SEC595: Applied Data Science and AI/Machine Learning for Cybersecurity Professionals


Experience SANS training through course previews.
Learn MoreLet us help.
Contact usBecome a member for instant access to our free resources.
Sign UpWe're here to help.
Contact UsFOR589: Cybercrime Intelligence authors share the top cybercriminal evolutions to focus on after examining CrowdStrike's 2023 Threat Hunting Report

On 8 August 2023, cybersecurity vendor CrowdStrike released their annual Threat Hunting Report. It shared the trending tactics, techniques, and procedures (TTPs) leveraged by adversaries against victim organizations observed by the CrowdStrike Threat Hunting team in the last 12 months. The report shared multiple new insights into the current cybercriminal threat landscape.
Key Findings:
Cybercriminals have gotten faster at intrusions: In 2023, the average amount of breakout time – how long it takes to go from initial access to lateral movement – for cybercriminals is 79 minutes, a five-minute drop from 2022. Plus, breakout time for cybercriminals has been as fast as seven minutes.
Intrusions have gotten easier for cybercriminals: 2023 saw a 312% increase in the usage of legitimate remote monitoring and management (RMM) tools and close to 14% of all intrusions saw an RMM tool deployed. These are free or open-source tools that can be used to efficiently evade detection and blend in with common software in the target environment.
Cybercriminals increasingly outsource the first phase of intrusions: CrowdStrike Intelligence tracked initial access broker (IAB) advertisements across the cybercriminal underground and found a 147% increase compared to 2022, highlighting the rising demand for this type of work and the need to monitor these activities for early warning detection.
When compared to state-sponsored adversaries, cybercriminals pose a much broader and omnipresent threat to any type of organization, no matter the size, due to the opportunistic nature of their targeting (see Figure 1). CrowdStrike observed that the most prominent threats include ransomware, data theft extortion, as well as the initial access brokers (IABs) that enable them.
Both the financial and technology sectors are two of the most targeted by cybercriminals. This is because these sectors are the most likely to pay a ransom or possess valuable data to steal and sell to others.

In the last 12 months, there has been rampant usage of legitimate remote monitoring and management (RMM) tools, such as AnyDesk and TeamViewer, by cybercriminals. RMM tools are attractive programs for threat actors because they offer ease of use and lack of effort required, when compared to developing their own custom tooling and malware.
While designed to make an IT admin’s job easier, RMM tools have been increasingly leveraged by cybercriminals to avoid detection for protracted periods of time. RMM software are also self-contained, portable executables, that can bypass both administrative privilege requirements and software management control policies. This enables cybercriminals to maintain privileged and persistent access to sensitive data and support the delivery of ransomware payloads.
CrowdStrike highlighted that the most common RMM tool used by adversaries, by far, was AnyDesk and in up to 73% of intrusions where AnyDesk was deployed it was attributed to cybercriminal activity. Another interesting finding was that multiple RMM tools are frequently observed in a single intrusion by a cybercriminal. Common methods to deliver RMM tools by cybercriminals involves command-line ingress procedures including curl, wget or PowerShell, and if an active remote desktop protocol (RDP) session has been established, they can use standard web browsers or RDP clipboard redirection.
The most common RMM tools observed by CrowdStrike in the last 12 months include: AnyDesk, ConnectWise ScreenConnect, Atera Agent, TeamViewer, RemoteDesktopPlus, RustDesk, Splashtop, Fleetdeck, TightVNC, and N-Able. CrowdStrike recommended that if these RMMs tools are not already in use in an organization’s environment, their unexpected delivery and installation should be treated as a potential indicator of attack (IOA).
In January 2023, the US Cybersecurity and Infrastructure Security Agency (CISA) shared an advisory on protecting against the malicious use of RMM tools. In October 2022, CISA observed a widespread phishing campaign spreading AnyDesk and ScreenConnect, which cybercriminals were using in refund scams to steal money from victim bank accounts.
