SEC595: Applied Data Science and AI/Machine Learning for Cybersecurity Professionals


Experience SANS training through course previews.
Learn MoreLet us help.
Contact usBecome a member for instant access to our free resources.
Sign UpWe're here to help.
Contact UsHow you define insider threat is critical, because how the problem is defined will drive how you define and implement the solution.

When it comes to the world of human security, one of the most common terms I hear is the term Insider Threat. Quite a few organizations have some type of insider threat program, however, in just about every organization I’ve worked with, each organization has a different definition of insider threat. How you define insider threat is critical, because how the problem is defined will drive how you define and implement the solution. I’m not going to attempt to define insider threat for your organization, I’m going to leave that to you. But I hope to define the different categories that can inform your definition and explain how the categories you choose impact the solution you implement.
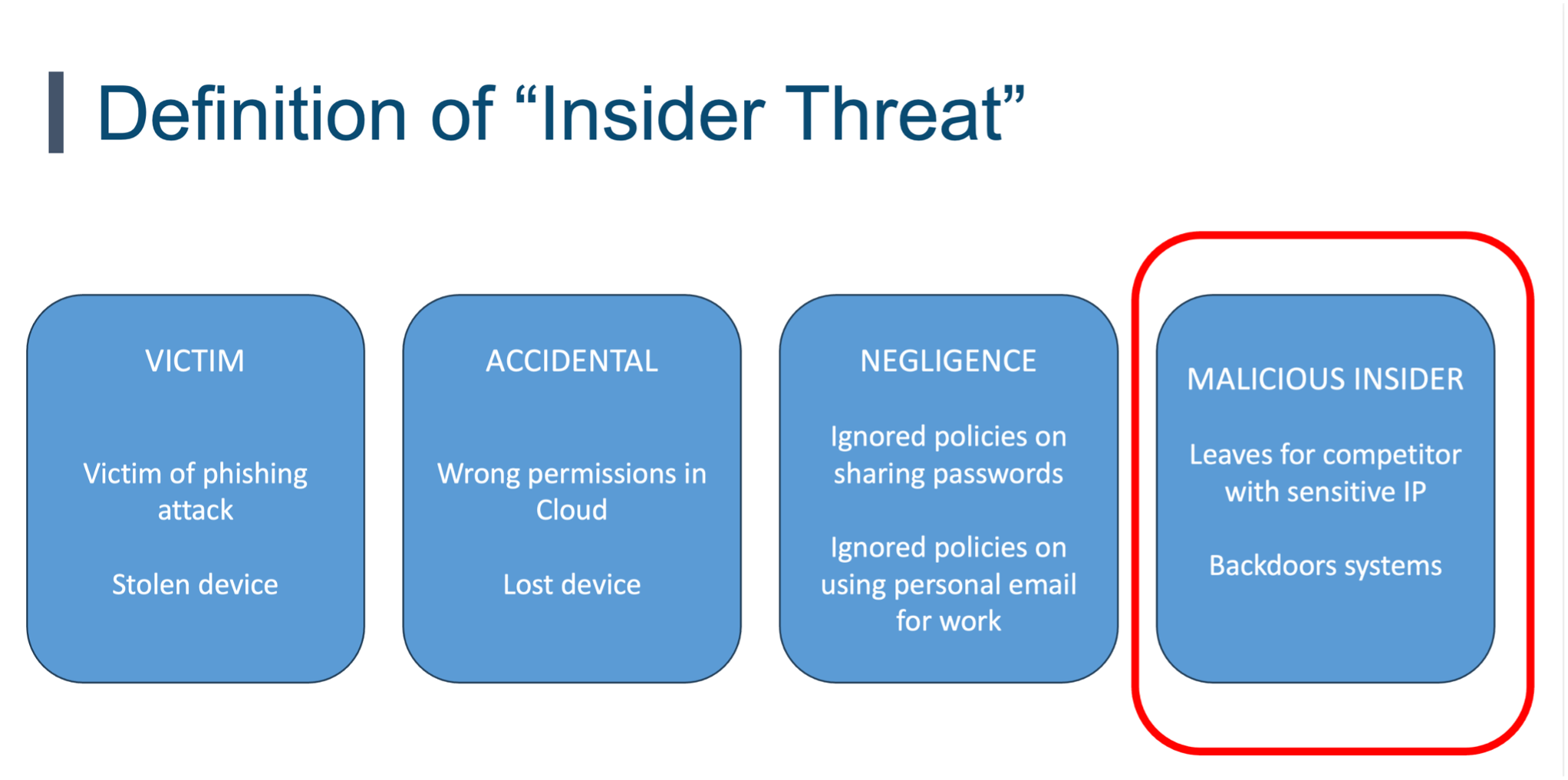
I find there are four different categories that can be included in insider threat. The one commonality these categories share is the threat of a trusted individual such as an employee, contractor, intern, or volunteer, (I leave it up to you if you also include third party vendors, often that falls under an entirely different group called Third Party Risk Management (TPRM)). The four categories are:
This is a trusted individual who causes harm on purpose. Quite often their motivations vary from financial gain, ego, revenge, and more. These individuals use their trusted access to cause harm on purpose. A common example is when an employee leaves the organization and takes a great deal of sensitive information with them such as the customer database or trade secrets. These types of incidents rarely happen, but when they do, the impact is very high. What is interesting is regardless of how organizations define insider threat, this is the threat I most often see insider threat programs focusing on.
In this scenario, the individual does not cause harm on purpose but does so through a failure to adhere to security policies and procedures. A common example is they know the security policy but choose to ignore or bypass it so they can get work done. They may take sensitive work home on a personal laptop or forward sensitive documents to a personal email account. They know they are violating policy but feel it may be the only way to get their job done. This can be an indication that security policies are too confusing, complex and/or blocking people from their daily jobs.
Human error is a huge driver of breaches. This happens when people are trying to get work done and cause an incident stemming from carelessness, lack of awareness, or insufficient training. One of the most common examples is what the Verizon DBIR calls misdirection. This is when auto-complete in email causes you to email the wrong person. You type in the name Sarah in finance as the email recipient, but because of auto-complete in email, you accidently send the sensitive documents to your daughter’s basketball coach who is also named Sarah. Before you laugh, keep in mind, human error like this causes 25% of all breaches globally. This is often an indication that technology or policies have become too complex, making mistakes that much easier.
