This blog describes a new and significant update to SANS ICS515 and offers insights into the course content and history, which mirror the growing importance and complexity of industrial control systems (ICS) security to the point where today it is one of the most critical areas of cybersecurity across the world.
As the course author, I’ve updated ICS515 before, but this new version finally feels like the course is where I’ve wanted it to be all along, with real programmable logic controller scenarios from real ICS ranges and equipment, as well as material tailored to benefit anyone who plans to assess industrial networks, perform ICS incident response, or build and operate security programs such as industrial security operations.
The History
At the SANS ICS Summit in March 2014, I was chatting with Michael Assante and Tim Conway about the SANS ICS curriculum, which at that point had the fairly new ICS410: ICS/SCADA Security Essentials course. The summit had been around for years but SANS only ran hosted (non-SANS) and non-ICS SANS courses at the event. ICS410 was a fantastic addition as an introductory course that bridged IT and OT skill sets to provide a professional language and understanding of ICS.
At the time I was a U.S Air Force officer leading the mission of the National Security Agency (NSA) to identify previously unknown threats targeting ICS. I had a small but capable team that combined skills across intelligence, network traffic analysis, and incident response domains with a focus on ICS and the threats that were targeting them. I told Mike that it was difficult getting the right talent and that we had resigned ourselves to just bringing people in and teaching them what they needed to know. Mike asked about using ICS410 to help up-level the folks I needed. I mentioned that while ICS410 was a good course, it was aptly focused on introductory material, whereas I was looking for something more advanced and focused on the skill domains of our mission.
Mike and Tim proceeded to challenge me to build something myself as a SANS course. The idea was intriguing, I had been authoring and teaching small hacking-related classes on the Air Force base in Germany for a few years and liked teaching. But I had never really considered becoming a SANS instructor – to be candid, I didn’t think I was good enough. I had a lot of respect for SANS instructors and figured anything I had to offer probably would not meet their standard of quality. However if you’ve ever talked to Mike you know that he can talk you into anything, so after some encouragement to go for it, I agreed.
