SEC595: Applied Data Science and AI/Machine Learning for Cybersecurity Professionals


Experience SANS training through course previews.
Learn MoreLet us help.
Contact usBecome a member for instant access to our free resources.
Sign UpWe're here to help.
Contact UsThere are many utilities for acquiring drive images. I maintained my snobbish attachment to plain old dd for a long time, until I finally got tired of restarting acquisitions, forgetting checksums, and making countless other errors. The truth is: there are plenty of good tools that provide a high level of automation and assurance. The rest of this article will walk the reader through the process of taking a drive image using AccessData's FTK Imager tool.
FTK Imager is a Windows acquisition tool included in various forensics toolkits, such as Helix and the SANS SIFT Workstation. The version used for this posting was downloaded directly from the AccessData web site (FTK Imager version 2.6.0).
Run FTK Imager.exe to start the tool.
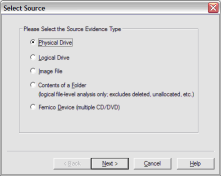
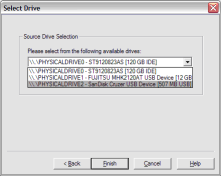
From the File menu, select Create a Disk Image and choose the source of your image. In the interest of a quick demo, I am going to select a 512MB SD card, but you can select any attached drive. NOTE: FTK Imager does not guarantee data is not written to the drive, so it is important to use a write blocker like the Tableau T35es.
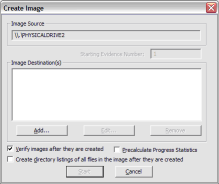
Click Add... to add the image destination. Check Verify images after they are created so FTK Imager will calculate MD5 and SHA1 hashes of the acquired image.
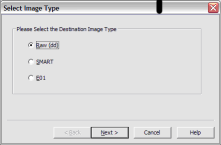
Next, select the image type. The type you choose will usually depend on what tools you plan to use on the image. The dd format will work with more open source tools, but you might want SMART or E01 if you will primarily be working with ASR Expert Witness or EnCase, respectively.
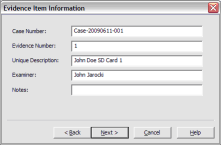
If your version of FTK requests evidence information, you can provide it. If you select raw (dd) format, the image meta data will not be stored in the image file itself.
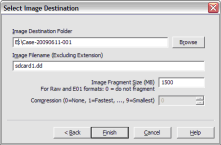
Select the Image Destination folder and file name. You can also set the maximum fragment size of image split files. Click Finish to complete the wizard.
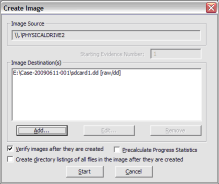
Click Start to begin the acquisition:
A progress window will appear. Now is a good time to refill that coffee cup! Once the acquisiton is complete, you can view an image summary and the drive will appear in the evidence list in the left hand side of the main FTK Imager window. You can right-click on the drive name to Verify the Image:
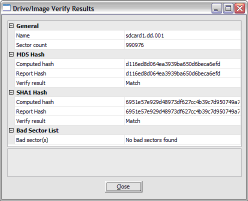
FTK Imager also creates a log of the acquisition process and places it in the same directory as the image, image-name.txt. This file lists the evidence information, details of the drive, check sums, and times the image acquisition started and finished:
Created By AccessData® FTK® Imager 2.6.0.49 090505
Case Information:
Case Number: Case-20090611-001
Evidence Number: 1
Unique description: John Doe SD Card 1
Examiner: John Jarocki
Notes:
--------------------------------------------------------------
Information for E:\Case-20090611-001\sdcard1.dd:
Physical Evidentiary Item (Source) Information:
[Drive Geometry]
Cylinders: 61
Tracks per Cylinder: 255
Sectors per Track: 63
Bytes per Sector: 512
Sector Count: 990,976
[Physical Drive Information]
Drive Model: SanDisk Cruzer USB Device
Drive Interface Type: USB
Source data size: 483 MB
Sector count: 990976
[Computed Hashes]
MD5 checksum: d116ed8d064ea3939ba650d6beca6efd
SHA1 checksum: 6951e57e929d48973df627cc4b39c7d950749a70
Image Information:
Acquisition started: Fri Jun 12 07:39:02 2009
Acquisition finished: Fri Jun 12 07:49:55 2009
Segment list:
E:\Case-20090611-001\sdcard1.dd.001
Image Verification Results:
Verification started: Fri Jun 12 07:49:56 2009
Verification finished: Fri Jun 12 07:50:00 2009
MD5 checksum: d116ed8d064ea3939ba650d6beca6efd : verified
SHA1 checksum: 6951e57e929d48973df627cc4b39c7d950749a70 : verifiedThat's all there is to it!
John Jarocki, GCFA Silver #2161, is an Information Security Analyst specializing in intrusion detection, forensics, and malware analysis. He also holds GCIA, GCIH, GCFW and GSEC certifications and the Treasurer of NM InfraGard.
John Jarocki is a SANS instructor and contributor for the SANS digital forensics blog. He is also an IT Manager and founding member of the global information security team at Xilinx, Inc.
Read more about John Jarocki