SEC595: Applied Data Science and AI/Machine Learning for Cybersecurity Professionals


Experience SANS training through course previews.
Learn MoreLet us help.
Contact usBecome a member for instant access to our free resources.
Sign UpWe're here to help.
Contact UsThe Verizon Data Breach Incident Report (VZ DBIR) is one of the security industries most respected annual reports on risk.

The Verizon Data Breach Incident Report (VZ DBIR) is one of the security industry's most respected annual reports on risk. For more than 15 years now the Verizon team has been publishing its data-driven report on the top risks that organizations face around the world. What makes this report so valuable is that the report is vendor neutral, is based on a global data set, and analyzes a broad range of risks, including not only deliberate cyber threat actors but other risks such as physical, malicious insiders, and simple human error (which is a much bigger deal than people realize).
The report is especially useful in that it is highly actionable, breaking down and categorizing risks by threat actors and their actions, which is why I recommend everyone make the report as part of their regular reading. With that said, let’s dive in and see what the 2024 report has to offer us. As always, I will be looking at this report from the human risk perspective.
This year’s report is based on 30,458 real-world security incidents, of which 10,626 were confirmed data breaches (a record high for breaches). VZ DBIR defines a breach as a type of incident where data has been compromised, which are often the most damaging type of breaches, as media, lawyers, and regulators get involved. Here are a couple of my key take-aways from the Executive Summary.
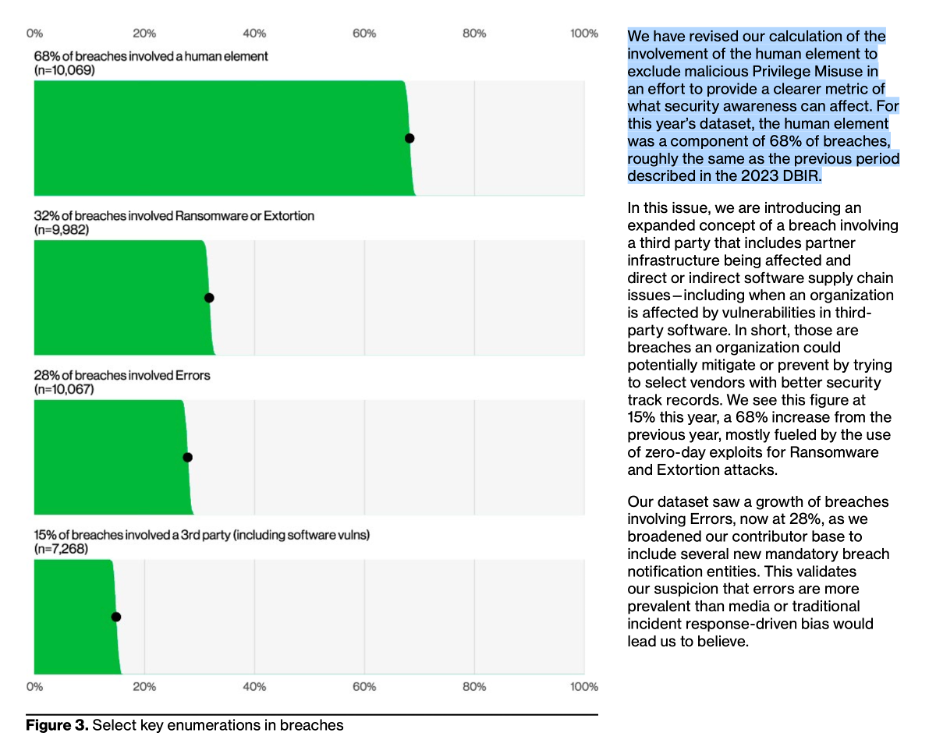
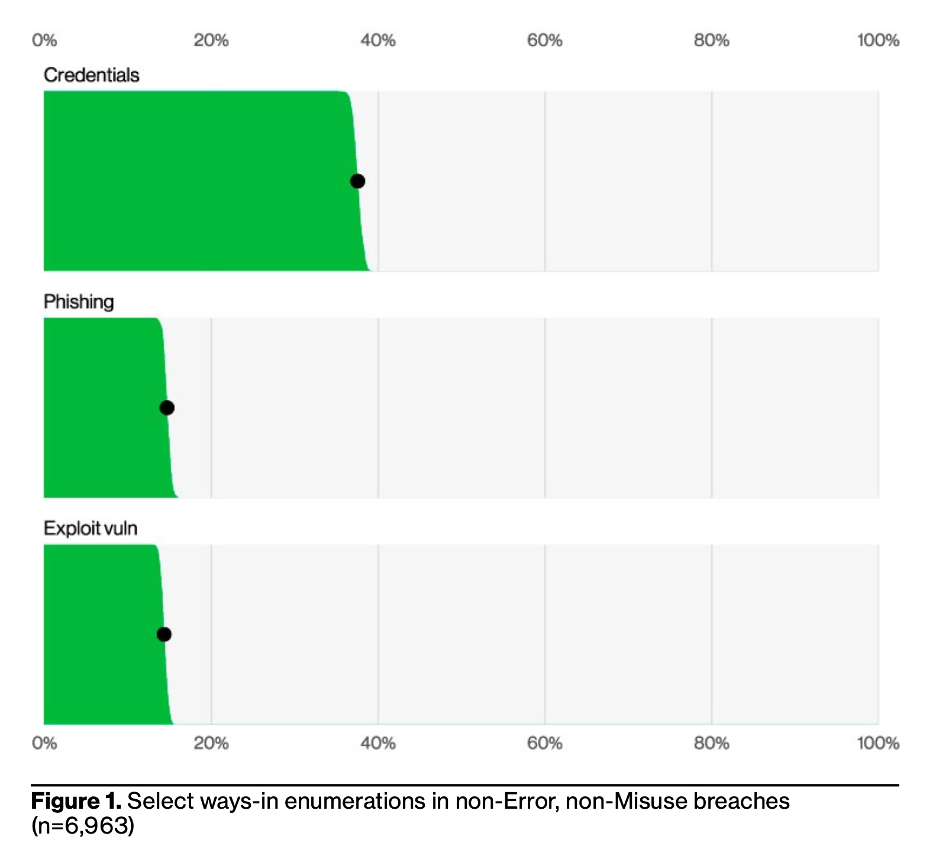
In Figure 1 below, we see the top three ways cyber threat actors are getting into organizations: credentials, phishing, and vulnerability exploiting. These are the same top findings from the past three years. I was intrigued to see that phishing seemed to be much lower percentage-wise compared to credential/account takeover. The VZ DBIR team explained that a huge percentage of credential stealing happens with phishing, but the VZ DBIR team often cannot prove how cyber threat actors got the credentials in the first place. Long story short, just as in the past three years, if you are focusing on human security, continue to focus on:
Phishing continues to be one of the biggest categories of phishing attacks, but what I found interesting in this year’s data set is that over 40% of successful social engineering attacks were Business Email Compromise (BEC)/CEO Fraud imposter attacks, or what VZ DBIR calls "pretexting" (see Figure 34 in the report). These are email attacks that have no malicious link or infected email attachment. Instead, these attacks are most often financially motivated, tricking people into approving invoices, payments