SEC595: Applied Data Science and AI/Machine Learning for Cybersecurity Professionals


Experience SANS training through course previews.
Learn MoreLet us help.
Contact usBecome a member for instant access to our free resources.
Sign UpWe're here to help.
Contact Us
One of the biggest complaints that many have in the DFIR community is the lack of realistic data to learn from. Starting a year ago, I planned to change that through creating a realistic scenario based on experiences from the entire cadre of instructors at SANS and additional experts who reviewed and advised the attack "script". We created an incredibly rich and realistic attack scenario across multiple windows-based systems in enterprise environment. The attack scenario was created for FOR508: Advanced Incident Response, Threat Hunting, and Digital Forensics. Our main goal was to place the student in the middle of a real attack that they have to response to.
The purpose is to give attendees real filesystem and memory images that they will examine in class to detect, identify, and forensicate APT-based activities across these systems in class. The goal is to give students who attend the course "real world" data to analyze. The goal was to create attack data to use in our courses at SANS so our students could have a direct feel for what it is like to investigate advanced adversaries.
As a part of that exercise, the main spearphishing attack was the result of a Java Applet attack. It can be clearly seen in this super timeline created as a part of the course. We find the exact pivot point in the timeline using memory analysis - both Redline from MANDIANT and Volatility in the SIFT Workstation.
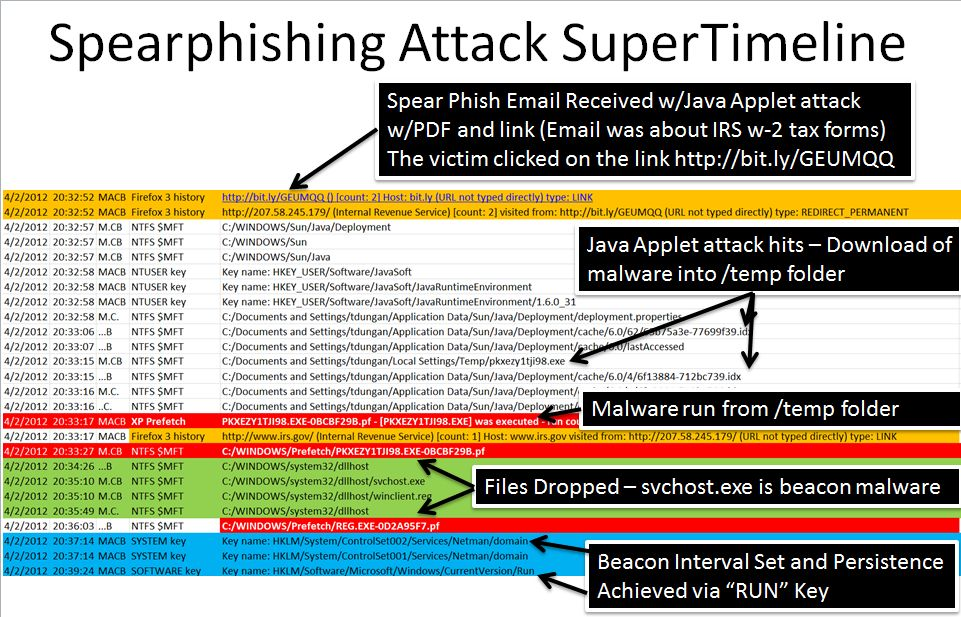
Over the past few weeks, many capabilities have been created to parse the JAVA based malware specifically in the IDX files that can be seen as a part of this attack.
Note: By downloading the zipfile, you consent automatically to the following agreement: I certify that by having access to tools and programs that can be used to break or "hack" into systems, that I will only use them in an ethical, professional and legal manner. This means that I will only use them to test the current strength of security network so that proper improvements can be made. I will always get permission before running any of these tools on a network. If for some reason I do not use these tools in a proper manner, I do not hold SANS liable and accept full responsibility for my actions.


Launched in 1989 as a cooperative for information security thought leadership, it is SANS’ ongoing mission to empower cybersecurity professionals with the practical skills and knowledge they need to make our world a safer place.
Read more about SANS Institute