SEC595: Applied Data Science and AI/Machine Learning for Cybersecurity Professionals


Experience SANS training through course previews.
Learn MoreLet us help.
Contact usBecome a member for instant access to our free resources.
Sign UpWe're here to help.
Contact Us
On November 15-16, thousands from around the globe tuned in for the SANS Pen Test HackFest Summit. These two days were filled with new tools and techniques to help attendees advance their skillset.
We invited Ashton Rodenhiser to create graphic recordings of our Summit presentations. If you missed a talk or are looking to view the SANS Threat Hunting Summit through a visual lens, take a look at the recordings below.
In addition to graphic recordings, PDFs of Summit presentations are available on the SANS Summit Archives page (SANS account required) and videos will be posted to YouTube over the next several months.
*If you registered for the Summit, video recordings are available on your Summit Access page in your SANS Portal.
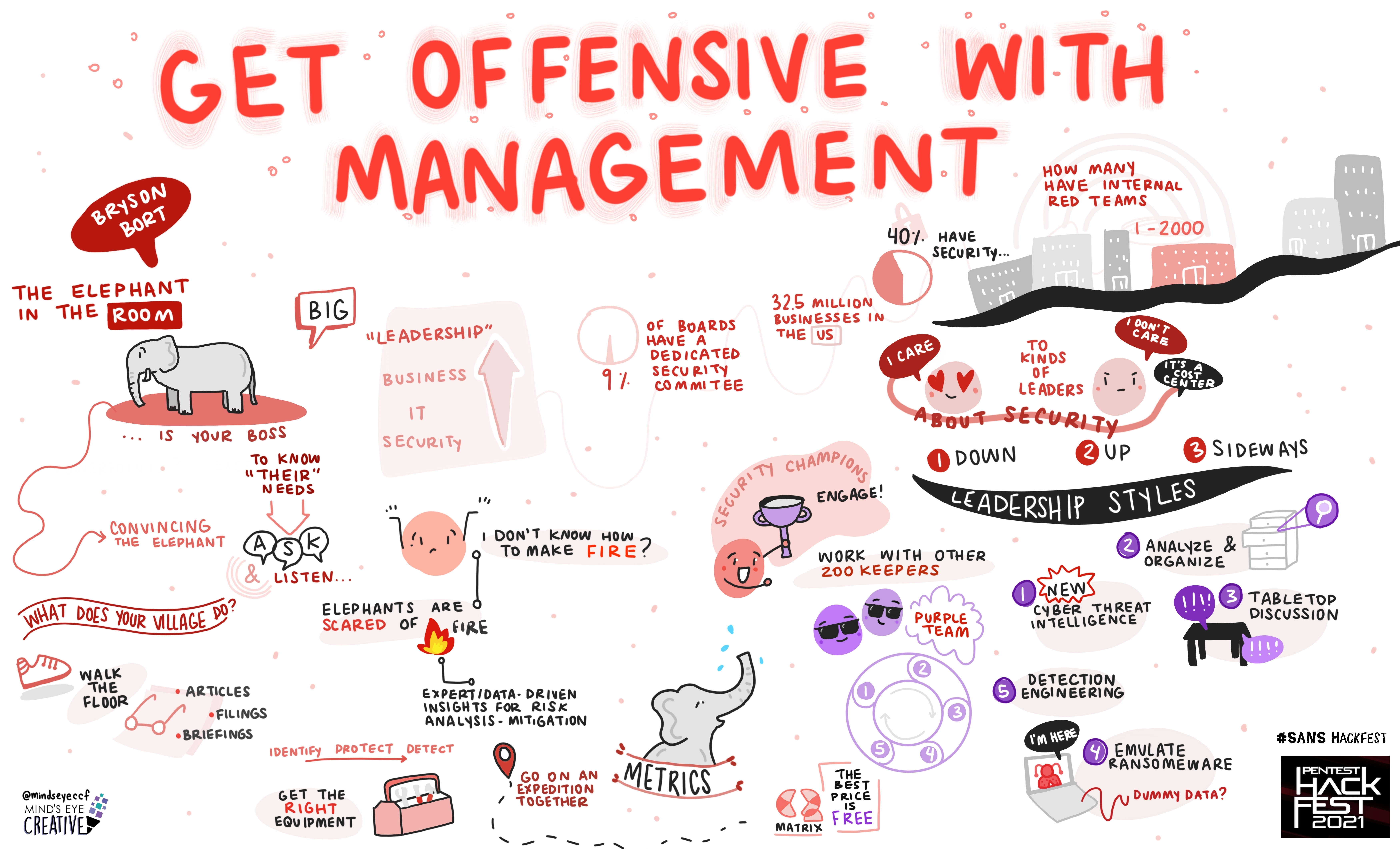
