I have encountered a number of people who are dealing with Windows Mobile Devices in cases and need to recover text messages and e-mails, including deleted items. For the most part, the contents of such messages are stored in the cemail.vol database (MMS attachments are treated separately). This file can be acquired from a Windows Mobile Device as described in the Acquiring Data from Windows Mobile Devices blog entry.
The cemail.vol file is a proprietary Microsoft format and there are limited tools for parsing this format directly. In some situations, viewing this file using a hex viewer will reveal deleted messages and other items that are not acquired using common forensic tools. Although XACT from Microsystemation has the ability to interpret cemail.vol databases automatically, forensic practitioners with limited budgets are seeking lower cost solutions.
One effective approach to interpreting this type of database using freely available software is to mount a copy of the acquired cemail.vol file into a Windows Mobile Emulator and use the itsutils package to navigate the database and extract the desired items. The pdblist utility in the itsutils package can dump many databases on a Windows Mobile device.
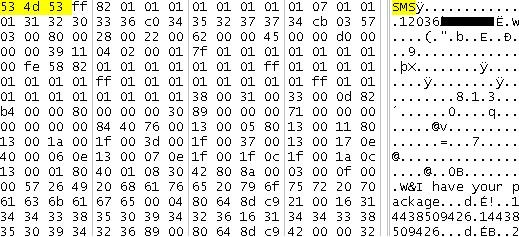
To illustrate, consider the following message "I have your package" in an acquired cemail.vol file viewed with a hex viewer.
Mounting the Acquired File in Window Mobile Emulator
First, it is necessary to mount the acquired cemail.vol file in a Windows Mobile Emulator. Although it is not necessary to use an Emulator that exactly matches the evidentiary device, some similarity is recommended. There are a number of emulators included in Visual Studio. Additional emulators can be downloaded from the Microsoft Web site.
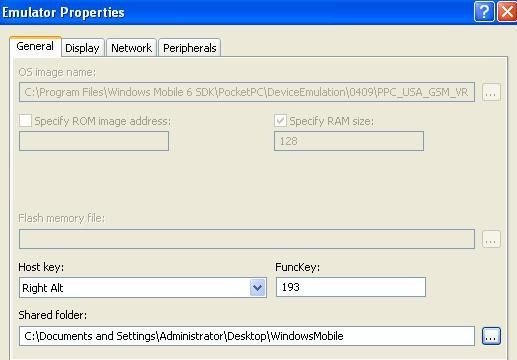
Once a suitable Windows Mobile Emulator has been selected, it is necessary to configure it to access the folder on the examination computer where the acquired cemail.vol file is stored. The following screenshot shows the shared folder being configured to point to C:\Documents and Settings\Administrator\Desktop\WindowsMobile, which is then accessible under the volume named "Storage Card" within the Emulator.
After launching and configuring the desired Windows Mobile Emulator, it is necessary to create a conduit that itstutils uses to send commands to the Emulator by establishing an ActiveSync connection. You achieve this by opening the Device Emulator Manager in Visual Studio (under the Tools menu), then right-clicking the selected Emulator and selecting Cradle. In addition, within ActiveSync connection settings it is necessary to allow DMA connections.
Useful Commands
After an ActiveSync connection has been established with the Emulator, you can access its contents using components of the itsutils package. For our purposes, the pdblist utility can list accessible volumes, including the virtual "Storage Card" that contains the cemail.vol file to be examined as shown here:
C:\Tools\itsutils>pdblist -v
volume {00000000-0000-0000-0000-000000000000} \Documents and Settings\default.vol
volume {40684a00-994b-f835-7742-f7f435ba8d2b} \ReplStorVol
volume {15005d00-12f3-a6e9-76e8-595b9d742cc8} \mxip_notify.vol
volume {65ca7a00-7d53-6505-5671-0b1908d7e6eb} \cemail.vol
volume {225c1b00-e193-8a1a-785f-68f818cf3dd0} \Storage Card\cemail.vol
volume {c479de00-e4b7-9037-1352-dced359be0ad} \mxip_system.vol
volume {d071d100-fb8f-1505-782c-e71b23e00165} \mxip_lang.vol
More importantly from a forensic examination perspective, pdblist can list components of databases that are accessible via the emulator as shown here:
C:\Tools\itsutils>pdblist -D
volume {225c1b00-e193-8a1a-785f-68f818cf3dd0} \Storage Card\cemail.vol
oid310000c0: dbase F00000017 T00000000 0 356 ... 'fldr31000095'
ORDERING: 0e060040:00000000 0c1a001f:00000002 0037001f:00000002 001a0013:00000000
