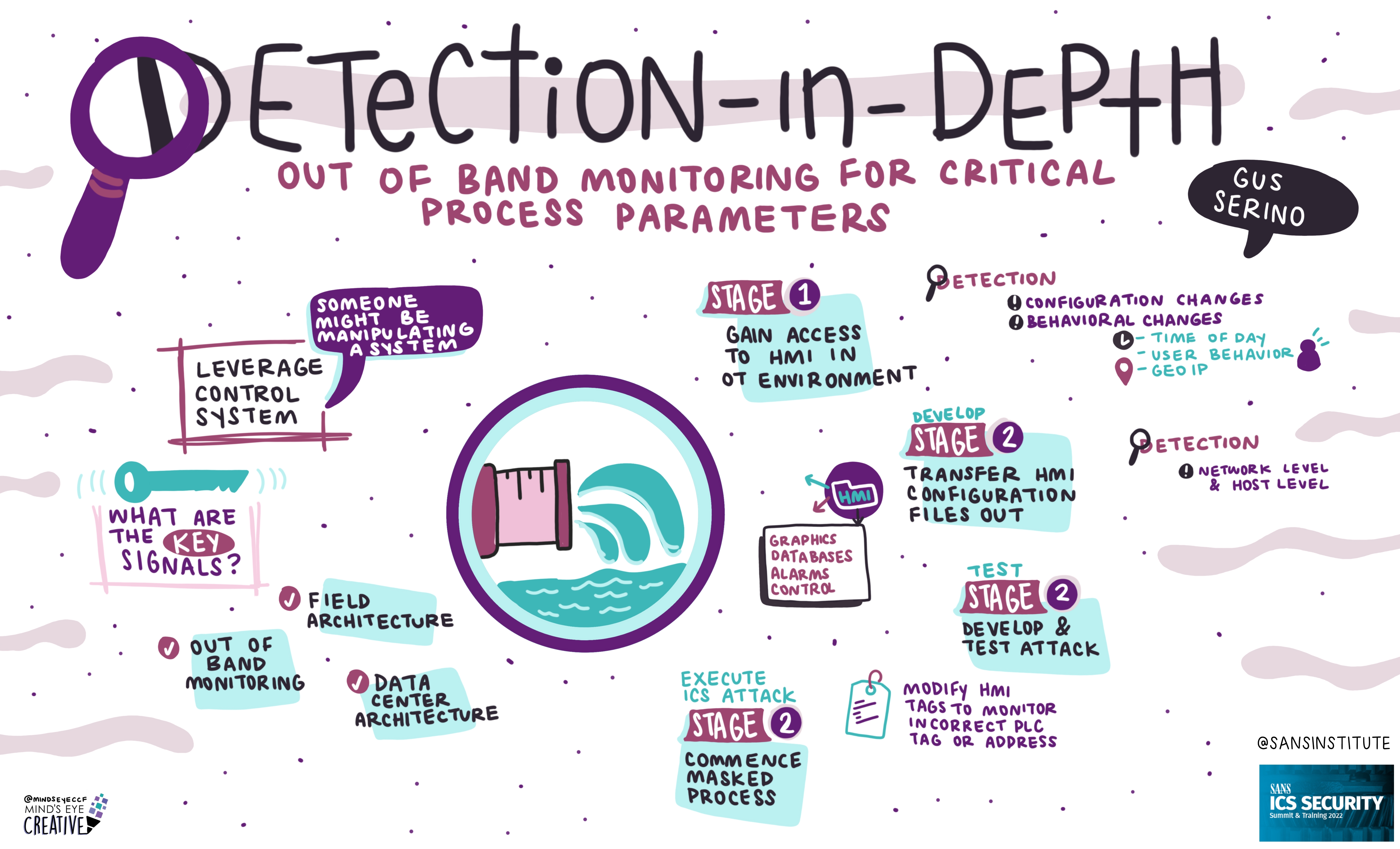
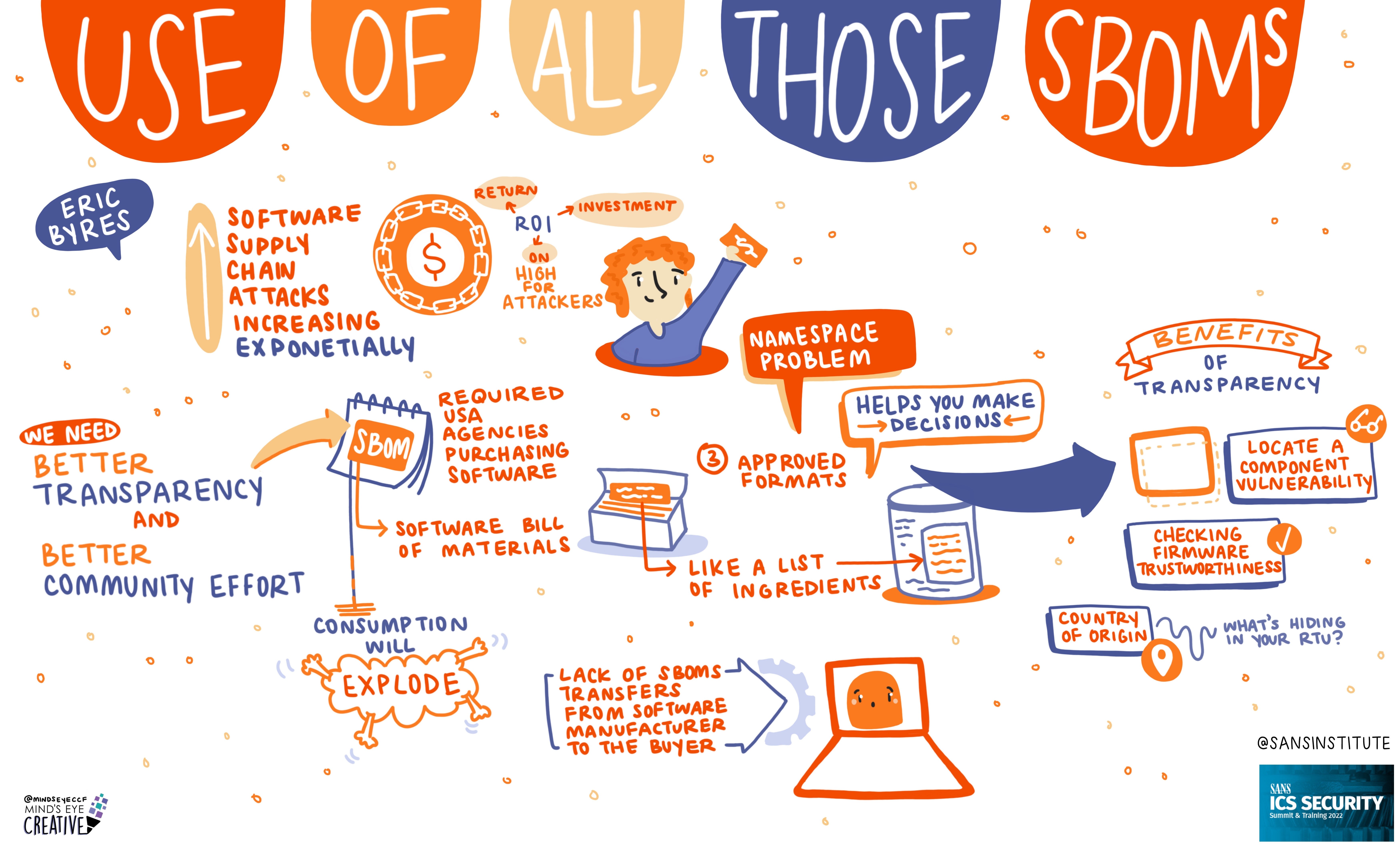
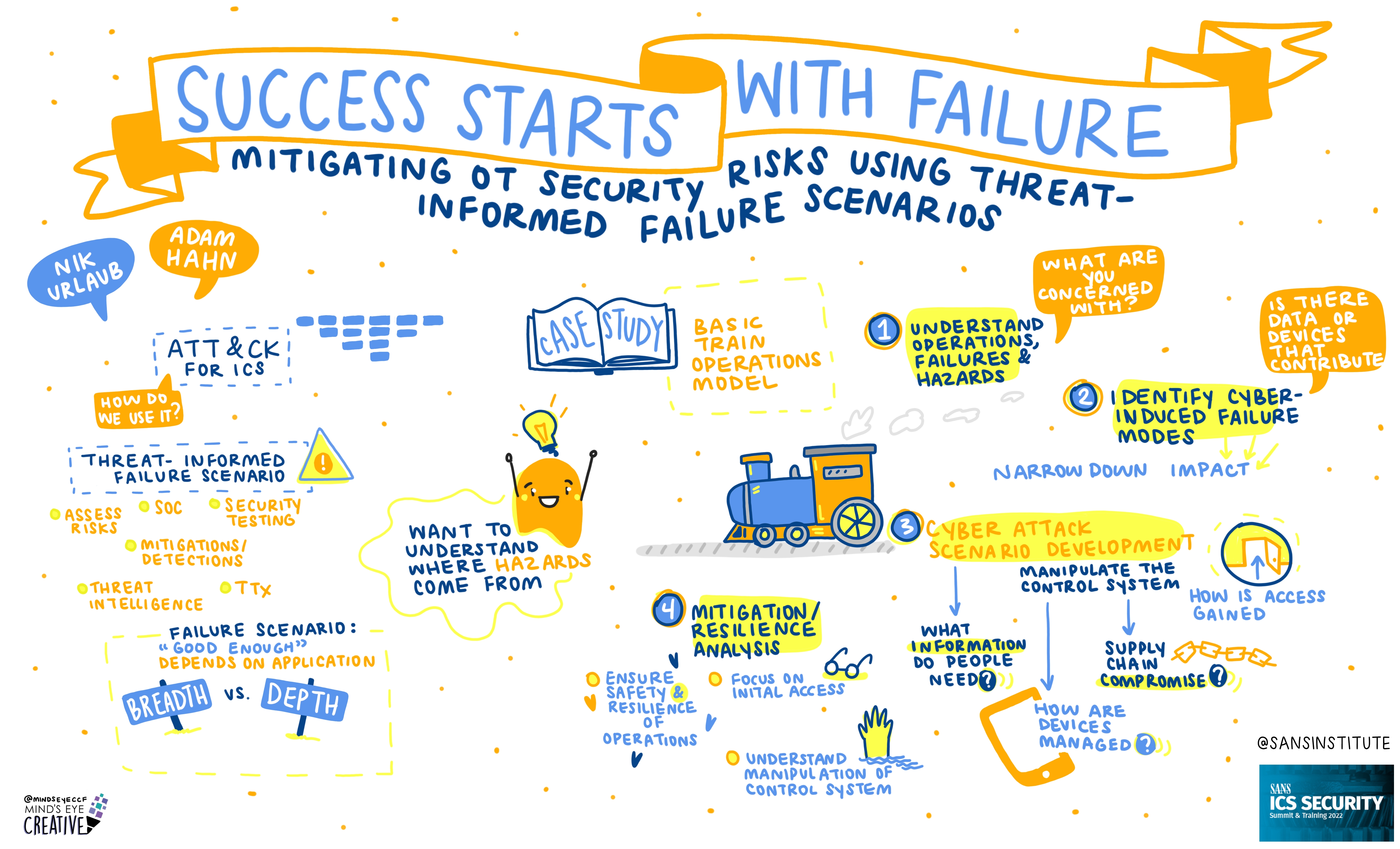
On June 2nd and 3rd, thousands from around the globe tuned in for the SANS ICS Security Summit.