This is when the individual is the victim of an attack. A common example is when someone falls victim to an email phishing attack or phone call vishing attack.
The question becomes, which of these categories fall under your definition of insider threat? I leave that up to you. HOWEVER (and this is a BIG, however), different categories are managed different ways.
For a malicious insider, you manage this risk like you would in a counter-intelligence program. You begin by doing background checks, hiring people that have a high probability of behaving in a trustworthy manner. Then you have numerous processes and controls in place to limit the amount of damage trusted individuals can do. Finally, you actively look for people that are attempting to cause harm, i.e., indicators of malicious insider activity. This is very hard to do as those people are not only trusted, but almost every malicious insider has different motivations or takes different actions than previous insiders, making it very difficult to look for common indicators.
For the other three categories, negligence, error and victim, your approach is the opposite. These are good, trusted people, who want to do the right thing. Our job is to enable them by making security as simple as possible. This is where Security Awareness and Training programs are key. As we provide people with the knowledge, skills, and tools to make security simple for them, they are enabled to use your organization’s technology safely and securely.
How you approach malicious insiders should not only be different, but it might also need to be led by a different team, as a malicious insider threat requires an entirely different mindset and skills. You are a hunter looking for evil. For the other three categories, negligence, accidental, and victim, you are an enabler helping and encouraging good.
How you define insider threat is up to you. All I ask that if you use the term insider threat or have an insider threat program, that you clearly define what you mean by that term and adjust your security program accordingly.
Learn the key lessons and roadmap to building a mature awareness program by taking the SANS LDR433 Managing Human Risk course. Apply techniques such as the BJ Fogg Behavior Model, AIDA Marketing funnel, the Golden Circle, and ADDIE training model and learn about the Elephant vs. the Rider. Gain access to the course digital download package and community forum. In addition, not only will you learn from your instructor, but you will also learn from your extensive interactions with your peers in seven interactive labs. Finally, you will have the opportunity to earn the SANS Security Awareness Professional (SSAP) credential, the industry standard in human risk management.


Lance revolutionized cyber defense by founding the Honeynet Project. At SANS, he has empowered over 350 organizations worldwide to build resilient security cultures, transforming human risk management into a cornerstone of modern cybersecurity.
Read more about Lance Spitzner