Last year I covered the free Encrypted Disk Detector (EDD) tool and challenged the community to help crowdsource its development [link]. Thank you to all that took part in the experiment. Magnet Forensics announced today that Encrypted Disk Detector version 2 is available [get it here].
Survey Results
In addition to encouraging additional development of EDD, a side benefit of the project was to get an idea of the most popular disk encryption products being deployed. Figure 1 provides the survey results, with Checkpoint Full Disk Encryption, Symantec Endpoint Encryption, and Sophos (formerly Utimaco) Safeguard rounding out the top three. I think many of us could have guessed that big players like Symantec and Sophos would be near the top, but I was surprised to see products like BestCrypt and SecureDoc pull ahead of Credant Technologies (now owned by Dell).
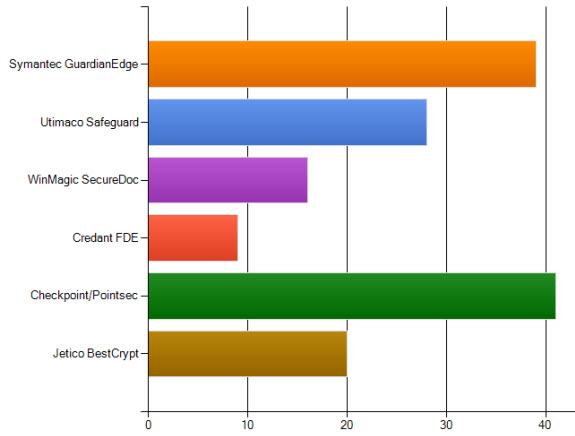
Figure 1: EDD Survey Results
EDD Version 2
The EDD team took the feedback and implemented support for the top four survey results:
- Checkpoint
- GuardianEdge
- SafeGuard
- BestCrypt
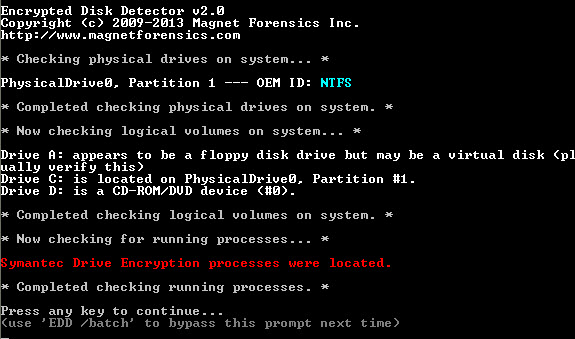
Recall that the previous version of EDD identified full-disk and volume based encryption from Truecrypt, Bitlocker, and PGP. Interestingly, the newest additions do not have accessible disk signatures like the previous set. Thus EDD v2 now augments disk signature identification with process detection, which searches for running processes indicative of disk encryption products.
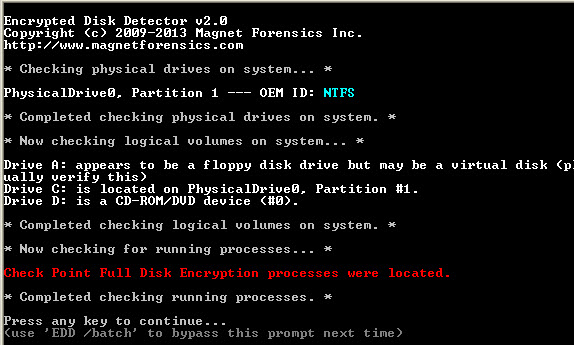
In addition to taking the survey, many respondents volunteered to be beta testers. Their help testing the update in real world environments was invaluable. Thank you! The following are a few screenshots from the final testing run:
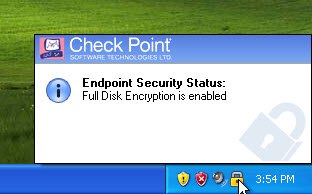
Checkpoint Full Disk Encryption Detection
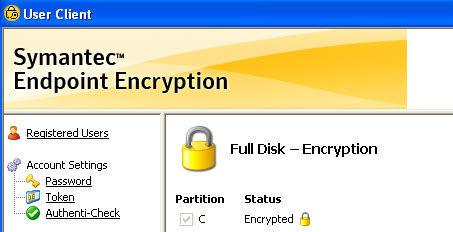
Symantec Endpoint Encryption
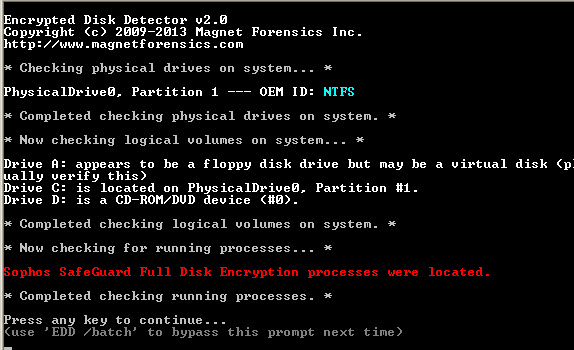
Sophos Safeguard
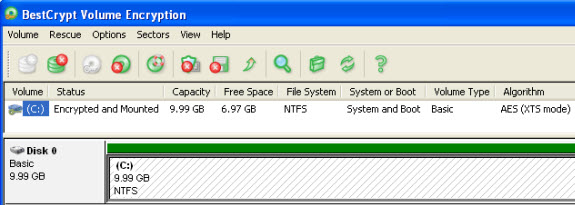
Jetico Bestcrypt
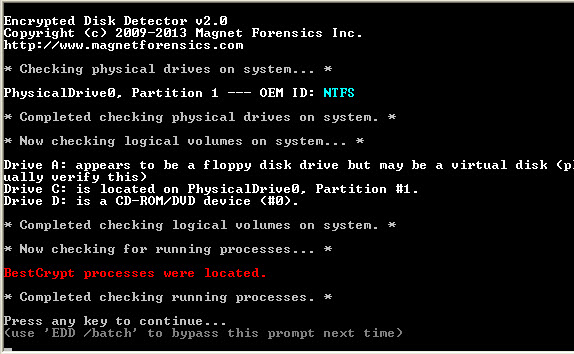
The Future
In a zetabyte world, digital forensic triage becomes more important as our traditional "image everything" processes don't scale. Identifying encryption should be a critical step in live triage. With the current penetration of disk encryption products, we no longer have the luxury of assuming they don't exist, and our best opportunities for circumventing them exist while the system is running. Jad Saliba and his team were early proponents of triage and one of the first to release an encryption detection tool. Even with the latest updates, EDD does not purport to identify the universe of encryption products. However, it is an excellent start, and, with the v2 update, it now identifies the most popular products on the market. I am a big believer in the phrase "perfect is the enemy of good" and I would rather have a tool that can get me most of the information I need today rather than wait indefinitely for a "perfect" detection product. Hopefully this update to EDD will inspire additional innovation in this area. As mentioned by one survey respondent, the encryption detector of the future may need to go even further and detect device drivers and hooks to reduce false negatives. In the meantime, please thank the Magnet Forensics team next time you see them for this great update to EDD!
Chad Tilbury, GCFA, has spent over twelve years conducting computer crime investigations ranging from hacking to espionage to multi-million dollar fraud cases. He teaches FOR408 Windows Forensics and FOR508 Advanced Computer Forensic Analysis and Incident Response for the SANS Institute. Find him on Twitter @chadtilbury or at http://forensicmethods.com.




