SEC595: Applied Data Science and AI/Machine Learning for Cybersecurity Professionals


Experience SANS training through course previews.
Learn MoreLet us help.
Contact usBecome a member for instant access to our free resources.
Sign UpWe're here to help.
Contact UsAs ransomware attacks increase in number and severity, even the most advanced security systems can be compromised. Here is what you can do to prepare.

Cyber criminals are targeting every type of organization, from small businesses to large enterprises. Many people tend to believe that ransomware actors only target large enterprises and/or critical systems; unfortunately, the opposite is true. If you have internet-connected devices, you are at risk of a ransomware attack.
Some ransomware actors target very specific victim environments, others focus on specific verticals and/or sectors, and yet others take a more opportunistic approach. These latter types of actors utilize a wide-net approaches, sometimes even purchasing access to victim environments from initial access brokers (IABs), whose role is to break into a wide variety of networks to later re-sell this access to threat actors such as ransomware actors.
Ransomware attacks in 2022: An overview
Tracking all ransomware incidents is impossible. No one on the planet knows exactly how many ransomware attacks have occurred over time or even within a given year. Some victims negotiate directly with the threat actor and provide a ransom payment before the rest of the world becomes aware of the situation. Many incidents are handled in private with non-disclosure agreements (NDAs) signed by all parties involved. In these situations, the consulting groups involved are barred from discussing specifics.
Though even coming close to tracking all ransomware attacks is not possible, some groups release reports that contain statistics along with techniques, tactics, and procedures (TTPs) of the various groups involved. The reports you will find released to the public are often written through the lens of the firm or group writing the report. For the purposes of this article, we have opted to use statistics from ecrime.ch, a paid threat intelligence service that aggregates and reports on ransomware data leak sites (DLS). These sites are run by the ransomware operators themselves.
Based on intelligence from ecrime.ch, ransomware actors made over 2,600 posts in 2022 related to their victims. These posts included victim identification, while some even provided sample files and/or notes concerning full data dumps (typically as a result of non-payment). Within this data set, the following were the top 10 sectors in terms of compromise, in order:
According to Coveware’s April 28th article concerning ransomware attacks in Q1 2023, the two most common company sizes impacted by ransomware were those with:
However, companies with employee counts between 1 to 10 served as 6.3% of impacted companies. That number is not insignificant and should serve as a warning to organizations who think to themselves, “Ransomware only hits enterprises… so we should be safe.”
Consulting firms, insurance agencies, and law firms alike see small businesses, such as dentist offices and small accounting agencies to name a few, being hit with ransomware. The threat is not only relegated to larger companies. If you have network infrastructure on the internet, you are a viable target.
----
Should you be interested in free sites similar to ecrime, we recommend the following resources:
Ransom Watch provides a group index, recent DLS posts, group profiles, and statistic/graph pages: https://for528.com/ransomwatch.
Ransom Look provides a group index, forum and market links, a listing of data leaks, telegram messages, and statistic/graph pages: https://for528.com/ransomlook. The team also maintains a GitHub repo that you can review: https://for528.com/ransomlook-gh.
Ransom.Wiki focuses more on allowing users to search for recent victims and/or ransomware groups by name: https://for528.com/rwiki.
DarkFeed provides several resources for identifying ransomware DLS and blog information: https://for528.com/darkfeed.
How serious is the threat of a potential ransomware attack?
During the development of our SANS Forensics “FOR28: Ransomware for Incident Responders” course, we experienced a real-world, eye-opening attack. To generate the data for our labs and capture the flag (CTF) event, we created multiple network ranges. One night, I left one of our ranges in a vulnerable state, purposefully. The servers in the range had Remote Desktop Protocol (RDP) open with insecure passwords for no more than 8 hours while I slept.
I joked that I wanted to give a real threat actor a chance to brute-force one of the Administrator account passwords. When I awoke, I found that not only had the range been breached, but the entire environment was ransomed! We could not have asked for a better, real-world example of just how serious the threat is… we’re up against a monster!
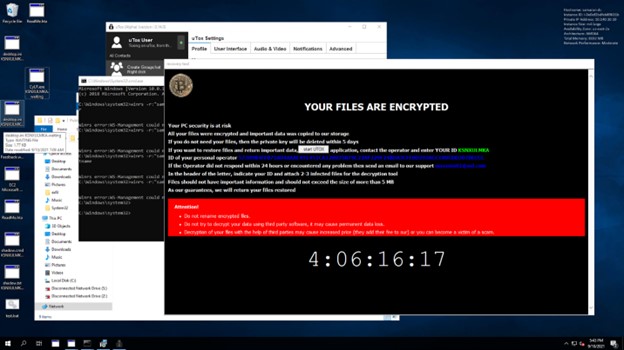
Figure 1. One of our network ranges after being ransomed after being vulnerable for no more than 8 hours.
IInitial Access – How the Ransomware Actors Are Getting In
The top three methods used to obtain access to victim networks in ransomware attacks, along with some prevention/mitigation-related questions, follow:
Some ransomware groups carry out their own attacks (e.g., Vice Society), while some use affiliate groups as part of their Ransomware-as-a-Service (RaaS) model (e.g., Lockbit 3.0). Regardless, entry into victim networks often comes by way of the three above methods. Initial entry may not be direct via the operator or affiliate group. Rather, access may be purchased and/or leased via an Initial Access Broker, or IAB, as noted earlier.
The IAB’s role is literally in its name: to broker initial access to victim networks. Such groups work around the clock, literally, to breach victim environments using the above three methods. Once in, they sell, auction, or trade access to other threat actors, including ransomware actors. That’s the threat we’re up against: Entire teams of humans are using well-known, tried-and-true attack methods constantly – And they work all too often.
To learn more about the IAB landscape, see https://for528.com/iab.
Protecting Your Organization
What is the best way to protect me and my organization from ransomware?
The only way to stay safe from ransomware is to be prepared. As ransomware attacks increase in number and severity, even the most advanced security systems can be compromised. However, there is one thing that can help you fight back: train your team!
One of the most important things you can do as an organization is to train your cyber team on how to recognize the signs of a possible attack, what steps they should take, and how they can help prevent it from happening in the first place. A well-trained team will be able to identify what ransomware attacks look like, and thus will be able to help you work out a plan for responding if it's detected on your network.
For example, how might you determine that an identified actor within your environment may be a ransomware affiliate? What signs do you look for? Should you make this determination, what steps would then be appropriate? You do not respond to a potential ransomware attack the same as you do an Advanced Persistent Threat (APT). Do you know the difference? If not, it’s time to prepare you and your organization.
A recent study found that organizations that have trained their IT or cybersecurity teams are 28% less likely to experience a breach than those who haven't. This makes sense: when you know what you're doing, you can act quickly and efficiently when the time comes.
If you're a business owner, you know that staying on top of the latest in cybersecurity can feel like an uphill battle. But there are ways to ensure that your business stays secure from the dangers of ransomware and other forms of malware.
Here are five tips for staying safe:

Learn more about the course at www.sans.org/FOR528


Ryan Chapman has redefined ransomware defense through hands-on leadership in major incidents like Kaseya and by arming thousands with proactive threat hunting tactics now standard across the industry.
Read more about Ryan Chapman