Modern day mobile devices are a double-edged sword, creating new security risks while providing valuable sources of evidence for digital forensic investigators. Their ever expanding capabilities make mobile devices more like personal computers that accompany us as we navigate the world. Digital forensic investigators can use information stored on and generated by mobile devices to reconstruct our movements, communications, and other personal details.
If you need to extract information from cell phones, smart phones, and other mobile devices, or are concerned about the security of data on such devices, here are some important things you should know.
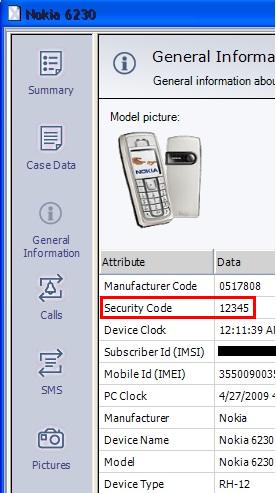
Bypassing Security Codes: Digital forensic investigators can extract the security code from some locked mobile devices using specialized tools. The screenshot below shows the security code "12345" recovered from a Nokia 6230 using .XRY (subscriber identifier redacted). Being able to bypass security mechanisms on a mobile device enables digital forensic investigators to acquire data from the device with forensic software.
Safe SIM Card: Inserting the wrong SIM card into a cell phone destroys some useful data in memory. To mitigate this issue, digital forensic investigators can create "safe" SIM cards designed for forensic examination purposes.
Live Acquisition: Removing the battery from a cell phone before performing a forensic acquisition may destroy valuable evidence. In some cases, to ensure that all available evidence is preserved, digital forensic investigators will leave a mobile device powered on until a forensic acquisition can be performed, taking precautions to prevent external influences from altering data on the device.
Trusted Time Source: Even if the clock on the evidentiary device is incorrect, some time stamps on the device may still be accurate because they are generated by system on the core network. For instance, the time stamp in a received SMS message is set by the Short Message Service Center, not by the phone.
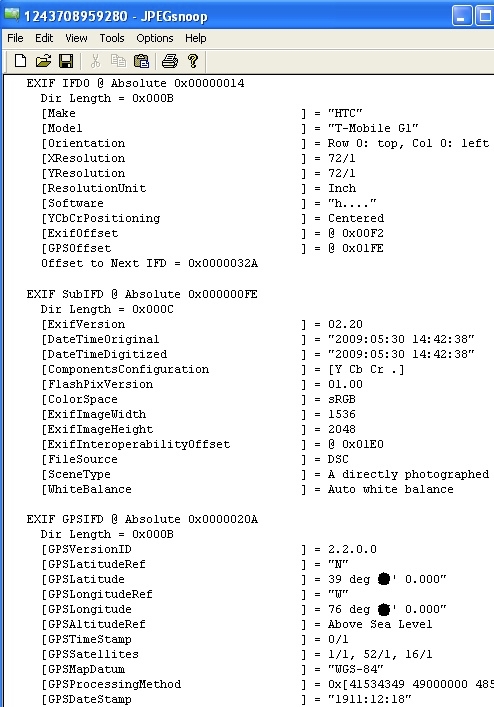
Tracking Movements: Some mobile devices store location-based information associated with certain media and actions on the device. Digital forensic investigators can recover this information to determine the geographic location of the mobile device at a particular time. For instance, the following screenshot shows Exif metadata extracted using JPEGsnoop from a digital photograph taken using a G1 mobile device. This metadata includes the date and time the photograph was taken and GPS coordinates of the location (location details redacted).
Recovering Deleted Data: When the user clears the call log from a cell phone, it may still be recoverable with relative ease. Therefore, even when call logs are not displayed on the device, digital forensic investigators may be able to view details about dialed, received, and missed calls on the device using readily available tools.
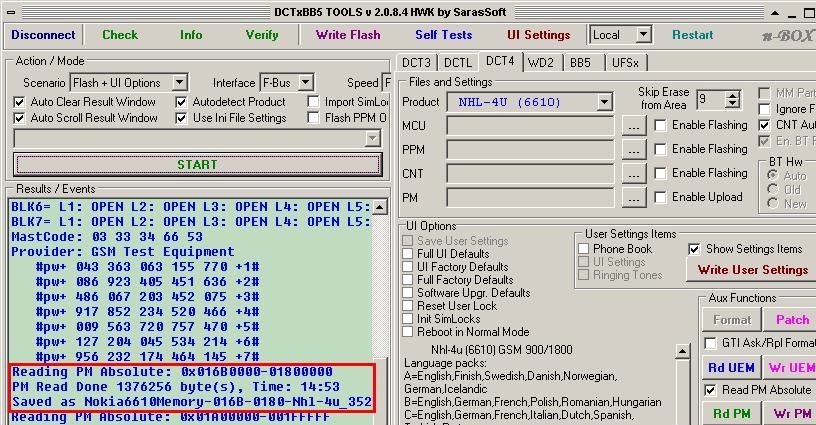
Getting Physical: Digital forensic investigators can recover substantial amounts of deleted data from an increasing number of mobile devices by acquiring and analyzing the full contents of memory. This screenshot shows a physical memory acquisition of a Nokia 6610 using the Sarasoft application via a Twister flasher box.
Deleted data like photographs, call logs, and traces of user activities (e.g., Web browsing and file viewing) recovered from a mobile device can provide digital forensic investigators with some of the most useful and incriminating evidence in a case.
To learn how to perform these and other Mobile Device Forensics techniques, joins us for the debut of SEC563 Mobile Device Forensics in Baltimore, July 27 - 31. This is an intensive technical course with plenty of hands-on exercises to familiarize you with the inner workings of various mobile devices and show you the benefits and limitations of various approaches and tools. We not only demonstrate state-of-the-art mobile forensic tools and techniques, we peel back the layers of digital evidence on mobile devices to show what is going on behind the scenes. In this way, you obtain a deeper knowledge of the information you rely on when investigating cases involving mobile devices.

Eoghan Casey is founding partner of cmdLabs (http://www.cmdlabs.com/) , author of the foundational book Digital Evidence and Computer Crime, and coauthor of Malware Forensics. He has been involved in a wide range of digital investigations, including network intrusions, fraud, violent crimes, identity theft, and on-line criminal activity. He has testified in civil and criminal cases, and has submitted expert reports and prepared trial exhibits for computer forensic and cyber-crime cases.