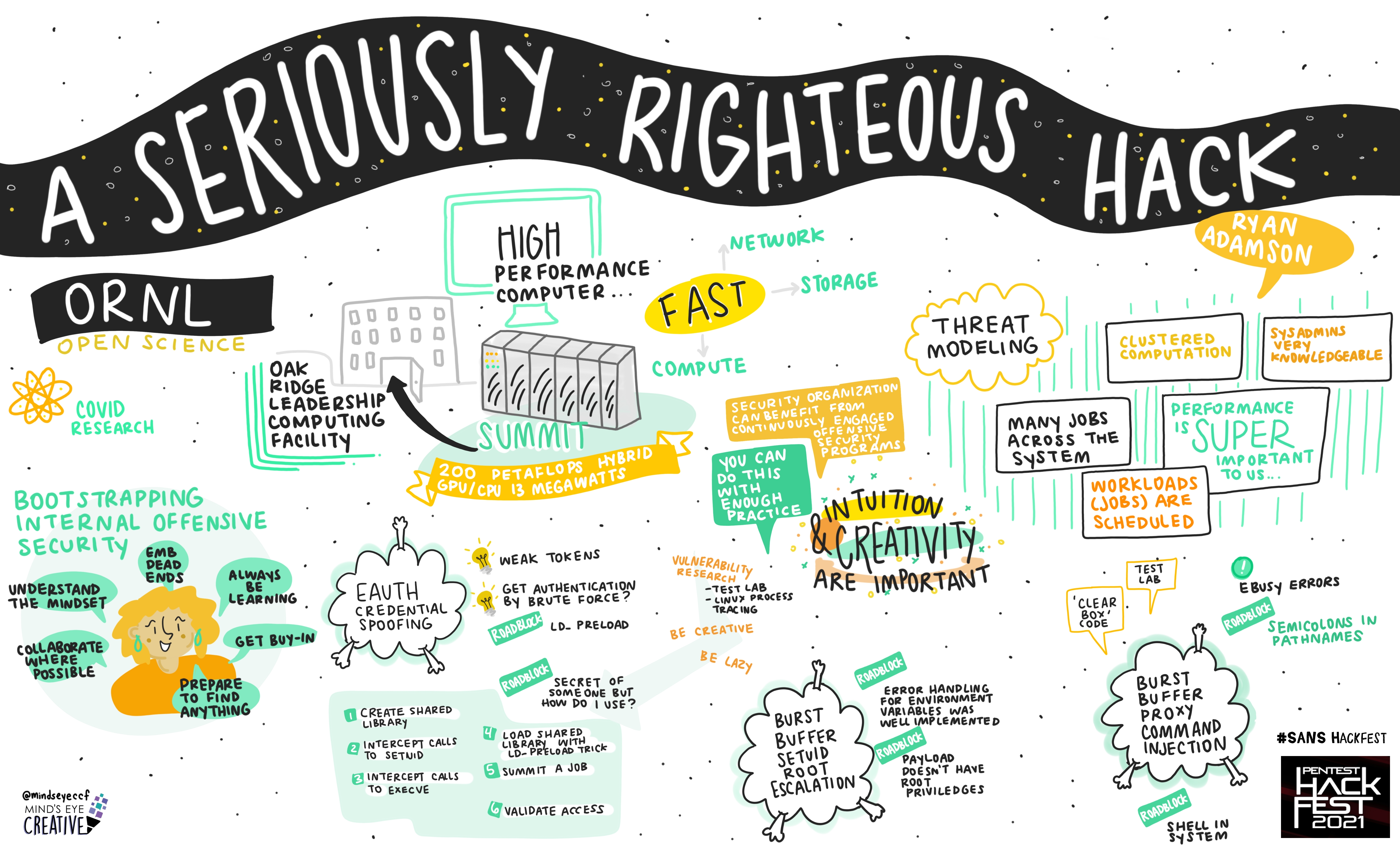
Keynote: Get Offensive with Management Bryson Bort, Founder & CEO, Scythe
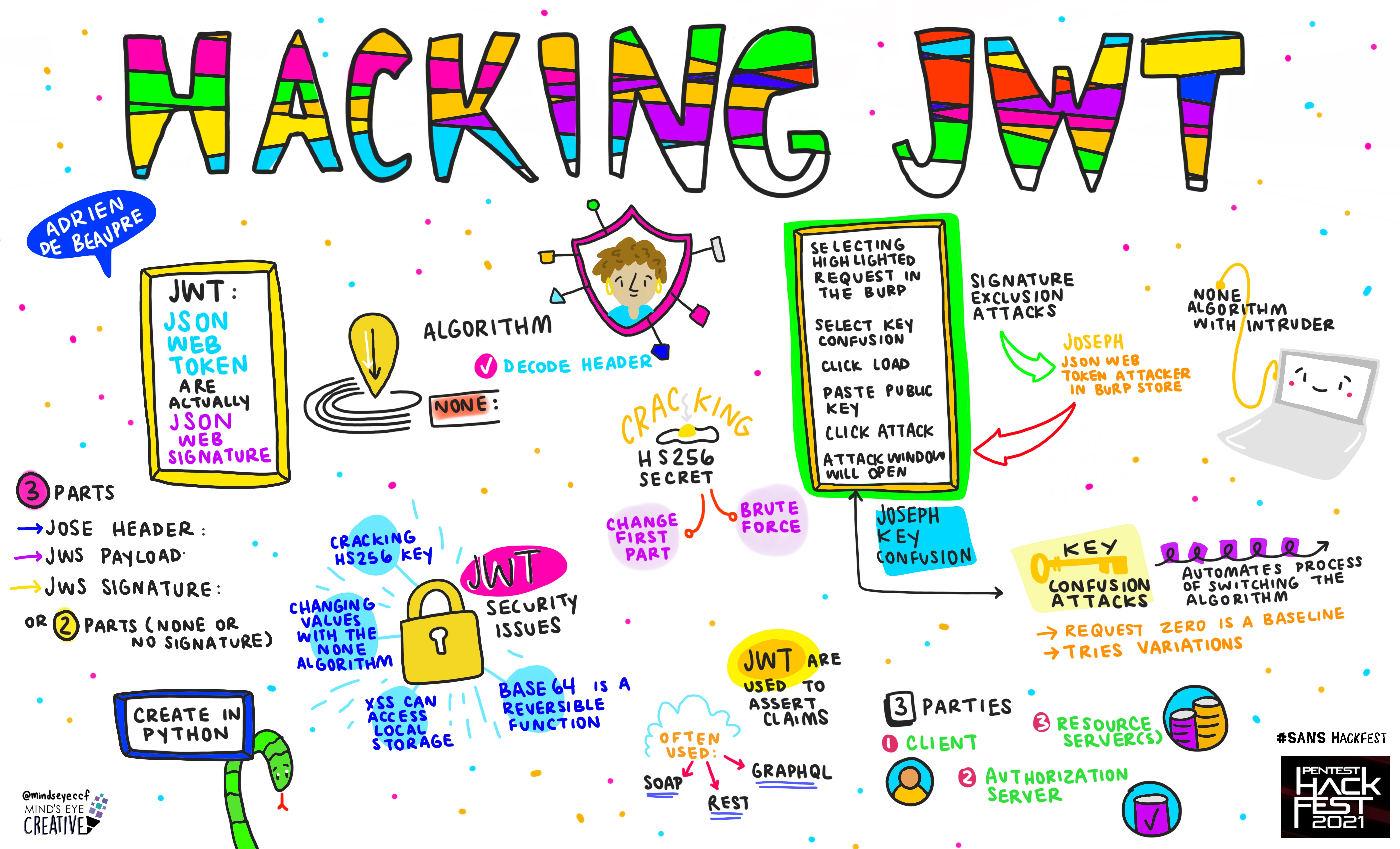
Adrien de Beaupre, Principal Instructor, SANS Institute
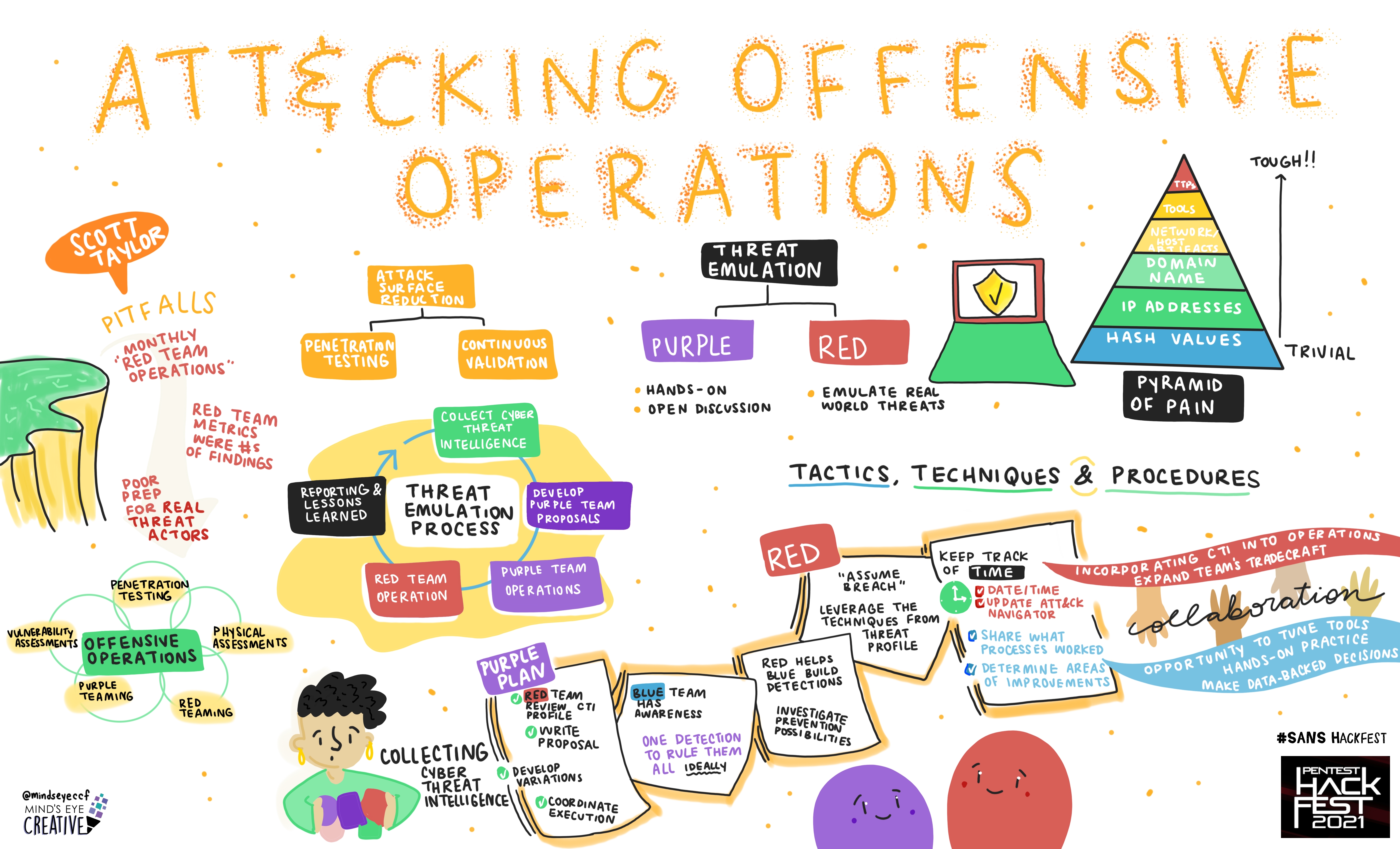
Scott Taylor, Senior Red Team Operator, T. Rowe Price
