Editor's note: Brad Garnett recently had an opportunity to interview Jad Saliba, of JADSoftware about how he got started in computer forensics and about some of his company's products. Please note that JADSoftware has offered a discount to readers, see the details below.
Q: Jad, Take a minute to introduce yourself and give us some insight into your background. How did you get involved in computer forensics and software development?
I've been involved in software programming on and off for a long time, going back to my teenage years. I've always had an interest in system tools and figuring out what's going on behind the scenes in a computer. I went to college and studied computer networking and programming, and worked in the industry for a short while before getting into law enforcement, which is another passion of mine. I didn't want anyone to know about my computer skills when I first got hired! But a few years later I was diagnosed with cancer and after being off for a year fighting with that, I started to think that something a little less stressful and with a better schedule would be a good thing for my family and my health. I approached the head of the Technological Crimes Unit, Eugene Silva, who needed an extra hand and graciously brought me into the unit and has kept me there so far!
Q: You have developed several software tools that can assist computer forensic professionals during the analysis phase of a forensic exam. Tools like Internet Evidence Finder (IEF), FChat (FCT), Encrypted Disk Detector (EDD), and Facebook® JPG Finder (FJF) are all great for the forensic examiner's toolkit. We are going to focus on IEF. Explain how IEF is used during media analysis and its capabilities/limitations.
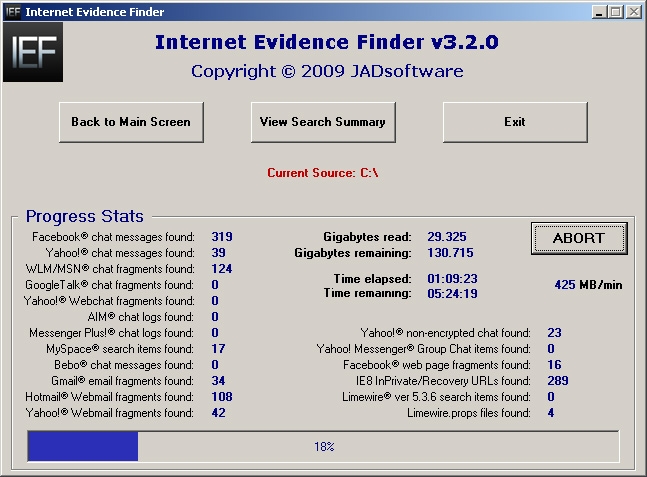
IEF is simply a tool that searches for Internet related artifacts on a disk or in a file and parses them out into a readable format. It currently supports 19 different types of artifacts, including things like Facebook chat, Yahoo! Messenger chat, MySpace chat, Hotmail and Yahoo webmail, Limewire searches, and many more. IEF can be run in a number of different ways. You can run it directly against a drive that is connected via a write-blocker, or on a mounted image (mounted by Encase's PDE or a program like Mount Image Pro). If there are specific files or areas you want to search (pagefile.sys/hiberfil.sys files, or unallocated clusters), you could copy these out and point IEF to the specific files or to a folder containing files. As IEF searches the specified item(s), the results are saved to CSV/TSV report files or individual files, depending on the format of the artifact. Statistics are displayed during the search to keep you updated on the progress.
Q: There have been several updates recently to IEF. What are some future enhancements and capabilities in development for IEF?
I hope to add things that include greatly improved reporting features, an option to search unallocated space only, Unicode support, more searches, and a portable version of IEF that could be run on a live system. There's a long list that I hope to start tackling in the near future.
Q: What programming language did you use when you wrote IEF and why?
I use a mix of Visual Basic and other code, depending on the process. I try to use as many low level system calls as possible to make things run as quickly as the hardware and/or medium will allow. I'm comfortable with Visual Basic and it enables me to easily put my ideas into code while keeping the processes manageable, optimized and running fast.
Q: Do you have any future plans for IEF to be a cross-platform application (i.e. Linux, Mac)?
I don't have any plans for a cross platform application at this time. However, IEF can search drives formatted in Linux and Mac systems if they are mounted on or directly connected to a Windows system. The drive will appear as a PhysicalDrive(#) without a drive letter and IEF can search that raw drive (point it to the PhysicalDrive# that appears).
Q: You stated that there are plans for developing a portable edition of IEF to be used forensically on a live system. As live forensic acquisitions continue to grow, this would be a great tool for the incident responder/forensic analyst. Explain.
I think IEF is very well geared towards memory dump files created by tools such as ManTech's MDD and HBGary's Fastdump PRO. A lot of the testing I do when adding support for new artifacts is with memory dumps. I also have plans for an "IEF Portable" that will run from a thumb drive and could be used with a Windows FE (Forensic Edition) boot disk or other forensic boot disk that would allow IEF to run forensically on the live system. I'm also planning to add a "Quick Search" option for the searches that would only search common areas and things like the pagefile.sys file to give the investigator a quick look or preview of the drive.
Q: Do you have any additional tools in development that you would like to share with the SANS Computer Forensics blog audience?
I'm currently working on an application that will take a list of URLs (or import URLs from a CSV file, such as an Internet history report file) and then visit each URL, taking "scrolling screenshots" of each page and saving them all to an indexed, easy to browse HTML report. I think it will be useful for preserving or visually displaying a portion of a user's web browsing history, and to show what they may have seen when they visited those URLs. It would be especially useful in situations where no Internet connection is available, such as courtrooms.
Q: What can the forensic community do to make IEF better? Do you have a mailing list or a way users can submit issues or provide feedback on IEF?
I'm always open to suggestions for new features (although I won't always be able to make them happen!) and bug reports. I just want IEF to be as easy to use, feature rich, and bug-free as possible. I do have a mailing list that folks can sign up on to receive updates when new programs or releases come out. Comments and suggestions can be sent either through the contact page on my website or directly to my email address, jad-at-jadsoftware-dot-com.
Mr. Brad Garnett, CCE, GCFA is a law enforcement officer specializing in computer forensics. You can follow Brad on Twitter @bgarnett17




