This blog is jointly authored by Anastasia Sentsova, Ransomware Cybercrime Researcher at Analyst1; Margo Lychak, a former Cybercrime Researcher at Intel 471; and Sean O’Connor and Will Thomas, co-authors of the SANS FOR589TM: Cybercrime IntelligenceTM course. This blog sheds light on the often-overlooked role of women within Russian-speaking cybercriminal networks, exploring the complex dynamics of gender within a predominantly male underground world. This blog examines women's contributions and challenges in cybercrime, offering insights into their roles in illicit ecosystems. It also highlights themes like attribution and organizational roles related to the SANS FOR589 course, covering cybercriminal motivations, network structures, and intelligence techniques.
Russian-speaking cybercrime is considered one of the largest and most active communities in the global cybercrime landscape. Historically, the landscape of Russian-speaking cybercrime has been predominantly male-dominated, with men occupying most visible roles in the underground. However, women, though fewer in number, are also involved in various capacities within this hidden world. This aspect of women in cybercrime remains under-researched, raising critical questions about the nature of their involvement: Who are these women? What roles do they assume within cybercriminal enterprises? And, more importantly, how significant is their presence?
To address these questions, we implemented a multidisciplinary research approach. Our investigation includes first-hand accounts, such as an interview with a former female hacker, known cases of women convicted for their involvement in cybercrime, proprietary intelligence gathered during investigations, and analysis of activity across platforms used by cybercriminal networks. Additionally, we incorporated a socio-economic analysis of Russian-speaking countries - Russia, Belarus, and Ukraine - particularly as these factors influence gender dynamics in both legitimate and illicit labor markets, as well as the relationships between men and women.
Through these diverse channels, we aim to provide a nuanced understanding of the gender dynamics within Russian-speaking cybercrime, shedding light on the unique roles women play both historically and in the present day - from technical positions to more organizational functions. This holistic approach allows us to offer a more comprehensive perspective on the role of women in cybercrime, which has traditionally been framed as a predominantly male domain.
Key Findings
- Russian-speaking cybercrime is a complex landscape characterized by its national and gender diversity. While Russian and Russian-speaking cybercrime involves a geographically diverse array of threat actors from different nationalities, a significant difference between the two lies in the geopolitical alignment of the threat actors and their operations. Russian cybercrime is often characterized by a direct or indirect alignment with the Russian government.
- The full extent of the presence of women in Russian-speaking and Russian cybercrime is unknown. Based on research incorporating qualitative data, including investigations of known cases and proprietary intelligence, it was concluded that the percentage of females in cybercrime is significantly lower than that of males, with the underground remaining predominantly male-dominated.
- It was identified that women present in cybercrime historically engage in various activities, including carding operations, ransomware, hacking, and the production of fake documents. With the emergence of hacktivist-like groups following Russia's invasion of Ukraine in February 2022, a notable shift has been observed, with women increasingly assuming leadership and operational roles in informational campaigns that are widely implemented as part of hybrid warfare.
- As identified, the dynamics of the relationships between men and women in Russian-speaking cybercrime closely reflect the social norms across Russian-speaking countries. Through a socio-economic analysis of Russia, Belarus, and Ukraine, it was observed that social norms dictate gender roles, with women being seen less frequently in high-ranking positions. This reflects the dynamics of cybercrime, where, although women are accepted, they are often perceived as less capable than men, with gender stereotypes and ageism also playing a role in this perception.
- The impact of ongoing geopolitical tensions between Russia and Ukraine has led to the further evolution of the roles that women occupy in society, which will likely evolve and be reflected also in the realm of offensive cyber operations and cybercrime. Due to Russia and Ukraine including cyberattacks as a component of their military strategies, women are set to become much more involved in the cyber domain, as opposed to fighting on the battlefield.
Part I: The Historical Role of Women in Russian-Speaking Countries: A Socio-Cultural and Economic Perspective
To better understand the role of women in Russian-speaking cybercrime, it is essential to analyze the overall status of women in their respective societies, considering their cultural backgrounds. Various factors, including socio-cultural and economic influences, must be taken into account, as these significantly shape daily life and define women's roles within society. By examining these broader societal contexts, we can gain a more comprehensive understanding of how gender dynamics influence both the involvement of women in criminal networks and the roles they assume within these networks, as well as the nature of the relationships between men and women.
Understanding the National Diversity and Variety of Cultural Backgrounds in Russian-speaking Cybercrime
In the context of Russian-speaking cybercrime, attribution, and cultural analysis presents significant challenges due to the national diversity of the actors involved. Therefore, distinguishing between Russian and Russian-speaking cybercriminals is crucial for accurate assessment. The term "Russian cybercrime" is often mistakenly used to refer to criminal activities carried out by individuals of Russian nationality proficient in Russian language, and typically operating within Russia's borders. However, many cybercriminals involved in Russian-speaking cybercrime are not Russian nationals; they often originate from the Commonwealth of Independent States (CIS) and the broader set of former Soviet Union countries, hold different citizenships or dual citizenships, and/or reside outside of Russia.
*There are 15 former Soviet Union countries, including Armenia, Azerbaijan, Belarus, Estonia, Georgia, Kazakhstan, Kyrgyzstan, Latvia, Lithuania, Moldova, Russia, Tajikistan, Turkmenistan, Ukraine, and Uzbekistan.
