If you have been keeping your forensic toolkit up to date, you have undoubtedly used Registry Explorer, a game-changing tool for performing Windows registry analysis. RECmd is the command line component of Registry Explorer and opens up a remarkable capability to script and automate registry data collection. My interest in this tool was recently sparked when I noticed new example batch processing files available on the RECmd GitHub page. RECmd has the capability to ingest .reb files which enable bulk collection and organization of registry artifacts. As an example, the tool author provides this sample file:
Description: Sample RECmd batch file of a whole lot of stuff Author: Eric Zimmerman Version: 1 Id: ab13eb5f-31db-5cdc-83df-88ec12dc1a Keys: Description: Typed URLs HiveType: NTUSER Category: Browser history KeyPath: Software\Microsoft\Internet Explorer\TypedURLs Recursive: false Comment: A comment about Typed URLs Description: WordWheelQuery HiveType: NTUSER Category: User searches KeyPath: Software\Microsoft\Windows\CurrentVersion\Explorer\WordWheelQuery Recursive: true Comment: Dear lawyer, this is what a bad guy searched for <snip></snip>
Troy Larson submitted one of the more intriguing RECmd batch files to Github. "RegistryASEPs.reb" holds an enormous collection of auto-start extensibility points (ASEPs), a fancy Microsoft term for locations that can grant persistence to malicious code. At last update, this batch file collects data from nearly 500 registry keys and 400 registry values. While this sounds like a crazy number of locations to audit, keep in mind that even auditing one the most common persistence mechanisms, registry "CurrentVersion\Run" keys, requires collection from over twenty Windows, WindowsNT, Wow6432, and Terminal Server keys in both the SOFTWARE and NTUSER registry hives.
