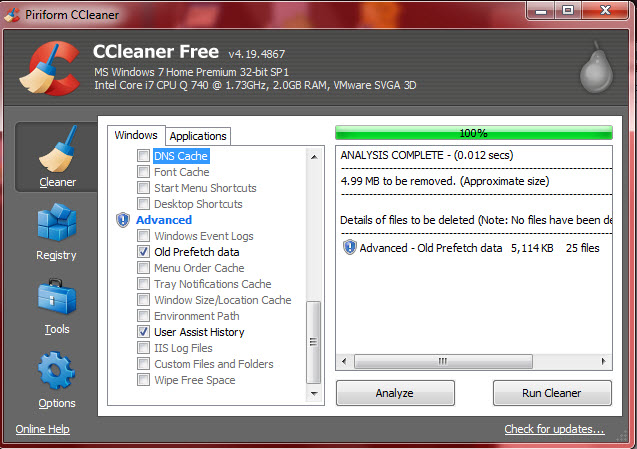
One of the great pleasures of performing Windows forensics is there is no shortage of application execution artifacts. Application execution tells us what has run on a system and is often the pivot point that reveals important activity on the system. Why was FTP run on this workstation? Is it normal to see execution of winsvchost.exe? Why was a privacy cleaning tool used for the first time during the system owner's last week of work? While undoubtedly useful, our adversaries are more forensic-aware than ever and often take steps to eliminate application execution artifacts. At CrowdStrike we routinely encounter nation-state groups that attempt to delete Prefetch. Even the popular CCleaner anti-forensics tool defaults to clearing Prefetch and UserAssist data. Hence having additional sources of data can often mean the difference between an easy examination and a long, painful one.
UserAssist, Muicache and Prefetch have been long understood and even significantly upgraded in newer versions of Windows. Jared Atkinson and Yogesh Khatri provided excellent updates on Prefetch changes in Windows 8. More recently, Andrew Davis documented the Application Compatibility Cache (Shimcache) and Corey Harrell posted information on the RecentFileCache.bcf file. Yogesh Khatri followed up with Amcache.hve, the replacement to RecentFileCache.bcf in Windows 8. All of these artifacts have particular strengths and weaknesses, but one we haven't heard much about lately is SuperFetch.
SuperFetch

SuperFetch has been on the forensic radar since the preview versions of Windows Vista. It was lauded as an upgrade to the venerable Prefetch with the promise to proactively optimize application memory with regards to time and usage scenarios. The applications you use first thing in the morning are often different than those after lunch and perhaps different still from those run after work hours. It is important to note that it does not replace the Prefetch service. SuperFetch must have had the desired effect on performance as Microsoft chose to continue its use in Windows 8.1 and Windows 10.
SuperFetch consists of a series of "Ag*.db" database files located in the %SystemRoot%\Prefetch folder. It is wildly complicated with a variety of different header formats for different databases, versions and architectures (x86 and x64) of Microsoft operating systems. On systems with SSD drives, it may be turned off by default (similar to Prefetch). There are still many gaps in our knowledge of SuperFetch, but it feels like the community is inching closer. Joachim Metz started a specification document for the format In April of 2014 as part of the libyal documentation project. However, the number of "Unknown" values in the document make it clear that we have a way to go in developing a true understanding.
Parsing SuperFetch
SuperFetch tracks "performance scenarios" and is specifically designed to anticipate frequently run applications after system activity like standby mode, hibernation, and fast-user switching. It records the set of memory pages used over a long period of time, allowing it to model user behavior and make better decisions about when to pre-load application data into memory. It is these databases recording what has been loaded in the past that we can take advantage for application execution artifacts. We can currently derive the following information:
- Application executable names
- Execution count
- Foreground count
- Supporting files (includes the full paths of a wide range of files that have been mapped into memory including DLLs, zip files, documents, database files, and files and folders present on removable media, the Recycle Bin, temp folders, and even Volume Shadow Copies and encrypted volumes)
- Volumes accessed (example: HardDiskVolume1)
- Full path information providing data on folders present on various volumes access by the system
- Timeframes of application activity
- Timestamp (from the AgAppLaunch database - purpose unknown but appears to not be reliably tied to execution time in testing)
The timeframes of application activity fall into the following ranges:
- Weekday 6AM to 12PM
- Weekday 12PM to 6PM
- Weekday 6PM to 12AM
- Weekday Global
- Weekend 6AM to 12PM
- Weekend 12PM to 6PM
- Weekend 6PM to 12AM
- Weekend Global
Curiously there seems to be a blind spot in the 12AM to 6AM range. Good thing so many hackers are working business hours these days! While timeframe information stored by SuperFetch has yet to be vetted for its reliability, it presumably could help identify application activity occurring at strange times. For instance, is it normal to see your company database application accessed over the weekend?