Collaboration among cybercriminals from various national backgrounds, often united by the Russian language, is common within Russian-speaking cybercrime. This national diversity characteristic, grounded in a shared linguistic trait, has facilitated the formation of cross-border cybercriminal networks, creating an extensive and interconnected system of illicit activities. Understanding this significantly advances investigation efforts, thus providing a higher chance for operational disruptions and arrests. More on the characteristics of Russian-speaking cybercrime can be found in this report from Analyst1.
Multiple pieces of evidence of national diversity were confirmed by ongoing law enforcement actions against Russian-speaking cybercriminals. A notable example is the TrickBot/Conti case and two rounds of sanctions that took place against its members last year.First, on February 9, 2023, the U.S., in coordination with the U.K., against seven members andsecond, on September 7, 2023, additional sanctions targeted eleven members of the group. The list of sanctioned members, while primarily consisting of Russian nationals, also includes some Ukrainian citizens, highlighting the national diversity within Russian cybercrime.
Close collaboration between nations in the realm of cybercrime was also highlighted in Europol'sreport, "Decoding the EU’s Most Threatening Criminal Networks," which applies equally to both traditional crime and cybercrime. According to the analysis, it was found that Eastern European nationals from Belarus, Czechia, Hungary, Moldova, Poland, Russia, Slovakia, and Ukraine often cooperate in changing compositions. Another national group identified as closely collaborating with Russians includes nationals from the Baltic States (Estonia, Latvia, and Lithuania). In addition, Russians and Ukrainians were identified as the most represented nationalities within criminal networks specializing in cyberattacks as their primary activity, while others engage in cybercrime to support fraud and money laundering activities.
While each of the countries involved in Russian-speaking cybercrime is unique in terms of culture and socio-economic development, Russia, Belarus, and Ukraine offer a distinctive framework for comparative analysis due to their geographic proximity and shared socio-cultural traits. In the next section, we will conduct a socio-economic analysis to examine how social and cultural factors shape the roles of women in these societies, as well as the dynamics between men and women. This analysis will provide a deeper understanding of women’s presence and participation in cybercrime.
Socio-economic Analysis of Russia, Ukraine, and Belarus: Historical Practices
An analysis of gender roles in Russia, Belarus, and Ukraine reveal both shared historical and socio-cultural foundations as well as unique developments shaped by each country's specific socio-economic context. These countries historically share deep-rooted cultural, linguistic, and political ties, stemming from their common heritage within the former Soviet Union. This shared history has resulted in similar institutional structures, values, and norms that continue to influence various aspects of life, including gender roles and societal expectations.
During the Soviet period, gender equality was officially promoted, with women being integrated into the workforce. The economies of all three countries were similar during this period. All offered fewer professional opportunities for women outside of traditionally feminine roles, including manufacturing, which was typically dominated by men. Women’s contributions to Science, Technology, Engineering, and Mathematics (STEM) fields were substantial during this era, and they were even encouraged to enter these fields as part of the broader state-promoted ideology of gender equality. However, women, while present in professional fields, are often taking lower-paying jobs across education, healthcare, and service sectors.
In all three countries, women were also expected to fulfill the roles of mothers and caregivers, with the expectation being deeply rooted in cultural norms and historical practices. This dual burden reflects a broader post-Soviet legacy, where women’s roles have been shaped by both historical policies of state socialism, which promoted women's formal workforce participation, and persistent cultural expectations regarding family responsibilities. Men are typically seen as breadwinners and authority figures within families, with overlapping traditions among Russia, Belarus, and Ukraine that reflect patriarchal values. These traditional views often dictate that men should be the decision-makers, leading to unequal power dynamics in romantic, familial, and professional relationships.
The Soviet Union was one of the first regimes to introduce legislation granting women equal rights in education and professional fields, theoretically placing them on par with men. However, they were often underappreciated and overshadowed by the dominance of men, a pattern that has evolved but persists in professional settings across Russia, Belarus, and Ukraine. They were rarely given leadership roles in research institutions or significant recognition for their achievements. In male-dominated sectors like engineering and physics, women frequently faced discrimination, being viewed as less capable than their male counterparts.
In addition to the existing gender disparities, women in Russia, Belarus, and Ukraine often face another significant layer of discrimination based on age. Ageism exacerbates the gender inequality women experience, particularly in professional and academic environments, limiting their opportunities and contributing to a culture that values younger women while marginalizing older ones. This age-based discrimination is deeply ingrained in the socio-cultural fabric of these countries and has profound implications for the roles women play in both legitimate and illicit sectors.
Ageism intersects with traditional gender roles, where older women are often seen as less dynamic or innovative compared to their younger counterparts, reinforcing stereotypes that limit their professional advancement. In these societies, there is a pervasive expectation that younger women will balance both professional and family roles, while older women are expected to focus more on domestic responsibilities, reducing their professional visibility.
The Alla Witte and TrickBot Case
The case of Alla Witte provides valuable insights into the national diversity within Russian-speaking cybercrime, as well as male perceptions of women and the relationship between the two genders. Alla Witte, also known as MAX, was part of the TrickBot group, a Russia-based organization responsible for ransomware operations and closely affiliated with the Conti group from approximately November 2015 to January 2021.
According to theindictment, “Witte was a Malware Developer for the TrickBot Group, overseeing the creation of code related to the monitoring and tracking of authorized users of the Trickbot malware, the control and deployment of ransomware, obtaining payments from ransomware victims, and developing tools and protocols for the storage of credentials stolen and exfiltrated from victims infected by TrickBot.”