In December 2022, CrowdStrike reported on the financially motivated and English-speaking threat group dubbed Scattered Spider, who are known for their unique style of attacks. The initial part of their intrusions can involve SMS phishing, social engineering targets over the phone, multi-factor authentication (MFA) fatigue attacks, and SIM swapping. These operators then often deploy multiple RMM tools from a list of up to 20 RMM tools to the victim’s system. The reason for this is because if one is blocked, then the adversary will rapidly deploy another to regain control. In July 2023, the Canadian Centre for Cybersecurity (CCCS) also reported on a suspected Scattered Spider campaign, this time deploying BlackCat (ALPHV) ransomware, marking a significant shift in the adversary’s TTPs.
Initial Access Brokers (IABs) are an expanding and core part of the cybercrime economy. These types of threat actors make a living compromising vulnerable systems and selling that access to others, enabling a myriad of activities. CrowdStrike Intelligence observed that many IABs have established relationships with big game hunting ransomware operations and individual affiliates that use Ransomware-as-a-Service (RaaS) programs.
There are several ways to decide the value of the access offered. Prices fluctuate considerably among sectors, countries, and per IAB. The most valuable and coveted types of access, which include a higher price on offer, are footholds with elevated privileges to large corporations with significant annual revenues.
Interestingly, IABs appear to exhibit similar characteristics and operational commonalities to state-sponsored adversaries. This is because IABs will attempt to gain initial access through exploiting internet-facing systems or stolen credentials and will remain hidden until follow-up actions begin.
Ultimately, IAB sales are available to the highest bidder. This enables a variety of types of cybercrime and has a notable impact on the ecosystem. IABs also lower the barrier to entry for other threat actors starting new intrusions and allow other cybercriminals, such as ransomware operators, to focus efforts on their main objectives more efficiently.
As the IAB work has become increasingly popular among cybercriminals on the underground, some threat actors are beginning to innovate with their own IAB single-vendor shops on the darknet. In June 2023, the SANS FOR589 authors identified a new IAB threat actor had emerged called “Br0k3r” on multiple forums. This new IAB has a neutral reputation among the underground community but appears to be credible.
It is important to note that there are several factors to consider when assessing the credibility of a threat actor offering access to a compromised system. This includes checking the public reputation score of the members on their forum profile. Many forums have systems that allow members to rate each other, based on their interactions. Another way is to look at the member's post history and see if they have a history of successful transactions and engagement with other members. Some cybercrime forums also have an arbitration or escrow system. These are designed to ensure that fair deals can take place and consequences are dealt for failed transactions, which provides additional protection for members. If the cybercriminal offering access or a service is willing to use an escrow system, they are likely to be more credible.
The threat actor uses TOX (aka qTox) and XMPP (aka Jabber) for encrypted communications with other members on cybercriminal forums. It is also possible to track the posts by “Br0k3r” via their identifiers as they use them across multiple forums:
TOX ID | B761680E23F2EBB5F6887D315EBD05B2D7C365731E093B49ADB059C3DCCAA30C30D8E65B0D58 |
Jabber ID | br0k3r[@]xmpp[.]jp |
It is possible to tell if an identifier is a TOX ID as they are always a random string of 76 hexadecimal characters. Jabber IDs are also quick to identify as they look like email addresses, but the domain belongs to a Jabber server, rather than domain with a Mail Exchange (MX) server.
https://images.contentstack.io/v3/assets/blt36c2e63521272fdc/blt78012108b3683e14/64ef525a7ea5c53fd1a07af7/Br0k3r_Exploit.pngIn Br0k3r’s case and at the time of investigating the threat actor, they have a neutral score because they are new. Br0k3r is using a paid account and has deposited funds into the forum’s escrow system. The threat actor also takes a professional approach, using a custom self-made Tor website and setting up TOX and Jabber encrypted communications channels, which are preferred by members of top-tier forums. These factors point to signs that they are likely credible but are trying hard to build their new account’s reputation as their operation is just starting out.
