SEC595: Applied Data Science and AI/Machine Learning for Cybersecurity Professionals


Experience SANS training through course previews.
Learn MoreLet us help.
Contact usBecome a member for instant access to our free resources.
Sign UpWe're here to help.
Contact UsWeak Security Program, Unprotected Systems, and Poor Detection & Response

This is Part 2 of 4. Read the other parts here:
This blog series is based on the REKT Casino Hack Assessment: Transformational webcast series, which you can view starting here.

To summarize what happened: Rekt Casino suffered a ransomware attack that resulted in a breach. The Ransomware came in over email due to no spam filtering, phishing or malware protections on the email server. The initial malware was able to beacon out to the attackers because there were no outbound firewall rules. Memory dumps showed the attackers were using PSEXEC, PowerShell and an unknown executable. RDP connection were observed taking place on the network using the domain admin account – domain admin had been compromised.
In reviewing Rekt Casino and how it parallels to much of what I teach in LDR512: “Security Leadership Essentials for Managers”, it brought back memories of questions I would get from my students. Some students who took my class came from organizations came from security programs that were mature and time tested, while others were just in the infancy of building their program. Yet I noticed a theme with many of the questions. What was being asked showed that no matter what stage of program building they were in, they were nervous that their program “wasn’t enough”. For example, they were worried about getting the buy in they needed to have their programs succeed or that their program was not comprehensive enough to protect against all the advanced ways bad actors would circumvent even the best security programs. All of these questions came to a head when I reviewed the ransomware event that caused Rekt Casino to not only fall victim to a ransomware attack, but also not have the basic building block of a security program to identify, protect, detect, respond and recover (I am sure you hear your NIST Cybersecurity Framework ears ringing as you read that).
While there were many downfalls of this event, there were a few key areas I wanted to focus on that Rekt Casino could have done much better on. However, I don’t think that it is just Rekt Casino that could have done better in these focus areas. Everyone who has the opportunity to take LDR512 will be able to put their “management hat” and think back to the state of their security programs back at their organization. Even though the ransomware attack against Rekt Casino is one of the many worst-case scenarios that could happen to an organization, as Winston Churchill famously stated
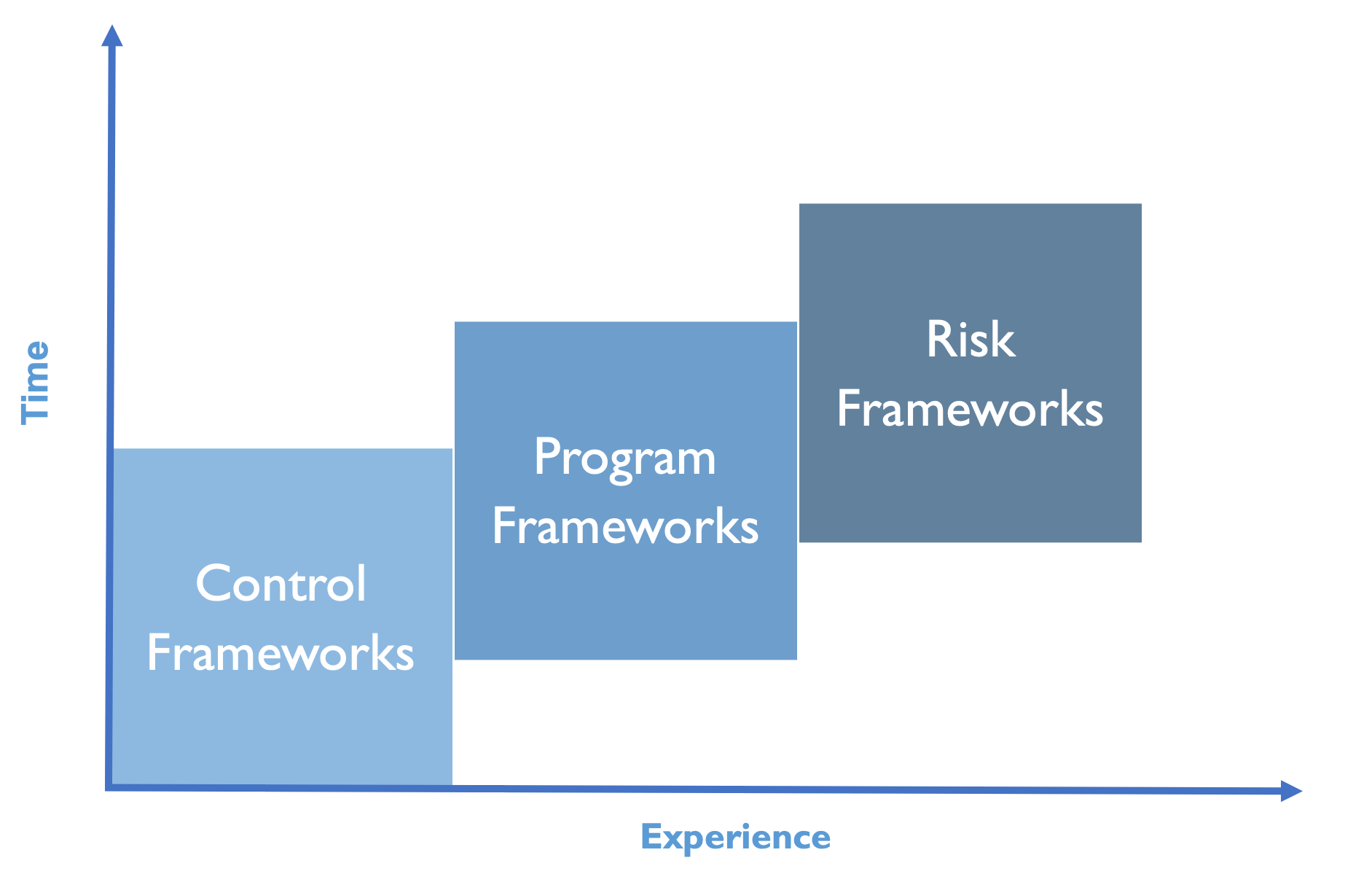
Rekt Casino went into this security event with no security frameworks to build their program against. In LDR512, we talk about the build up of the Control, Program and Risk frameworks as the bedrock of any security program to be like telling a story. However, in order to tell a story effectively, you need to know the basics to build up to something special.
Control Framework | The words |
Program Framework | The sentences |
Risk Framework | The story |