Running the RegistryASEPs script against multiple registry hives takes less than sixty seconds, and results in CSV output, ready for analysis.
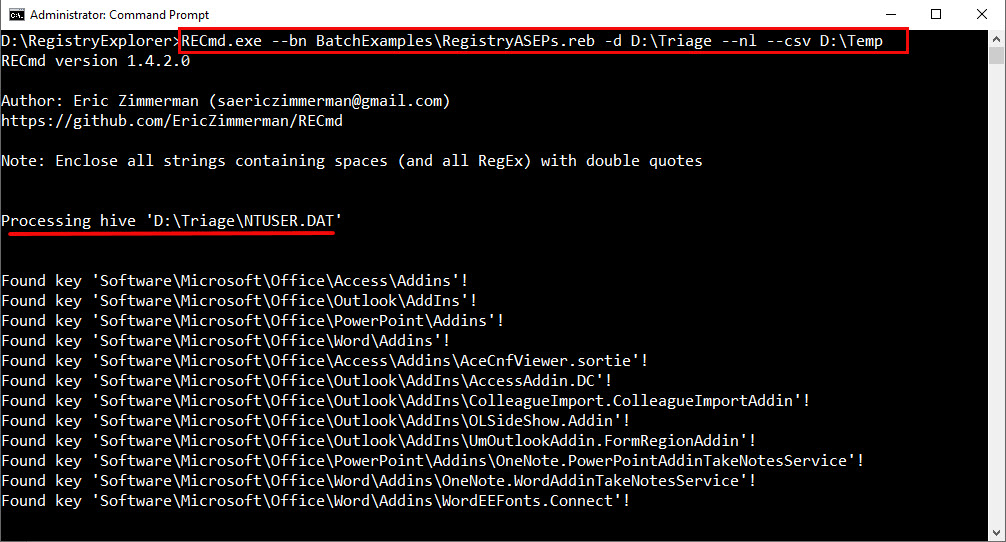
Output will be voluminous, providing deep insight as to just how many different persistence locations exist in Windows. At first glance, the amount of data seems insurmountable. Persistence mechanisms in Windows can seem like a bottomless abyss. However, this kind of data set should be approached through the lens of threat hunting. Creative filtering of the output allows anomalies to bubble to the surface. Some examples (using Timeline Explorer to view/filter):
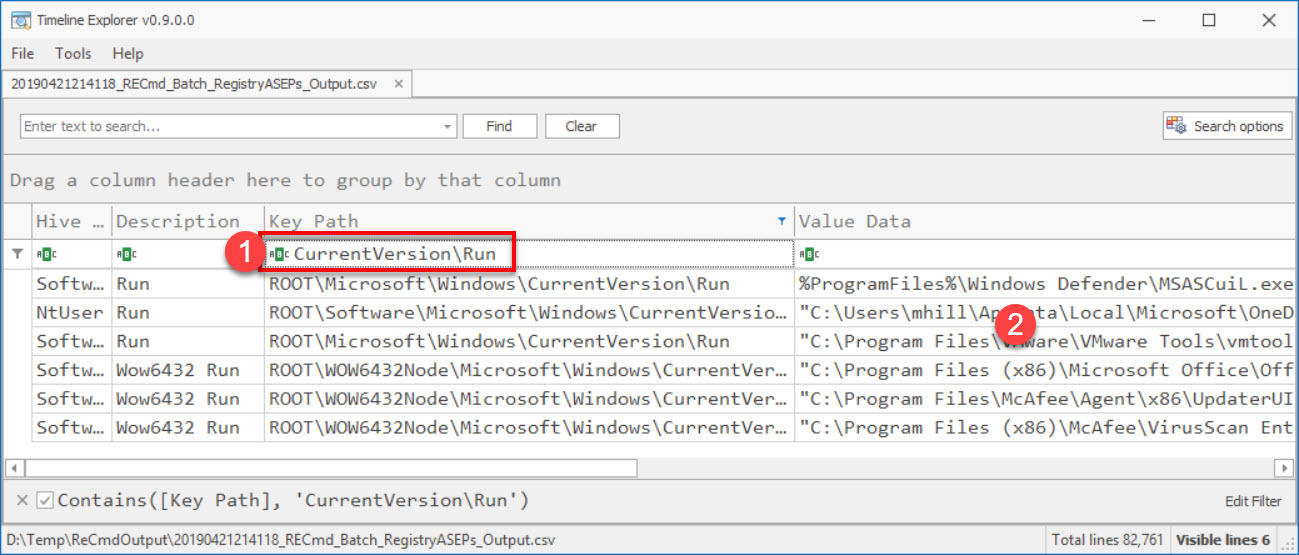
- Zoom in on a specific persistence mechanism (CurrentVersion\Run keys
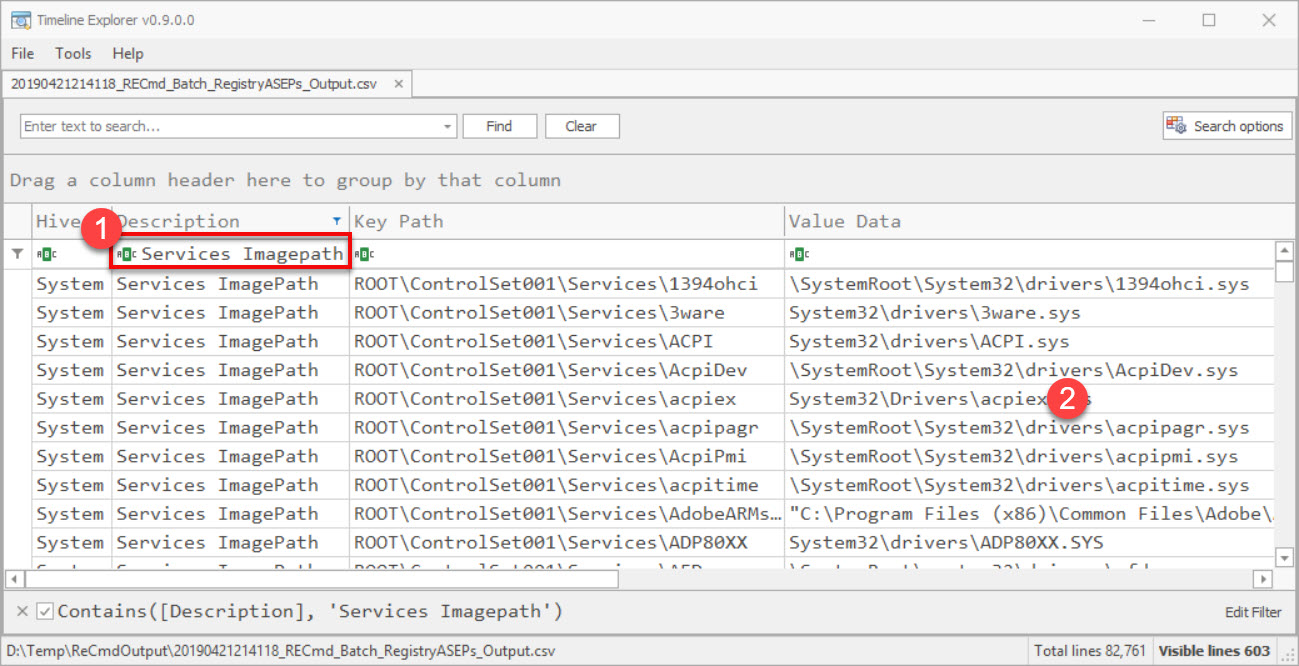
Look for Windows services with suspicious image paths
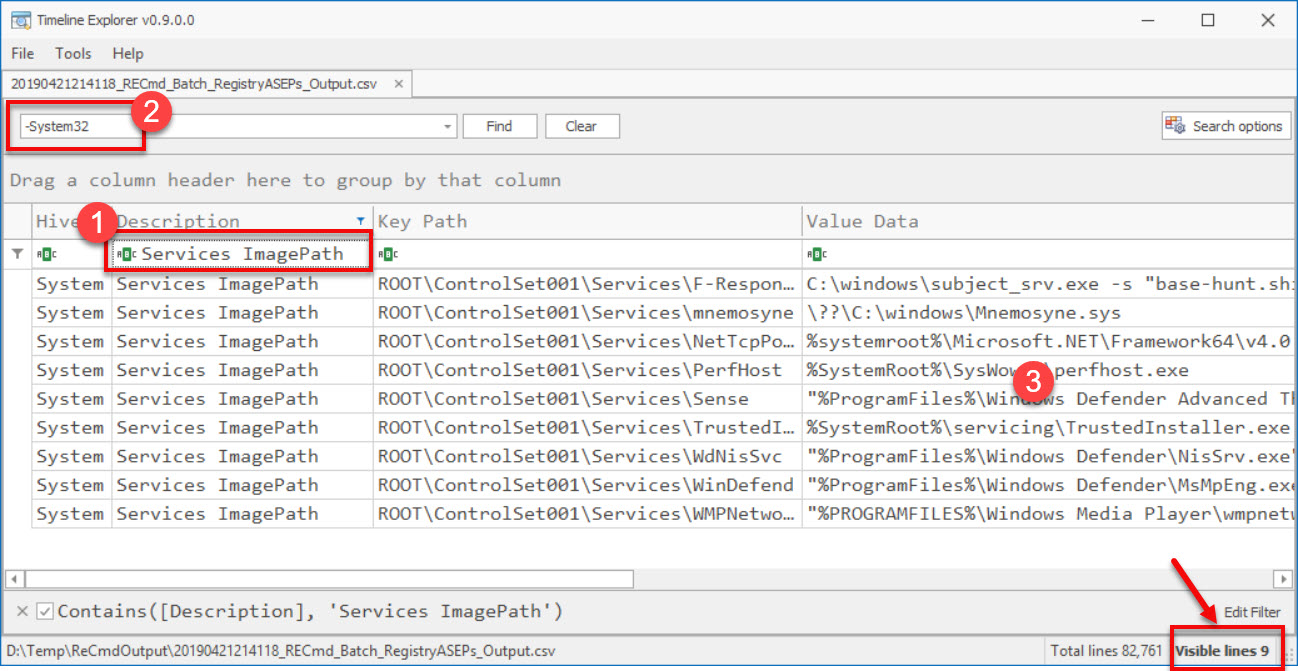
- Perform further data reduction by looking for service image paths not in the System32 folder
Sort by registry LastWrite times to focus on a specific time period of attacker activity
RECmd Strengths for Persistence Auditing
- RECmd is shockingly fast, allowing registry parsing to easily scale to hundreds of registry hives. The batch files are in YAML format and are trivial to create or modify.
- If a Registry Explorer plugin exists for a key, it will be automatically used to parse and export the data appropriately (there are plugins for the most common keys analysts review).
- More complete ASEP auditing could be accomplished using RECmd in conjunction with KAPE to also collect non-registry based ASEPs, including automated registry collection using your .reb batch file of choice.
- This solution works against any collection of Registry hives — full disk images are not required.
- RECmd includes registry forensic "upgrades" like repair of dirty hives and inclusion of deleted registry keys and slack space, of which few other tools take advantage.
