Like many great inventions, the idea behind F-Response is so simple and elegant it is hard not to punish yourself for not thinking of it. Using the iSCSI protocol to provide read-only mounting of remote devices opens up a wealth of options for those of us working in geographically dispersed environments. I have used it for everything from remote imaging to fast forensic triage to live memory analysis. F-Response is vendor-neutral and tool independent, essentially opening up a network pipe to remote devices and allowing the freedom of using nearly any tool in your kit. The product is so good, I really wouldn't blame them for just sitting back and counting their money. Luckily, counting money gets boring fast, so instead the folks at F-Response have kept innovating and adding value. Their latest additions are new "Connector" tools: Database, Cloud, and Email.
Now is the time to start planning how to acquire forensic copies of all that data your organization is pushing to cloud providers. Hopefully you already have established agreements and processes in place with your top tier providers. But what about all of the cloud providers you allow your employees to use? Those Gmail accounts used by the remote sales team that are now subject to a discovery order or the Amazon S-3 storage your engineering team is building upon? Nearly every law firm I have worked with recently has needed to acquire at least some form of data from a web provider without having the tools to do so. Depending on your circumstances, an F-Response Connector may be just the simple tool you need to get the job done.
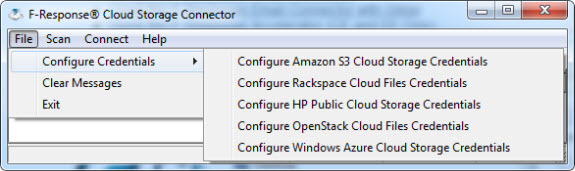
The F-Response Cloud Connector allows remote mounting of Amazon S3, Rackspace Cloud Files, HP Public Cloud, OpenStack Cloud Files, and Windows Azure storage. The Email Connector currently interfaces with Gmail, Yahoo! Email, and any other provider supporting the IMAP protocol, including Microsoft Office 365. Finally, the Database connector appears to be in its infancy, only supporting Microsoft Sharepoint databases at this time. The connectors are all currently included with the purchase of any F-Response product (Tactical through Enterprise Edition). The examples shown here were accomplished using the F-Response Tactical dongle provided in the SANS Forensics 508 course. Since all of the connectors essentially work the same, I'll use this post to demonstrate the Email Connector tool.
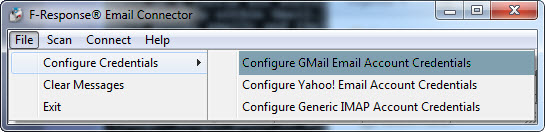
First, we need to configure the account credentials.
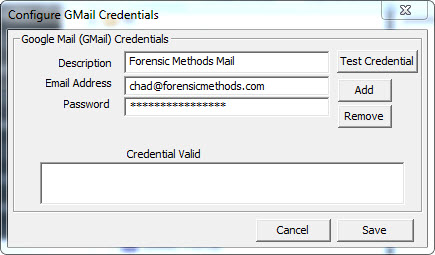
After entering credentials, there is a handy "Test Credential" option. Also, keep in mind that you can input more than one set of credentials, allowing collection from multiple accounts simultaneously. Amazingly, Google two-factor authentication doesn't impede the process; just use the account's "Application Password" instead of login credentials.
Once credentials are in place, use the Scan tab to connect to the account(s), and the remote store will be made available as a locally mounted device (in this example, we see the Google Mail store mounted as "J:"). Behind the scenes, a local cache is created, and we now have read-only access to the remote account data via the J: mount point.
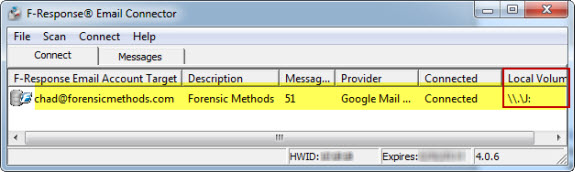
For those of you familiar with the simplicity of the F-Response model, you know what to do from here. If you are new to F-Response, a few use cases are in order.
