In recent posts, I have reported on some of the findings published in a paper I published with Dave Kleiman and Sundhar S. R. S [1]. We are working on a series of follow-up papers on the topic where we are using Spin-disk and SEM based techniques to map out what occurs in each bit cell as they are overwritten. Prof. Fred Cohen (the person who first made the term computer virus in the 80's) has been coercing us to do this.
One thing I shall try and clear up for the moment is that of multiple overwrites. What people have missed in many instances is that use of the drive is equal to a wipe sequence. This is that the wipe can be done BEFORE as long as a wipe is also done after. This is the drive that is wiped two (2) times before being used and then is wiped before being handed over is equivalent to the drive that has had three (3) wipes done sequent.
What matters is that random data or writes are made to the drive platter at some time. This can be from use or a prior wipe. Even a zeroing of the drive before use reduces the chances of recovering data following a single wipe. There is no order in the magnetic flux density that occurs from data use. Each grain in a bit-cell varies, but it does not remember the order it was written to. For instance, if we take the table below to represent a single bit cell with each of the table's cells being a bit cell, we get an idea of how the data is distributed. For instance a one (1) could be distributed as:
Within this bit cell we have an average or mean value that equals 0.80. This is read as a "1" by a ePRML drive.
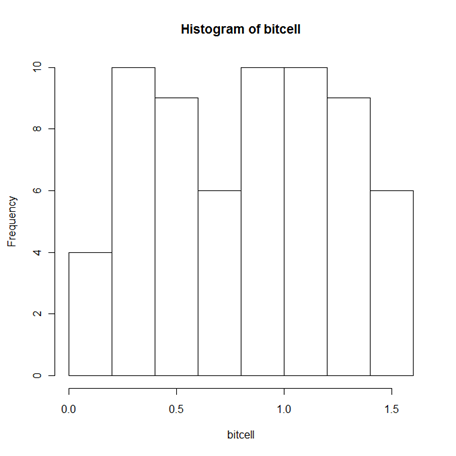
A histogram of the grains is displayed above. As you can clearly see, there are some grains in the bitcell that are less than a ePRML drive would map to be a "1". With values as low as 0.20, you see that not all grains act as they should. On the other hand, if we write a series of '1's to the bitcell in a sequence, there is some clear increase in the mean value and distribution. The results of one such test are displayed below.
Here we have a bitcell with a mean or average read value of 1.09. This is clearly closer to the '1.00' value that ideally we would always obtain. PRML and ePRML are statistically based methods however. In this second table, the write pattern was '1', '1', '0', '1' with a greater number of writes of a '1', more grains have held higher values of magnetic flux. We can see this displayed in the histogram below.
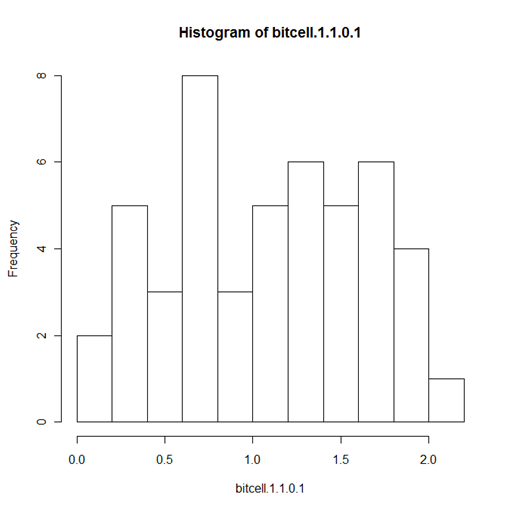
What is of interest is that we do not get to see that the prior value was a '0'. If our forensic examination was attempting to uncover a single bit in the bitcell, the writes to the bitcell of the '1' and the '1' that occurred PRIOR to the wipe of the '0' with another '1' value are in themselves sufficient to remove all chance of recovering the value of the data before the wipe. This is, there is no way to determine if a write of a '1' followed by a '1' occurred or if the '1', '1', '0', '1' pattern occurred.
Even a series of low level formats will do. A tool such as the "hdd low level format tool 2.36" will completely erase the data. So you start by wiping your drive (or doing a series of low level formats), use it as you normally would, and that final single wipe is just as good as a series of wipes. One thing that can be demonstrated from this is that there is no magic wiping formula. A single random pass is ok. There is no magic formula for what order you wipe drives in.
Of course, all of this implies that the entire drive has been wiped (even the HPA — host protected area). On top of that we need to remember that even single recovered bits are going to be stochastically distributed following even a single wipe.
Most importantly, if you ever do a forensic recovery of a drive using a Spin-Stand, you will not have the prior values of the grains and hence the bitcells before the wipe. This would be equivalent to having the data and image before the disk was wiped - negating the need to do the exercise.
To this end and to have time for my academic pursuits as well as paying the bills I have started a new company. I doubt I will have much call for drive recovery using a spin-stand, but I shall offer it and see what is about. More importantly, I will be writing a manual on using SEM's and Spin-Spands for drive recovery to add to Scott Moulton's great new course; SEC 606 - Drive and Data Recovery Forensics. This is being offered at SANSFIRE 2009.
[1] Wright, C.; Kleiman, D, & Sundhar S. R. S.: (2008 ) Overwriting Hard Drive Data: The Great Wiping Controversy. ICISS 2008: 243-257
Craig Wright, GCFA Gold #0265, is an author, auditor and forensic analyst. He has nearly 30 GIAC certifications, several post-graduate degrees and is one of a very small number of people who have successfully completed the GSE exam.



.jpg)