Br0k3r has taken a new approach to the IAB business model by using a single vendor Tor-hosted site to advertise their accesses across multiple forums. This Tor site includes instructions for inquiries and how to purchase access. According to Br0k3r, every access sale includes Windows domain administrator (DA) credentials, active directory (AD) user credentials and password hashes, DNS zones and objects, as well as Windows domain trusts.
The site and system developed by Br0k3r is reportedly operated by Br0k3r himself and is not connected to other threat actors. This is by design, so that Br0k3r can build trust with their cybercriminal clientele. It is a one-to-many service and not a market. In the future, however, an initial access market of this nature may appear following the success of Br0k3r’s Shop.
https://images.contentstack.io/v3/assets/blt36c2e63521272fdc/blt4f8e637bd524a7b0/64ef529bbb33f7514eb5b5ae/Br0k3r_Shop_v1.pngAround 1 August 2023, Br0k3r decided to update the Tor Shop with a new design. Additional information and details were shared on the pages of this new version of the site.
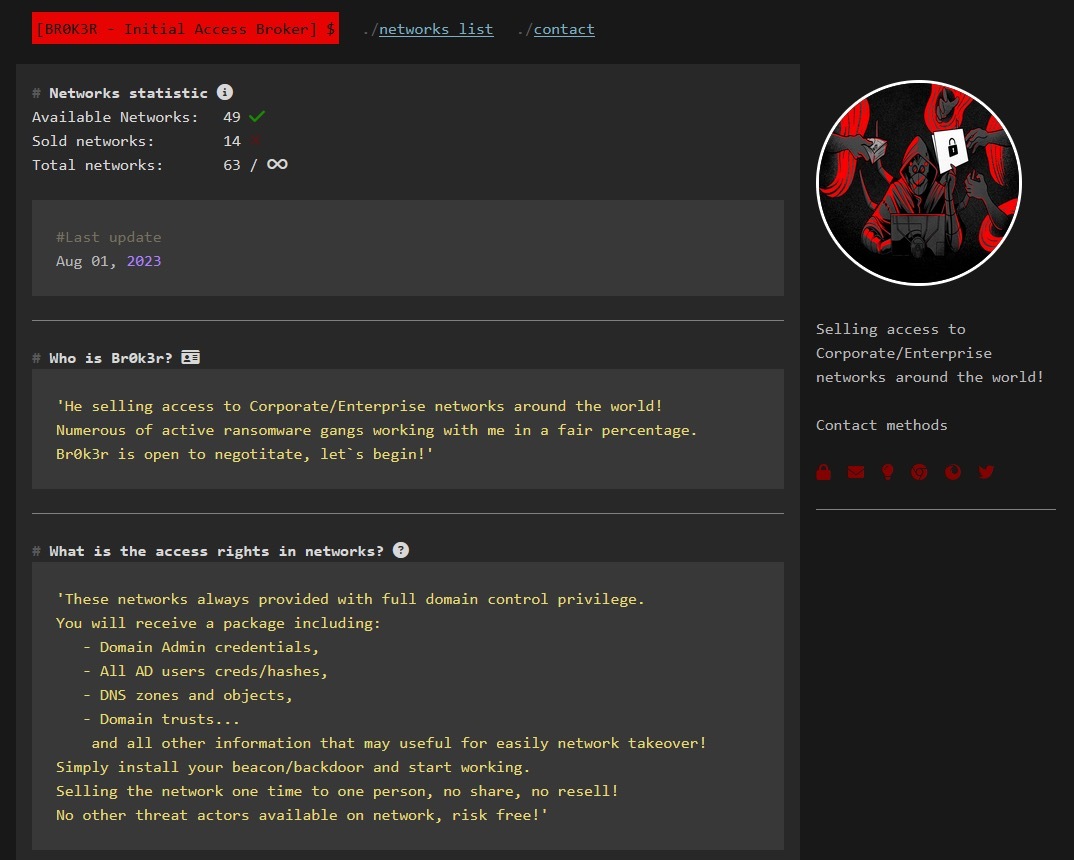
Br0k3r now states on the website that “numerous of active ransomware gangs working with me in a fair percentage [sic].” This highlights how Br0k3r exemplifies that the relationship between ransomware operators and initial access brokers (IABs) is one of mutual benefit. Br0k3r's Shop allows ransomware operators to focus on lateral movement, data theft, ransomware payload deployment, and extortion, rather than spending time on the time-consuming work of achieving network access. The ransomware operators also provide a constant revenue stream for Br0k3r. The cost for access is negligible compared with the ransom that is demanded of the victims, which has caused the number of offers to sell access to compromise organizations to explode.
