SEC595: Applied Data Science and AI/Machine Learning for Cybersecurity Professionals


Experience SANS training through course previews.
Learn MoreLet us help.
Contact usBecome a member for instant access to our free resources.
Sign UpWe're here to help.
Contact UsOne of the biggest challenges with AI comes with determining whether the artifact in question was generated by a human behind the keyboard or by AI.

Has anyone NOT heard the buzzwords Artificial Intelligence (AI) or Machine Learning (ML)? It should come as no surprise they are quickly being integrated into many of the products we use daily, including our smartphones. While adopting these technologies and using them to supplement ordinary tasks may often be overlooked by most users, they add a layer of convenience which may also serve to enrich forensic investigations during an examination. But this can be a two-sided coin as users seek out services aimed at data creation (think videos, images, and documents). We forensic analysts may also need to rely on AI and ML to assist in what could become a muddy field of artifacts.
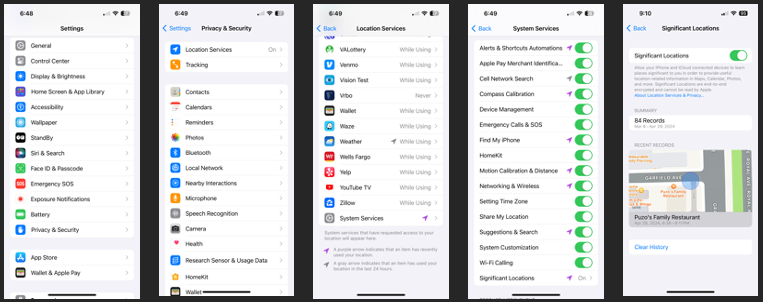
As mobile device users, we have reaped the rewards of ML for quite some time now, probably unbeknownst to most. I personally find many of these features extremely convenient (at least with my iPhone), but what are they and what do our phones do with all this data? As far back as iOS 8, Apple used the Frequent Locations feature to collect data points on the user’s most visited places. In iOS 10, they implemented Significant Locations, which also gathers a vast amount of data with astonishing accuracy. The purpose for collecting all this data? Based on the places you visit most and the length of time for these visits, Apple can provide with more tailored suggestions, alerts, and personalization when using Apple-related features like Apple Maps, Calendar, Photos, the Appstore, and Siri on your device. The information is encrypted and cannot be read by Apple, but as forensic investigators, we realize that this is a gold mine of location information on where and when the user (and their phone) had been.
From a user perspective, we can still see our Significant Locations (or are at least tipped off to the accuracy of what is being stored) by navigating to Settings > Privacy & Security > Location Services > System Services > Significant Locations and using our biometric or device lock to authenticate. What is slightly different than what was provided in pre-iOS 15 is that you are now presented with only the number of locations collected over a span of time (approximately a month), with only a few of your last locations being visible. Perhaps this was to deter people from clearing their location history or from preventing Apple from being able to collect this data in the first place by not being transparent on just how many data points and which ones were collected over time. From a forensic standpoint, because Apple is collecting (and storing for at least a short period of time) all this information based on our habits, we can reap those rewards, if we are fortunate enough to obtain a full file system image of the device, where we can dig into files like Local.sqlite and Cloud-V2.sqlite.
Another example of ML on our devices is the very accurate categorization of some of your favorite people or things when viewing your photo gallery. Our devices can accurately differentiate between and organize people, pets, places, and objects. Again, if your phone can present this level of detail to you, then it must be stored that way somewhere on the device. And fortunately, there are databases (photos.sqlite for iOS and several different databases on Android depending on your manufacturer: including media.db ugc_photos_location_data.db, and dme.db) which exist to record metadata related to multimedia files on these devices.
https://images.contentstack.io/v3/assets/blt36c2e63521272fdc/blt50eadc94d2177703/6633cfa7fb61830dccdc57d4/LC-for585-blog-image-2.pngMultimedia files are often a crucial part of mobile forensics and can consume a significant amount of time to investigate as phone storage capacities continue to increase and people don’t feel the need to purge their data to free up space, so fortunately we can rely on our forensic tools to utilize similar ML capabilities from an investigative standpoint to categorize multimedia files and expedite analysis.
The Magnet Axiom Examine and Cellebrite Physical Analyzer digital investigation platforms, (which are licensed as part of the SANS FOR585: Smartphone Forensics Analysis In-Depth course), offer media categorization modules to organize data into areas of interest for quicker review. In both cases, feeding more data points (e.g., multimedia files) into a model continues to increase the accuracy of machine learning, which provides less false positives. Have you ever wondered how your phone is able to distinguish pets from people as well as uniquely identify them? This is ML at work, and our phones have been getting better at this for years thanks to the wealth of data points we are constantly providing.
https://images.contentstack.io/v3/assets/blt36c2e63521272fdc/bltd336cffcebb5c02c/6633cfa79db1ed6449f6dee3/LC-for585-blog-image-3.pngThings have started to get really interesting, however, with the advent of all of the AI applications and features available to us as users. AI is being natively built into browsers, voice assistants, and many chat applications by default. Chat bots, for example, have become eerily human-like and will even begin to mimic your speech patterns. Because again, you are providing the model with more data (chatting away for hours) for learning.
https://images.contentstack.io/v3/assets/blt36c2e63521272fdc/bltd449c345e2b12bf4/6633cfa76018973a9d40cc31/LC-for585-blog-image-4.pngOne of the biggest challenges with AI comes with determining whether the artifact in question was generated by a human behind the keyboard or by AI. When the artifact exists on the same device used to create it, we can follow traditional approaches like a deep-dive into the application directory of interest, where those app-generated artifacts live. But in many cases, files often get created, then manipulated, and possibly transferred, which strips away precious metadata and further removes the artifact from the application used to create it, making definitive identification much more difficult. This area of mobile forensics is going to get even more challenging as more people utilize these features. With more than 5 million unique applications in Apple’s App store and Google’s Play store combined, this solidifies my stance that there will never be a dull day in the life of a mobile device forensic analyst/researcher.
Dive into the latest in mobile forensics with our updated SANS FOR585: Advanced Smartphone Forensics course. This course has been updated to incorporate the latest tools, techniques, and industry insights. Check out our free course demo or register now to secure your place in our next session. Don’t miss this chance to enhance your expertise and tackle the complexities of modern smartphone forensics—empower yourself to uncover critical evidence and solve complex cases!


Domenica brings 20 years of mobile forensics experience supporting U.S. federal law enforcement and intelligence agencies while leading global training programs for elite investigative units including FBI and military special operations forces.
Read more about Domenica (Lee) Crognale