RECmd Weaknesses for Persistence Auditing
- The Sysinternals Autoruns tool has a superior output format to RECmd for this use case. Autoruns nicely normalizes data from disparate data sources, bringing important information to the forefront.
- You may find the sample ASEP batch file provides far more data sources than you care about. More targeted collection files have also been submitted, but my recommendation is to start with the most comprehensive and pare it down to those ASEP categories in which are interested. A starting point could be auditing items tracked on the Mitre ATT&CK page on common persistence techniques.
- This solution is not as fully featured as the Sysinternals Autoruns tool, which also provides file hashes and digital signature verification (though to be fair, the offline version of Autoruns verifies only a small subset of digital signatures).
Conclusion
RECmd is a revolutionary tool for automating Windows registry parsing, as demonstrated via this use case of auditing for malware persistence. It can do much more, so hopefully this inspires you to give it a test drive (and submit your own .reb files). RECmd in conjunction with Troy Larson's sample collection script is a good alternative to the SysInternals Autoruns tool, but the output requires a lot of filtering to be useful for the average investigator. Tight filtering, data reduction, and threat intelligence make the use case more feasible, especially at scale. Happy hunting!
Chad Tilbury, GCFA, has spent over twenty years conducting computer crime investigations ranging from hacking to espionage to multi-million dollar fraud cases. He is a senior instructor and co-author of FOR500 Windows Forensic Analysis and FOR508 Advanced Incident Response, Threat Hunting, and Digital Forensics at the SANS Institute. Find him on Twitter @chadtilbury.