As I set off on developing the course, Mike and Tim served as my preeminent guides and we set a deadline to launch a beta class in October 2014 at GridSecCon. In hindsight, agreeing to develop a course and have it edited and tested over only a few months was ridiculously ambitious. But I didn’t know any better, and sure enough, I was able to launch the beta class at GridSecCon. It was also incredibly useful that my friend Matt Luallen had what he called CYBATI kits, which consisted of a Raspberry Pi and snap circuits. He agreed to let me use them as the student kit in the course so students would get some hands-on experience with an emulated programmable logic controller (PLC).
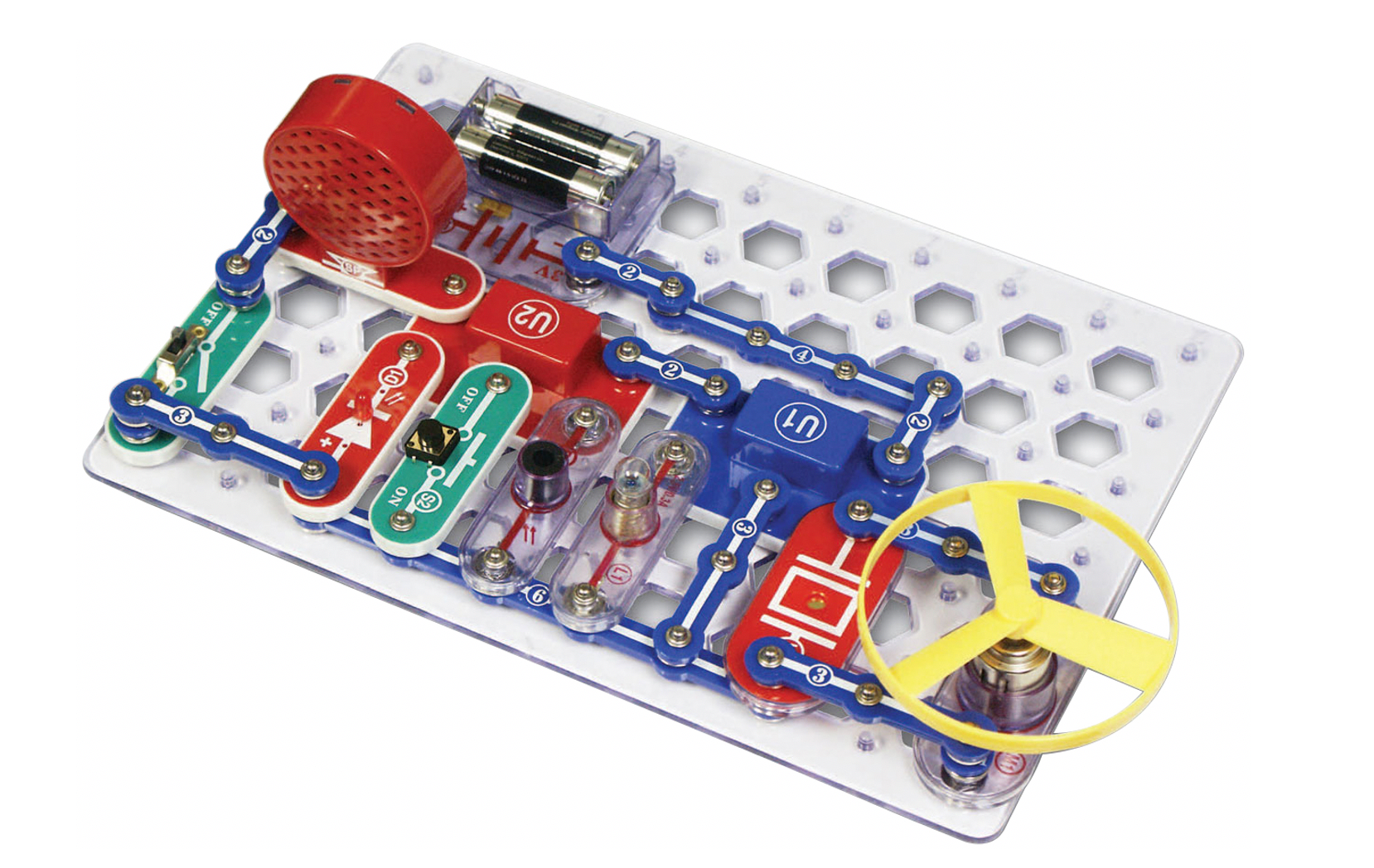
What was then called ICS515: Active Defense and Incident Response was then officially launched at the next SANS ICS Summit in 2015. The course consisted of five days:
- Threat Intelligence Consumption
- Asset Identification and Network Security Monitoring
- Incident Response
- Threat and Environment Manipulation (some very light malware analysis)
- Capstone: Under Attack
The course was a ton of fun, and at the time no one was doing anything like it. There was other ICS security training already out there (Red Tiger Security had a great pen testing course, for example), but the idea of taking an intelligence-driven approach to ICS security was completely foreign to most of the community. The course was all about the skillsets I wanted my NSA and military peers to have coming into the mission and what I thought would be useful for the broader community. The course had one long scenario that the students worked throughout the first four days (using an emulated ICS range of Raspberry Pi kits) and then the capstone, which was another emulated scenario leveraging the kit’s materials. The biggest lesson I learned was that giving students screwdrivers and boxcutters to unpack and build the snap circuits was probably a safety violation waiting to happen!
While ICS515 was a success, I was always chasing making it better and more and more real. Kits were something new to SANS, however, and ICS515 was the first course to use the physical kit and integrate it into the curriculum. So we were learning as we went along.