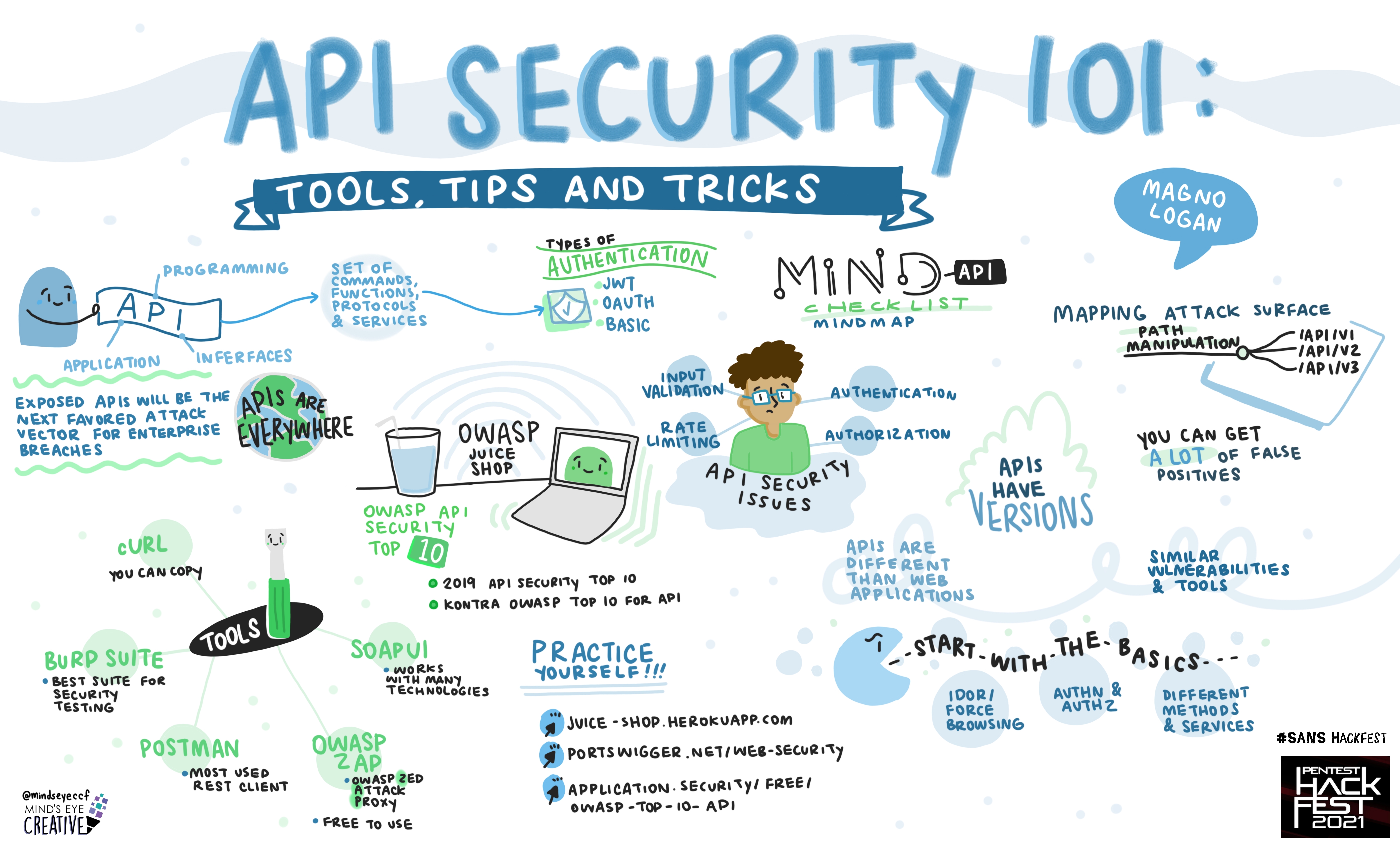
API Security 101: Tools, Tips and Tricks
Magno Logan, Information Security Specialist, Trend Micro
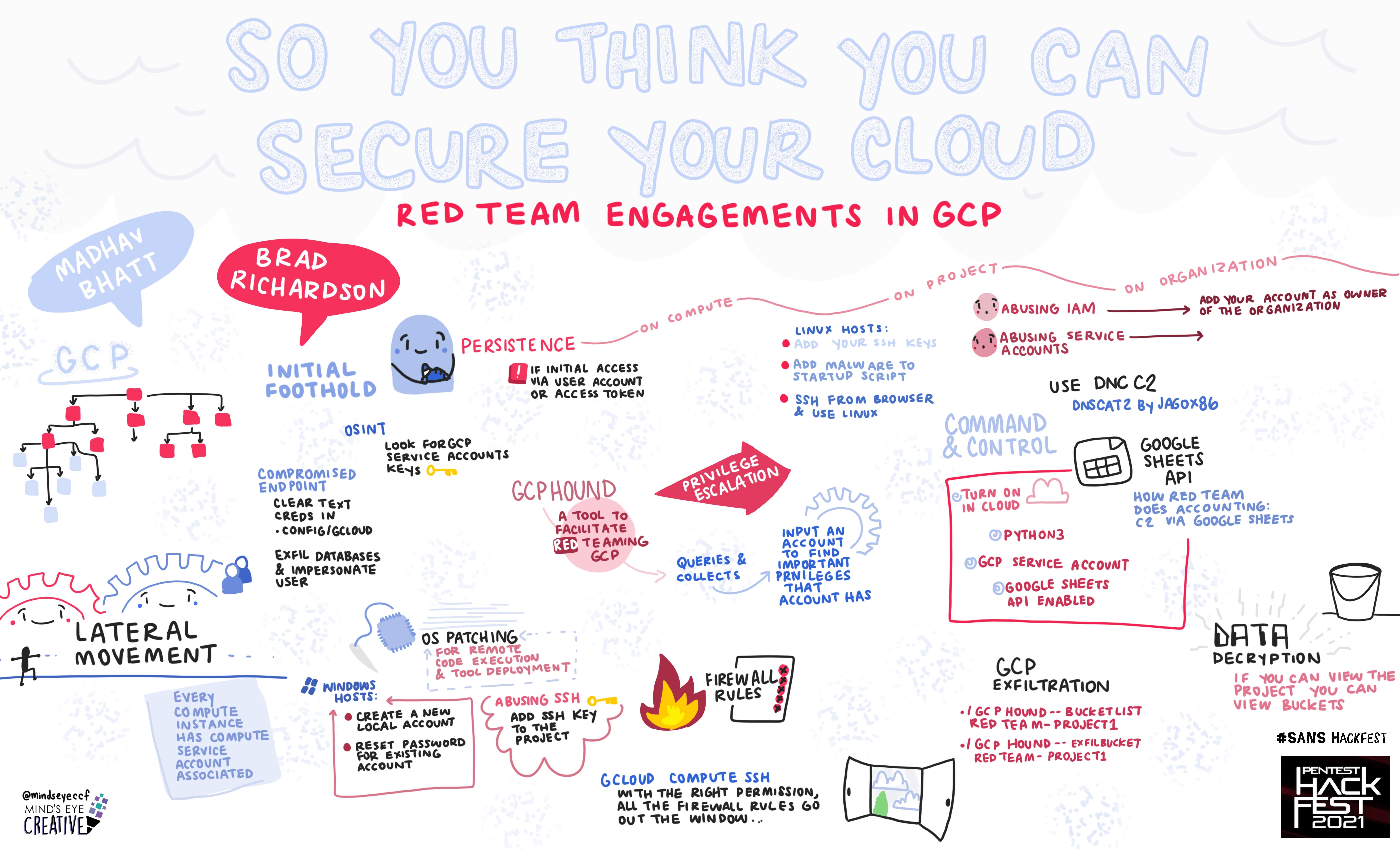
Madhav Bhatt, Offensive Security Engineer, Credit Karma | Brad Richardson, Credit Karma
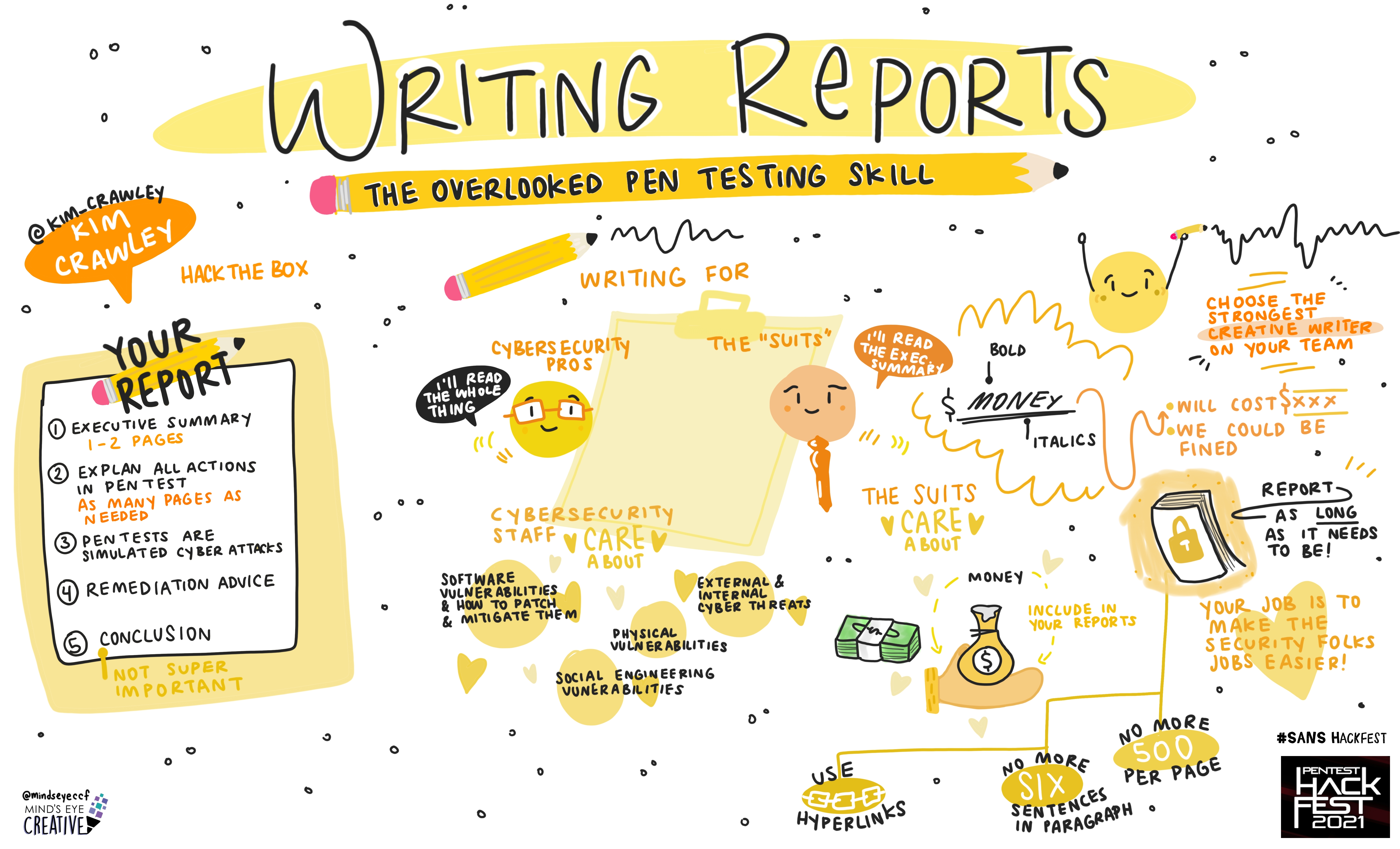
Kim Crawley, Blog Manager, Hack the Box