Despite a wide announcement of Witte as a Latvian national, she is Russian by her origin and cultural background. Alla Witte (maiden name Klimova) was born in the Soviet Union, Rostov-on-Don in 1965 and moved to Riga, Latvia in 1983. Latvia was a popular place to live for many Russians who immigrated there during the post-warimmigration period. It became a home to a significant Russian-speaking population sharing linguistic and cultural connections to Russia. In 2021, the Latviancensus reported that approximately 464,000 people identified as ethnic Russians, accounting for over 24% of the country’s population.
Prior to herarrest, which was announced in June 2021, she had lived in Suriname with her husband, a citizen of the Netherlands. On February 4, 2021, the Surinamese police raided the home of the Witte couple. "Four cars, a dozen armed men," Witte's husband stated in an interview with a Russianmedia outlet. The house was thoroughly searched, and all electronic communication devices were confiscated. Alla Witte was taken to the police station, where her passport was stamped, prohibiting her from returning to the country. She was then put on a plane to the United States, where she faced 19 charges, including computer fraud, identity theft, and conspiracy to commit money laundering.
When examining Witte’s online presence, multiple aspects of her private life and personality emerge. She graduated from the University of Latvia in 1988 with a Bachelor of Science in Mathematics and has held various positions throughout her career, including programmer engineer, sales manager, math teacher, and web developer, according to herLinkedIn profile where she is registered as Alla Klimova, using her maiden name.
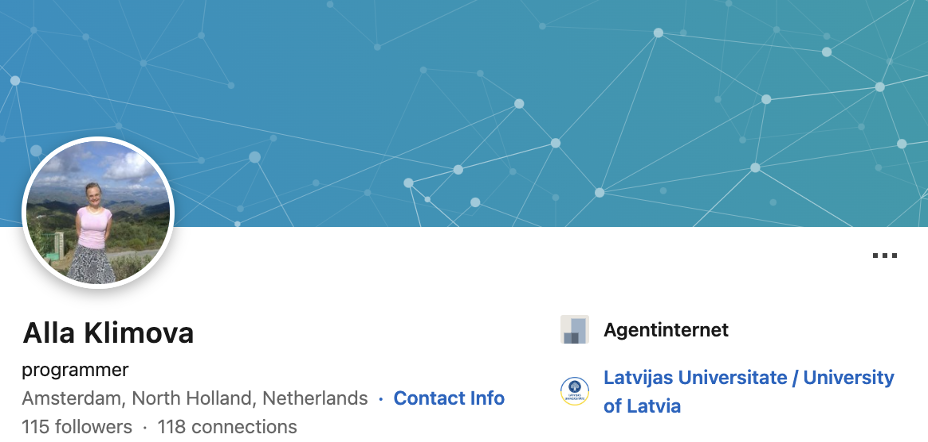
On her website promoting her web development services, she presented case studies and highlighted some of her interpersonal skills, including her commitment to continuous professional growth. She stated, “If I encounter unfamiliar technical issues while working, I fill that gap in my knowledge (all benefits are available on the internet at any time). This provides me with a constant growth of skills in site layout of varying complexity.”
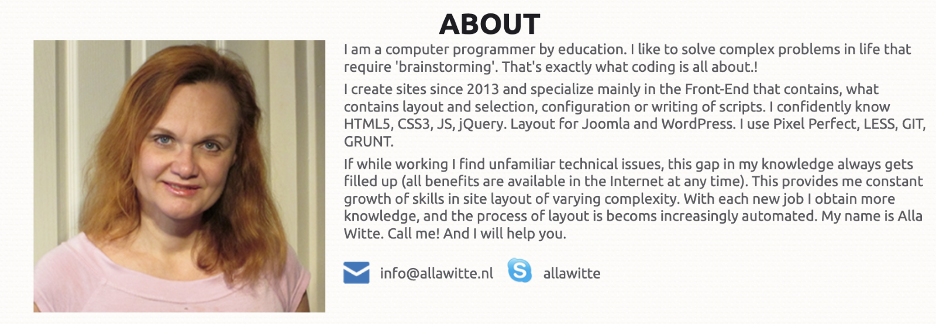
Given Witte’s diverse places of residence and her acquisition of multiple languages, including English, Latvian, and Dutch, she maintained her connections to Russia. Witte’s profile was identified across multiple Russian job websites where she also used her maiden name Klimova to register an account. Based on the indictment, which details TrickBot's approach to hiring developers through Russian and Belarusian job websites, Alla Witte was potentially recruited by actors via one of these platforms. Her native proficiency in Russian, a key criterion for acceptance into Russian cybercrime, allowed her to integrate into the TrickBot group, where she utilized her programming skills.
Based on the TrickBot/Conti chats that were leaked in February 2022 following Conti’s public announcement of support for the Russian government, several insights into Witte’s relationship with members of the group emerged. In particular, syndicate members expressed concern regarding Witte’s arrest and attempted to arrange legal representation for her in court, including efforts to transfer funds to cover their services. “There are 50 episodes related to our case. She is likely to be prosecuted as a Russian hacker, with a political undertone to this case,” stated an actor operating under the moniker Mango on May 20, 2021.

“I found a very good and licensed lawyer who reviewed the case and said that it is quite challenging. There is a high likelihood of receiving a prison sentence, and the best-case scenario would be to secure the minimum sentence and pursue a plea deal to facilitate an early release from jail,” Mango added in the following message.

