SEC595: Applied Data Science and AI/Machine Learning for Cybersecurity Professionals


Experience SANS training through course previews.
Learn MoreLet us help.
Contact usBecome a member for instant access to our free resources.
Sign UpWe're here to help.
Contact UsIt usually takes an incident such as ransomware to change an organization’s focus and approach on how they view security, but where do they start?

This is Part II of a 3-part blog series based on MGT514: Security Strategy, Policy, and Leadership.
Read Part I here. Read Part III here.
An important question to answer at this point is, how did Rekt Casino get here? You can find the answer to that question by reviewing the history of the organization, interviewing the executive team, other key stakeholders, and visiting with accounting.
I’ve found that accounting departments categorize spending really well, and you’ll want to review all the technology related investments over the past few years.
A good way of representing that investment to the business leaders is to show how technology and attacks have changed over the years in comparison to their investment in security over the years.
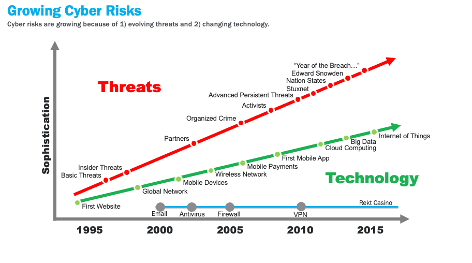
Figure 2: Threats versus Technology Evolution
The above diagram shows how technology has advanced from 1995 to 2015 in comparison to how threats and attacks have progressed over the same time period.
To show the comparison to Rekt Casino you could prepare a similar timeline and show what their security investments have been over the past 5-10 years.
Now is also a good time to perform a SWOT analysis. In a post breach scenario, you have real information base your assessment on where ordinary it might be from self-reporting or partially hypothetical data.
A SWOT analysis shows the Strengths, Weaknesses, Opportunities, and Threats to the casino from a security perspective.
A simplified SWOT analysis for Rekt casino might look similar to the following:
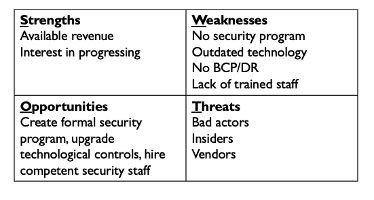
An actual SWOT analysis would go into more detail, this simplified version is just an example of a high-level analysis.
Based on the events at Rekt Casino, it can be assumed that there is no understanding of the threats they face. Take the time to outline the threats and create a high-level threat model that explains them in context. This makes it easier for the decision makers to understand as your build your security program.
Complimentary to the SWOT analysis is the PEST analysis. The PEST analysis is relevant because the breach could have been a result of Political, Economic, Social, or Technological factors.
Performing a PEST analysis can help you and the organization understand the threats that might not have been previously realized.
Even if the PEST analysis doesn’t show data directly related to the attacker, it could reveal areas of threats where defenses were not invested in previously. This is important to know as you start the process of building an information security program.
A simplified PEST analysis for Rekt Casino might look similar to this:
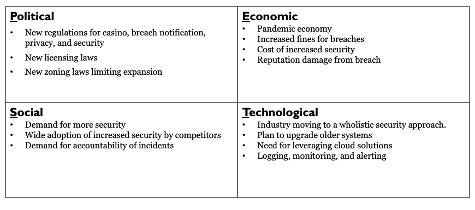
As you can see in the above PEST analysis example, most of these factors are outside of the organization’s control. You won’t be able to address all of them, but you can consider implementing compensating controls to help limit the impact in some cases.
Now is a good time to take a step back and consider how you are going to start building the program.
You might be considering the approach of implementing Initiatives to immediately secure the environment and improve from there. A better approach would be to follow an industry standard framework and build in compliance by design.
This approach secures the network, and all covers the MICS regulations Rekt Casino is subject to. For our example with Rekt Casino, we are going to utilize the following frameworks
Notice we are using two industry standard frameworks:
One is a security program framework, and the other is a control framework.
The reason for this is, if you compare the two individually you will realize there are some gaps, by utilizing both with this approach, we cover the gaps and have a more secure environment.
If you map the NIST CSF to the CIS Controls, and the MICS regulations, you will find you have overlap that creates a comprehensive information security program.
In fact, if implemented the NIST CSF, and CIS Controls, and then looked at what you needed to implement MICS, you would find nearly all of the requirements for MICS are already met.
By following the NIST CSF we are going to focus these security related functions:
Identify, Protect, Detect, Respond, and Recover. The NIST CSF is an industry standard approach for managing security risk.
At a high level, the NIST CSF looks like this:

There are subcategories under each activity that an organization can choose to implement. Since this is a voluntary framework, it’s up to the organization what they want to implement, and when they want to implement it.
The Center for Internet Security Controls, or CIS Controls, are 20 actionable items you can implement to prevent most attacks. Within the 20 controls, there are 180 sub controls that define further activities.
The 20 high level controls are as follows:

Now that we have selected the frameworks, we need a way to measure maturity. Measuring the maturity of your security program informs how you are progressing.
For the Rekt Casino scenario we are going to utilize the Capability Maturity Model Integration as shown below:

Most organizations strive to reach and maintain level 3. Once you progress past level 3, security and technology related activities start to slow down. In some cases, organization have found levels 4 and 5 as a hinderance and have actually rolled back to become more efficient.
A good way to visualize maturity in a way that business leaders can understand is the following chart based on the current maturity of Rekt Casino:
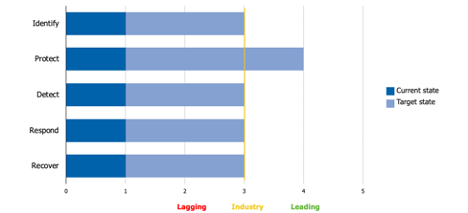
On the left side we have the functions of the NIST CSF, on the bottom we have the 5 maturity levels. The yellow line is there the industry is at from a maturity perspective.
The dark blue represents the current maturity level of Rekt Casino. As you can see, they are very immature from a security perspective. The light blue is the target maturity level Rekt Casino is striving for.
Rekt is striving to achieve the industry standards in all areas except the protect function. They want to invest more in protecting their assets than others in the industry.
This graphic is good to keep socializing with your business leaders. By utilizing a graphic such as this you can also identify areas of under investment and over investment.
This is Part II of a 3-part blog series based on MGT514: Security Strategy, Policy, and Leadership.
Read Part I here. Read Part III here.
Joe Sullivan has over 20 years of experience in information security. Joe is Principal Consultant at Rural Sourcing in Oklahoma City where he manages and develops the security consulting services and the teams that provide them. Over his career Joe has worked in incident response, penetration testing, systems administration, network architecture, forensics, and is a private investigator specializing in computer crime investigations. Joe teaches MGT514: Security Strategic Planning, Policy, and Leadership.


Joe Sullivan has over 20 years of experience in information security and is a senior security consultant for TrustedSec. Joe teaches LDR514: Security Strategic Planning, Policy, and Leadership.
Read more about Joe Sullivan