We invited Ashton Rodenhiser of Mind's Eye Creative to create graphic recordings of our Summit presentations. If you missed a talk or are looking to view the SANS ICS Security Summit through a visual lens, take a look at the recordings below.
In addition to graphic recordings, PDFs of Summit presentations will be made available on the SANS Summit Archives page (SANS account required) and videos will be posted to YouTube over the next several months.
*If you registered for the Summit, video recordings are available on your Summit Access page in your SANS Portal.
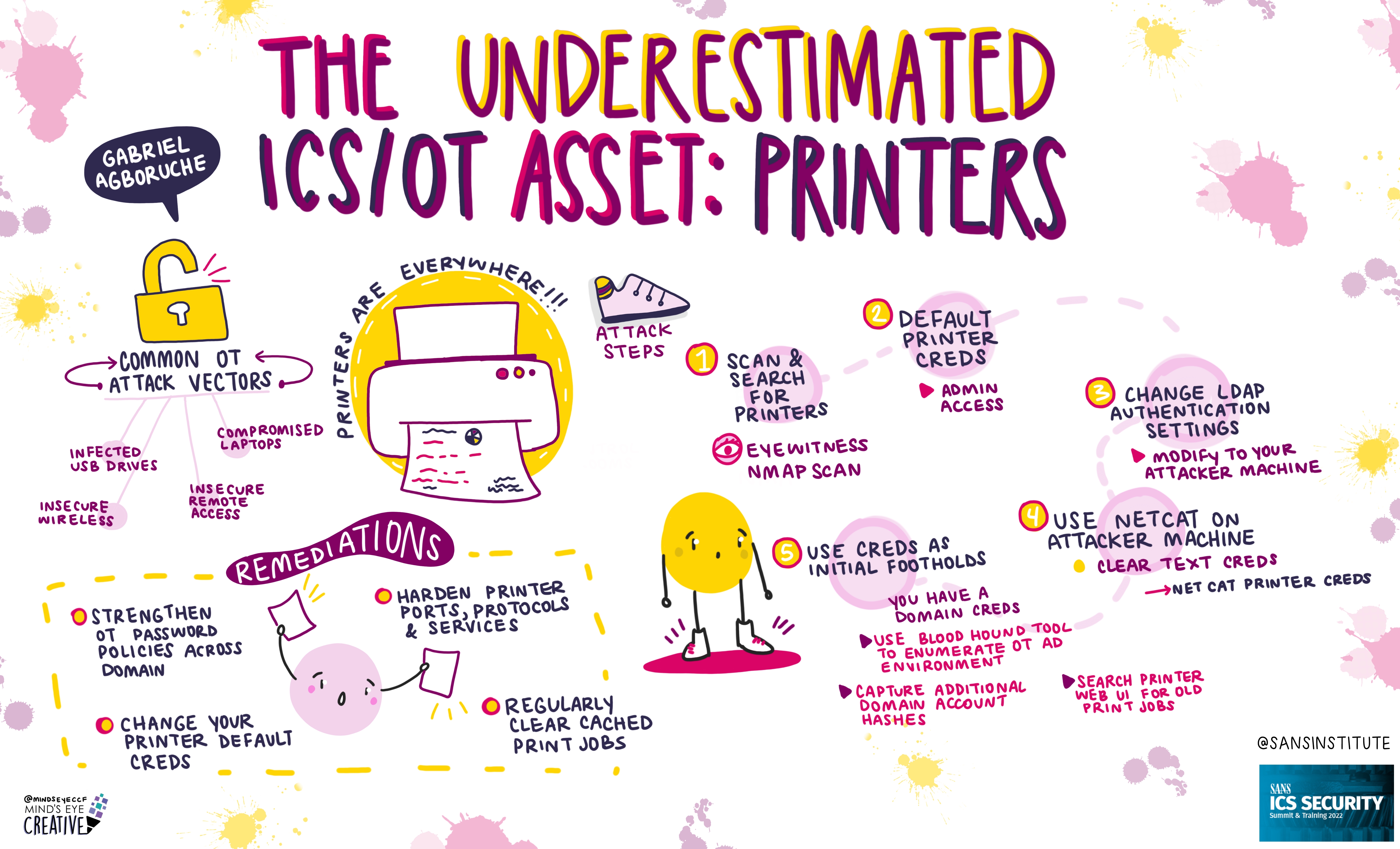
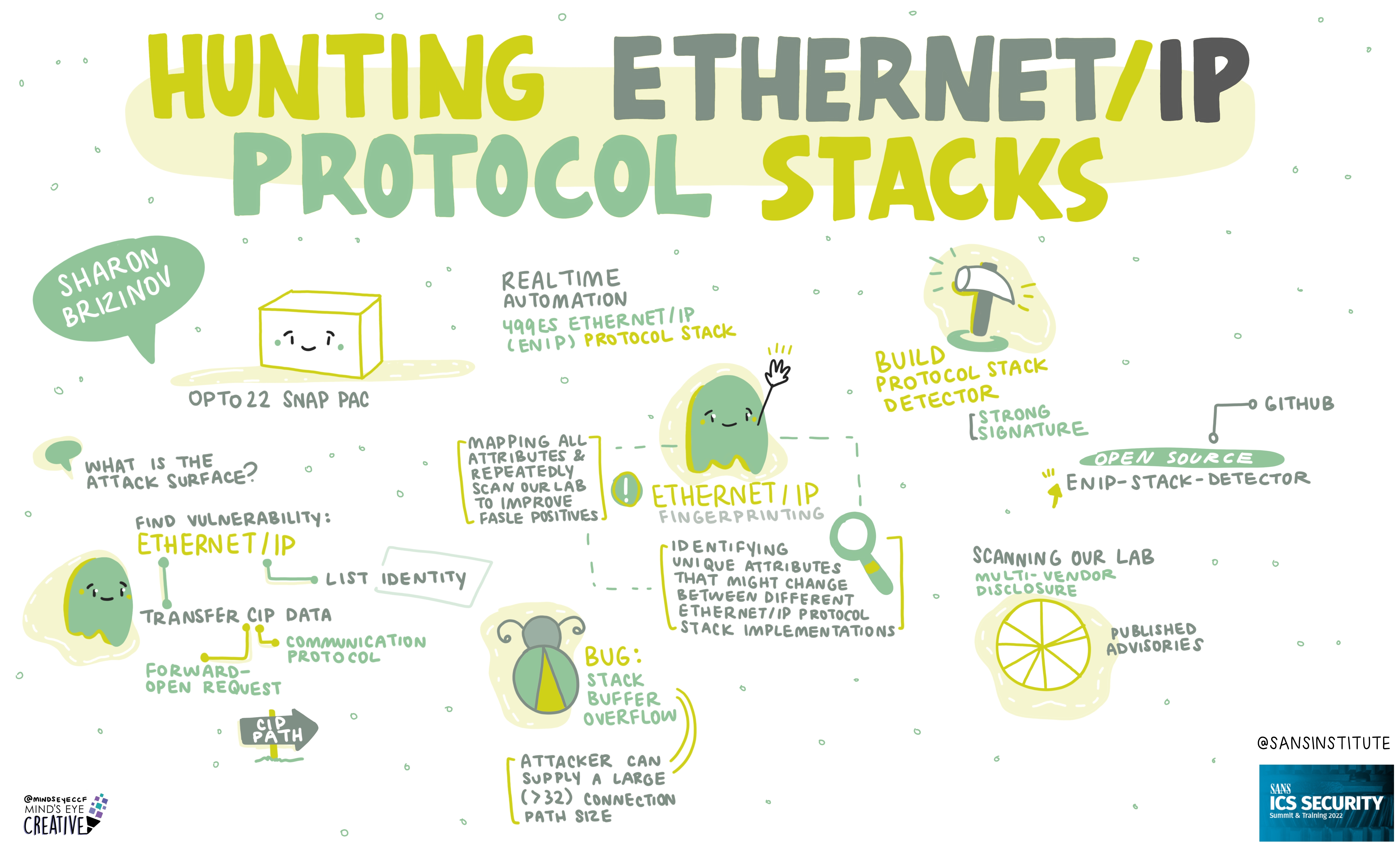