Rekt Casino did not even have the words, or the Control Framework in their case, to build up their program. No wonder why they had so many other failures in this ransomware event along the journey. If they did not have the words, they certainly did not have the ability to make the sentences of their story, or the Program Framework. If the words and sentences, or the Control and Program frameworks were not in place, they certainly would not have been able to get to the end goal, the Risk framework, or the story. We talk about these three frameworks on day one because they are so critical to the success of all of the other variables to the story we talk about for the next four days. As managers, we can always think back to day one of LDR512 as the building blocks for the perpetuity of your program at your organization.
Making others in your organization aware that they are part of the security program just as much as the security team is the job of the security team. Rekt Casino did not empower users to be an extension of the eyes and ears of the future security organization. Bad actors know many companies fall short on empowering users to be an extension of their team. Not surprisingly, bad actors also use this weak spot to wiggle their way into an organization. As a manager, you have an incredible opportunity to evangelize not only your security program, but also to make others away of all of the good work you and your team are doing to help protect your organization from catastrophic events such as a ransomware attack. In LDR512, we learn about bringing other functional areas from the organization into the conversation to help build awareness together. Security awareness can and should be a powerful message to your organization that you take securing your organization seriously. Rekt Casino would have greatly benefited from empowering their users.
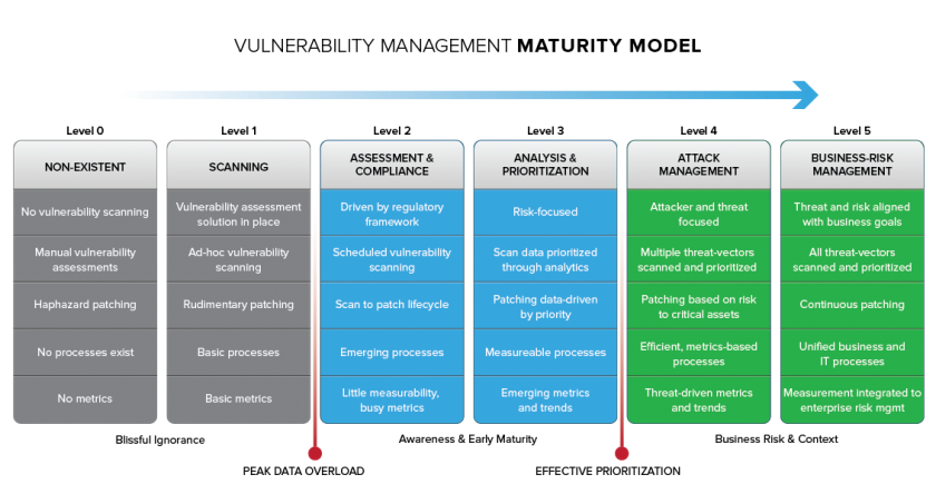
Many ransomware variants use unpatched vulnerabilities in an organization’s infrastructure to unleash their payload. From there, ransomware can and will have the ability to be incredibly detrimental to the organization. A strong vulnerability management program provides the opportunity to address these identified risks through a series of prioritizing vulnerabilities, maturing the program and patch management practices. In LDR512, we measure maturity on a numerical scale. Rekt Casino could easily be classified has having an immature vulnerability management program given much of the immaturity in other areas. I am sure you could agree with me Rekt was to the far left of the maturity scale (Level 0):
Vulnerability management also allows managers to put their “management hat” on and interact and grow with other functional areas of the organization such as remediation teams, application owners and business owners. As managers, we allow others in our organization to help them better assess their risks through the vulnerability management program. It is a powerful tool in the management arsenal that should be used to not only help reduce vulnerability risks in your organization, but also communicate the importance of the security program you are managing. Rekt had a great opportunity to do the same internally.
Retk Casino was missing key tools to help identify the ransomware in the organization. In LDR512, we go through a full list of tools as managers you should know about and evaluate if they fit into your security program back at your organization. Three tools that I highlighted missing from Rekt Casino and just one of their benefits are included below:
Cloud Based Antivirus | Update signature files for all endpoints even if they are off the network |
File Integrity Monitoring | Detection of any changes to a file. |
Endpoint Detection and Response | Help an organization detect, contain, respond and recover from security incidents |
Toolsets help support the vision of the security program build from the frameworks we talk about in LDR512 on day one. Without the frameworks, these tools made sit dangerously dormant. As managers, we are empowered to not only identify what tools can help support our frameworks, but also to ensure they are used appropriately.
Lastly, Retk Casino fell woefully short on the response to the incident. In fact, some of Retk’s Information Technology staff reached out to another organization’s incident response department to help them work through this ransomware incident. That should make you sweat a little just reading that. However, as managers this provides us an opportunity to think about if we would have to do the same thing during a response in our organization. Building up your incident response function will pay dividends in the heat of the moment. Letting one party be an incident handler may allow the incident response team to focus on their technical response.
In LDR512, we talk about incident response in the “PICERL” model described below. I love focusing on “Lessons Learned” when teaching to my management students. Not only to lessons learned allow you to identify what can be improved, but it also reduces your changes of an event similar to this happening again. As a manager, it is one of the strongest responses after an incident and one that showcases to your organization you never want to go through an event like this again.

Retk Casino’s poor security posture is much more common than you may think. Even if the security program is mature, it does not mean a major even such as ransomware could not hit an organization. Retk showcases what even a few immature links in the cyber chain can do to an organization. In LDR512, we learn about many of these links and much more so that when you go back to your organization after the training is complete, you can put your “management hat” back on and lead your organization to where you are empowered to see it. “Never let a good crisis go to waste” will enable you as a manager to look back on this event like this in the future as the turning point to you and your program’s success in your organization.
Kevin Garvey is the US IT Security Manager for an international bank responsible for overseeing incident response, vulnerability management, cyber threat intelligence, as well as the security operations center (SOC). Previously, he worked at New York Power Authority, JP Morgan and WarnerMedia (formerly Time Warner). Kevin has always had a passion to hunt down the adversary and has loved tackling the risk and threat challenges his responsibilities have thrown at him. Kevin teaches SANS LDR512: Security Leadership Essentials for Managers. Read Kevin's full instructor profile here.


Kevin is the IT Security Manager for an international bank, responsible for overseeing incident response, vulnerability management, cyber threat intelligence, as well as the SOC. He has worked at New York Power Authority, JP Morgan and WarnerMedia.
Read more about Kevin Garvey