
"Get-ChildItem" may be the most horrific way to express the concept of listing the contents of a directory, but fortunately PowerShell has aliases: "gci", "dir", and "ls!" That's right PowerShell has solved the antediluvian ls/dir wars by aliasing both to a magical, if nonsensical, yet grammatically complete, sentence. Because PowerShell cmdlets are steadfast in their dedication to objects we can avoid much of the string comparison troubles that are an inherent tribulation when working in other shells, like bash. Let's take a moment to examine just how simple it can be to find "juicy" files on target systems.
Methods Covered in this Section
Looking for files by name with ls:
ls -r -file -filter *secret*
Using ls to find files containing specific string:
ls -r c:\ -file | % {select-string -path $_ -pattern mypassword}
The true value proposition of a penetration test is the demonstration of the cause and effect relationship between vulnerability and business risk as demonstrated by exploitation. Importantly, exploitation does not end at compromise that is where it begins to pick up steam. In a post-compromise scenario a constant challenge for security testers is management of an organization's worth of data.
What kinds of data are we even looking for?
While ever situation is different, our data harvesting goals are generally motivated by two general desires:
- Gaining more access
- Exfiltration of critical data
In the first case our goal is to target specific files on the system that can result in extending our intrusion campaign. Useful data acquired here may allow us to escalate privileges from user to administrator or to gain access to other targets by moving laterally. Typical files to target may include:
| Filename | Purpose |
| Passwords.txt | Users often create password files as reminders. |
| wp-config.php | WordPress configuration file. Stores database passwords. |
| key3.db / logins.json | Password file for the Firefox web browser. |
| <custom>.sh | Administrators often store plaintext passwords in automation scripts |
| fstab | The fstab may contain passwords to mounted samba shares |
| *.pst | Users may email passwords around. These can often be found in .pst files |
Alternatively, we might find ourselves near the end of our journey. It's time to begin harvesting critical data sources. Names and contents of these files can vary wildly based on the business of the target organization. Having a wide degree of flexibility in search queries can prove particularly helpful in these cases.
Looking for files that match a name we are interested in is the most straightforward use case, but what happens if we are not entirely certain how the user decided to spell the file? Is it passwords.txt, pass.txt, Password.lst? Using the wild card operator (*) we can account for each of these use cases. We may also need to use the -r option to enable recursion. This allows us to walk our way down the directory structure looking in every folder as we go.
Looking for files by name with ls:
ls -r -file -filter *secret*
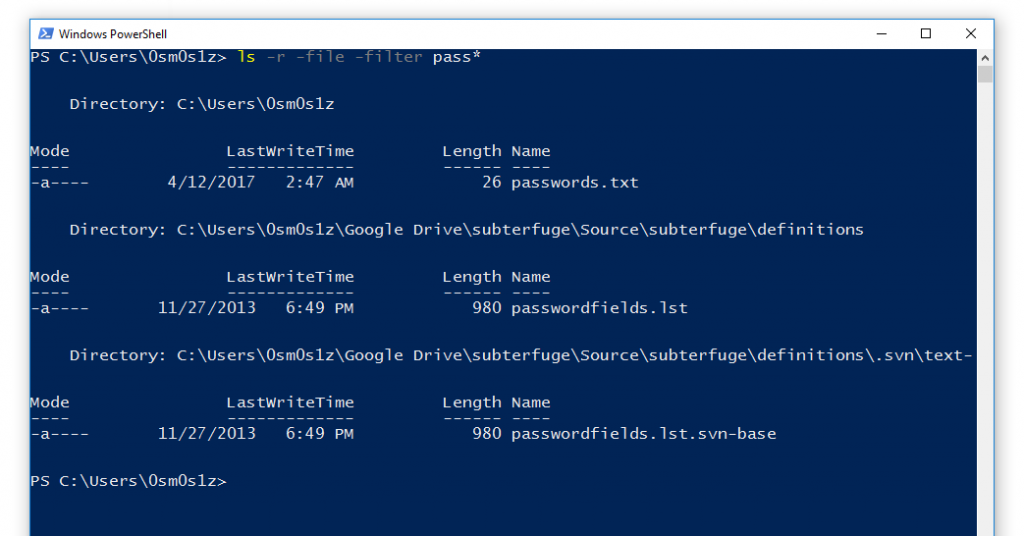
Command Breakdown:
ls - Short for list. This is a utility for listing the contents of a file system.
-r - Recurse all directories in the target folder
-file - Only list files
-filter *secret* - Filter string (criteria to match)
A significant limitation of the above use case is its surface level approach. Diving deeper we can have PowerShell programmatically evaluate the contents of each file to identify interesting strings.
Using ls to find files containing specific string:
ls -r c:\ -file | % {select-string -path $_ -pattern mypassword}
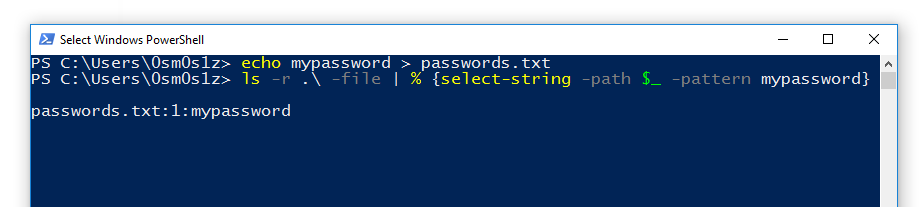
Command Breakdown:
In this command we leverage the | (pipe) operator to direct the output of our ls command into the % {} loop. In PowerShell % is an alias that simply means "for each object". Because ls outputs individual objects for each file we can evaluate them this way individually. The $_ operator is PowerShell's way of saying "current object". In this case we are essentially creating a list of files with ls -r and running select-string against each one of them in order to search for the -pattern "mypassword".
Conclusion
Using other PowerShell cmdlets like Invoke-Command could enable even more efficiency by allowing us to execute these search commands against a list of hosts! PowerShell can be a bit mind bending when first encountered, but its predilection for near-human-readable syntax makes it a language that can be rapidly incorporated into any pentester's toolbox.
Matthew Toussain
https://twitter.com/0sm0s1z


