Tags:
SEC488: Cloud Security Essentials has received a major update to ensure that organizations can continually enhance their security posture in their migration to cloud technologies. During this update, you will now embark on a journey to prevent, detect, and respond to threats in their role as a Cloud Security Engineer for the fictitious rock band CD/CA. This organization requires your expertise to protect their critical, cloud-based infrastructure to ensure that they can continue to focus on what they do best: tour the world and provide their music to their dedicated fans.
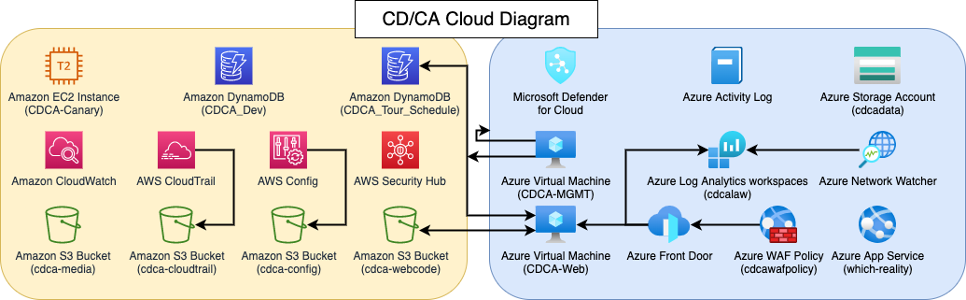
The bulk of this course update comes in the form of its hands-on exercises. You will be tasked to defend not one, but two cloud vendor environments: Amazon Web Services (AWS) and Microsoft Azure. In these environments you will find cloud virtual machines, cloud storage, logging services, and a few vendor-managed security services to assist in further defense of the critical CD/CA services.
Also included in this update are the necessary revisions to the defensive techniques, topics, and discussions in several areas that have matured or became available to customers since the last major course update. This is all in an effort to ensure that you walk away with the most relevant and up-to-date material possible to defend your organization’s cloud workloads as cloud is ever-changing.
Below is an overview of the major changes in this update that you will learn about or practice in the hands-on exercises:
SEC488.1: Identity and Access Management
- Deeper discussion on cloud vendor CLI tools and usage
- More techniques to work towards a least privilege permissions model
- Setting up new cloud users to ensure the confidentiality, integrity, and non-repudiation security principals
- Create permissions boundaries to restrict user access and prevent “privilege creep”
- Deploy the brand-new CD/CA cloud environment using HashiCorp Terraform
SEC488.2: Compute and Configuration Management
- Focus on “shifting security left” when deploying cloud-based virtual machines
- Explore real-world breaches and the vulnerabilities responsible
- Practice deploying a new cloud virtual machine, hardening it to security and organizational standards, and save the image for future use
- Place network-based restrictions on cloud storage
SEC488.3: Data Protection and Automation
- Discuss more techniques to find sensitive data in your cloud-based storage—whether it is stored in a managed service or virtual disk
- Due to several changes to Microsoft 365’s Admin Centers, updated to discuss how protecting Microsoft 365 data
- Practice data hunting in both disk storage and NoSQL database storage using cloud vendor CLI tools
SEC488.4: Networking and Logging
- Deeper discussion on how to protect virtual machine management services—including how to address challenges related to a mobile workforce
- Use Just in Time (JIT) to allow access to important services only when required
- Detect suspicious management and data plan activity in your cloud accounts and services
- Integrate virtual machine operating system and application log data into a cloud vendor-managed logging solution
SEC488.5: Compliance, Incident Response, and Penetration Testing
- Discussion on how to leverage serverless technologies, as a defender, to automate response to suspicious cloud account activity
- Discussion of new and emerging technologies that help limit the blast radius on a compromise
- Discover new methods to breach, pivot, and exfiltrate data in a cloud environment
- Detect and respond to a previous infection in your cloud accounts
SEC488.6: CloudWars Challenge
- Brand new and modified challenges to further prove to yourself and fellow competitors just how well you understand how to defend a cloud environment
This updated version of the course will be released at SANS 2022 in Orlando FL, starting April 10, 2022.




