Introduction
The acquisition of process memory during behavioural analysis of malware can provide quick and detailed insight. Examples of where it can be really useful include packed malware, which may be in a more accessible state while running, and malware, which receives live configuration updates from the internet and stores them in memory. Unfortunately the execution of some samples can be transient and the processes will be long gone before the analyst has a chance to fire up ProcDump. A while back, HBGary released a nifty tool called Flypaper, which prevented a process from closing down, allowing more time for the memory to be grabbed, but unfortunately the tool is now difficult to find and awkward to use. I've spent some time considering a suitable alternative that would work on the latest versions of Windows.
A little known feature...
During my research I found an article detailing a little known feature in Windows entitled 'Monitoring Silent Process Exit'.
TL;DR - You can configure Windows to automatically generate a memory dump when a process with a specified name exits.
So what this means for us is, even though the malware finishes running very quickly, we can obtain a full memory dump and extract what we need from it at our leisure.
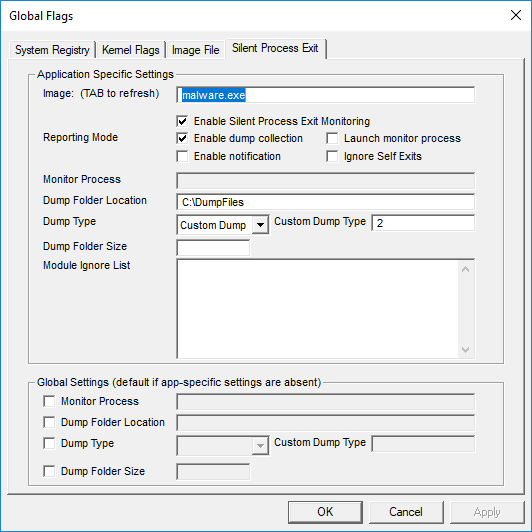
This feature is designed as part of the Windows debugging portfolio, but we can use it as a tool in our belt. The easiest way to configure is by using a Microsoft tool named gflags.exe, which is easy to download and use. The screenshot below shows the configuration that I've had success with. You provide the name of the executable you're interested in keeping an eye on (it doesn't matter from where the process is run). In addition you have the option to choose what kind of memory dump you want generating, Custom Dump Type 2 represents MiniDumpWithFullMemory, which I found to give the most comprehensive output. There are plenty of other options that can be found on MSDN. Then you just need to run the process and wait for it to finish.
Testing the concept
To test the concept I wrote a tiny program, shown below, designed to load a string to memory and have the process exit very quickly - certainly before we would have a change to pull the string from live memory.
int main()
{
char secretString[] = "This is a secret string!";
return 0;
}
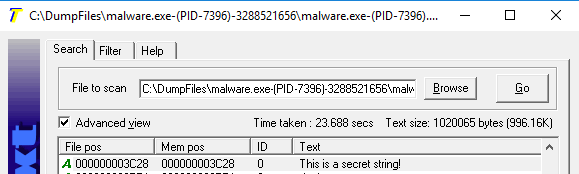
I compiled, executed and the mini dump appeared in the appropriate folder. A quick check with BinText showed the secret string that had been stored in memory.
This is all instigated through a small number of registry entries, details of which are listed in the Microsoft article on the subject, and could easily be implemented into a sandbox or endpoint security setup to gather clues about what has occurred. I've found this to be a neat alternative to Flypaper without having to go to the trouble of writing a hook for the ExitProcess function.
Happy analysing!
-Adam (Twitter: @CyberKramer)




