
If Windows Management Instrumentation (WMI) is the Matrix then its console (WMIC) is Neo.

WMI is the Microsoft variant of Web Based Enterprise Management (WBEM) and Common Information Model (CIM). Essentially, it forms the connective tissue that defines application specific characteristics to enable cohesive interactivity between systems from differing sources. For the information security practitioner, WMI provides a mechanism to query an underlying system with a massive amount of capability and information built in. In this post we explore the robust set of features available within WMIC.
Methods Covered in this Section
wmic to get a full listing of the running processes:
wmic process list full
wmic print to a HTML formatted list of processes:
wmic /output:wmic.html process list full /format:hform
wmic query running services:
sc query type= service
wmic startup programs:
wmic startup list brief
wmic remote command execution:
wmic /node:10.0.0.1 /user:Administrator process call create "cmd.exe /c calc.exe"
The wmic process list full command displays all the information available for a process. Output data here is substantial and frequently overwhelming. Here is what the output (for one process) looks like:
wmic to get a full listing of the running processes:
wmic process list full
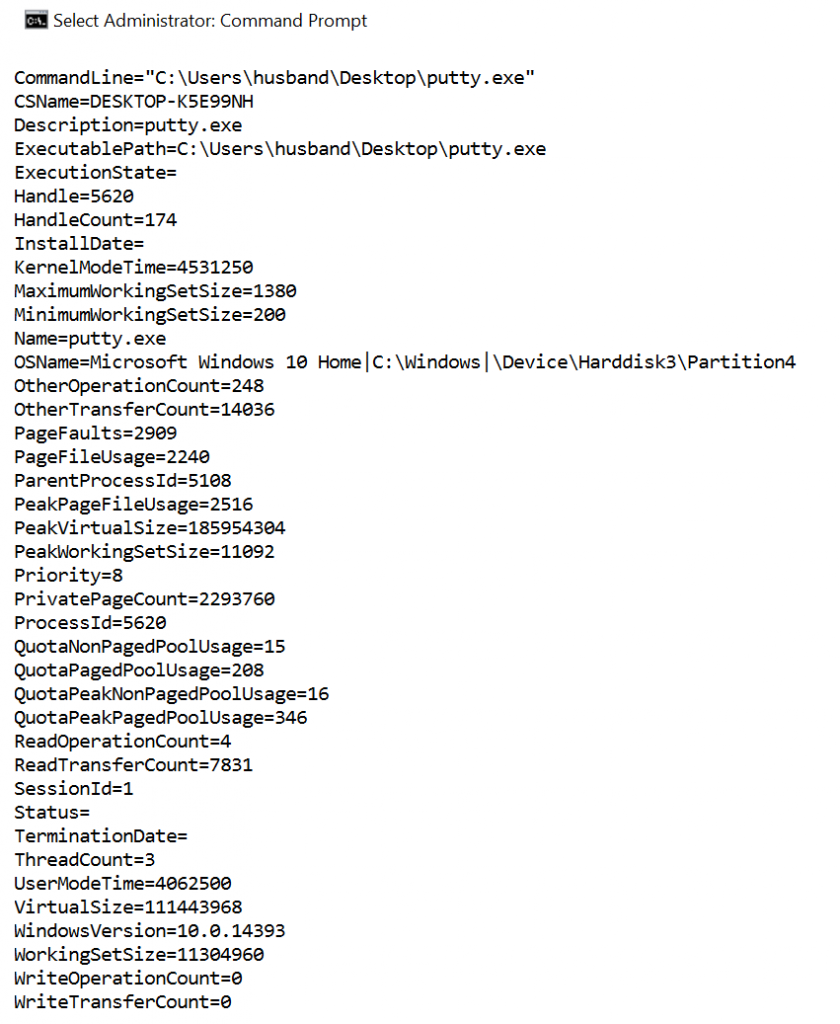
From the information listed, the key fields that may require additional investigation include:
1. CommandLine - If run with any options, for example nc -l -p 4444, it would appear here.
2. ExecutablePath - This is where the binary executes from
3. ParentProcessId - At times there may be a child/parent relationship which may be exploited
4. ProcessId - The PID of the process
Process list full provides an excessive amount of data. Data handling is advised. Consider leveraging more or storing stdout into a text file:
wmic process list full | more
wmic process list full > output.txt
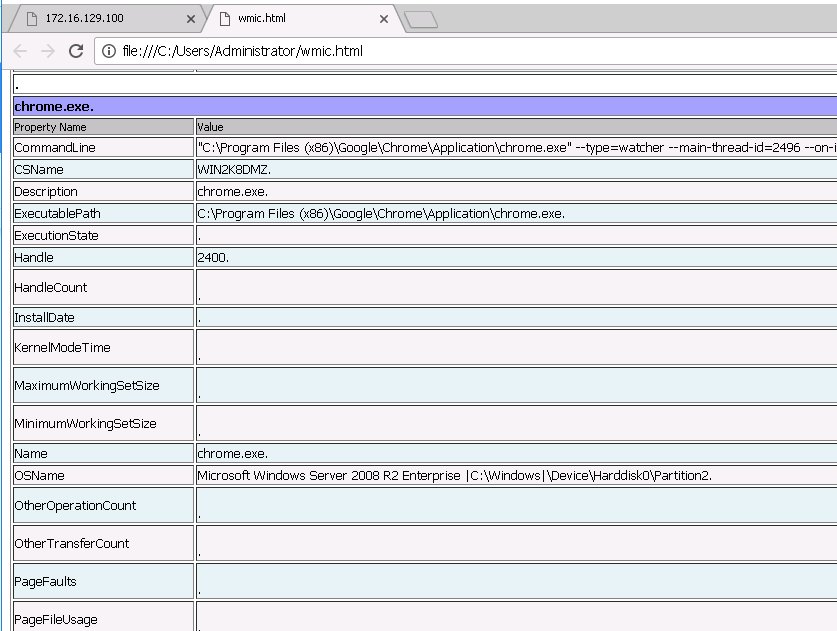
It is also possible to format wmic output as HTML:
wmic print to a HTML formatted list of processes:
wmic /output:wmic.html process list full /format:hform
Command Breakdown
wmic process list full
1. wmic - Windows Management Instrumentation Command-Line
2. process - WMIC can work with virtually all aspects of a system. This tutorial only covers processes, but WMIC displays a full list of potential objects with wmic /?