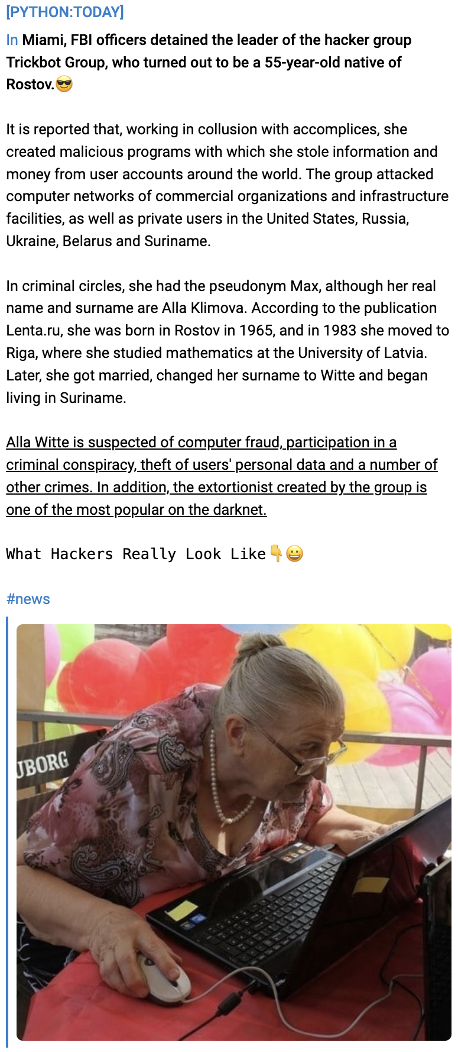
Another notable aspect is that the actors spoke freely and openly about Witte’s gender. If the theory of hiring her through the website holds true, her being a woman did not stop them, and they seemed to know her gender from the beginning. However, there was a clear tone of sarcasm regarding her age, reflecting one of the dynamics and prejudices present in Russian-speaking societies concerning women's age, which we discussed earlier in the research. "We were slightly mistaken about Alla’s age; she’s not young at all; she's 55 years old.))))) By Wednesday, I will try to find a way to send money to the lawyer. He’s started working on the case and is attempting to establish contacts with her relatives. Actually, being 55 might be advantageous in this situation; she might be able to portray herself as a victim of circumstances due to her age," Mango said in a message to Stern on June 5, 2021.

Another notable cultural observation regarding women in Russian-speaking societies emerges from reporting Witte’s arrest by official Russian media outlets and private Telegram channels. Both sources portray Alla Witte in an unexpected light, challenging the accepted stereotypes of hackers. For instance, on the private Telegram news channel “Python Today,” a user posted an image of an unknown elderly woman with a news clip about Witte, accompanied by the sarcastic caption, “What hackers really look like.”
In other reporting, an article by the Russian media outlet “Present Time” was titled “A Math Teacher and Criminal Vacancy,” presenting two contradictory references that do not align with perceived stereotypes, in addition stating Witte’s age. This further reinforces societal perceptions of women and the roles they typically occupy in tech industries, that in turn closely aligned with cybercrime, where the stereotypical portrayal of hackers is usually a young man.

The case of Alla Witte exemplifies the complexities of gender dynamics and the presence of women within Russian-speaking cybercrime. Several key insights emerge from her story: while Russian-speaking cybercrime remains a heavily male-dominated field, there is still acceptance of women within its ranks. However, this acceptance is often accompanied by the reinforcement of gender stereotypes, particularly those related to age. Overall, Witte's case underscores the challenges women face in navigating a landscape that, while becoming increasingly inclusive, still widely experiences stereotypes and biases.
Part II: This is a Man’s World: Roles, Motivations, and the Perception of Women in Russian-speaking Cybercrime
While the case of Alla Witte provides valuable insights, it represents only a narrow perspective on one case of women’s presence in Russian-speaking cybercrime. This singular case prompts broader questions about the overall participation of women in cybercrime: How many women are involved? What roles do they typically assume within these illicit ecosystems?
Accurately estimating the percentage of women involved in cybercrime is particularly challenging. One potential research method involves conducting linguistic and stylometric analysis of cybercrime forums, where cybercriminals maintain a strong presence. Given the specificities of the Russian language, it can often be inferred whether an individual identifies as male or female based on linguistic markers. However, while this approach might offer insights, it comes with significant limitations. Relying solely on linguistic analysis carries a low level of confidence due to the potential for obfuscation of gender or anonymity that is prevalent in these environments.
For this part of the research, we relied on two primary sources to assess the involvement of women in Russian-speaking cybercrime: 1) an interview with a former female hacker and 2) observations of underground activity within these networks. Each of these methods offers varying levels of confidence. While interviews provide a relatively high degree of reliability, observations of underground activity – though valuable – carry a lower degree of confidence due to the covert nature of these environments and the incomplete data available.
*Note: We express gratitude to the individual who participated in the interview. To respect her privacy, we are honoring her request for anonymity. For reference, we will refer to her as "Confidential Human Source (CHS)" throughout the research.
In everyday underground chatter, various topics are discussed, including the role of women in cybercrime. One conversation addresses women’s technical capabilities and presence within the cybercrime underground: “But seriously, are there any high-level women developers? There's Hasherezade, Rutkowska, etc., but that’s just a few. It seems to be a male-dominated field in general. Look at our forum, for example, we only have one woman, lisa99, present here.”
*Note: We do not hold any confirmation of the claimed XSS forum member lisa99 being a woman or involved in any illicit activities.