Tennisha Martin, Executive Director & Chairwoman, BlackGirlsHack

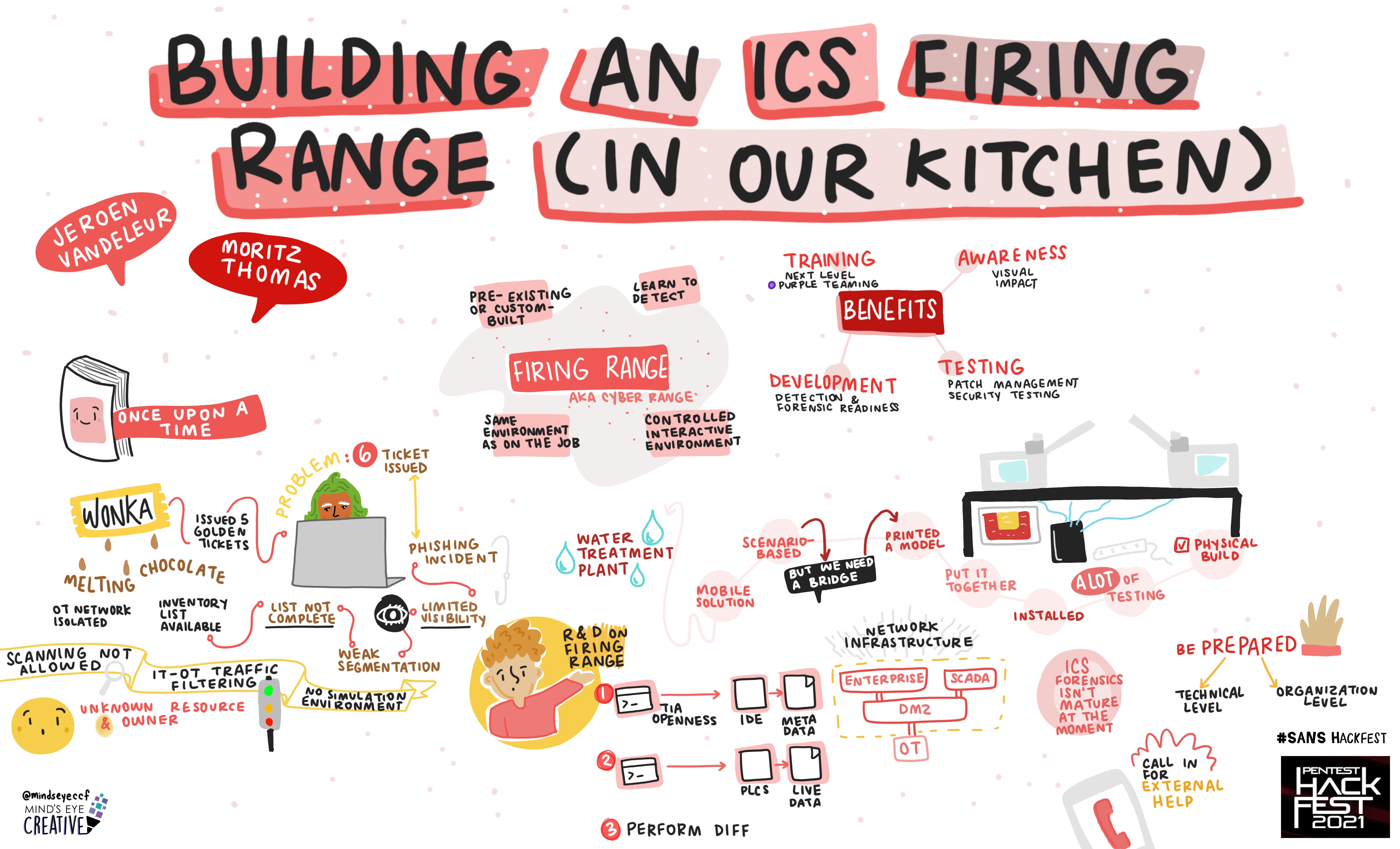
Jeroen Vandeleur, Service Line Lead, NVISO | Mortiz Thomas, Security Consultant, NVISO
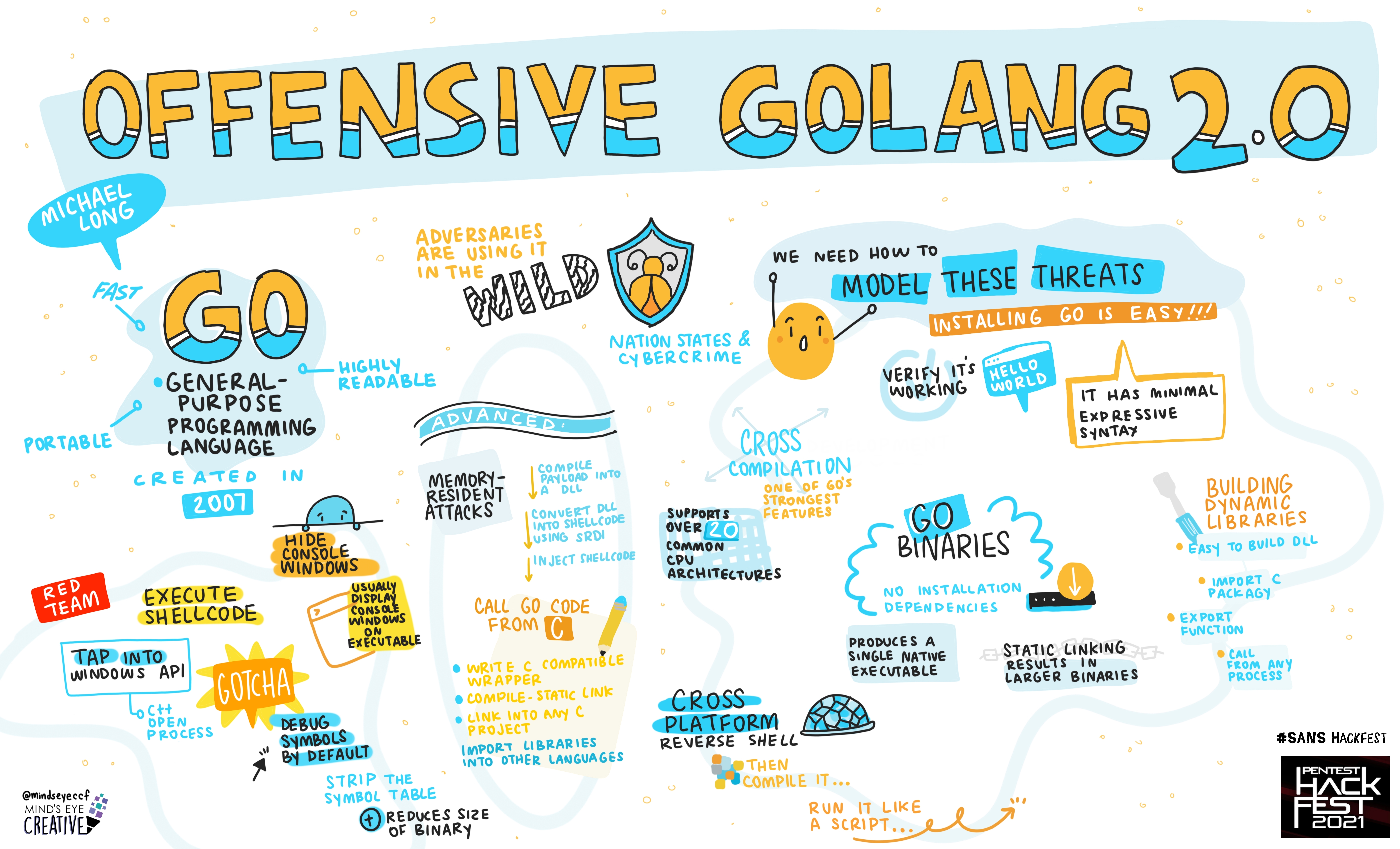
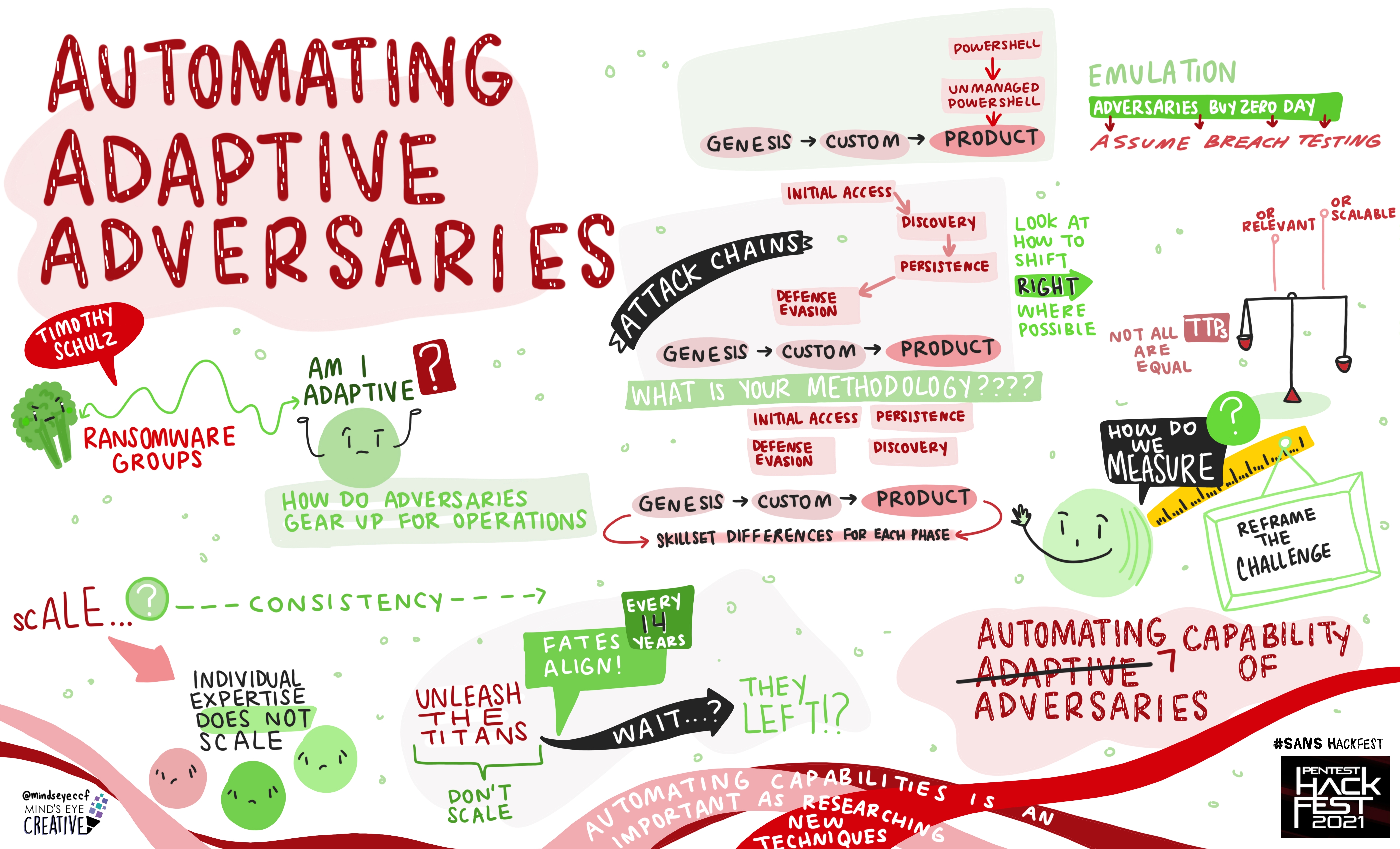
Michael Long, Principal Adversary Emulation Engineer, MITRE Corporation