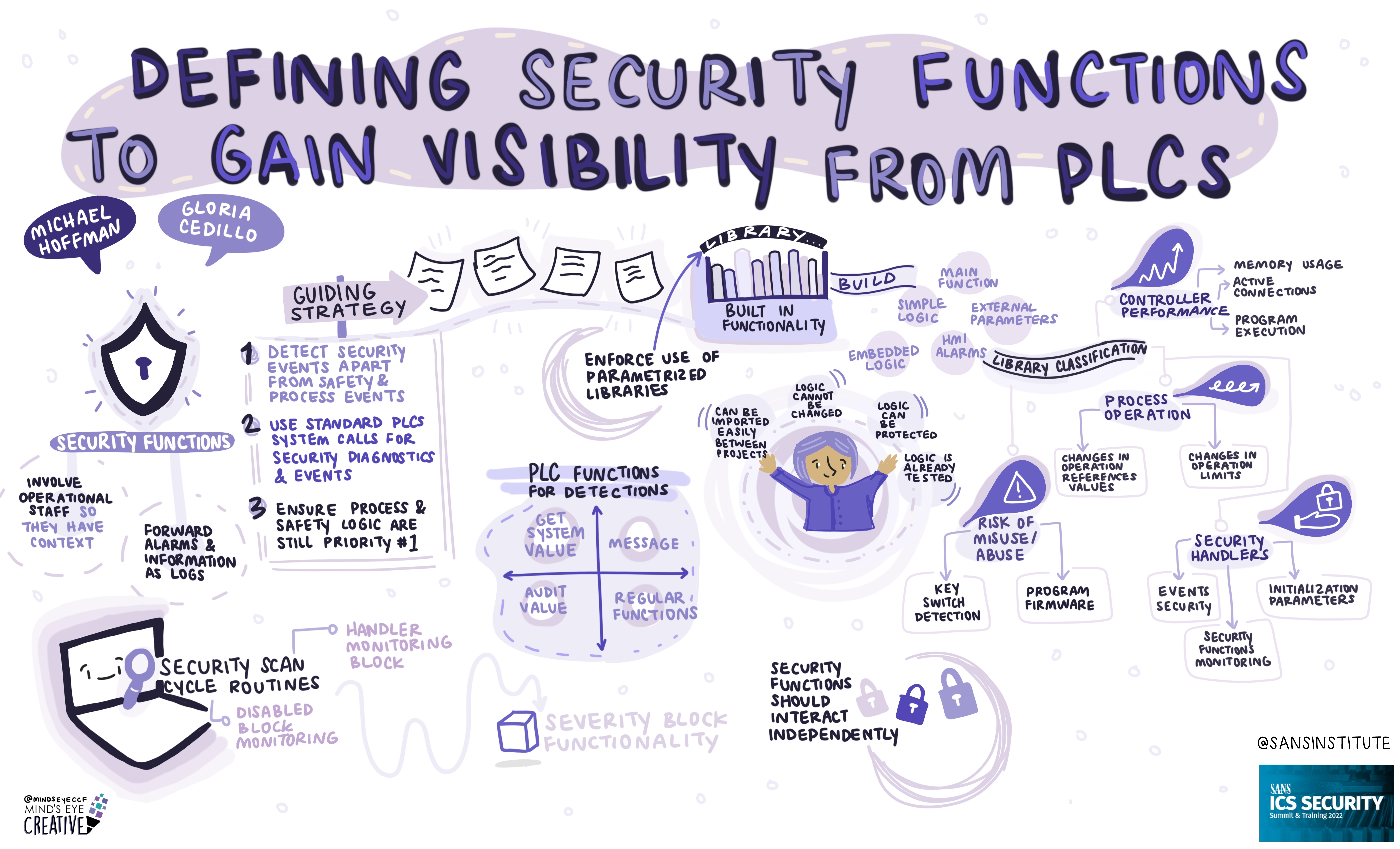
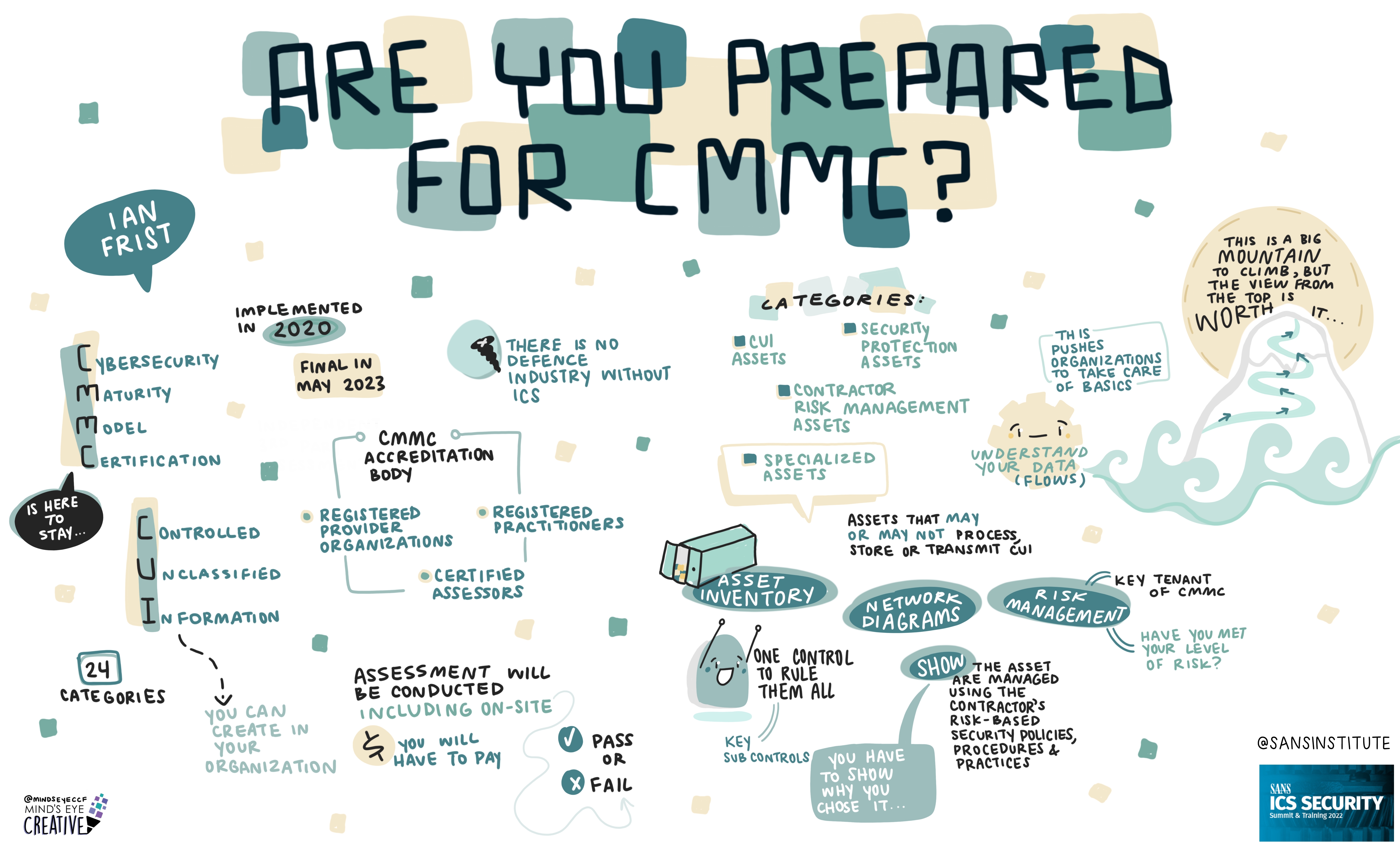
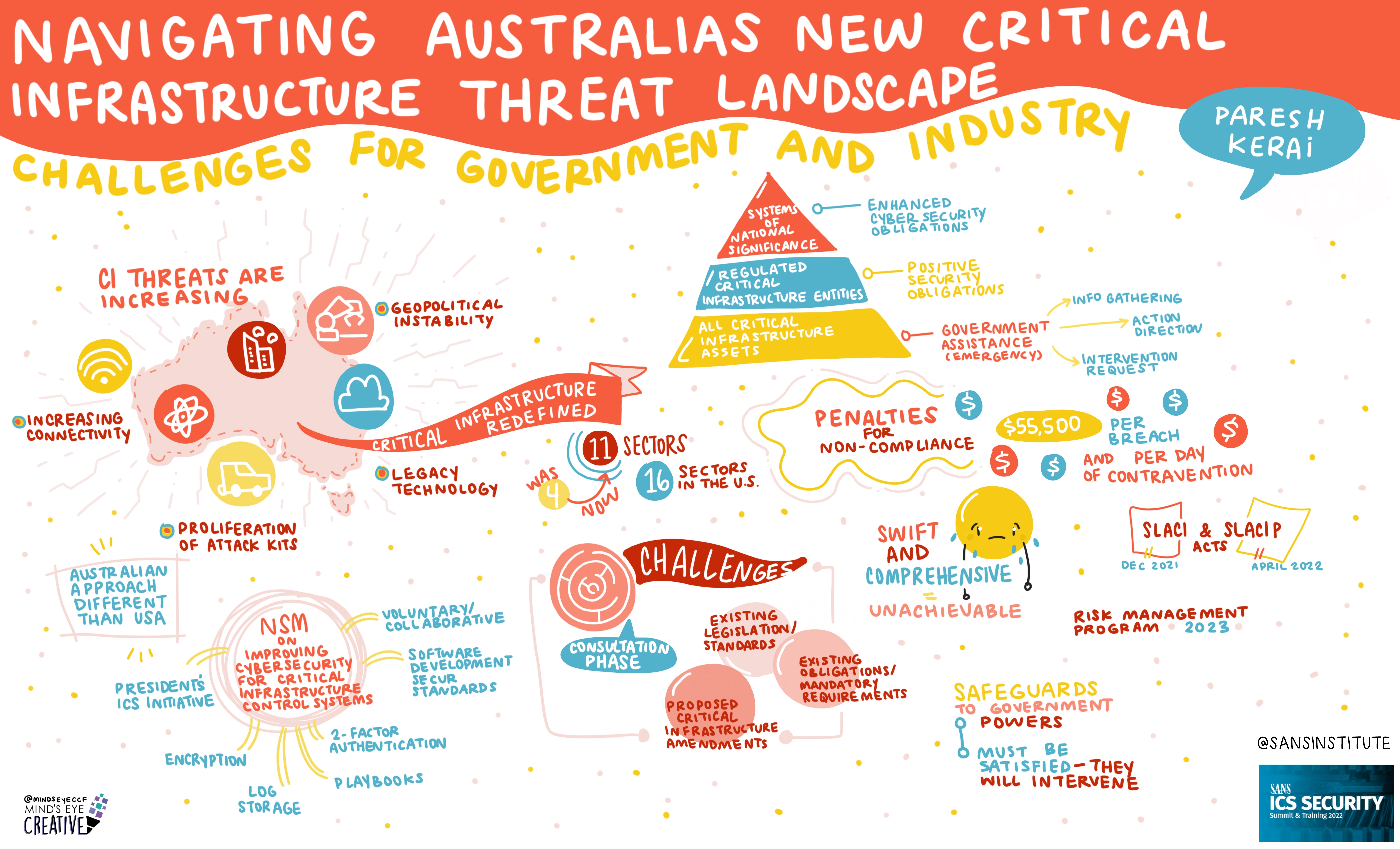
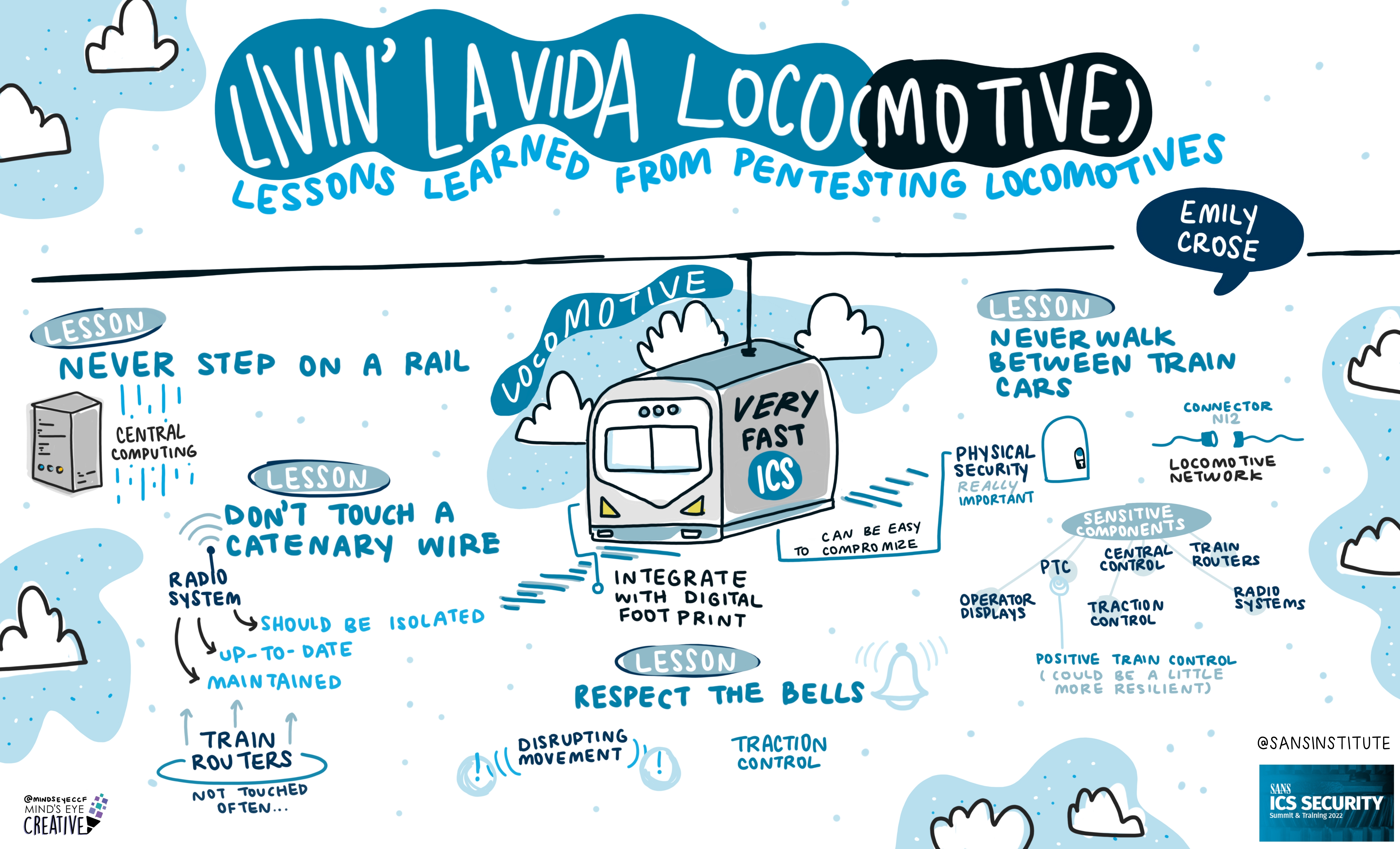
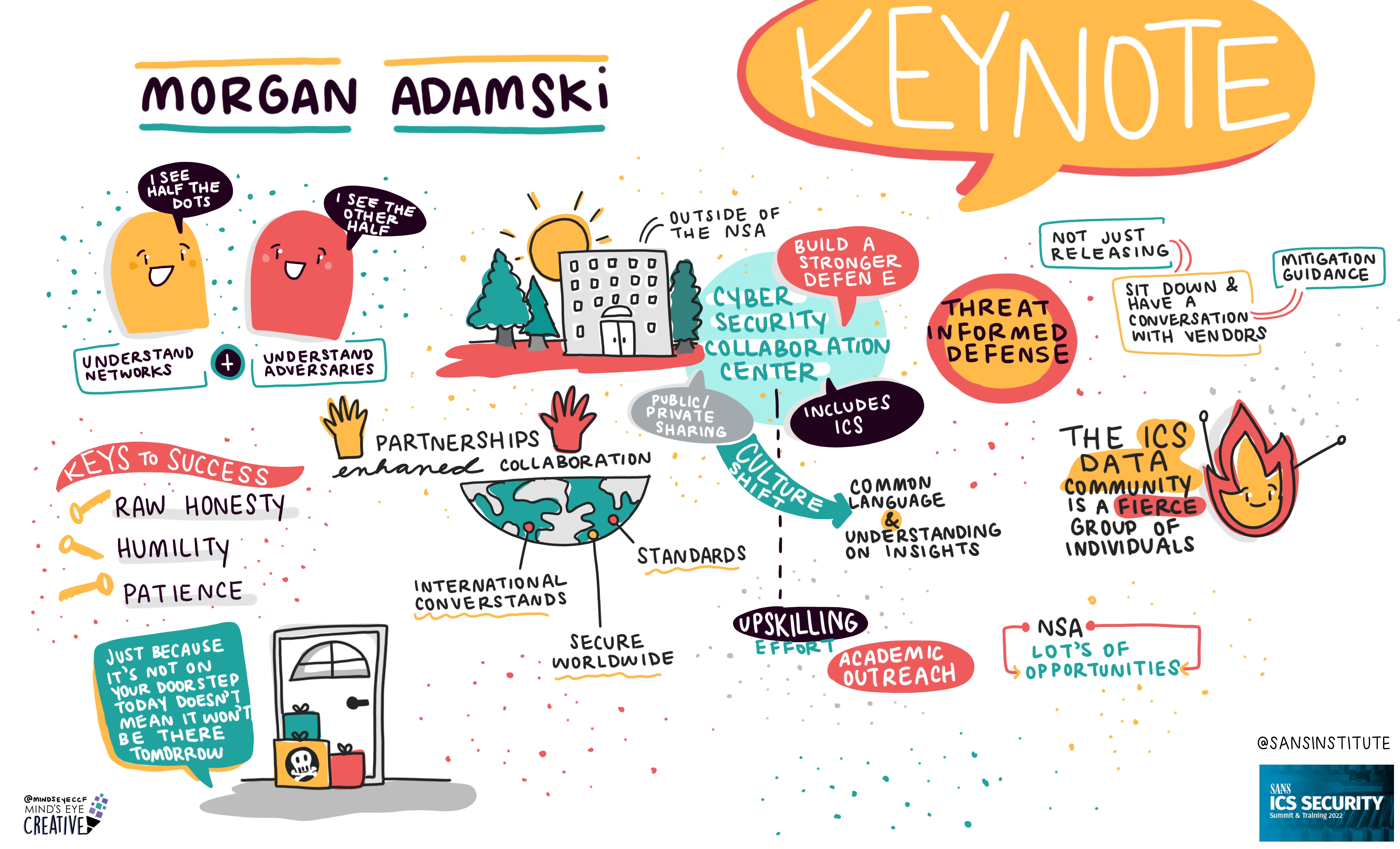

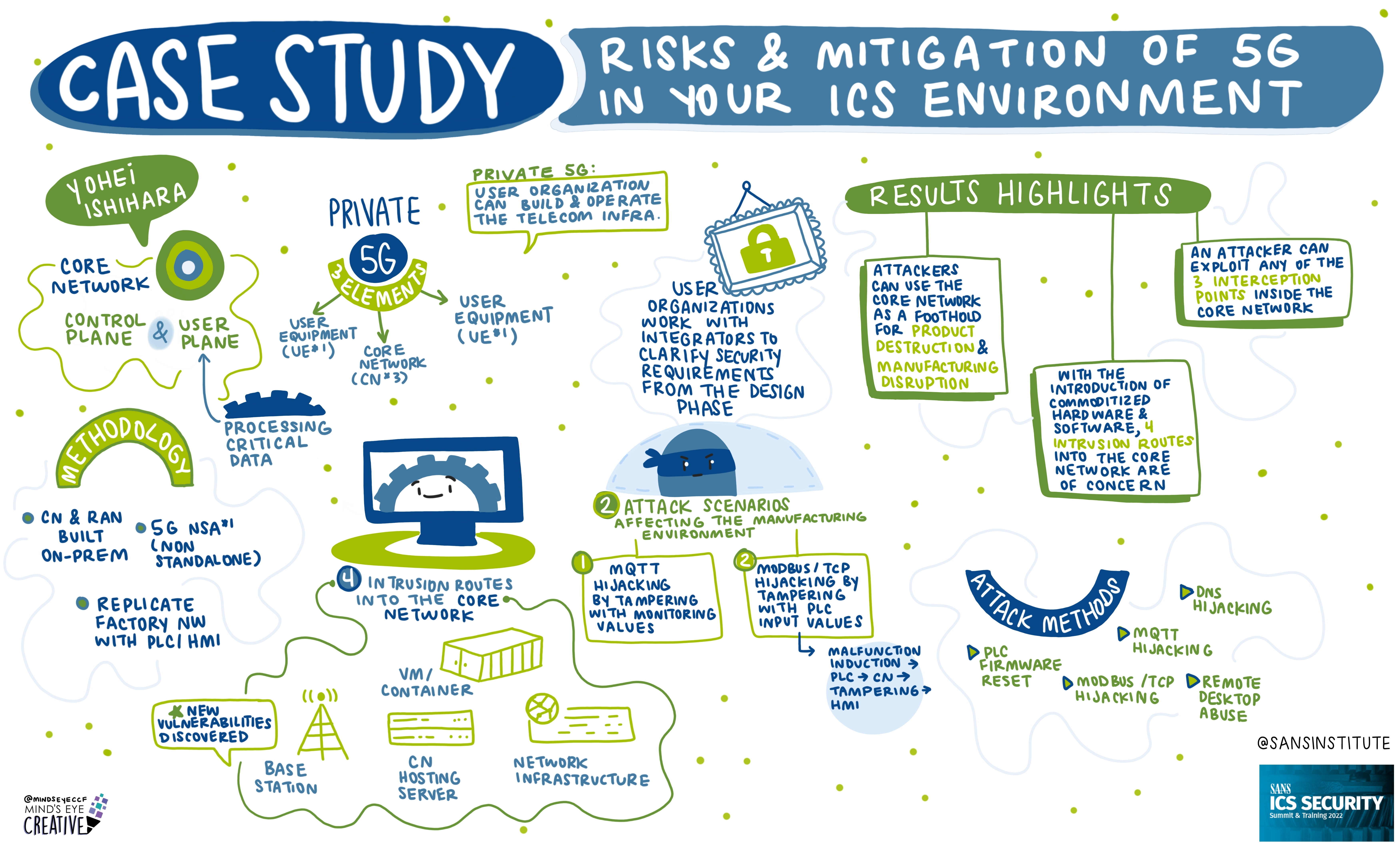
