In Part 1 of this post, we explored defragmenter usage in Windows XP, specifically trying to gain more information about user activity when we see the following in the Prefetch directory:
Vista made many file system changes, modifying some of the XP artifacts we relied upon in Part 1 and adding some artifacts that can greatly simplify our investigation. Importantly, Vista ships with a default scheduled task for a full volume defragmentation every Wednesday evening at 1am. This is in addition to the limited defrags conducted by the Prefetch / Superfetch components. Thus we should expect to see even more defragmenter activity on a Vista machine. Taking this into consideration, we will perform the same analysis that we did for Windows XP.
We will focus on the two primary methods a user can invoke the Windows Defragmenter tool:
- Running defragmenter from a graphical user interface (GUI)
- Running defrag from the command line using defrag.exe
Defragmenter Artifacts in Vista - Identifying GUI Usage
The Vista GUI defragmenter tool can be accessed in the same way it was in Windows XP (Start Menu -> Accessories -> System Tools ). When performing a Vista analysis we will focus on the following artifacts:
- Prefetch Entries
- UserAssist Registry Key
- File Timestamps
- Event / Scheduler Logs
Prefetch Entries
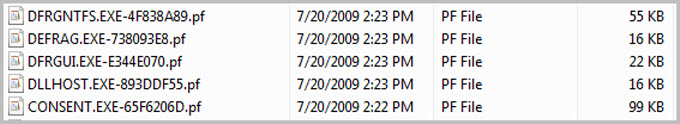
The Prefetch signature generated by the GUI defragmenter is significantly different in Vista. As shown in Figure 2, you should expect to see defrag.exe, dfrgntfs.exe and a new application named dfrgui.exe. The latter is a replacement for the Microsoft Management Console (MMC) snap-in (dfrg.msc) that was used in XP. Additionally, you may find consent.exe executed immediately before the GUI tool. This is part of the Vista User Access Control (UAC) protections.
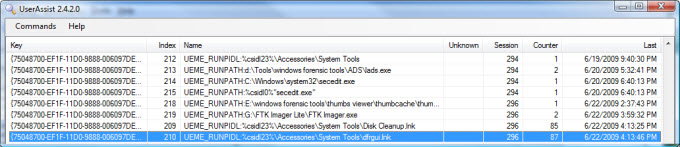
UserAssist Registry Key
Our XP analysis showed that we can use artifacts in the UserAssist key to show manual defragmenter execution by a user account. For Vista, the artifact stored within UserAssist is for the dfrgui.lnk file, which is a shortcut to the dfrgui.exe application. The "Last" time indicates when the application was last run by the user.
File Timestamps
Vista ships by default with access timestamp updating disabled. In systems where this has been enabled by the administrator, access timestamps can be used to identify when an executable was run and corroborate activity witnessed via other artifacts.
One important note regarding Prefetch entries is that in the absence of access timestamps, their modified timestamp can also indicate when the application was last run (due to the execution count being updated within the Prefetch file).
Event / Scheduler Logs
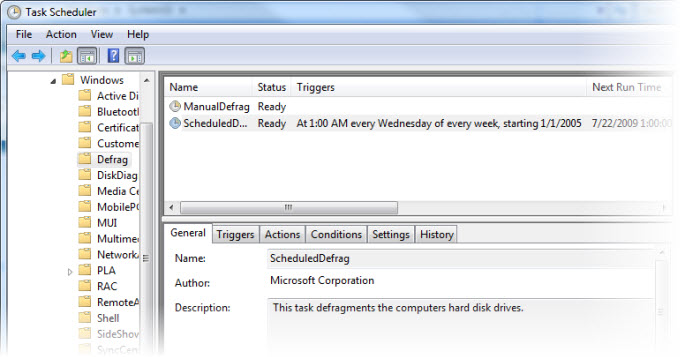
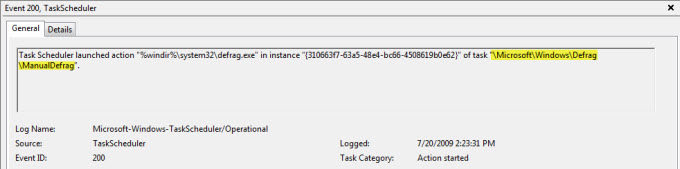
Perhaps the most important change to affect our defragmenter analysis in Vista is that it now includes a mechanism to record defragmenter usage in the event logs. Execution of the defragmenter is tracked for both manual and scheduled executions (see Figure 4). This is part of the greatly expanded event logging accomplished by Vista. Logging is on by default and can be reviewed either through the Task Scheduler "History" tab, or in the Application and Services Logs/Microsoft/Windows/Task Scheduler event log. Figure 5 shows a log entry for a manual defrag task that was started by Vista. The event logs provide enough granularity to identify when the defrag was scheduled, started, completed, and/or terminated before completion. One limitation is that the defrag process is run as user SYSTEM, and thus user attribution is not possible using this artifact. However, it can be easily coupled with the UserAssist information covered previously to identify the user. Unfortunately, command line and Prefetch/Superfetch (limited) defrag executions are not recorded in the event logs.
Defragmenter Artifacts in Vista - Identifying Command Line Usage
While we gained some additional artifacts in Vista for tracking GUI usage, we received no additional artifacts to track command line usage of the defragmenter tool. Additionally, with access timestamps disabled by default, our timelines will be missing critical information making it more difficult to identify malicious use of the defragmenter.
As the steps are identical to those of XP, the reader is directed back to Part 1 for the discussion of artifacts generated by command line usage of the tool.
Conclusion
The expanded event logging within Vista provides an excellent means for examiners to identify manual versus scheduled executions of the defragmenter tool. However, we will still need to use multiple artifacts to prove user attribution. While identifying command line execution did not get any easier in Vista, it is still by no means a lost cause. Good timeline analysis can often go a long way towards identifying user actions and intent.
Chad Tilbury, GCFA, has spent over ten years conducting computer crime investigations ranging from hacking to espionage to multi-million dollar fraud cases. He teaches FOR408 Windows Forensics and FOR508 Advanced Computer Forensic Analysis and Incident Response for the SANS Institute. Find him on Twitter @chadtilbury or at http://ForensicMethods.com.