3. list - List all of the processes within the process object
4. full - List all aspects of the process. Different display options are available including brief, instance, IO, and many others. Each displays a different subset of process information.
wmic /output:wmic.html process list full /format:hform
1. /output:wmic.html - Print the output of WMIC to an HTML file
2. /format:hform - Options include table, list, csv, xml, htable, and hform. hform prints the WMIC output in HTML format.
Bonus - Services, Autoruns, and Remote Command Execution, oh my!
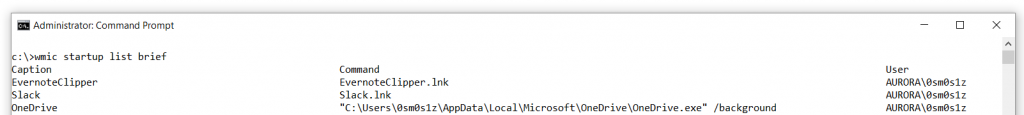
Wmic is a critical component in any information security professional's bag of tricks, and we would be remiss not to discuss some of its extended features. For instance, a particularly useful technique for detecting network intrusions is to target common persistence mechanisms utilized by threat actors. Wmic can be used to quickly identify applications that run on system reboot.
wmic startup programs:
wmic startup list brief
wmic remote command execution:
wmic /node:10.0.0.1 /user:Administrator process call create "cmd.exe /c calc.exe"
Finally, when moving laterally, wmic provides a tried and true method for leveraging network credentials to perform remote command execution and establish sessions on an endless stream of hosts. In this fashion, wmic functions much like psexec, but it has the added benefit of existing by default on all windows operating systems from Windows Me and NT onwards.
Conclusion
WMIC is a great tool for moving within and manipulating the environment with native capability. Not only is it incredibly powerful, but will likely draw less attention than many other more distinct and well known pentesting tools. Only the shallowest depths of its functionality are explored here, but the potential is nearly endless. Try, explore, and learn!
Print Your Own:
Get all of the CMD.exe tips from the SANS Pen Test Poster: "White Board of Awesome Command Line Kung-Fu!"
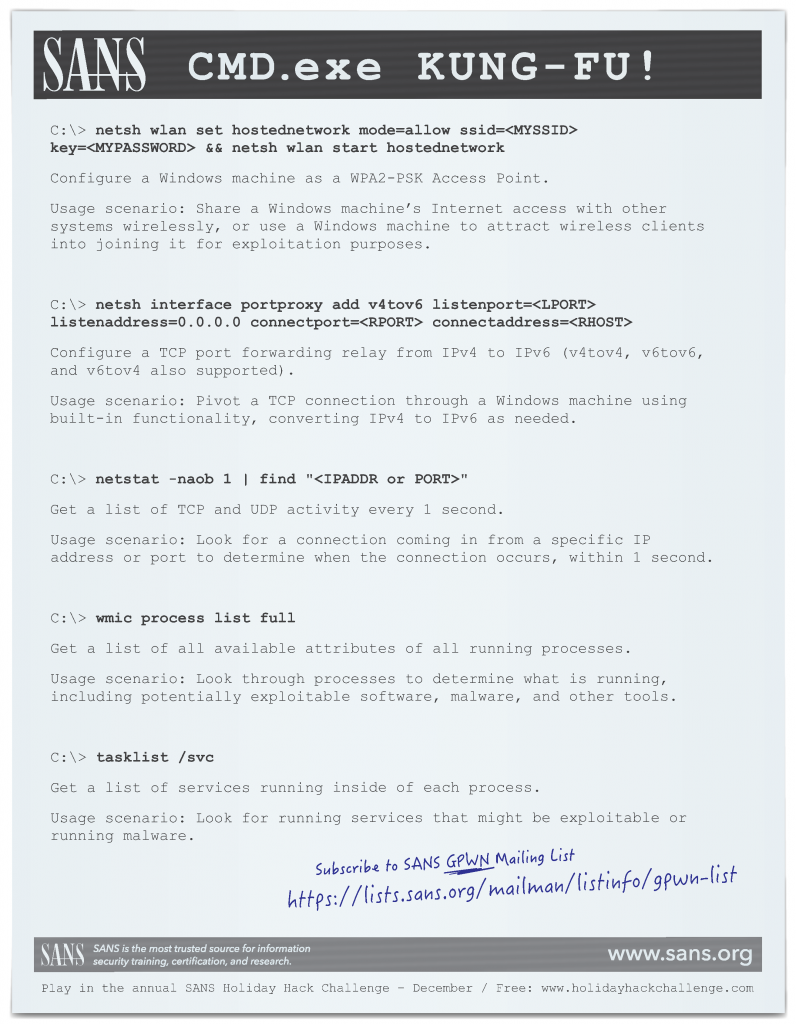
PDF: board-elements-kung-fu.pdf
Matthew Toussain
https://twitter.com/0sm0s1z



