Targeted Web-Based Malware?
Malware authors are frequently observed leveraging server side scripting on their infrastructure to evade detection and better target their attacks. This includes both exploit kits and servers hosting secondary stage payloads, all of which can easily be set up to alter their responses based on the footprint of the visitor. This could include geolocation of the IP address visiting the site if the attacker is targeting users from a particular country or region, or perhaps user-agent if they are only focused on certain browsers or operating systems. Without access to the source code leveraged on the server, it is difficult to detect whether it would alter its behaviour if you were visiting from a different device or location, and therefore malware analysts may find themselves declaring a link benign, or that the payload server is down, when in fact, it is only presenting that way to the analyst in question.
Got an example?
An example of this can be seen in the Malwarebytes blog on Magnitude exploit kit which details that "...users are inspected at a 'gate' that decides whether or not they should be allowed to proceed to Magnitude EK. This gate, which has been nicknamed 'Magnigate' by Proofpoint, performs additional checks on the visitor's IP address and user-agent to determine their geolocation, Internet Service Provider, Operating System and browser information..."
Hmm, so what can I do?
There is of course a balance here, even if you have access to VPN software, which allows you to select the country you want to appear from, it would be extremely time consuming and cumbersome to iterate through all of the available countries, each time using different browsers and painstakingly looking to identify whether there was any variation in the responses.
To aid in this task, I have written a new tool which automates this whole process and may be useful during malware analysis if you suspect the server is hiding something from you.
It works as follows -
- Loads a list of countries and user-agents that you want to appear from
- Leverages a proxy listing website's API to obtain various country proxies
- Verifies that the proxies are working, and that the geolocation is per requirements
- Connects to the server using the proxy and iterates through all of the user-agents requesting the site multiple times
- Identifies any results which are different from the control value and highlights to the analyst
Demonstration
I've uploaded a number of test documents to my webserver, which you are welcome to use for your testing:
adamkramer.uk/browser-test.php & adamkramer.uk/browser-test-404.php
Both of these do the same thing - they wait until they observe someone connecting from a Chinese IP address with an iPhone user-agent before presenting the main content. The first URL will return a result in all other circumstances stating "Go away", and the second will return a 404 error unless the conditions are met.
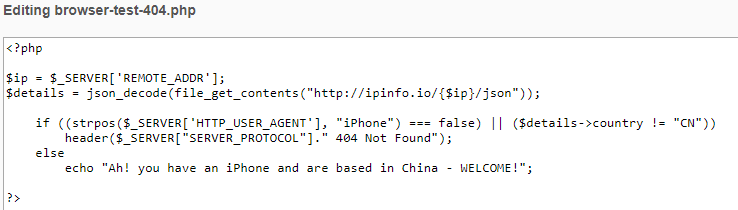
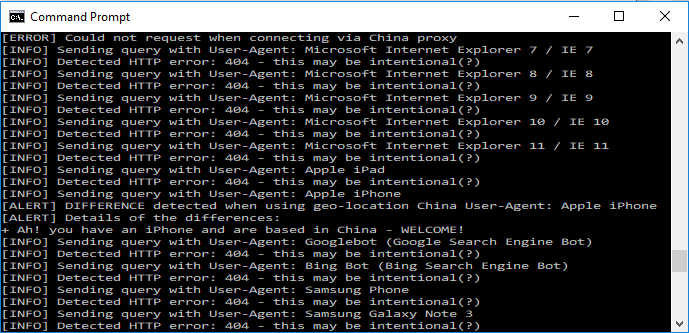
The screenshot below shows the script iterating through various user-agents whilst connected to a Chinese proxy. In each case we can see the result was a 404 until the iPhone user-agent was sent, after which the script presented a 'diff' style output on what was different about this case.
Great! Where can I get it?
The script was written in Python (v3.x) and is available from Github here.
Please feel free to use / fork / enhance / provide feedback.
Happy analysing!
-Adam (Twitter: @CyberKramer)