My first major update to the course, courtesy of Matt, was to upgrade the CYBATI kit to a traffic light system, replacing the snap circuits. The kit was much easier to create (way less parts) and thus no screwdrivers and boxcutters were required (ICS is a safety-focused community after all)! At the same time, I updated the course scenario to include a new emulated range and a full APT-styled intrusion, including the deployment of HAVEX. This gave students a real-world example of seeing ICS-tailored malware and the challenge to identify it correctly.
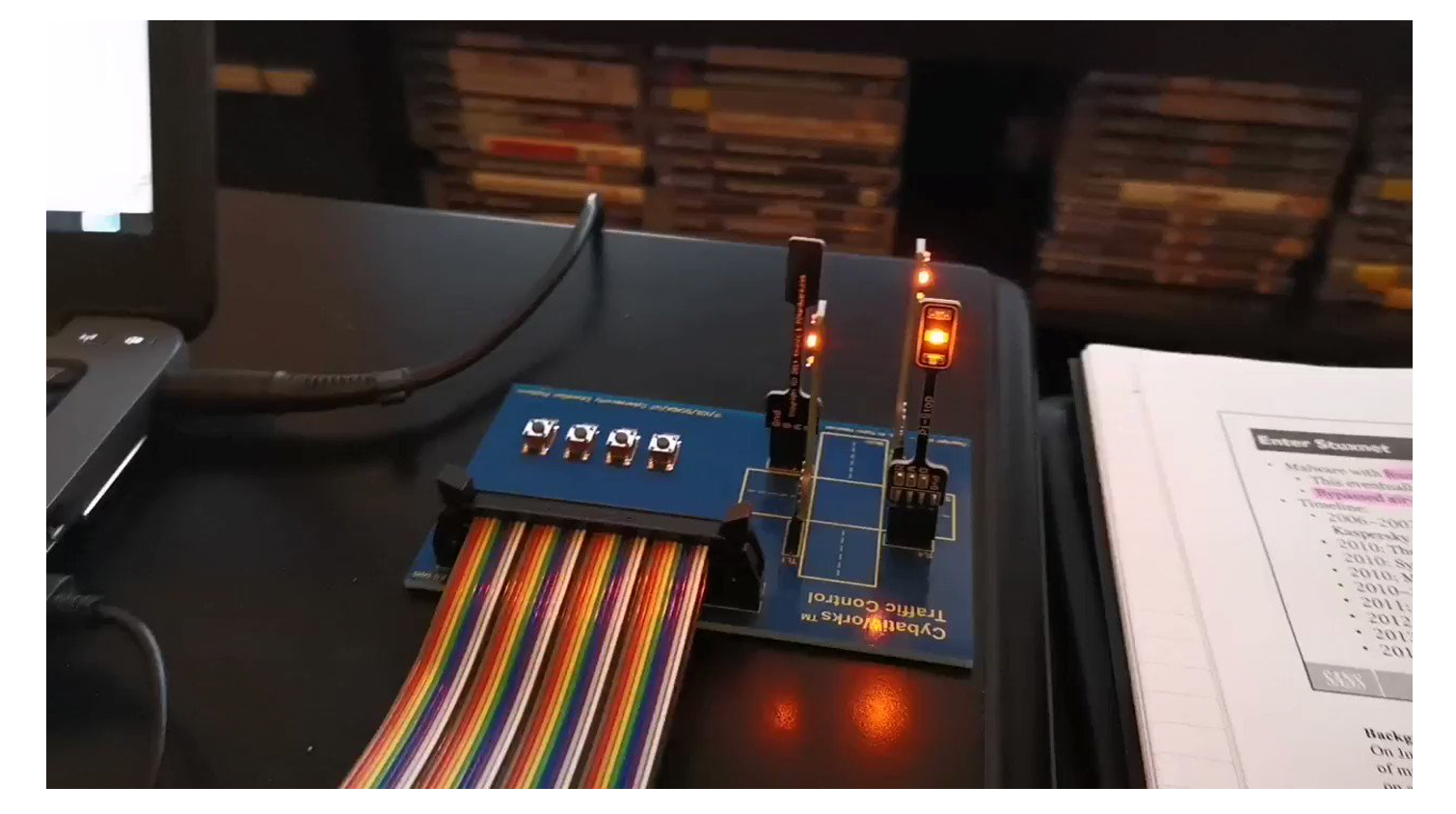
In the ensuing years I’ve always kept the course fresh with new material, slides, case studies, and so on, but the CYBATI kit and the emulated range scenario have remained in various iterations. The students have continued to have a lot of fun and it’s been exciting seeing so many of them progress their careers with SANS ICS515 and the accompanying GIAC Industrial Response and Defense (GRID) certification in their résumés.