Tools
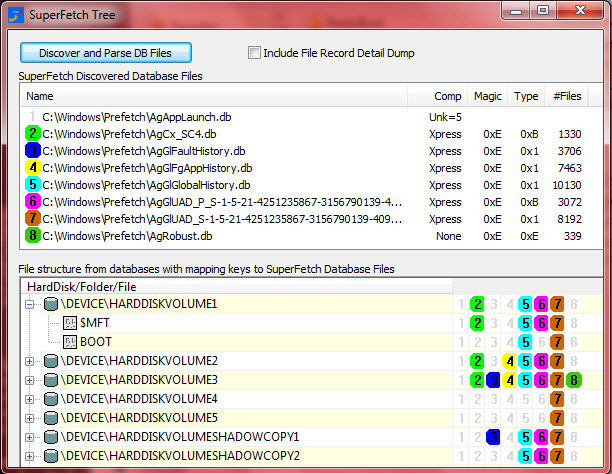
The first tools that I became aware of for parsing SuperFetch were released by TMurgent. Superfetchlist.exe is a CLI tool providing full path information for files referenced in the various SuperFetch databases. SuperFetch Tree is a clever GUI application that provides a graphical tree structure and neatly identifies what databases a given file or folder were referenced within.
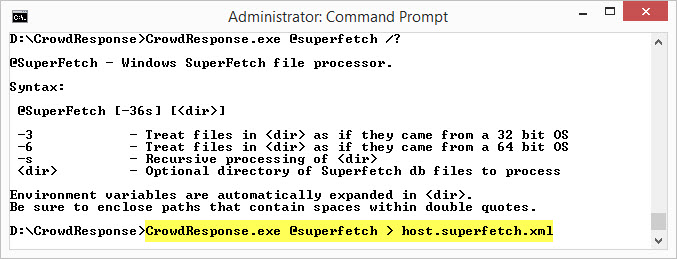
A few days ago I posted on the CrowdStrike blog about the latest version of the free CrowdResponse tool now supporting Prefetch, Shimcache, and SuperFetch application execution artifacts. CrowdResponse includes a SuperFetch module providing the most solid and useful data from this artifact that I have seen. It is the brainchild of research and development by Alex Ionsecu and Robin Keir and can be used for live data collection or run against databases files exported from a system or forensic image. CrowdResponse parses data from the AgAppLaunch.db SuperFetch database and provides output in XML, CSV, or HTML. The tool extracts an abundance of application execution information, execution counts, and timeframe information.

Conclusion
It is exciting to have the capability to parse yet another Windows application execution artifact. However, given the state of our knowledge of SuperFetch, I recommend taking a cautionary approach to interpreting data found within these files. There is still much to be discovered, and the good news is that early indications show this artifact will likely continue to exist in Windows 10. Hopefully with more eyes on the databases we can get more comfortable with the available data and continue to learn more.
References:
[1] Forensics Wiki: SuperFetch
[2] Inside the Windows Vista Kernel: Part 2
[3] Windows SuperFetch (DB) Format from libyal Project
[4] SuperFetch Tools from TMurgent
[5] CrowdResponse with @superfetch plugin
Chad Tilbury, GCFA, serves as a Technical Director for CrowdStrike and has spent over fifteen years conducting computer crime investigations ranging from hacking to espionage to multi-million dollar fraud cases. He is a Senior Instructor and co-author of FOR408 Windows Forensics and FOR508 Advanced Computer Forensic Analysis and Incident Response at the SANS Institute. Find him on Twitter @chadtilbury.