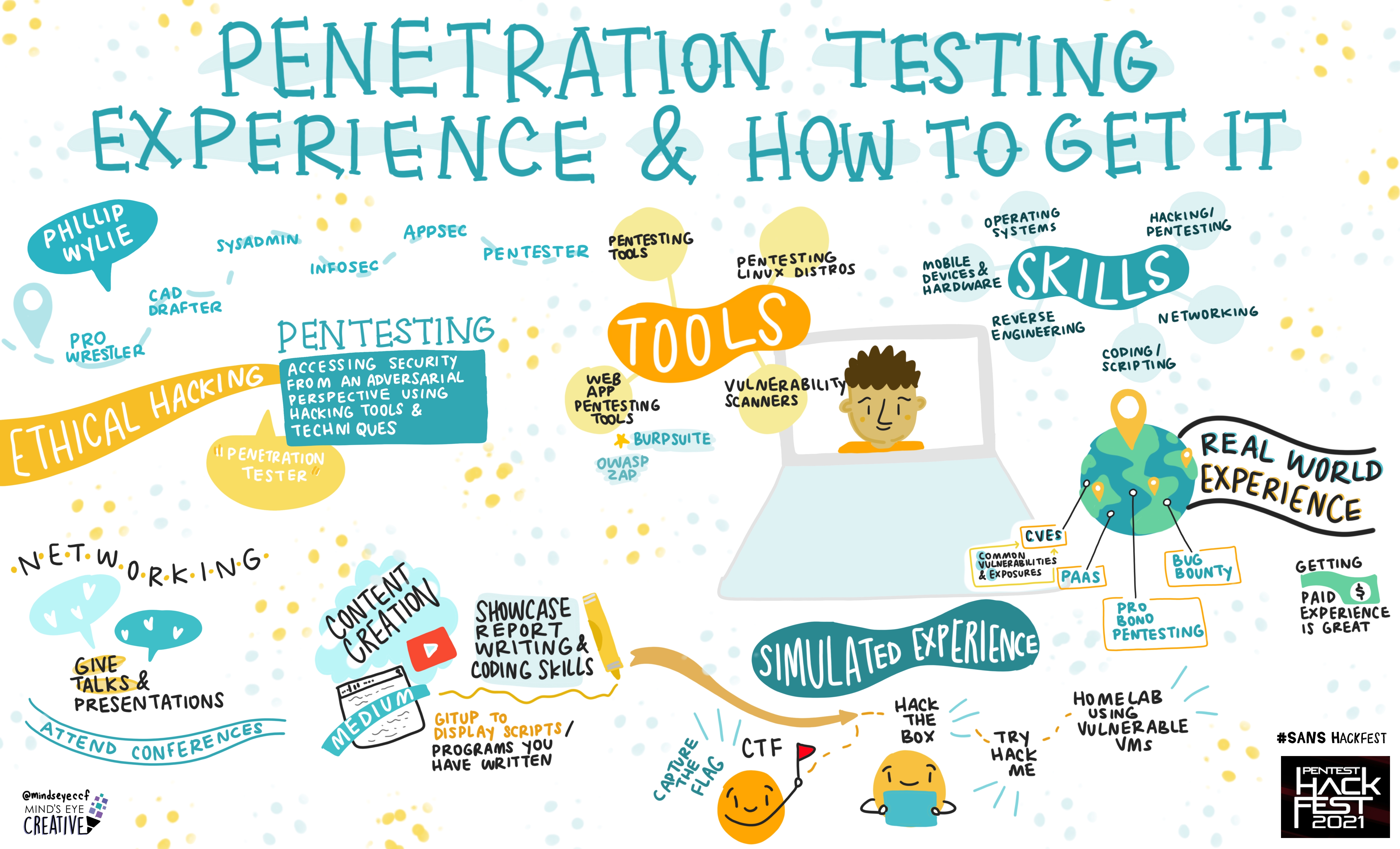
Penetration Testing Experience and How to Get It
Phillip Wylie, Senior Cloud Penetration Tester, U.S. Bank
Timothy Schulz, Adversary Emulation Lead, SCYTHE Inc.
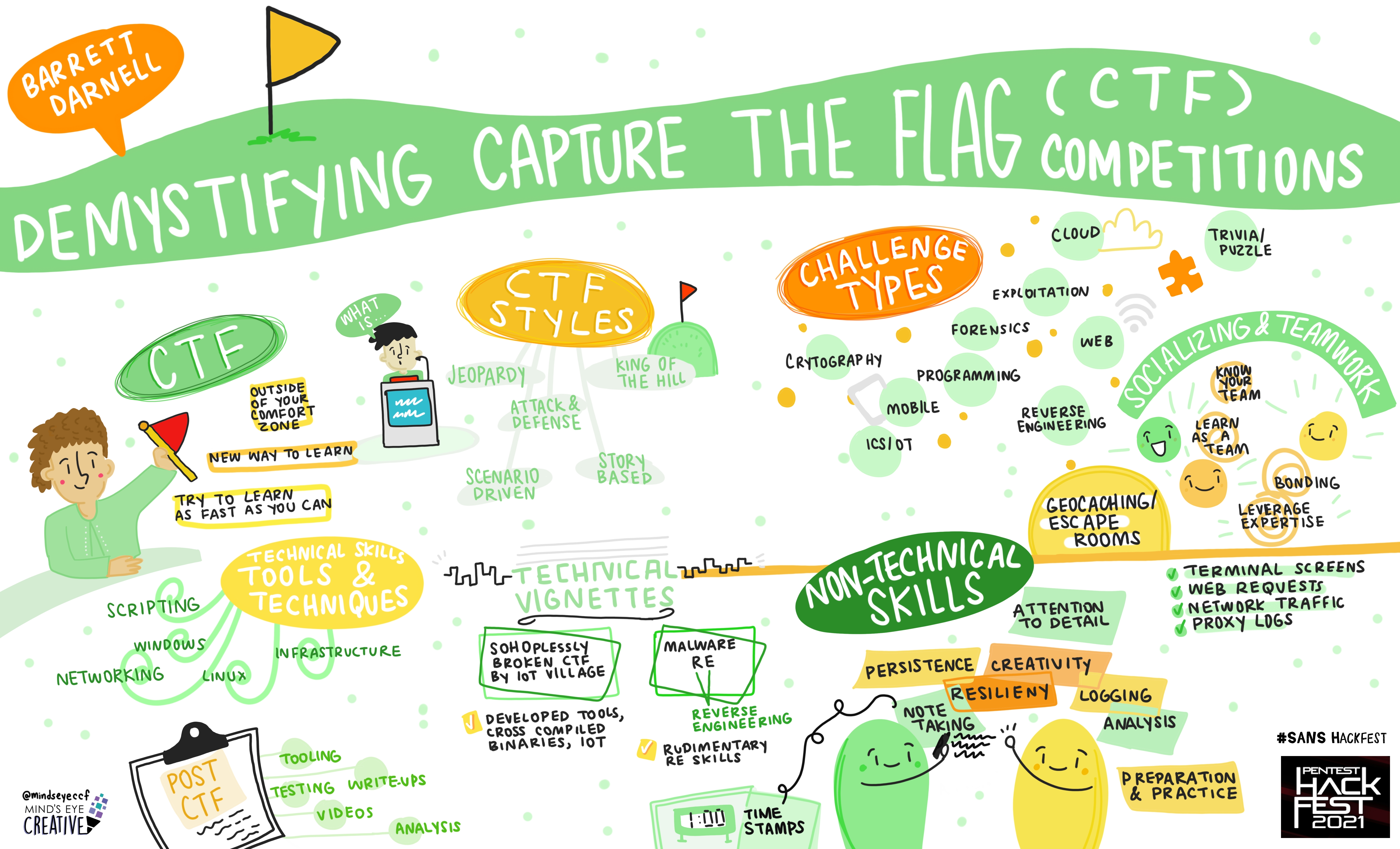
Demystifying Capture the Flag (CTF) Competitions
Barrett Darnell
If you’re interested in seeing other in-person and free virtual events SANS has lined up, visit the current listing.


Launched in 1989 as a cooperative for information security thought leadership, it is SANS’ ongoing mission to empower cybersecurity professionals with the practical skills and knowledge they need to make our world a safer place.
Read more about SANS Institute