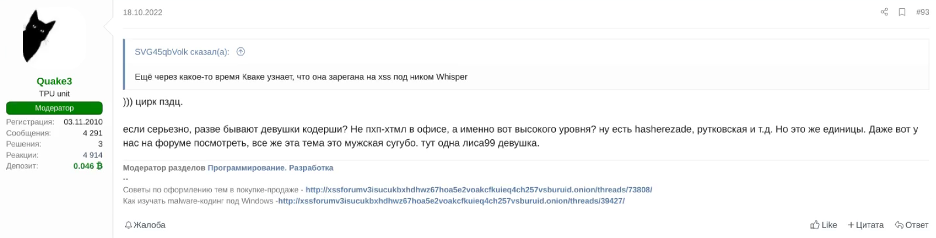
This casual exchange underscores the perception of gender disparity within the cybercriminal world, where women are often seen as rare participants, reinforcing the stereotype of male predominance. However, female presence and participation in underground cybercrime may be underestimated, as women often go to great lengths to obfuscate their identity for protection.
“This is a man’s world,” our CHS stated during the interview. Throughout her time in cybercrime, she rarely encountered other women. The only woman she ever heard of was a Russian known by the moniker "Ryabina" (moniker obfuscated), who worked in chat support and assisted someone involved in carding operations.
On cybercrime forums, CHS often hid the fact that she was a woman, choosing to present herself as a man. This was not only for self-protection but also to avoid drawing attention due to the low number of women in cybercrime and the prevalent gender stereotypes in Russian-speaking societies. Coming from a former Soviet Union country, she was acutely aware of the gender disparities, especially in STEM and IT fields, where women are often perceived as inferior.
In cybercrime, these gender norms were not just present but intensified. “I often took my boyfriend to in-person meetings,” CHS shared, revealing an intriguing dynamic within the Russian-speaking cybercrime world. Unlike what many might assume, interactions within these illicit circles often go beyond online exchanges and extend into in-person meetings, where gender biases become even more evident.
“The men in the community often looked down on me simply because of my gender. I constantly had to prove myself, and in business meetings, I often brought my boyfriend along to increase my credibility. It was frustrating, but I used men as shields when needed, especially to close deals,” she reflected on the difficulties she faced. The primary struggle she faced was the persistent dismissal of her hacking abilities, with her skills and credibility frequently undermined and questioned by those around her. Being a woman in a field dominated by men, she was constantly met with skepticism, and her advanced technical skills were often disregarded or belittled. Her capabilities were seen as an anomaly, and those in her circles - both allies and rivals - tended to downplay her achievements, often crediting her successes to luck rather than recognizing her talent and expertise. This gender bias not only challenged her ability to gain respect and trust within hacker networks but also forced her to repeatedly prove her skills in ways her male counterparts were rarely asked to do.
When discussing her motivations for joining cybercrime, her reasons were not unlike those of many others: financial hardship. The collapse of the Soviet Union drastically altered her family’s fortunes, leaving them in poverty almost overnight, like many others in that period. “This drastic shift in our financial situation left a deep impression on me, and from a young age, I started thinking about how to earn money to escape this situation. My skills in computers, math, and the IT degree I eventually earned formed the basis of my decision to pursue cybercrime.”
She first learned about hackers at around 15 or 16, stumbling upon stories on the internet. After joining chat rooms and studying the various platforms, she made her first attempt at hacking. By 17, she was actively involved, teaming up with a group of carders. Her role in cybercrime evolved over time, starting with small tasks like hacking into web panels and chat platforms, before transitioning into carding. Her victims included financial institutions and online stores from which she stole credit card information. She expanded her operations to include card production, creating counterfeit plastic credit cards that were marketed on underground forums. In addition to credit cards, she also produced fake driver's licenses and other identification documents, a process known in Russian as "отрисовка" (Eng: drawing).
Over time, she fully mastered the mechanics of bank payments within the networks she hacked and engaged in hacking financial institutions, facilitating millions of dollars in transfers. Concurrently, she sold credit card dumps and plastic cards containing this stolen data. This scheme involved various roles across different levels of cybercrime, which eventually enabled her to expand into hacking federal agencies. She found additional ways to profit, such as selling unpublished press releases for insider trading and blueprints from jet propulsion laboratories. Additionally, she managed her own botnets and wrote exploits for vulnerabilities she personally identified.
Shared experience by our CHS offers valuable insights into our understanding of women in Russian-speaking cybercrime. Her journey reflects the multifaceted roles women can play in cybercrime, highlighting both the opportunities and the challenges they face in navigating a space still dominated by men and established gender norms. With the exploration of the roles that women have historically taken in cybercrime, we will now move to the next section, which will examine the newest developments in the roles women occupy in the cyber domain today.
Part III: Women in Russian-speaking Countries Today: New Roles and Shifting Expectations Across Legal and Cybercrime Spheres
Russia’s invasion of Ukraine in February 2022 introduced new dimensions to gender dynamics in the Russian-speaking regions. In Russia, Ukraine, and to a lesser extent, Belarus, the war has introduced women into leadership roles across both legitimate and underground sectors as the men were sent to the battlefield. As a result, women have become more visible in resistance movements, digital warfare, and various initiatives that either support or oppose the war.
