SEC595: Applied Data Science and AI/Machine Learning for Cybersecurity Professionals


Experience SANS training through course previews.
Learn MoreLet us help.
Contact usBecome a member for instant access to our free resources.
Sign UpWe're here to help.
Contact Us
Examining static properties of suspicious files is a good starting point for malware analysis. This effort allows you to perform an initial assessment of the file without even infecting a lab system or studying its code. Let's take a look at several free Windows tools that are useful for extracting such meta data from potentially-malicious executables.
PE Studio by Marc Ochsenmeier is a GUI tool for statically examining many aspects of a suspicious Windows executable file, such as imported and exported function names and strings. You many of these details through other means; however, it's very convenient to capture this information on one shot.
For instance, PE Studio not only shows the names and other properties of the PE file's sections, it also automatically computes each section's MD5 hash. Hash values could be used as indicators of compromise (IOCs), but malware authors can easily tweak the specimen to change the file's hash. For this reason, it's useful to note hash values of the sections that comprise the malicious program. This way, if the attacker changes a portion of the file, hash values of one or more sections might still match as an IOC.
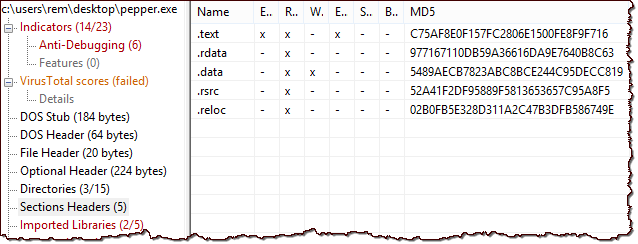
Perhaps most usefully, PE Studio automatically flags aspects of the file that could indicate that is is malicious, as you can see below. These indicators include "blacklisted" strings and API calls, as shown below. PE Studio can also query VirusTotal for information it might contain that matches the hash of the file you're examining, if your lab system is connected to the Internet.
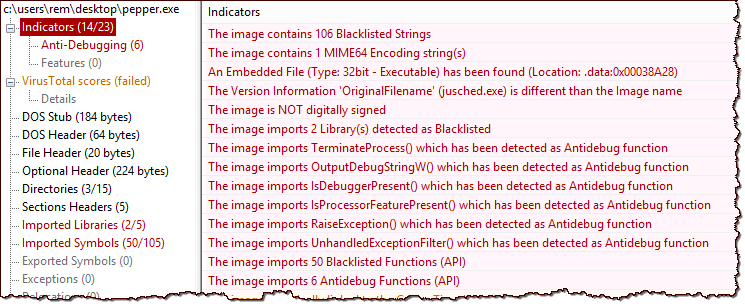
PE Studio also shows "meta" information that could be embedded into the file to describe its author and version. Such details can be easily faked, but at times they can be used as potential IOCs.
Peframe by Gianni Amato is a command-line tool that can automatically extract static file properties, displaying some of the information you can explore interactively with PE Studio. Peframe can compute hashes, extract PE header details, identify common packers, detect suspicious API calls, etc.
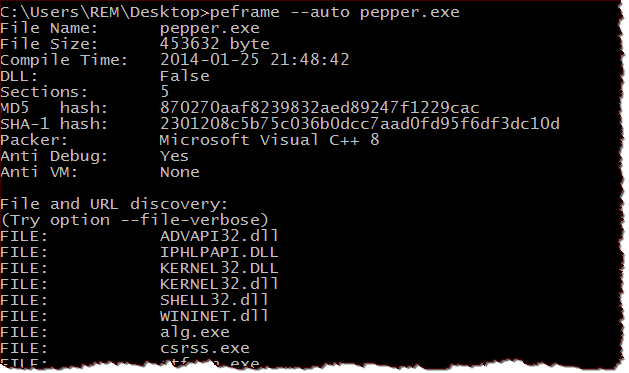
Peframe is written in Python. It runs well on Windows, as long as you install the Python runtime.
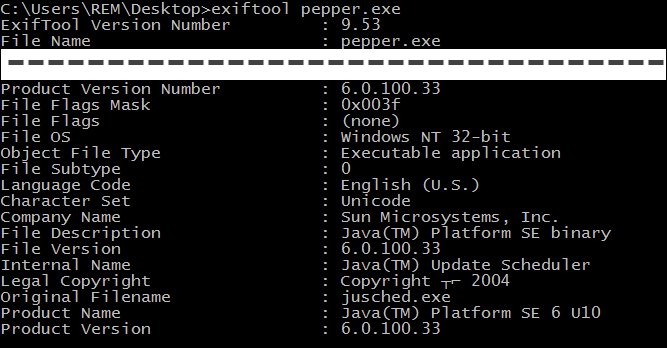
As convenient as PE Studio and peframe are, sometimes it's nice to have command-line tools designed for one specific job. Moreover, it's generally a good idea to include in your toolkit multiple tools that perform similar functions. For instance, ExifTool Phil Harvey can extract various meta data embedded into files. It really shines when analyzing images, but it can also extract some data from Windows executables, as you can see below.