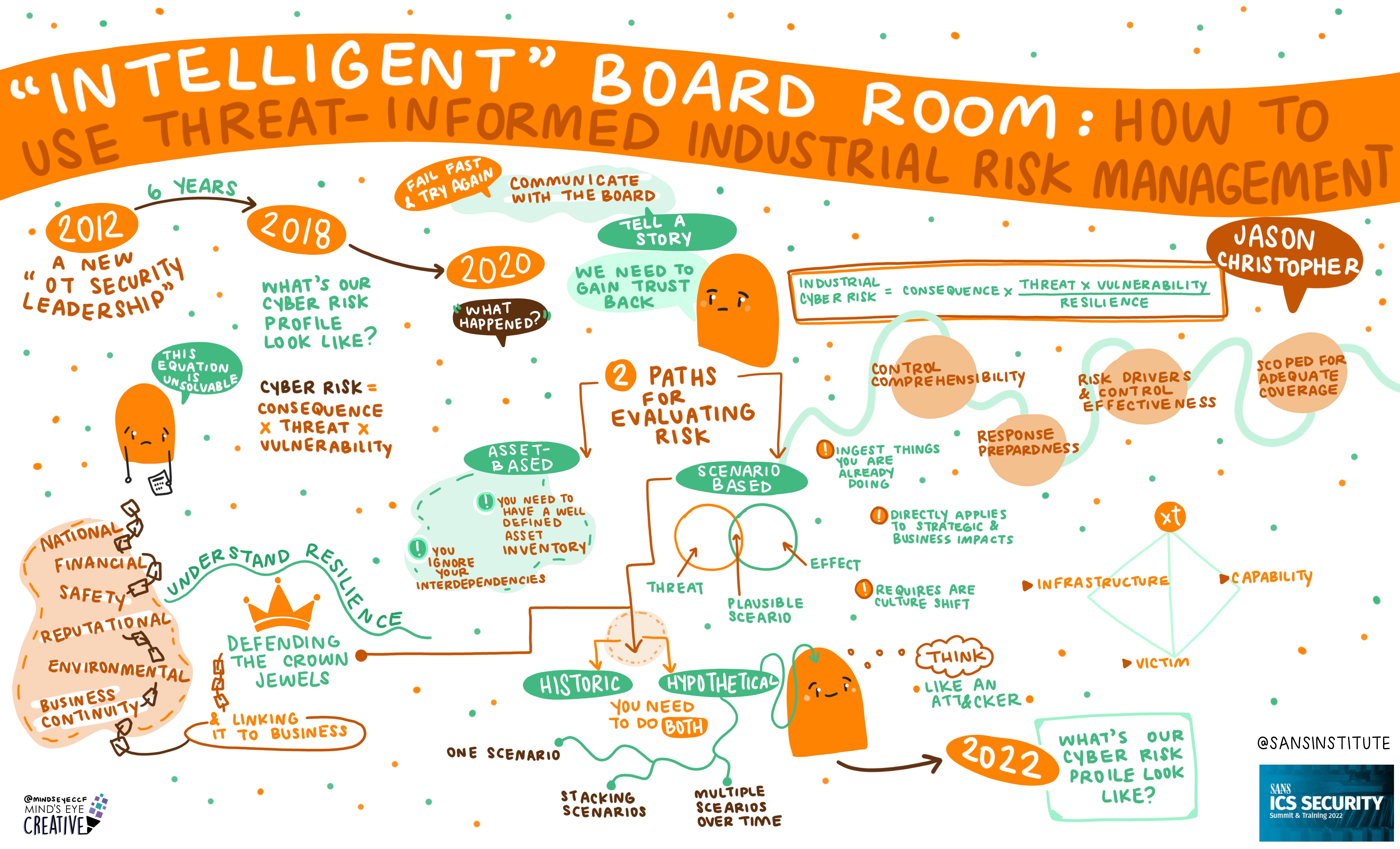
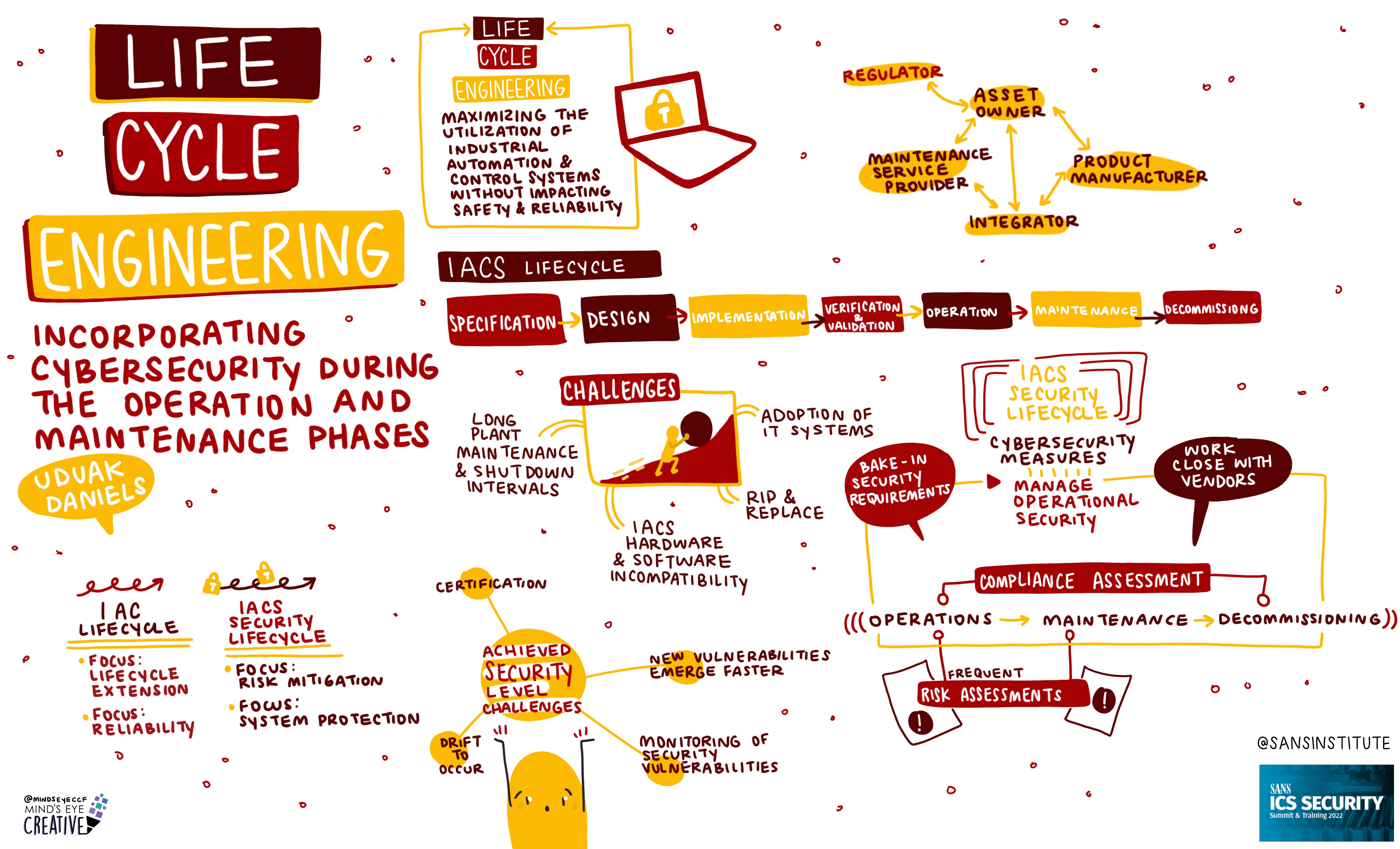
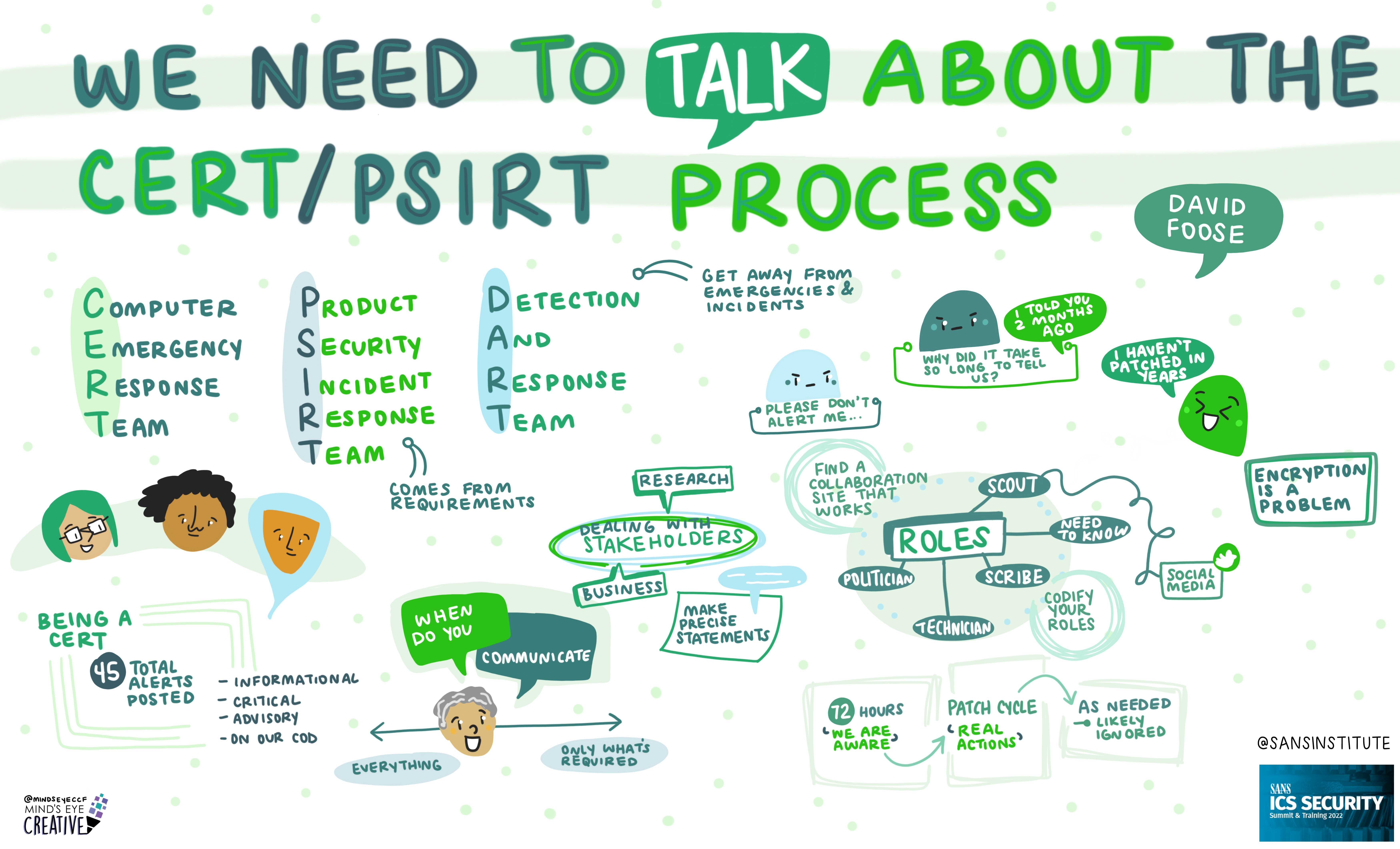
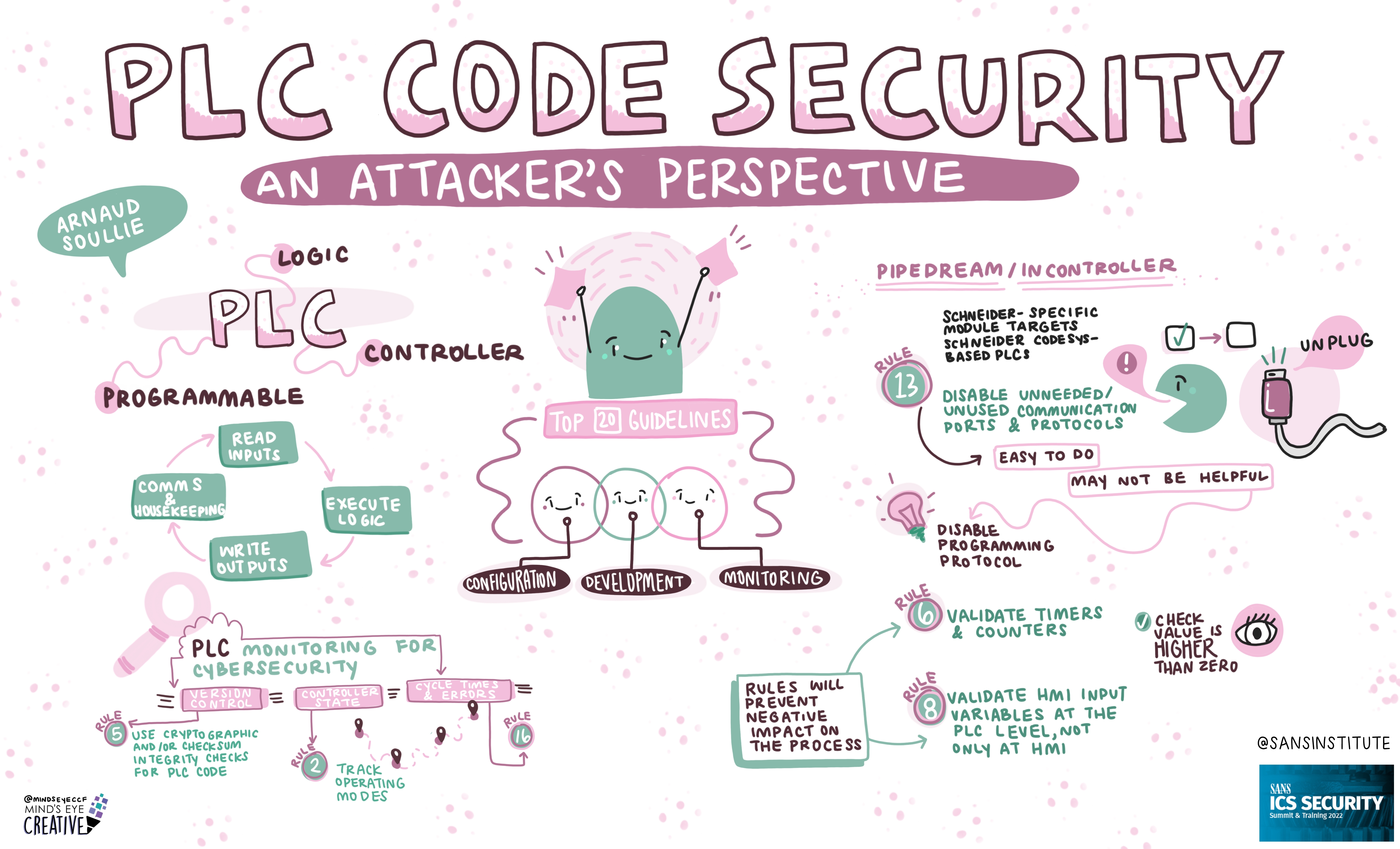
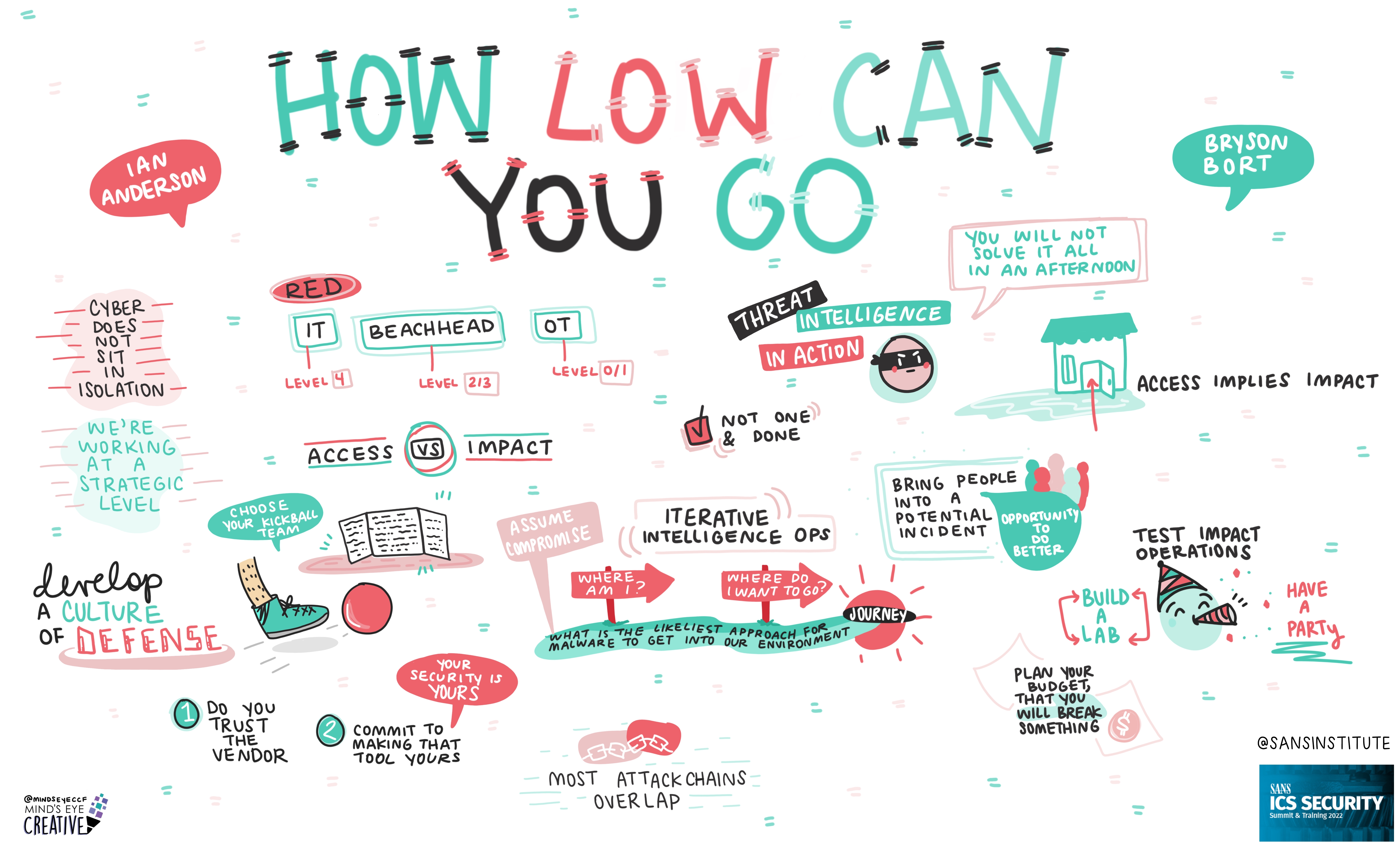