The certification was an exciting complement to the course because it gave a professional language and understanding to everyone who’s taken the course. Certs don’t make you an expert, but they are a signal to others that you have a base of knowledge rooted in something. So if you have the cert it can shortcut a lot of conversations to get to a practical lexicon and shared concepts to work together more efficiently.
Even though thousands of students have by now passed through ICS515 and it has an impact in ways I never could have imagined when it started, I always felt it wasn’t “real” enough. I have wanted to level it up further, but the mechanism to do that was difficult. Having a full ICS range as an example is not a cheap endeavor, so emulation would have to suffice. Eventually Tom VanNorman helped me make a small water-themed range to add as a scenario in the course, but even that wasn’t enough for my over-engineering purposes.
The New SANS ICS515
Now, with the help of Tim Conway, Jeff Shearer, and Jason Dely, who constitute the SANS ICS research and development team, today I can introduce the new SANS ICS515. The course has a new name – ICS515: ICS Visibility, Detection, and Response – to underline the significant changes and to account for the new day of material, as the course has been expanded to six days. The course days are:
- Threat Intelligence Consumption
- Visibility
- Threat Detection
- Incident Response
- Threat and Environment Manipulation
- Capstone
The previous Asset Identification and Network Security Monitoring day has been split into two days to give each area a full day of content and incorporate important models such as the Collection Management Framework. The fifth day has also been compressed to allow for more time to have a mini-capstone (a full scenario for students to work together independently or collaboratively). The old fifth day is now day six with the technical capstone, though that’s also been updated. The scenario in the course no longer uses an emulated ICS environment and instead uses a full ICS range, borrowing data from the Dragos range. Altogether, the course material is 70%+ new in the slides and material and 90%+ new in the technical content and exercises.

And of course the most exciting change is an all new kit! We’ve moved away from the CYBATI kits and now have a real PLC with a full physical setup, human machine interface (HMI), and engineering workstation. Students will leverage this across multiple exercises in the course and get to keep the kit after the course to continue to leverage it for learning and fun projects.
