Hardly a day goes by without me hearing the phrase 'Threat Intelligence' being used in the context of big budget enterprise protection, but recently I have been giving some thought to what this means to the home user and small business.
Most computers have (or at least, should have!) up-to-date antivirus software installed which provides a certain degree of protection and gives insight on whether a particular file, or set or circumstances, are suspicious according to vendor X (using signatures, reputation lookup and several other methods), but I'm sure there is more that the open source cyber security community can do to protect itself by leveraging fantastic free resources, such as the VirusTotal Public API.
check_first.exe, a proof of concept
To this end, I've just finished writing a proof-of-concept tool to demonstrate how public threat intelligence APIs can be leveraged to provide automated insight
(Disclaimer: This isn't supposed to replace your existing protection - it's just an idea!!)
So here's how it works...
- A SHA256 hash is generated for the file being examined
- The hash is transmitted to VirusTotal via their public API
- The response is processed in conjunction with the user specified option to determine the next action, which will either be run the program / open the file (if we're happy) or don't run the program, and open the web browser to the appropriate VirusTotal analysis page for review (if we're not so happy)
[Update: As of version v1.1, in addition to hash based checks, you now have the option of automatically uploading files that VirusTotal hasn't seen before (for a full scan by all 57 AV engines) and then waiting for the result live, before the decision on whether the file should be run/open is made]
Mode vs outcome
So, if VirusTotal says it has seen the hash before and it's definitely infected, or "probably" clean, the choice is pretty easy - but what if they've never seen the hash before? Well, this is where the user decides.
If you use the /stop-unknowns argument, then the presumption is that if the hash hasn't been seen before, then it's not trusted enough to execute. If you leave the option off, then it will presume it's okay and the file will execute (as detailed in the table below). At this point, it's a trade-off between functionality and security.
| Mode / Response | Normal Mode | Stop Unknowns |
|---|---|---|
| VT positive detection | Does not run / VT site opens | Does not run / VT site opens |
| VT negative detection | File runs / opens | File runs / opens |
| VT never seen hash | File runs / opens | Does not run / VT site opens |
It's easier if I show you...
I've created a short video demo of the tool in action, to show it's capability and my thought process during its development. If you'd like to watch, click on the image below!
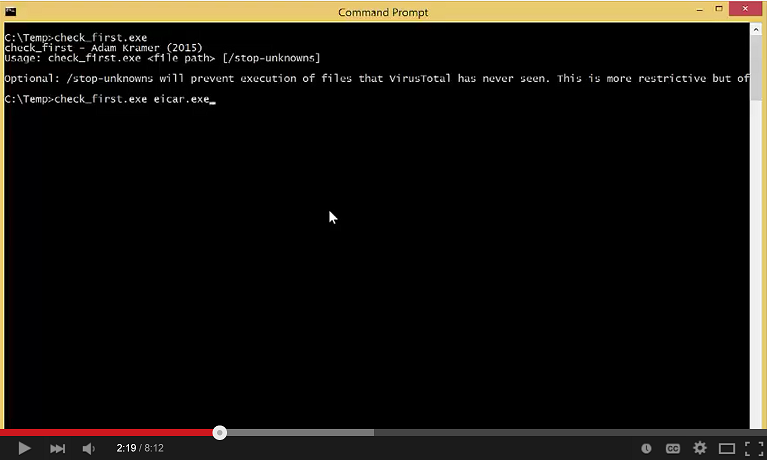
So what's next? Well, I've been considering using the NT Kernel Logger or a file system filter driver to further automate the analysis based on process launches.
Before anyone says it! I know that searching on hash is not the most effective way to protect against malicious software, but I would like you to consider the following...
- Unless it's targeted or polymorphic, the chances are that at least one of VirusTotal's 57 AV vendors will have seen it before it arrives on your PC
- If you use 'stop unknowns' and combine it with the NIST software hash library you'd have quite a nice cloud-based-crowd-sourced-whitelisting solution (for free!)
- ...this just an open-source proof-of-concept, I'm not asking you to buy it!!
- [Update: As of v1.1, you have the option of uploading files that VirusTotal hasn't seen before (for a full scan by all 57 AV engines) and then waiting for the result live, before the decision on whether to run/open the file is made]
I have released the source code and binary on my github page, and would very much welcome feedback on how it can be improved.
If you'd like to continue the discussion about home user threat intelligence, I can be found on Twitter: @CyberKramer
Thanks for reading!