[cut for brevity]
oid38000079: dbase F00000017 T00000000 1 484 ... 'fldr31000028'
ORDERING: 0e060040:00000000 0c1a001f:00000002 0037001f:00000002 001a0013:00000000
oid32000087: dbase F00000017 T00000000 0 356 ... 'pmailAttachs'
ORDERING: 81000013:00000000
oid37000081: dbase F00000017 T00000000 0 356 ... 'fldr32000023'
ORDERING: 0e060040:00000000 0c1a001f:00000002 0037001f:00000002 001a0013:00000000
oid34000071: dbase F00000017 T00000000 3 800 ... 'fldr31000026'
ORDERING: 0e060040:00000000 0c1a001f:00000002 0037001f:00000002 001a0013:00000000
[cut for brevity] oid33000029: dbase F00000017 T00000000 0 356 ... 'pmailVolumes' oid3b000017: dbase F00000017 T00000000 53 3768 ... 'pmailNamedProps' ORDERING: 8300001f:00000000 83010013:00000000 oid30000009: dbase F00000017 T00000000 12 1020 ... 'pmailMsgClasses' ORDERING: 8300001f:00000000 83010013:00000000 oid30000007: dbase F00000017 T00000000 0 356 ... 'pmailOldTables' oid30000003: dbase F00000017 T00000000 6 1824 ... 'pmailMsgs' ORDERING: 800c001f:00000000 0e090013:00000000 00150040:00000000 oid30000001: dbase F00000017 T00000000 21 3052 ... 'pmailFolders' ORDERING: 0e090013:00000000 [cut for brevity]
The same utility can be used to dump a particular object by name. Working through the objects listed in the above pdblist output, the same text message shown earlier in a hex viewer is revealed in fldr31000026 as shown below using the pdblist command in this manner. Additional details like the date-time stamp associated with the message are also displayed along with other text messages.
C:\Tools\itsutils>pdblist -d fldr31000026
3f000089 ( 284 12 2)
8005 T13 L0000 F0000 UI4 838860938
8011 T13 L0000 F0000 UI4 3
001a T13 L0001 F0000 UI4 822083599
003d T1f L0000 F0000 STR [00169898]( 0) ''
0037 T1f L0000 F0000 STR [0016989c](19) 'I have your package'
0e17 T13 L1ebe F0000 UI4 262144
0e06 T40 L0000 F0000 FT 2009-04-22 21:01:47.000
0e07 T13 L0004 F0000 UI4 33
0c1f T1f L0000 F0000 STR [001698c4](11) '14438509426'
0c1a T1f L0000 F0000 STR [001698dc](11) '14438509426'
8001 T13 L0001 F0000 UI4 1056964745
3008 T40 L9b35 F0000 FT 2009-04-22 21:01:47.000
3000008e ( 284 11 78)
8005 T13 L0000 F0000 UI4 973078668
8011 T13 L0000 F0000 UI4 5
0e17 T13 L0001 F0000 UI4 0
001a T13 L0000 F0000 UI4 822083597
003d T1f L0000 F0000 STR [00169888]( 0) ''
0037 T1f L1ebe F0000 STR [0016988c](13) 'meeting place'
0e08 T13 L0000 F0000 UI4 9284
0e06 T40 L0004 F0000 FT 2009-04-22 21:05:45.000
8001 T13 L0000 F0000 UI4 805306510
0e07 T13 L0000 F0000 UI4 268501033
3008 T40 L0001 F0000 FT 2009-04-22 21:05:45.000
3e0000a1 ( 284 12 72)
8005 T13 L0000 F0000 UI4 855638176
8011 T13 L0000 F0000 UI4 7
0e1b T13 L0001 F0000 UI4 0
8012 T13 L0000 F0000 UI4 0
001a T13 L0000 F0000 UI4 822083597
003d T1f L1ebe F0000 STR [00169898]( 0) ''
0037 T1f L0000 F0000 STR [0016989c]( 8) 'codeword'
0e08 T13 L0004 F0000 UI4 17015
0e06 T40 L0000 F0000 FT 2009-04-22 23:56:46.000
8001 T13 L0000 F0000 UI4 1040187553
0e07 T13 L0001 F0000 UI4 268501033
3008 T40 L006d F0000 FT 2009-04-22 23:56:47.000
Additional Evidence
Be aware that Windows Mobile creates temporary files in various locations where you may find useful information depending on what you are seeking (e.g., e-mail, MMS). We cover Windows Mobile in the SANS Mobile Device Forensics course, and we delve into cemail.vol and other useful data sources on these devices.
Eoghan Casey is founding partner of cmdLabs (http://www.cmdlabs.com/) , author of the foundational book Digital Evidence and Computer Crime, and coauthor of Malware Forensics. He has been involved in a wide range of digital investigations, including network intrusions, fraud, violent crimes, identity theft, and on-line criminal activity. He has testified in civil and criminal cases, and has submitted expert reports and prepared trial exhibits for computer forensic and cyber-crime cases.




