The pivot. Many intrusion campaigns follow a similar modus operandi. Attack the publicly available DMZ. Gain access to an initial target and leverage that access to pivot into the internal network. Now seize the objective. On Linux systems, Secure Shell (ssh) natively supports socks proxying. We can use this to bounce our tools off of a compromised host. This has two powerful use cases: attribution and pivoting. In the first case, sophisticated attackers and nation state threats often hop through an infrastructure of pre-compromised hosts to hide their true source or to perform misattribution (framing someone else for your attack). For penetration testers the latter use case, pivoting, tends to prove more useful. Specifically, leveraging an attack beachhead to further an ongoing intrusion campaign is standard and essential tradecraft. As mentioned on Linux this is often quite simple, but what about Windows?
Pivoting through Windows is often accomplished through specialized tunneling applications. Pivoting and port forwarding, for instance, are capabilities built directly into the popular Metasploit meterpreter. Nevertheless, more advanced attackers often rely on native system components in order to evade detection. In this post we will examine inherent Windows mechanisms to accomplish network pivoting.
Methods Covered in this Section:
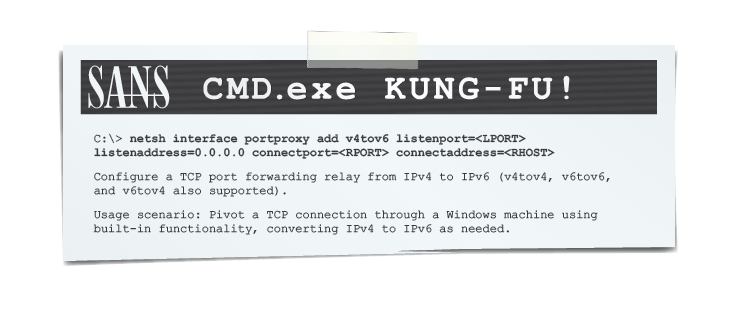
netsh IPv4 to IPv6 port conversion for a remote computer:
netsh interface portproxy add v4tov6 listenport=8888 listenaddress=0.0.0.0 connectport=80 connectaddress=2000::1:215:5dff:fe01:247
netsh IPv4 port to another IPv4 port on the same host:
netsh interface portproxy add v4tov4 listenport=9999 listenaddress=0.0.0.0 connectport=445 connectaddress=192.168.1.112
netsh ipconfig:
netsh interface ipv4 show addresses
The network shell or netsh is a Windows command-line utility that was included in Microsoft operating systems beginning with Windows 2000. Its focus is command-line configuration of network utilities, but netsh encompasses a wide range of dynamic functions.
The Netsh Interface Portproxy provides command-line connection proxying between systems with direct IPv4 to IPv6 translation built in. This sounds a bit like tunneling, right? It is, from the DMZ host execute:
netsh IPv4 to IPv6 port conversion for a remote computer:
netsh interface portproxy add v4tov6 listenport=8888 listenaddress=0.0.0.0 connectport=80 connectaddress=2000::1:215:5dff:fe01:247
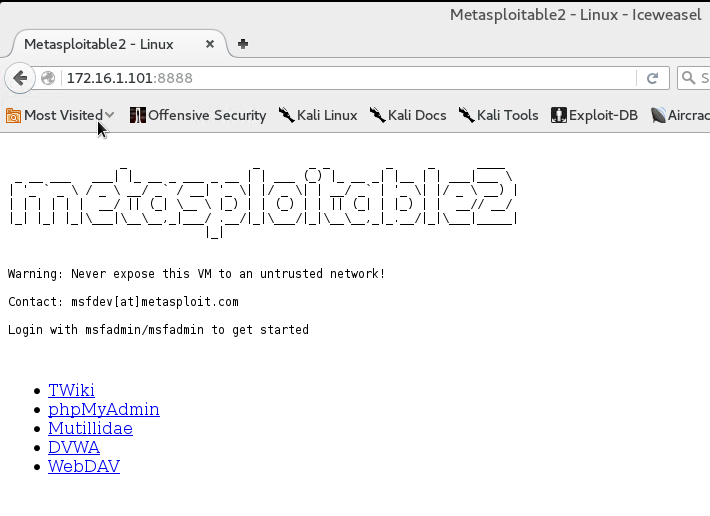
Now that we have a proxy established on our beachhead, all traffic directed to the compromised host on port 8888 is redirected over IPv6 to the internal target on port 80. Connecting to the DMZ target on port 8888 with our web browser reveals a web application running on the internal target.