Due to the war, the Russian-speaking cybercriminal community has experienced an internal split. One notable event was the Conti case, a ransomware group that publicly announced its “full support of Russian government [sic]” in February 2022. This marked a significant political and ideological alignment within cybercrime circles, where groups began to take sides, aligning with either Russia or Ukraine, thus mirroring the broader geopolitical conflict.
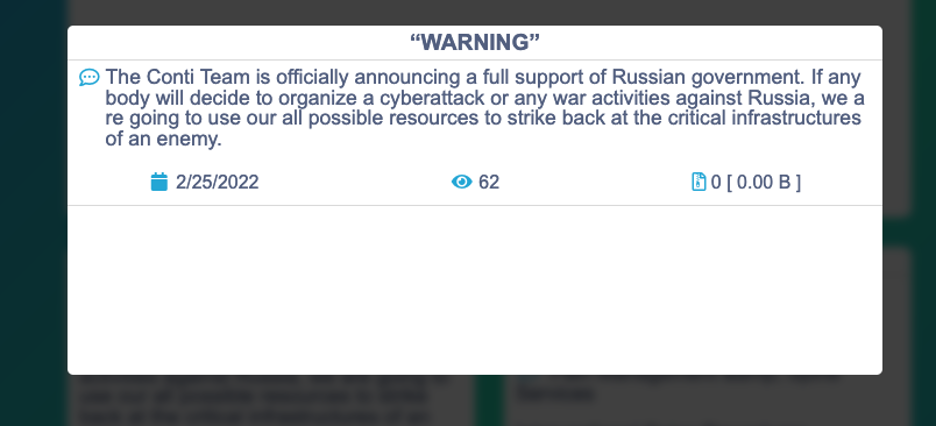
These changes demand a reevaluation of the dynamics within Russian-speaking cybercrime. The landscape has undergone considerable shifts, resulting in the emergence of new types of threats, fractures within previously unified networks, and divisions among cybercriminal actors based on nationality and political alignment. This reconfiguration has created a more complex cybercriminal ecosystem, where the lines between politically motivated attacks and financially driven crimes have become increasingly blurred.
Considering new developments, it is important to distinguish between "Russian cybercrime" and "Russian-speaking cybercrime." While both share similar characteristics, including diverse national presence and geographical distribution, Russian cybercrime is now characterized by its geopolitical alignment with the Russian government, whether directly or indirectly, with its operations closely aligned with the state’s agenda. This shift highlights how geopolitical allegiances have begun to shape the underground, influencing the alliances, motivations, and targets of cybercriminals in the region.
Hacktivist-like groups are one of the newer threats that have emerged from the current geopolitical landscape and ongoing multiple military conflicts in which Russia is involved. These groups are different from typical hacktivist groups and characterized by their high level of coordination, large membership, and activities closely aligned with state interests. The probability of government influence (direct or indirect) or support is high, as these groups often pursue specific political or ideological agendas, reflecting a more strategic and state-oriented approach to cyber operations. Given the substantial resources and support these groups receive, including significant technical and informational backing, they should be considered a high-level threat.
The Cyber Army of Russia was identified as one of the groups engaging in these hacktivist-like activities. Yuliya Pankratova, a woman, was identified as one of its members, whose case and the history of the group we will explore in the next section.
The Mother of Bears: Yuliya Pankratova of the Cyber Army of Russia, Ideological Leader and the Female Face of Hacktivist-like Groups
The case of Yuliya Vladimirovna Pankratova demonstrates the new realities surrounding hacktivist-like groups activities and the evolving roles women take on today. On July 19, 2024, Pankratova, a member of the Cyber Army of Russia Reborn (CARR), was sanctioned along with Denis Olegovich Degtyarenko. While Pankratova was identified as the group’s spokesperson, overseeing its operations, Degtyarenko was named as a key hacker involved in multiple breaches, including the compromise of industrial control systems (ICS) belonging to water utilities in towns across the U.S.
CARR emerged around March 2022, alongside other pro-Russian groups such as KillNet, with their rise directly correlated to the invasion of Ukraine in February 2022. Initially portraying themselves as a typical hacktivist group, it soon became evident that their operations were far from traditional, displaying characteristics of a more sophisticated, state-aligned agenda.
Russian state involvement was assessed as likely with moderate confidence byMandiant in their report uncovering CARR operations, which were connected to the Russian military intelligence (GRU) unit called Sandworm (also known as APT44). It was revealed that APT44 is behind multiple online personas tied to various hacktivist groups, including Xaknet, CARR, and Solntsepek. APT44 and CARR were involved in an attack on water tanks in Muleshoe, Texas, manipulating the human-machine interface (HMI) to activate the pumps, causing the water level to overflow. The precise level and methods of cooperation between CARR and APT44 have currently not been disclosed by Mandiant, however.
The attack on the water tanks in Texas was accompanied by informational support via the group’s Telegram channel, which serves as their primary communication platform. On January 18, 2024, the Cyber Army of Russia posted a video showing actors inside a compromised network. The video began with a woman’s robotic voice saying in Russian, "Hi everyone, today we have U.S. infrastructure facilities, particularly water supply systems. Enjoy the video." (Rus: Всем привет. На сегодня у нас объекты инфраструктуры США, а именно системы водоснабжения.)
