Tags:
John Pescatore - SANS Director of Emerging Security Trends
Avoiding “Too Big to Fail” Risk Assessment and Mitigation Blind Spots
This week’s Drilldown will focus on an item (included below) from NewsBites Issue 20, again focusing on high criticality, zero day vulnerabilities in Microsoft Exchange software, which are being actively exploited by multiple threat actors. Some attacks started before Microsoft issued the emergency patches.
SolarWinds Orion and Microsoft Exchange are two examples of prime targets for attackers. Those products are directly handled and/or placed on network segments where highly sensitive information is being processed. But an underlooked, and equally as important, factor is that those products have an extremely high enterprise market share. Finding an exploit opens up thousands of targets for exploitation.
There are many other products that fit this profile. For an example, here’s a market share chart of IT Service Management vendors:
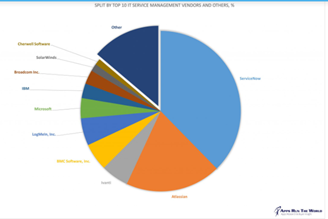
ServiceNow would be the obvious target in this market. Open source tools such as Ansible, Jensen, and others have high “market” shares. Remember the impact of the Heartbleed vulnerability in OpenSSL? Cloud services like Azure and AWS have dominant shares.
Products in use by the IT infrastructure aren’t the only examples. Products like SAP or Oracle Business Solutions have high market shares overall or in certain verticals. In manufacturing, power, medical, retail, and other verticals, there are similar software products and appliances that have dominant market shares.
High market share products are often seen as safe and “too big to fail.” The old phrase was, “No one ever got fired for choosing IBM or Cisco.” That thinking has created a blind spot in risk analysis. The damage if one these “safe” choices is compromised is under-represented in risk weighting.
This “concentration” risk means attackers are spending more time looking for vulnerabilities. Equally, if not more important, even if you escape damage, the odds are very high that multiple places in your supply chain will be compromised.
A quick inventory scan will find a few of these high market share products in your environment. Use one of them for a tabletop exercise around how prepared you are if one of them had a SolarWinds or Exchange-class vulnerability. Mitigation and avoidance will invariably require change in many areas outside of security, so the next step is a similar tabletop exercise with CXOs and boards of directors.
______________________________________________________________________________
2021-03-11
Multiple Threat Actors Are Exploiting Exchange Server Vulnerabilities
According to analysis from ESET, at least 10 APT groups are exploiting the Microsoft Exchange Server vulnerabilities. Many of the groups have ties to China. Six of the groups were actively exploiting the flaws prior to Microsoft’s emergency patch release on Tuesday, March 2.
Editor's Note
The interval between initial exploits by Hafnium and additional APT groups is simply too small for them to have independently discovered the vulnerabilities and developed working exploits. This suggests that after the initial exploits were leveraged by Hafnium in or before January, they then were shared with other groups, such as Tick, LuckyMouse, Calypso, Webslic, and APT41. Given the scope of added exploits discovered, assume they are shared even more broadly. For this reason, it is best to operate on the model that all Exchange servers are targets and that you not only need to apply the patches, but also check carefully for signs of compromise. Make sure that your real-time endpoint protection includes the Exchange vulnerabilities and IoCs.
Lee Neely
This issue of NewsBites features a wide array of vulnerabilities in IT critical infrastructure elements, such as Windows, MacOS, Exchange and F5 Big-IP--without even mentioning SolarWinds Orion. This points out two big issues that are pre-requisites to even considering talking about buzzwords like zero trust: (1) to be proactive, risk analysis has to focus as much (really more) on where vulnerabilities would cause the most impact to business as on who might launch attacks; and (2) if you can’t get the critical IT infrastructure elements to the essential security hygiene level (meaningful segmentation, rapid patching, configuration management), you have no chance in assessing the trustability of anything else.
John Pescatore
I concur with John Pescatore, but I want to stress the urgency and seriousness. Our infrastructure now stands naked before a nation-state willing to take the risk of being caught in the act of compromising that infrastructure. We must assume that that state will work to maintain its advantage and that in time of crisis would exploit it.