Command Breakdown
On pivot location:
netsh interface portproxy add v4tov6 listenport=8888 listenaddress=0.0.0.0 connectport=445 connectaddress=2000::1:21f7:fe55:df97:375e
1. netsh - Command line tool for manipulating network interfaces
2. interface - Allows a user to manipulate an interface's contexts (TCP/IP v4/6)
3. portproxy - Establishes a proxy between IPv4 and IPv6 networks and applications.
4. add - Adds an interface to the machine
5. v4tov6 - Translate received IPv4 traffic to IPv6
6. listenport - port to listen on
7. listenaddress - address to listen on
8. connectport - port to connect to
9. connectaddress - address to connect to
Netsh also allows a user to forward traffic within the same host. This may be helpful in the case of NAT where a firewall device permits one port inbound but you need to target a service listening on another port. This case often exists in the case of DMZ webservers where HTTP (port 80) is allowed inbound, but traffic from the MySQL or MSSQL databases (port 3306/1433) is restricted.
netsh IPv4 port to another IPv4 port on the same host:
netsh interface portproxy add v4tov4 listenport=9999 listenaddress=0.0.0.0 connectport=445 connectaddress=172.16.1.101
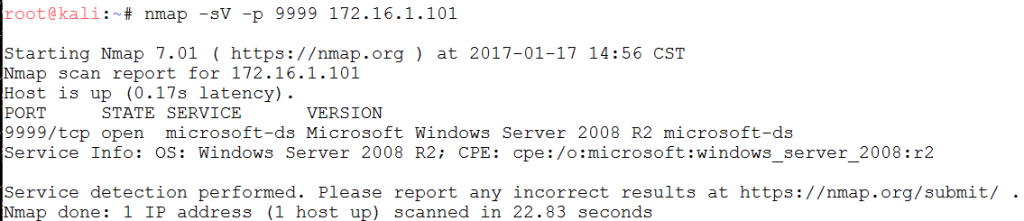
To verify that the portproxy is performing correctly we can Nmap port 9999 and observe the SMB (port 445) response traffic. Nice!
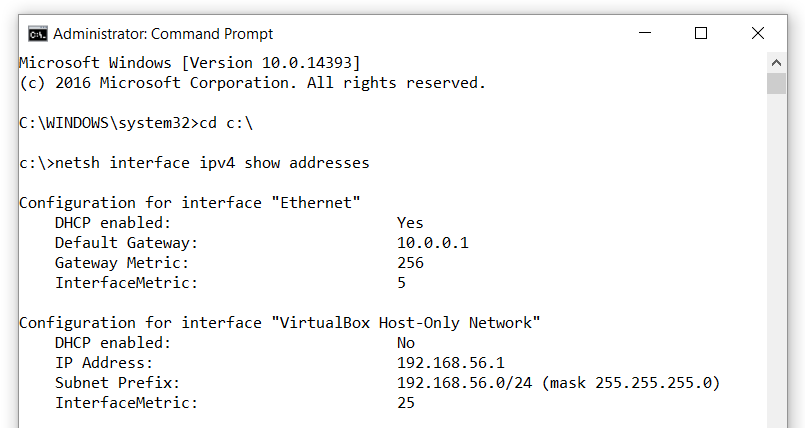
Bonus - Netsh ipconfig
The Windows ipconfig command provides network interface configuration details, but not always in the most convenient fashion. Netsh provides an alternative method.
netsh ipconfig:
netsh interface ipv4 show addresses
Additionally, netsh also provides a remote administration functionality if the Windows Remote Registry Service is running.
Anywhere with IP reachability to target machine:
netsh -r 192.168.1.103 -u entsim\administrator -p P@ssw0rd!
-r - The remote machine to connect to
-u - An administrator's username
-p - password
If netsh successfully connects, users may use an interactive netsh prompt to work with netsh as if they had shell on the target!
Print Your Own:
Get all of the CMD.exe tips from the SANS Pen Test Poster: "White Board of Awesome Command Line Kung-Fu!"
.png)
PDF: board-elements-kung-fu.pdf
Matthew Toussain
https://twitter.com/0sm0s1z