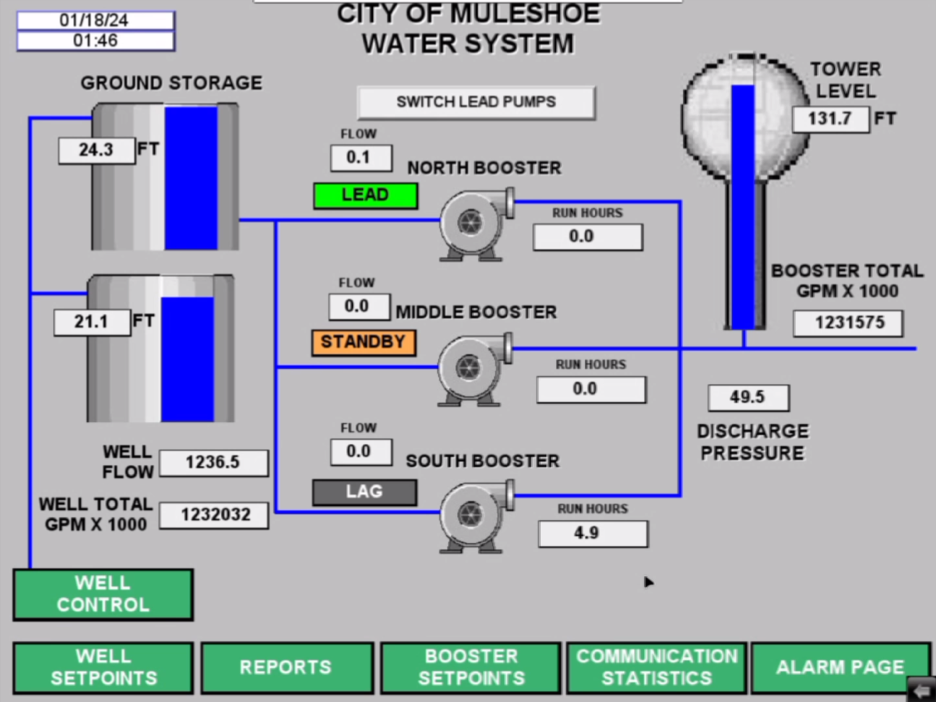
This video, like many others, is part of the informational support efforts for cyberattacks, which in turn are part of a hybrid warfare strategy aimed at supporting ongoing conflicts involving Russia. The strategy is designed to gain an advantage through psychological pressure and information operations campaigns. Yuliya Pankratova, identified as responsible for public relations and managing the group’s Telegram channel, is believed to be the one crafting these messages. The voice used in the video of the attack on Texas' water tank is also very likely hers.
However, despite this subtle hint – such as the use of a female voice in the video – the active presence of women within the group has not been widely promoted or highlighted prior to the sanctions announcement. It is noteworthy to observe how events unfolded following identities of Pankratova and other members involved being revealed. Rather than stepping back, Pankratova and the group amplified the presence of women within the group’s operations, using her role to underscore to embrace diverse participation and adapt to modern-day information warfare strategies.
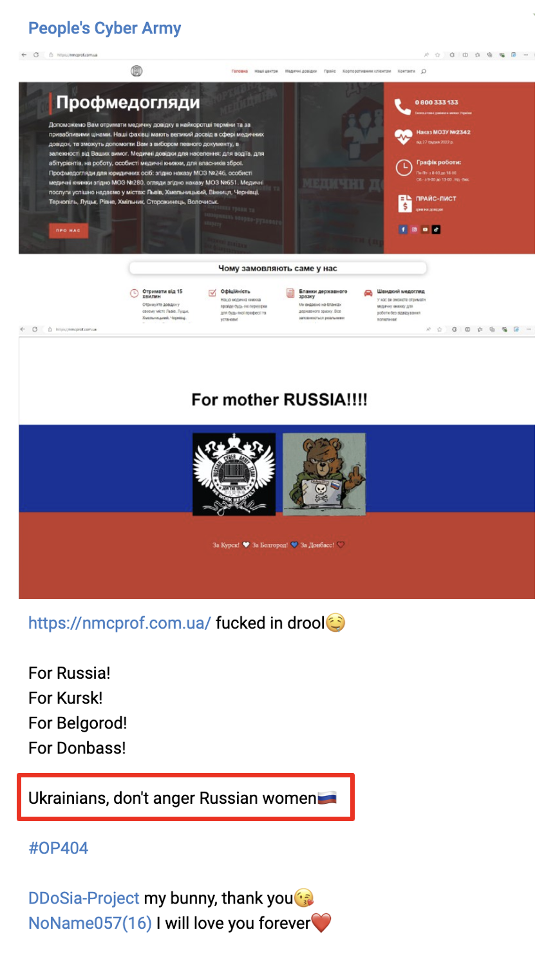
On August 19, 2024, exactly one month after the sanctions were announced, CARR posted a message to its Telegram channel claiming responsibility for a defacement attack against a Ukrainian entity. They stated that the attack was carried out in collaboration with other groups and highlighted the involvement of different roles, including a "designer, defacer, and DDoSer."
