SEC595: Applied Data Science and AI/Machine Learning for Cybersecurity Professionals


Experience SANS training through course previews.
Learn MoreLet us help.
Contact usBecome a member for instant access to our free resources.
Sign UpWe're here to help.
Contact UsICS security managers don't get to choose if they're a target of a cyber attack, but do get to choose many things about their OT security program.


Relying on control systems and critical infrastructure is commonplace. Flipping on a light switch at home or the office, pumping gas into your vehicle at a gas station, pouring water from a tap— we rely on industrial control and critical infrastructure systems to support all these things and ultimately our modern way of living. We rely on some of these critical systems to generate and distribute power and heat to our homes, businesses, and healthcare centers. In the fuel manufacturing industry, there’s a reliance on the production and refining of oil & gas. For critical city and town services for our homes there’s a reliance on the management of our water systems, etc.
This interconnected and interdependent complex mix of both legacy and modern computer systems and engineering systems is responsible for processes in the physical world. They require additional considerations when it comes to security. For the teams managing and tactically defending this control system infrastructure, the skills and knowledge of safety, engineering, control system deployments, and more, is required beyond the tried true and tested security skills applied to protect traditional Information Technology (IT) systems.
Industrial Control Systems (ICS) were not always as connected, highly automated, or complex as they are today. ICSs had been designed, built, tested, and deployed for a particular purpose and ran on proprietary protocols in isolation. These systems were engineered and operated in a completely isolated network away from other networks, including those in the outside world such as IT business networks and the public Internet.
Over the years of advancements in modern network technology and equipment, as businesses sought cost savings benefits, control systems have shifted away from an isolated control environment toward a more connected environment. Of course, more external connections ultimately broke the isolated, or "air-gapped," model, making ICSs less isolated and therefore more exposed to cyber risk.
This shift changed the risk surfaces and the threat landscape. We’ve seen increased threats including ransomware and tailored ICS-specific attacks against engineering control systems. As such the shift has also changed the security job tasks, security roles, and knowledge required to now perform ICS security for the protection of these engineering processes in today’s threat landscape.
We do not get to choose if we are a target of a cyber-attack. However, as ICS/OT security managers and tactical cyber defenders in ICS/OT, we get to choose many things about our control system security program. This includes but is not limited to how we conduct ICS incident response, how we prioritize safety, which tools will be available to assist our tactical teams, where best to deploy control system network visibility. And of course, we get to choose who will be on our teams defending our critical infrastructure. We have some much opportunity for ICS defense! Whether working in a converged IT/ICS or specific ICS security team, it is imperative those selected as ICS/OT security defenders be trained with the ICS-specific knowledge and have the many ingredients needed for protecting control systems.
Securing Data vs. Enabling and Securing Physics: Traditional IT security focuses on digital data at rest or data in transit and the pillars of C.I.A. (Confidentiality, Integrity, and Availability). Operating technology/industrial control systems (OT/ICS) manage, monitor, and control real-time engineering systems for physical input values and control output for physical actions in the real world. The main priority in OT/ICS is safety and reliability of operations.