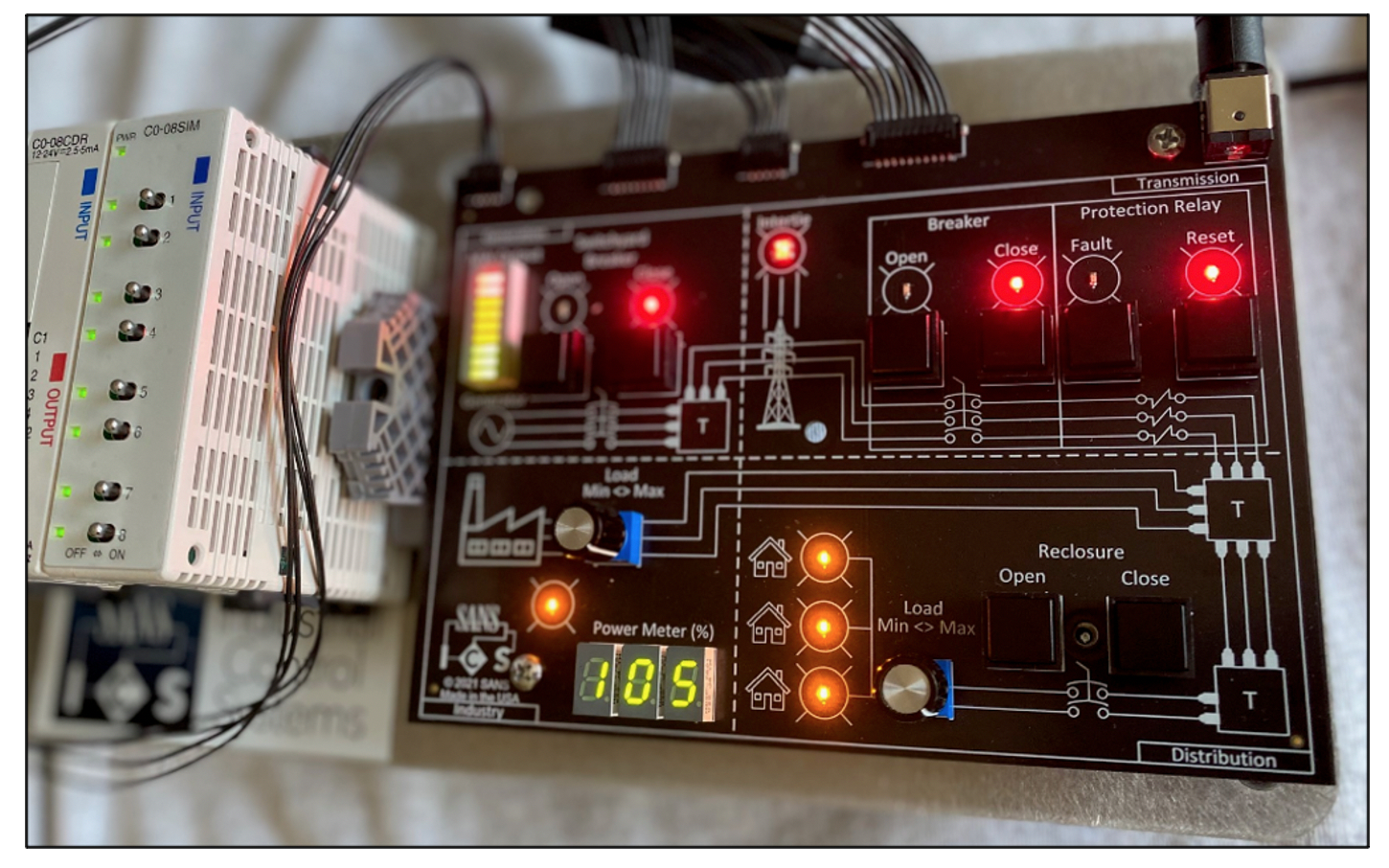
The new kit is quite impressive. Students will be operating a combined-cycle power generation site and electric system generation, transmission, and distribution, as well as an industrial oil and gas customer site. While the objective is cybersecurity training, students will also walk away with a much deeper understanding of industrial operations and a small window into what it means to operate an industrial plant. As mentioned earlier, the new ICS515 uses real PLC scenarios from real ICS ranges and equipment, as well as material tailored to benefit anyone who plans to assess industrial networks, perform ICS incident response, or build and operate security programs such as industrial security operations. I’m really excited for the students who are going to take the updated course. Thanks to everyone along the way who made this a possibility. I look forward to interacting with many of you in the future.
LEARN MORE ABOUT ICS515 & REGISTER TO TAKE THE COURSE
- Find out more about the new and improved ICS515 course here.
- The launch of this new ICS515 course will be at the SANS Dallas: Virtual Edition 2021 from October 11th-16th. Registration for the event can be found here.
- View all upcoming runs of ICS515 here.
LIVE STREAM
Check out the recording of this ICS515 livestream where Robert M. Lee was joined by other ICS515 instructors, and see them discuss all the updates to the course!



.jpg)
