Windows 7 was released this past week. A lot of work by the SANS community has been accomplished at uncovering digital forensic artifacts from it. First off, Windows 7 is really Windows VISTA release 2. Many of the features that are found in Windows Vista will be found in Windows 7.

First of all, all the SANS Digital Forensic Courses have already included up-to-date material fully covering Windows 7 and Vista unlike anyone has done before. In fact, our challenge for SEC408, Computer Forensic Essentials is strictly based off of a Windows Vista case. We have details in SEC408, Computer Forensic Essentials, that are not as covered in peer courses.
Here is just a few things we have helped document regarding Windows 7.
User Profiles:
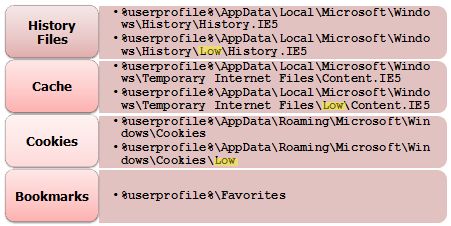
With the release of Vista/Win7, Microsoft significantly changed the folder structure and mechanisms used by the operating system for user profiles. One of these changes was to make roaming profiles more explicit. Roaming profiles allow users to log onto other systems in the domain and have their profile information follow them. They have been around for many years, and in Vista/Win7, Microsoft decided to make what follows a user, and what doesn't follow a user much more explicit. Hence within a user profile in Vista/Win7, there are now two different set of folders: Roaming and Local. For our purposes, we want to be able to determine where our browser artifacts will be located in this new file structure. Traditionally Microsoft has included cookies in a roaming profile and excluded cache and history files by default. Thus, cookies are now found under the Roaming folder and history and cache can be found within the Local folder.
Internet Explorer:
The major change within Vista/Win7 that affects us when performing browser forensics is the newly implemented "Protected Mode". The idea is that if malicious code is run in the browser, it will not have the necessary privileges to cause harm to the operating system. Since not all activities using the browser will be unprivileged, a duplicate set of directories were necessary to store files from unprivileged use, called Low folders. An example of what this looks like in the file system is:
%userprofile%\AppData\Local\Microsoft\Windows\History\Low\History.IE5 (for the IE history files)
"Protected Mode" conducts web browsing as an unprivileged user
- A new set of locations were added: low folders
- Most browser evidence will be in low folders
- Local file usage is stored in the standard history folder (because it is not performed with restricted permissions)
- If Protected Mode is turned off, low folders will not be utilized
- If User Access Control (UAC) is turned off, low folders will not be utilized (it is required for Protected Mode to operate)
- If the instance of IE is run with Administrator permissions, the low folders are also not used
USB Key Analysis:
We discussed full Windows 7 USB Key Analysis in this post.
USB Drive Enclosure Analysis:
We discussed how to perform Windows 7 USB Drive Enclosure Analysis in this post.
Defrag Analysis:
Chad Tilbury discussed detecting defrag analysis here.
Timeline Analysis:
Kristinn Guðjónsson developed and released a full scope timeline creation tool called log2timeline that is able to parse many Windows Vista and Windows 7 artifacts in a single simple tool.
- Prefetch directory (reads the content of the directory and parses files found inside)
- UserAssist key info (reads the NTUSER.DAT user registry file to parse the content of UserAssist keys)
- Squid access logs (with emulate_httpd_log off)
- Restore points (reads the content of the directory and parses rp.log file inside each restore point)
- Windows shortcut files (LNK)
- Firefox 3 history file (places.sqlite)
- Windows Recycle Bin (INFO2)
- Windows IIS W3C log files
- OpenXML Metadata (for metadata inside Office 2007 documents)
- ISA Server text export from queries (saved to clipboard and from there to a text file)
- TLN (Timeline) body file
- Mactime body file (so it can be output in a different format)
Shadow Copy Forensics
Troy Larson from Microsoft has done a wonderful job continuing to discuss the Shadow Volume Copy and ways you can examine them in an investigation. We posted back in 2008 on many of his techniques.
The work continues: There are many artifacts yet to be uncovered and more work is being done. Keep your eyes peeled on this site and additional sites like Harlan Carvey's http://windowsir.blogspot.com/ as he is publishing many details as well.
If you have any sites that contains Windows 7 artifact information please post them in comments and Ill update the post as we move forward.
Rob Lee is a Director for MANDIANT, a leading provider of information security consulting services and software to Fortune 500 organizations and the U.S. Government. Rob has over 13 years experience in computer forensics, vulnerability discovery, intrusion detection and incident response. Rob is the lead course author and faculty fellow for the computer forensic courses at the SANS Institute and lead author for SEC408 Computer Forensic Essentials and SEC508 Computer Forensics, Investigation, and Response.