Triage String Searching
Let's assume I do not really want to review the thousands of messages in a given email store and instead just care about the few that have a specific key word involved. Since I have a direct mount point to the email, I can use built-in tools (or better yet, a script) to perform the search. The "find" command in Windows is surprisingly useful for searching text. Here I did a simple case-insensitive search, and each line containing "gmail" is displayed. Notice how hits are grouped by file (each Gmail message is exported in the .EML format).
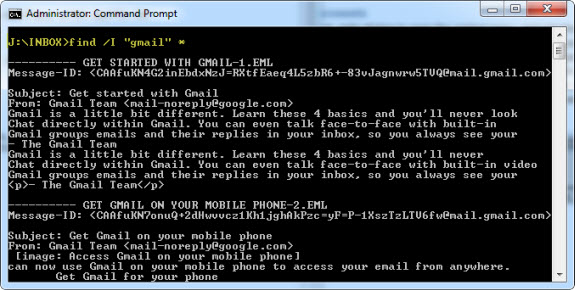
Forensic Acquisition
Now that we have verified that there is relevant data in our email archive, the next logical step might be to create a forensic image of the entire email archive. I employed FTK Imager using the option to acquire the "Contents of a Folder" — in this case everything present under J:\. The result is a logical image (.ad1 format). Looking at the contents of that image shows just how much information the Email Connector collected from Gmail. Sent files, the spam folder, and even data within the account trash folder were acquired.
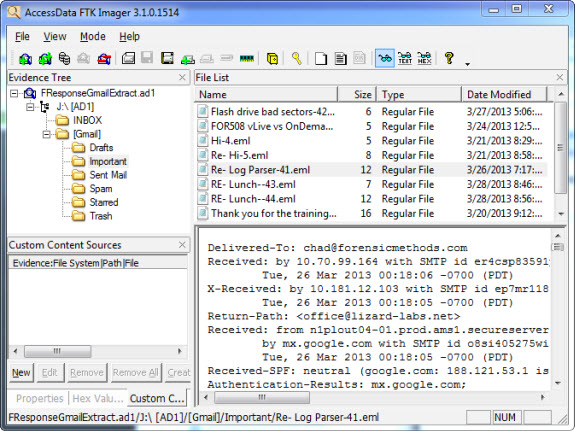
Data Analysis in a Full Forensics Suite
For my final example, I decided to point a commercial forensics suite (Access Data Forensic Toolkit) at the mounted email archive to perform a more complete analysis (my recommended procedure would be to create a forensic image first, and then analyze the image). I was able to index everything for fast searching, use FTK email features to drill down into mail domains (shown here), sort by mail addresses and dates, review email attachments, track replies and mail forwards, etc.
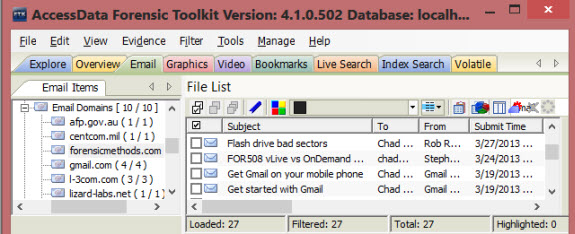
In all of these examples, the F-Response Email Connector did its job providing read-only access to the data and then getting out of the way. Use cases are only limited by your imagination (and available tools). If you have accomplished something interesting with F-Response or the new connectors, let us know in the comments!
Chad Tilbury, GCFA, has spent over twelve years conducting computer crime investigations ranging from hacking to espionage to multi-million dollar fraud cases. He teaches FOR408 Windows Forensics and FOR508 Advanced Computer Forensic Analysis and Incident Response for the SANS Institute. Find him on Twitter @chadtilbury or at http://forensicmethods.com.