Further, the Frequently Asked Questions (FAQs) section of the site also includes other details, such as base price of access being 0.5 BTC (worth around 13,000 USD as of August 2023). This is a considerably higher amount than most offerings on cybercriminal forums, but Br0k3r appears to be open for negotiations.
Threat actors who decide to buy access from Br0k3r Shop are also given a preview of the network they are purchasing. This includes the victim’s domain(s) and a summary of the victim organization from ZoomInfo. To prove the access is legit, Br0k3r also offers to provide proof of Domain Admin privileges, enterprise access level, size of the network, and which antivirus or endpoint detection and response (EDR) system is in use. Once the potential buyer confirms they have a wallet with available funds, the deal is then made.
In the last 12 months, the speed and ease of cybercriminal intrusions have increased considerably. This is a reminder that organizations should be monitoring the amount of time it takes them to detect, stop, and remediate attacks as adversaries are only getting faster and launching more efficient attacks.
RMM tools are a key driver in making attacks more time efficient. Cybercriminals no longer need to spend time developing malware that enables remote control over victim devices, when freely available tools online can do it for them that blend seamlessly into legitimate traffic and events. This enables them to shift their resources and time into launching more attacks.
It is recommended by CrowdStrike and the SANS FOR589: Cybercrime Intelligence course authors that organizations should take inventory and review what RMM tools are currently being used inside the environment and begin to monitor for signs of suspicious activities. This includes the installation of an RMM tool not used anywhere else in the organization. That could be a sign that a threat actor has gained initial access and is performing ingress tool transfer (T1105). Threat hunting for this type of behavior is key to preventing these types of attacks.
Mitigating the threat of initial access brokers requires a multi-pronged approach. Ransomware threat actors typically ingress one of several ways. This includes via credentials stolen through infostealer malware, brute-forcing external systems with the remote desktop port (RDP) open, exploitation of public-facing vulnerable servers, as well as traditional malicious spam (malspam) that leads to malware loaders and follow-up payloads, such as Cobalt Strike or, more recently, Brute Ratel C4.
In the SANS FOR589: Cybercrime Intelligence course, however, we will show students the process of how to intercept IAB sales by monitoring posts to underground forums and attributing the victim offered by the attacker. Due to IABs often describing their targets in forum adverts to attract customers, it is possible for cybercrime intelligence analysts to figure out who that target is. Once it is known who the target is, then it is possible to warn the victim of an impending ransomware attack – if contact can be made in time. On the other hand, knowing who is most likely to be the next ransomware victim in advance can help organizations reduce the potential impact of a severe third-party supply chain breach. Plus, from a strategic intelligence perspective, understanding the current trends in ransomware targeting can provide advanced warning and assist in preparing to combat this threat.



Will has revolutionized cyber threat intelligence by co-founding Curated Intelligence and exposing ransomware operations like Black Basta. His expertise in infiltrating dark web communities has advanced how we dismantle cybercriminal networks.
Read more about Will Thomas