SEC595: Applied Data Science and AI/Machine Learning for Cybersecurity Professionals


Experience SANS training through course previews.
Learn MoreLet us help.
Contact usBecome a member for instant access to our free resources.
Sign UpWe're here to help.
Contact Us
Microsoft releases out of band patch: https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-0796
SMBv3.11 has a buffer overflow vulnerability when compression is enabled (default value). Windows 10 and Server use SMBv3.11 and the service runs as SYSTEM. Successful exploitation will result in remote code exection, with SYSTEM privileges. This is considered “wormable”. Microsoft did not release a patch in March 2020 Patch Tuesday.
Microsoft pulled the patch for CVE-2020–0796 from March 2020 Patch Tuesday at the last minute and some information was leaked by Cisco Talos but then deleted from their post. A screenshot I took states:
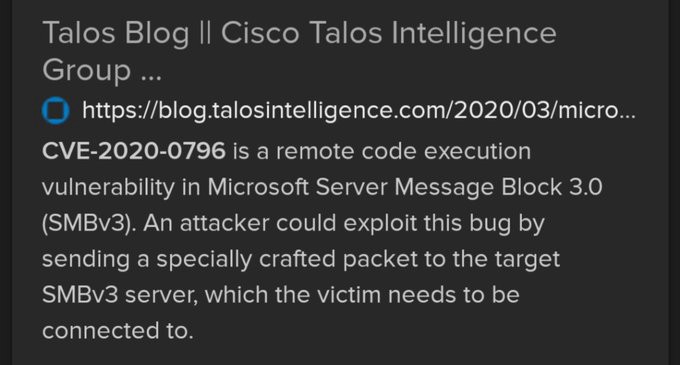
Microsoft then released an advisory with more information: https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/ADV200005
“Microsoft is aware of a remote code execution vulnerability in the way that the Microsoft Server Message Block 3.1.1 (SMBv3) protocol handles certain requests. An attacker who successfully exploited the vulnerability could gain the ability to execute code on the target SMB Server or SMB Client. To exploit the vulnerability against an SMB Server, an unauthenticated attacker could send a specially crafted packet to a targeted SMBv3 Server. To exploit the vulnerability against an SMB Client, an unauthenticated attacker would need to configure a malicious SMBv3 Server and convince a user to connect to it.”
CERT followed: https://www.kb.cert.org/vuls/id/872016/
This issue affects both SMB client and server that have SMBv3 Compression enabled. Remote code execution is possible from the network (unless TCP port 445 is blocked). CVSSv3 of 10. SMB runs with SYSTEM privileges.
Impacted systems must run SMB v3.11. Compression is enabled by default. Windows 10 Version 1903 for 32-bit Systems Windows 10 Version 1903 for ARM64-based Systems Windows 10 Version 1903 for x64-based Systems Windows 10 Version 1909 for 32-bit Systems Windows 10 Version 1909 for ARM64-based Systems Windows 10 Version 1909 for x64-based Systems Windows Server, version 1903 (Server Core installation) Windows Server, version 1909 (Server Core installation)
Method to identify if SMB v3.11 is running and therefore vulnerable, given no patch, is possible through nmap:
#!/bin/bash
if [ $# -eq 0 ]
then
echo $'Usage:\n\tcheck-smb-v3.11.sh TARGET_IP_or_CIDR'
exit 1
fi
echo "Checking if there's SMB v3.11 in" $1 "..."
nmap -p445 --script smb-protocols -Pn -n $1 | grep -P '\d+\.\d+\.\d+\.\d+|^\|.\s+3.11' | tr '\n' ' ' | replace 'Nmap scan report for' '@' | tr "@" "\n" | grep 3.11 | tr '|' ' ' | tr '_' ' ' | grep -oP '\d+\.\d+\.\d+\.\d+'
if [[ $? != 0 ]]; then
echo "There's no SMB v3.11"
fiOther scanners:
cve-2020-0796
#!/bin/bash
if [ $# -eq 0 ]
then
echo $'Usage:\n\tcheck-smb-v3.11.sh TARGET_IP_or_CIDR'
exit 1
fi
echo "Checking if there's SMB v3.11 in" $1 "..."
nmap -p445 --script smb-protocols -Pn -n $1 | grep -P '\d+\.\d+\.\d+\.\d+|^\|.\s+3.11' | tr '\n' ' ' | replace 'Nmap scan report for' '@' | tr "@" "\n" | grep 3.11 | tr '|' ' ' | tr '_' ' ' | grep -oP '\d+\.\d+\.\d+\.\d+'
if [[ $? != 0 ]]; then
echo "There's no SMB v3.11"
fiSMBv3 compression can be enabled for server service via registry as specified in ADV200005:
Disable compression:
Enable compression:


Jorge Orchilles currently serves as a Senior Director at Verizon, where he leads the Readiness and Proactive Security Team. His team specializes in Exposure & Vulnerability Management, Penetration Testing, Red Team, Purple Team, and AI Red Team.
Read more about Jorge Orchilles