Another handy command-line tool for examining static properties of files is strings2 by Geoff McDonald. In many ways, it's similar to traditional string-extracting utilities that you're familiar with. One of the nice features of strings2 is its ability to extract ASCII and Unicode-encoded strings in one step.
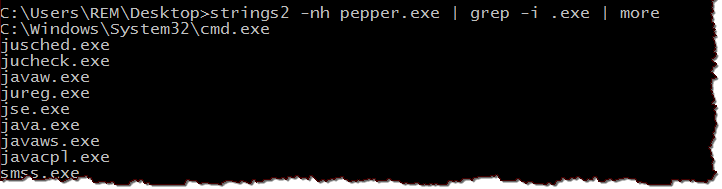
What makes strings2 quite unique is its ability to extract strings from a running process. Sure, you could do this using GUI tools such as Process Explorer and Process Hacker, but sometimes it's convenient to be able to get this information from the command prompt. A process might reveal strings that aren't visible inside a file until the program runs. I digress, though. After all, extracting data from running processes isn't a static malware analysis technique.
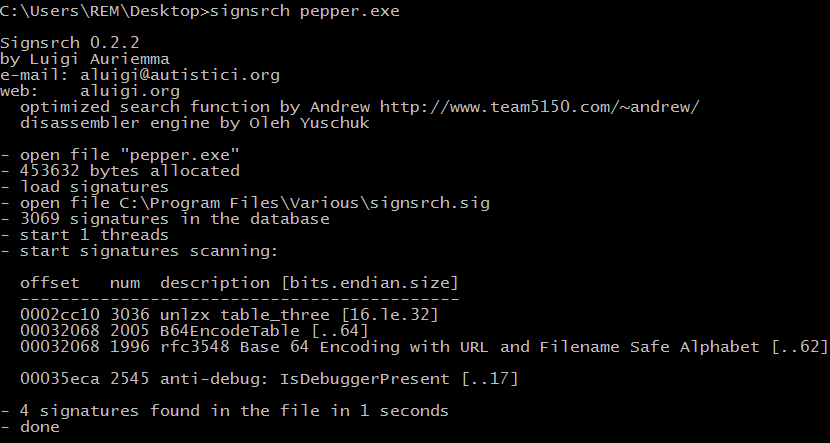
Another tool worth mentioning in this context is Signsrch by Luigi Auriemma. This handy utility can statically examine a file to spot patterns of "compression, multimedia and encryption algorithms and many other things like known strings and anti-debugging code."
Exeinfo PE is a handy tool for examining various aspects of a Windows executable. It's especially good at identifying signatures of commonly-used packers. In the example below, Exeinfo PE flags the file as being packed with UPX, a popular utility for obfuscating programs. Exeinfo PE works well, but I don't know who wrote it; for this reason, I only run it inside an isolated malware analysis lab.
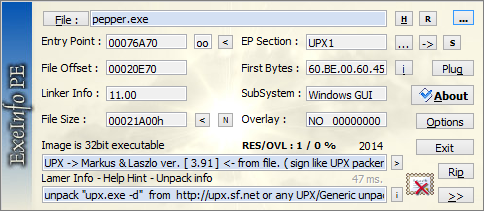
Even though generic UPX is relatively easy to bypass (just use the "upx -d" command), it is often used by malware authors. This allows you to continue examining the file in its less-protected form.
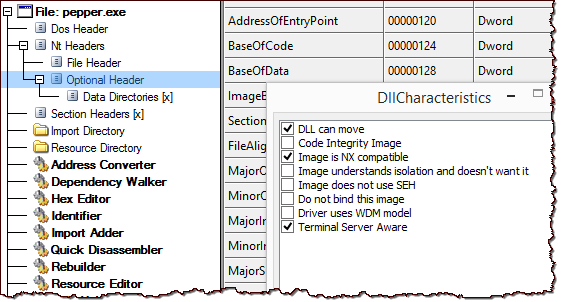
To examine additional details of the Windows executable file, consider loading the specimen into CFF Explorer by Daniel Pistelli. This tool lets you edit contents of the file's PE header. For example, if you decide to analyze the file's code on Windows 8.1, you'll need to clear the DynamicBase flag in the DllCharacteristics field to deal with the ASLR feature of the OS. CFF Explorer calls this field "DLL can move", as shown below.
As you examine static properties of a suspicious file, you will be able to assess whether it warrants a more thorough examination using other malware analysis techniques. You'll be able to determine where to focus your subsequent analysis efforts to determine whether the file is, indeed, malicious, how bad it is, how to detect it and how to best examine it.


Lenny Zeltser is a leader in developing resilient security programs. His invaluable tools, like REMnux, a widely used Linux distribution for malware analysis, have become industry standards in combating malicious software.
Read more about Lenny Zeltser