Digital forensic investigators who are not properly trained will alter evidentiary media or will misinterpret important information, potentially damaging a case. Pitfalls that less experienced practitioners encounter when processing Blackberry devices are discussed below with guidance on how to obtain the most useful information from these devices.
We frequently encounter Blackberry devices in digital investigations that are not fully supported by commonly available forensic tools. Fortunately, a significant amount of data can be obtained using Blackberry Desktop Manager, which is freely available from the manufacturer's Web site. In fact, even when forensic tools can acquire data from a Blackberry device, it is still advisable to obtain a logical backup using Blackberry Desktop Manager. By logical backup, we mean that only active items on the device are copied, not deleted data. An IPD file can contain almost any type of data stored on a Blackberry device, including call logs, calendar items, photos, contacts, text messages, e-mails and associated metadata.
There are several reasons for making an IPD backup of a Blackberry device even when a forensic tool can acquire data from the device:
- Nobody knows Blackberry devices better than the manufacturer (RIM), and their software may obtain more data than some forensic tools.
- Data acquired using a forensic tool can be compared with data in an IPD backup to ensure they are consistent.
- The IPD file can facilitate additional analysis such as inspecting data using ABC Amber Blackberry Converter or a Blackberry device simulator.
From a forensic perspective, there are some important considerations when creating an IPD backup file using Blackberry Desktop Manager. By default, Blackberry Desktop is configured to synchronize some data between the device and computer. Failure to disable these synchronization options will alter data on an evidentiary device. At the very least, the date and time on the device will be changed to match the computer clock. This alteration of an evidentiary device can negatively impact a forensic examination, particularly when multiple devices from different time zones are involved. For instance, if the original date and time settings of the device were not documented, it may be difficult to ascertain exactly when specific events occurred.
To prevent Blackberry Desktop Manager from altering an evidentiary device, it is necessary to select the Synchronize item in Blackberry Desktop Manager and disable all options as shown below.
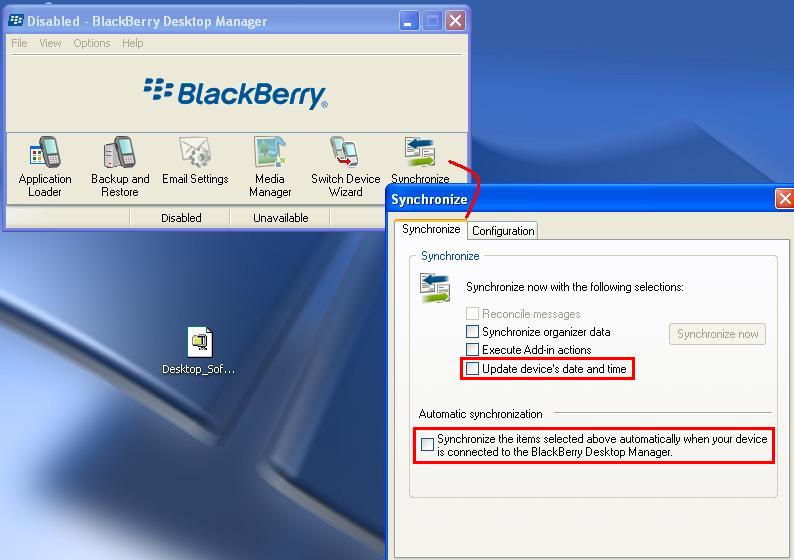
By default, the "Update device's date and time" is selected along with the Automatic synchronization option. Therefore, it is necessary to explicitly deselect these options before attaching an evidentiary item to the acquisition system.
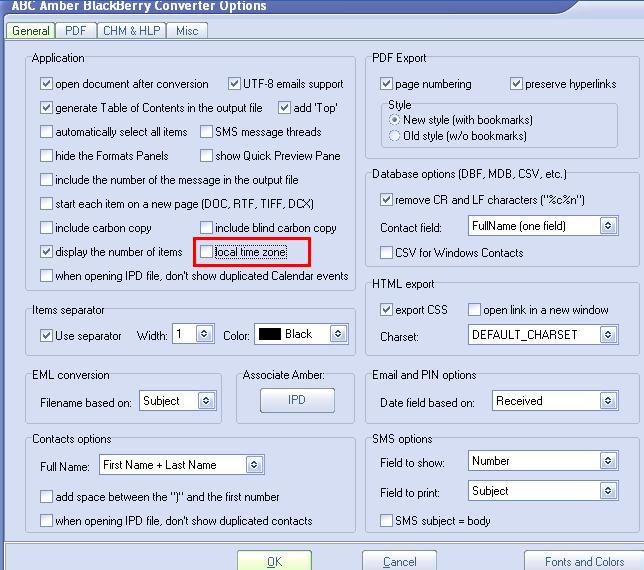
As mentioned above, an effective and inexpensive tool for examining data in an IPD file is ABC Amber Blackberry Converter. However, once again, it is necessary to change the default configuration before using this tool to examine an IPD file for forensic purposes. Specifically, the "local time zone" option must be deselected as shown below to prevent all times in the IPD file from being updated to the time zone of the examination system.
Keep in mind that Blackberry IPD backup files may exist on a user's computer. These backup files are particularly useful when the original Blackberry device is not available or accessible. Even when the original device is available, these backups may contain historical data that are no longer stored on the device.
By default, recent versions of Blackberry Desktop Manager save IPD files in the user's "My Documents" folder with the filename "Backup-(yyyy-mm-dd).ipd" but the user can provide and alternate location and filename. Fortunately, IPD files contain the distinctive line "Inter@ctive Pager Backup/Restore File" in their header. This header signature can be used to perform a comprehensive search of storage media for IPD backups.
To learn more about forensic acquisition and examination of mobile devices, including Blackberry devices, register for SEC563 Mobile Device Forensics.
Eoghan Casey is founding partner of cmdLabs (http://www.cmdlabs.com/) , author of the foundational book Digital Evidence and Computer Crime, and coauthor of Malware Forensics. He has been involved in a wide range of digital investigations, including network intrusions, fraud, violent crimes, identity theft, and on-line criminal activity. He has testified in civil and criminal cases, and has submitted expert reports and prepared trial exhibits for computer forensic and cyber-crime cases.