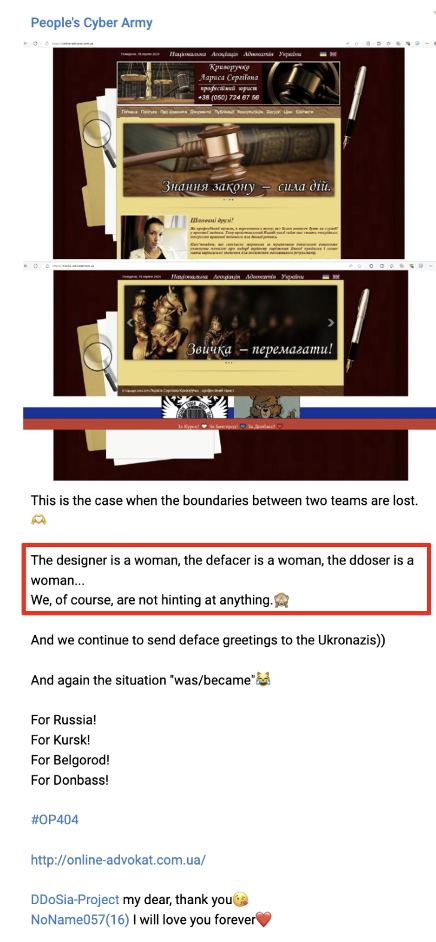
The following day, on August 20, 2024, the group claimed responsibility for another attack on a Ukrainian entity, with another message: "Ukrainians, don’t piss off Russian women." This remark not only asserted the operational capabilities of the group but also suggested the growing prominence of women within their ranks. We can’t confirm the claim of the wide involvement of women, but it does show the celebration of women in an attempt to inspire other women to join the ranks of their digital army.
* Note: We purposely substituted the slang term originally used in the message with "Ukrainians" in the translation, as the original term contained highly derogatory language.
Pankratova’s, who refers to herself as Mother of Bears on Telegram, continued involvement and the group's deliberate highlighting of her participation have promoted the presence of women within the group. On September 5 and 6, 2024, she posted personal photos wearing swag that mimicked military uniform colors, featuring the logos of groups that collaborate with CARR, including NoName057. Both photos were accompanied by casual messages showcasing her fighting spirit. One message read, “To all of my friends, have a good weekend; to all of my enemies, it goes without saying," referencing the middle finger she displays in the photo.
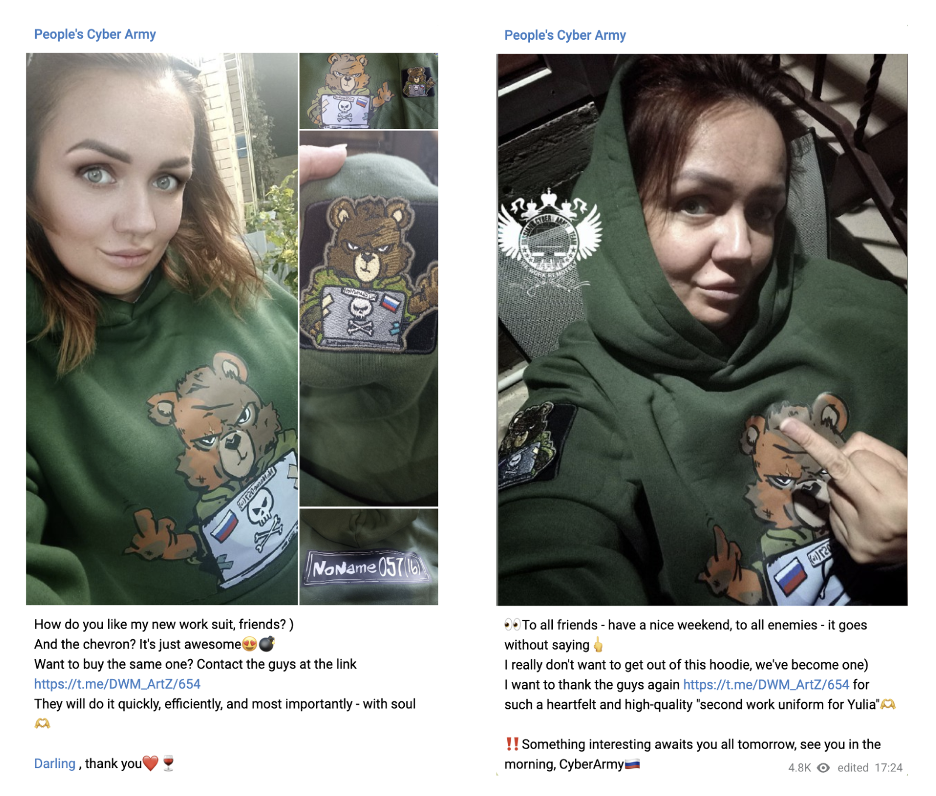
The promotion of gender diversity within hacktivist groups serves two purposes. First, to publicly respond to the sanctions imposed by the U.S., which is considered one of these groups' perceived enemies, aligning with the overall state agenda. And second, to promote women's presence for internal morale and external messaging. By positioning women as central figures in these activities, the group draws on traditional and cultural narratives of strength and resilience to support internal propaganda efforts. This aligns with Russia's broader militarization of society, where various spheres of life, including cybercrime, have become blended with state-driven narratives and military objectives.
Redefining Boundaries
Women’s roles in Russian-speaking cybercrime, though less visible than men’s, are evolving and significant. They occupy positions from technical to leadership in hacktivist groups, challenging traditional gender dynamics. This blog examines their contributions and the socio-cultural factors shaping their participation.
For a deeper exploration into cybercrime, the SANS FOR589: Cybercrime Intelligence course provides hands-on insights into the structure of cybercriminal organizations, roles within these networks, and techniques for intelligence practitioners. Discover methods for uncovering hidden networks, understanding cybercrime ecosystems, and applying attribution strategies. Sign up now for the course or request a free demo to see how the FOR589 course can elevate your cyber intelligence skills. Visit the FOR589 course page to get started!
.png)




