SEC595: Applied Data Science and AI/Machine Learning for Cybersecurity Professionals


Experience SANS training through course previews.
Learn MoreLet us help.
Contact usBecome a member for instant access to our free resources.
Sign UpWe're here to help.
Contact UsIn this blog post, we discuss the various methods of accessing and exporting the Unified Audit Log (UAL)

So far in our blog post series on cloud log extraction, we have looked at extracting logs from AWS, Google Cloud, Google Workspace and Azure. In the fifth and final installment of this series, we’ll be looking at how we can view and extract logs from Microsoft 365.
This first post will look at Microsoft 365. One of the benefits of Microsoft 365’s logging is that they centralize all logs into the Unified Audit Log (UAL). This single log will contain user and admin activity for Azure AD, Exchange, SharePoint, OneDrive, and more. We’ll specifically look at three ways in which we can query and export the UAL:
All three options have various strengths and weaknesses, so it’ll all depend on your use case which of the methods you want to leverage.
Accessing the logs via the Microsoft Purview Compliance Portal is best used in situations where you want to perform a quick, targeted search. It has good built-in search functionality but leveraging the data in the portal is more difficult and the export function has restrictions that make it less than ideal for use. If you do choose this method to extract logs, you can use the following steps:
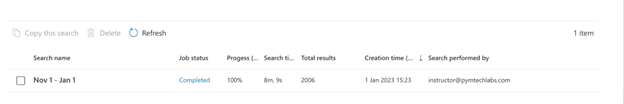
Unfortunately, another drawback of this method is that the SOF-ELK Microsoft 365 parser does not support Purview exports. For SOF-ELK compatibility, you should use the PowerShell method discussed in the next section. The most important data in the CSV export is stored in the form of a JSON blob within the “AuditData” column. As such, if you are going to review the logs in Excel or another CSV viewer, you need to transform that column. Microsoft provides step-by-step instructions on how to do this in their documentation.
PowerShell has a Cmdlet called Search-UnifiedAuditLog that allows you to query and export the UAL via a PowerShell interface. This method is best used when trying to export a small amount of the UAL as it limits the number of records to 5,000. If you need more than 5,000 records and want to leverage PowerShell, we recommend taking a look at the Microsoft Extractor Suite mentioned in the “Open-source UAL Collection Tools” section below.
Before attempting to export the UAL via PowerShell, you need to install the Exchange Online PowerShell module which provides the cmdlets for interacting with Microsoft 365. Furthermore, you need to ensure you have the permissions required to access the UAL via PowerShell. At minimum, you need the View-Only Audit Logs role assigned to your user via a role group in the Microsoft 365 admin center. Once these prerequisites are in place, the following steps can be performed to export the logs.
From this point, you can import the JSON file into SOF-ELK (by copying it to the Microsoft 365 Logstash directory) or another parsing tool of your choosing.
The final method that can be used for exporting the UAL is the Microsoft 365 Management API. This is best for environments looking to continuously query the UAL in order to ingest the logs into an external platform such as a SIEM or large environments that exceed the export limits of the PowerShell Cmdlet. The API endpoint will only return results from the last 7 days, so it must be polled on a continuous basis via a custom-developed application or commercial solution that leverages the API. The high-level steps for using the API are as follows:
For more in-depth guidance on leveraging the API, see Microsoft’s documentation here: https://for509.com/ualmgmtapi. If you are leveraging a commercial product for collecting these logs, they will most likely have a built-in integration and configuration guide for connecting your solution to the API.
As mentioned in the previous blog post in this series, Invictus IR has released a suite of scripts for extracting Microsoft logs (both 365 and Azure) using PowerShell. One of the major benefits of these scripts is that it breaks down the extraction into chunks in order to avoid the record limit imposed by the Search-UnifiedAuditLog PowerShell cmdlet. The scripts related to extracting the UAL are:
These scripts can be accessed at no cost at the following Github link: https://for509.com/invictus-suite.
In this blog post, we discussed the various methods of accessing and exporting the Unified Audit Log (UAL). If you need a way to perform a quick and targeted search, you can leverage the Purview Compliance Portal. If you want to retrieve a small part of the UAL and export to JSON format, PowerShell has the Search-UnifiedAuditLog cmdlet. For larger organizations or those who need to continuously poll the UAL, there is the Microsoft 365 Management API.
We hope that this series of blog posts on extracting cloud logs will better prepare you for when an incident occurs in your cloud environment! If you want to learn more about leveraging these logs for incident response, check out SANS FOR509: Enterprise Cloud Forensics and Incident Response.
https://images.contentstack.io/v3/assets/blt36c2e63521272fdc/blt7681227400dbbb3b/64de3c584eb700227af7e9b4/FOR509_banner.png

Megan is a Senior Security Engineer at Datadog, SANS DFIR faculty, and co-author of FOR509. She holds two master’s degrees, serves as CFO of Mental Health Hackers, and is a strong advocate for hands-on cloud forensics training and mental wellness.
Read more about Megan Roddie-Fonseca