or change of bank account information. The goal is purely to steal money. The reason I emphasize this is we often hear of ransomware in the news, as organizations have to go public when a ransomware incident happens. However, we almost never hear about BEC/CEO Fraud incidents in the news, as organizations do not have to, nor almost never do, go public. You have to go public when your data is breached; you do not have to go public when your money is stolen.
BEC/CEO Fraud emails are often the most difficult for automated security tools or people to detect, as these emails are often highly customized and have far fewer indicators in the email. In addition, Artificial Intelligence has the ability to make creating these customized attacks easier, and in almost any language the cyber attacker wants. This is why it's so critical that employees strictly adhere to and follow all policies related to the approving, invoicing, transferring of money, or modifying related financial accounts.
One data point I always find interesting is the tracking of lost and stolen devices. While we often don’t think of this as a risk, when we lose control of a mobile device, the data on that device is at risk. This is why controls such as screen-locks, encryption, and remote tracking/wiping are so important. You are far more likely to lose a mobile device or have one stolen than you are to have it be hacked (it’s actually quite difficult to hack an actively patched and maintained mobile device). In Figure 54 of the report, we see a fascinating statistic: You are far more likely to lose a device than have one stolen. So, when it comes to physical security, it is not the thief we should be concerned about, but the absent-minded, overwhelmed employee who is traveling.
These are by no means the only findings in the report; these are just the ones I found most interesting.
Still have questions or want other details, but don’t have time to read the full report? Want to learn all the key take-aways from the report specific to your role, industry, or challenges you face? Ask AI to help summarize key elements of the report for you. See example below.
To learn more about building a mature security awareness program, consider the SANS LDR433 Managing Human Risk course. This intense, three-day class provides you the strategic roadmap to not only managing human risk but also to effectively measure it. In addition, the class provides seven interactive team labs where you apply everything you learn with your peers. Finally, you have the opportunity to earn the SSAP (SANS Security Awareness Professional), the industry’s most recognized credential demonstrating expertise in managing human risk.


Lance revolutionized cyber defense by founding the Honeynet Project. At SANS, he has empowered over 350 organizations worldwide to build resilient security cultures, transforming human risk management into a cornerstone of modern cybersecurity.
Read more about Lance Spitzner