Tags:
SOC 2 & AWS Shared Responsibility
SOC 2 Overview
What is SOC 2?
Protecting customers' data is a concern for all organizations regardless of industry or size. Most organizations outsource key aspects of their business to third-party vendors such as
Software-as-a-Service (SaaS) solutions or cloud hosting providers (i.e. Amazon Web Services). As companies continue to share the responsibility of protecting sensitive data, there is increased importance and scrutiny on the cybersecurity practices implemented at these organizations.
Third-party assessments are a common way in which organizations prove their cybersecurity practices to vendors, customers, and prospects. SOC 2 compliance examinations have become one of the de facto standards for organizations to prove how there are securely managing their customers' data to protect their interests and privacy. For most organizations conducting business with a SaaS provider, SOC 2 compliance is a minimum requirement. SOC 2 reports are common for other service organizations as well such as law firms, marketing agencies, accounting firms, healthcare organizations, and more.
SOC 2 is a reporting framework developed by the American Institute of Certified Professional Accountants (AICPA) intended to meet the needs of a broad range of customers or vendors that require information and assurance about the controls at a service organization relevant to the security, availability, and processing integrity of the systems the service organization uses to process users’ data and the confidentiality and privacy of the information processed by these systems. SaaS or other service organizations utilize these reports to assist with:
- Vendor due diligence
- Demonstrating security as a differentiator
- Internal corporate governance and risk management processes
- Proving security to a regulatory body or governing authority
SOC 2 examinations involve a Certified Professional Accounting (CPA) firm assessing an organization's information security and privacy control environment. The assessment includes a description of the controls, the tests performed to assess them, and the results of these tests.


Shared Responsibility
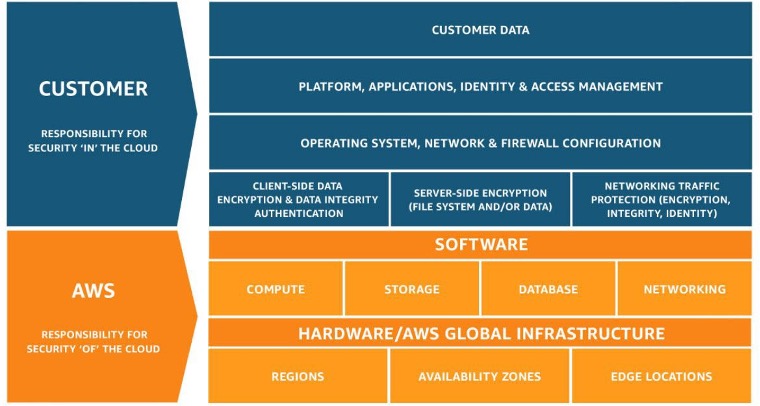
Photo Source: https://aws.amazon.com/compliance/shared-responsibility-model/
SOC 2 & AWS
The AWS infrastructure is SOC 2 compliant, all AWS compliance reports can be found on AWS Artifact. Which is a resource for compliance-related information related to AWS’s security and compliance reports including AWS SOC 2 reports.
The AWS shared responsibility model has a significant impact on your organization's SOC 2 reports. In a SOC 2 examination, there are required criteria related to the physical and environmental security of the infrastructure utilized to support the service.
When an organization is hosted on AWS, the required criteria associated with physical and environmental security controls are “carved-out” of the report. This means we document in your SOC 2 report that AWS is responsible for the criteria related to physical and environmental controls. Within your SOC 2 report, we also state that the service organization (you) will review AWS SOC 2 reports to verify the physical and environmental security controls are in place.
This carve-out is common in all SOC 2 reports that leverage AWS as a cloud hosting provider. In addition to taking advantage of AWS’s physical security controls, there are AWS services that organizations should take advantage of and document in their SOC 2 report. These aspects are basic services on AWS that offer companies the ability to demonstrate a robust cybersecurity program that protects customers' data.
Using Security Hub and Config to Demonstrate Security in Your SOC 2 Report
Demonstrate Security
Display Exceptional Security with AWS specific controls
AWS offers services to assist cybersecurity professionals with understanding their security environment and demonstrating compliance to auditors to ease the pain of cybersecurity assessments. The AWS security organization is continuously assessing the AWS environment and updating a knowledge base of security best practices and rules. These services built with these best practices in mind, enable organizations to leverage services that were built and designed specifically to perform security functions in their environment. Taking advantage of these tools can assist organizations with their overall cybersecurity compliance programs and respond to the ever-evolving threats and attack vectors, in real-time. Most of these services are free and are currently being utilized by organizations hosted on AWS.
However, auditors are often unaware of the services or lack the technical knowledge to advise clients and ultimately utilize these services to demonstrate stronger security in their SOC 2 reports.
The great thing about the majority of these controls, they require less documentation and should result in fewer questions from the auditors about your environment. Including these additional controls in your SOC 2 report can be utilized as a differentiator with prospective customers and other third-parties. The controls that follow on the next pages represent SOC 2 controls that you should immediately consider adding to your SOC 2 report.
Download CONTROLS: The Ultimate Guide to SOC2 for SaaS Companies Hosted on AWS
READ PART 2: Streamline Fifteen SOC2 Controls with AWS Config and AWS Security Hub