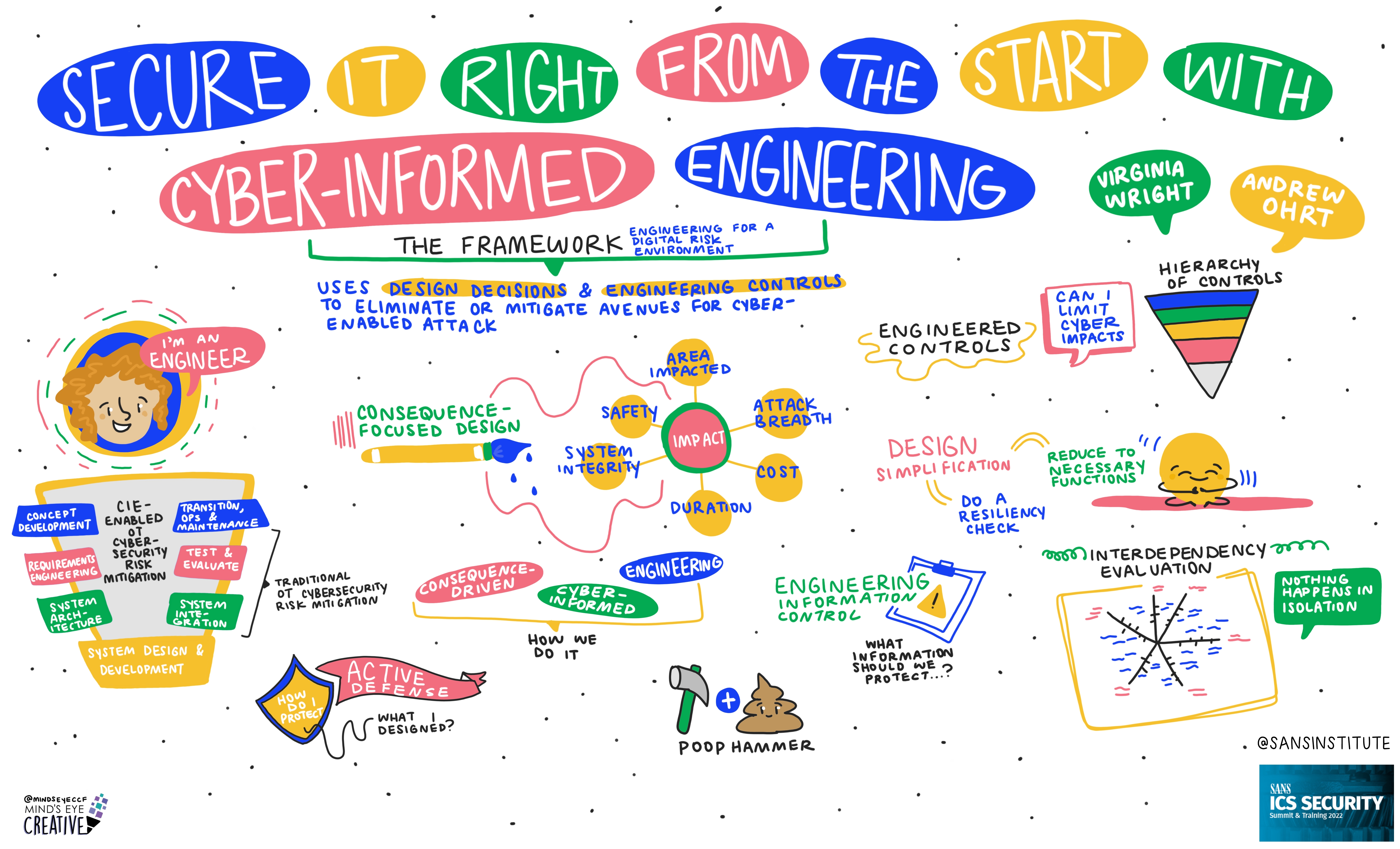
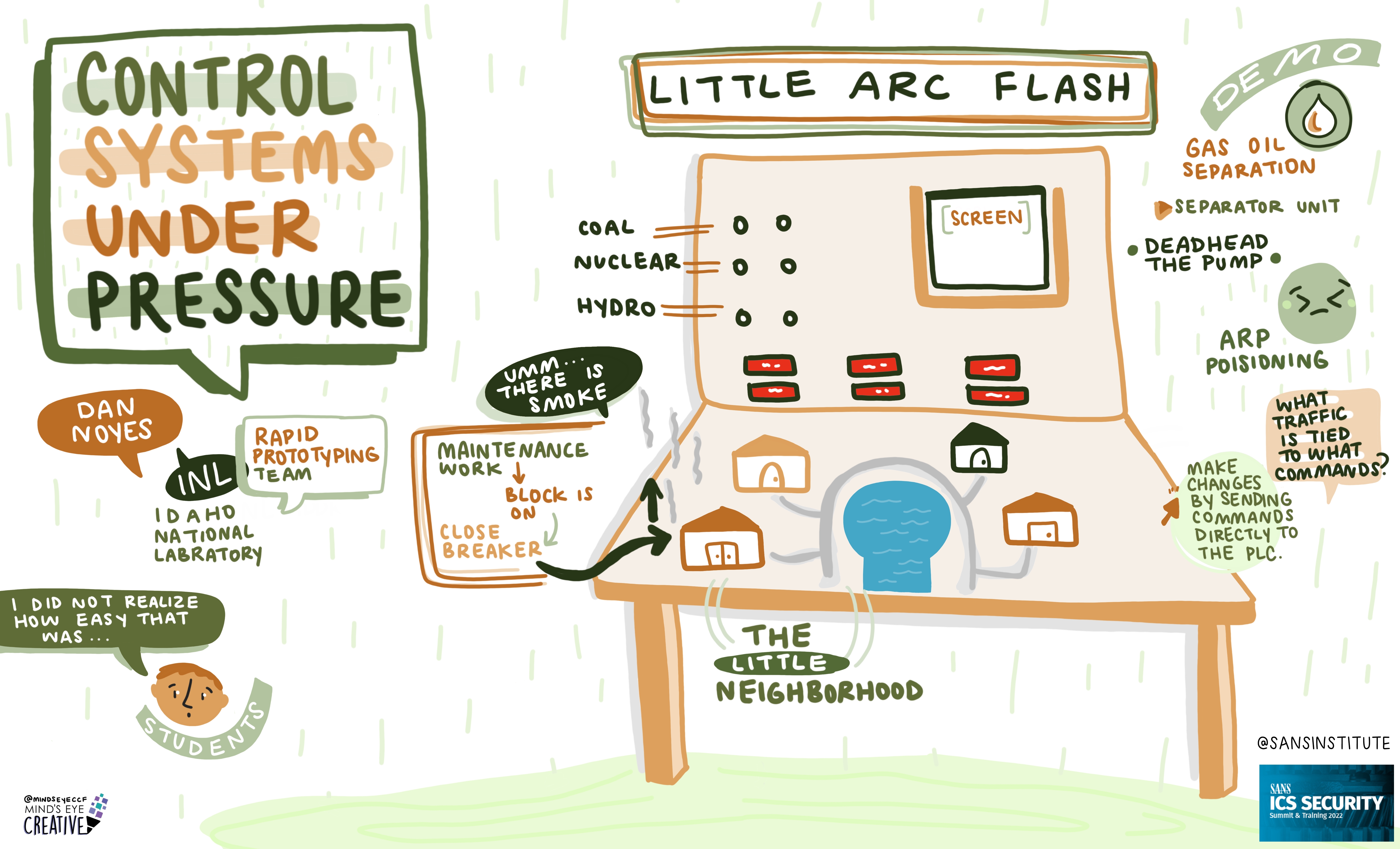
If you'd like to check out our other upcoming Summits, you can view the latest listing here.


Launched in 1989 as a cooperative for information security thought leadership, it is SANS’ ongoing mission to empower cybersecurity professionals with the practical skills and knowledge they need to make our world a safer place.
Read more about SANS Institute