Modern trained ICS cyber security staff understand the nuances between traditional IT and ICS security, the ICS mission, safety, the engineering process, ICS protocols and active defense strategies that excel inside control environments, impacts of incidents in ICS to equipment, the environment, and people. A recipe to help us obtaining, training and retaining the top ICS security defenders include these ingredients:
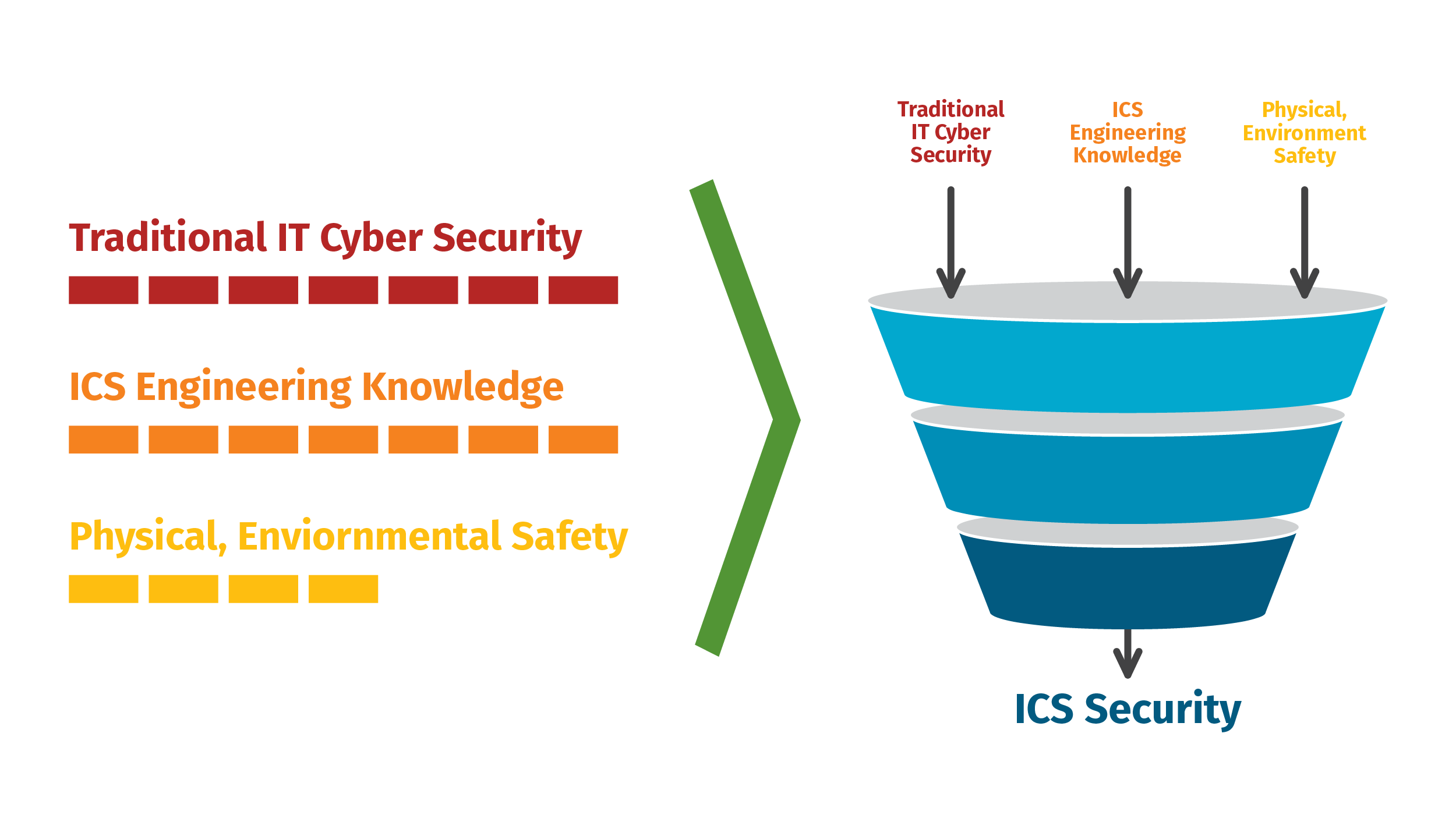
Technology and Processes (even if automated) do not get us far in the defense space without a trained and focused workforce. Human defenders—the people (workforce)—are the ones who use the ICS security technologies, work with the engineering, safety, business, IT department, and other teams and understand the ICS mission, possible impacts and recovery. These people understand the industrial process, protocols, normal vs. abnormal for engineering operations network traffic patterns, safety with context, the commonly targeted assets in control systems, etc.
If you're lucky, you'll...
You know you've succeeded in building an effective ICS security team when:
Safety could be at risk if information or traditional business systems are prioritized over industrial engineering control systems. Or, if the responsible reporting structure for ICS/OT security fails to fully embrace the differences between IT and OT/ICS.
Consider, for instance, a security incident on the IT business email system, and a security incident on the SCADA (Supervisory control and data acquisition) system of a power grid occurred simultaneously. Which incident gets the priority to focus efforts, tools, and team members to investigate, respond, and defend? What pace and rigor will the organization give to the incident selected as a primary focus. More specifically, what drives the decision to manage these very different risks, and related impacts, in these different environments?
Did the organization select their focus based on what was the most important for the safety of the people, the environment, and the organization overall? Today’s ICS incident response teams must understand the control system processes, the engineering, industrial protocols, safety factors, and ICS-specific cyber threats and tailor incident response playbooks, and risk management strategics accordingly.

The ICS418: ICS Security Essentials for Managers course empowers leaders responsible for securing critical infrastructure and operational technology environments. The course addresses the need for dedicated ICS security programs, the teams that run them, and the skills required to map industrial cyber risk to business objectives to prioritize safety. The course speaks to the needs of the full range of managers, including:
Those familiar with the Cyber42 cybersecurity leadership simulation game may have learned about it when taking SANS Cybersecurity Leadership courses. SANS has extended this awesome tool for ICS418 by introducing Cyber42: Industrial Edition, which borrows many features from the original Cyber42 game. The scenarios are specific to industrial control systems and, of course, safety is added to the mix of industrial cyber incidents. In Industrial Cyber42, the object of the game is to finish with the highest safety culture.
For deeper insights about building robust ICS/OT cyber defense teams, securing your critical infrastructure, and fostering an organization-wide culture of safety, download the SANS Strategy Guide: ICS is the Business.


Dean Parsons, CEO of ICS Defense Force, teaches ICS515 and co-authors ICS418, emphasizing ICS-specific detection, incident response, and security programs that support OT operations—aligning practitioners and leaders on clear, defensible action.
Read more about Dean Parsons