SEC595: Applied Data Science and AI/Machine Learning for Cybersecurity Professionals


Experience SANS training through course previews.
Learn MoreLet us help.
Contact usBecome a member for instant access to our free resources.
Sign UpWe're here to help.
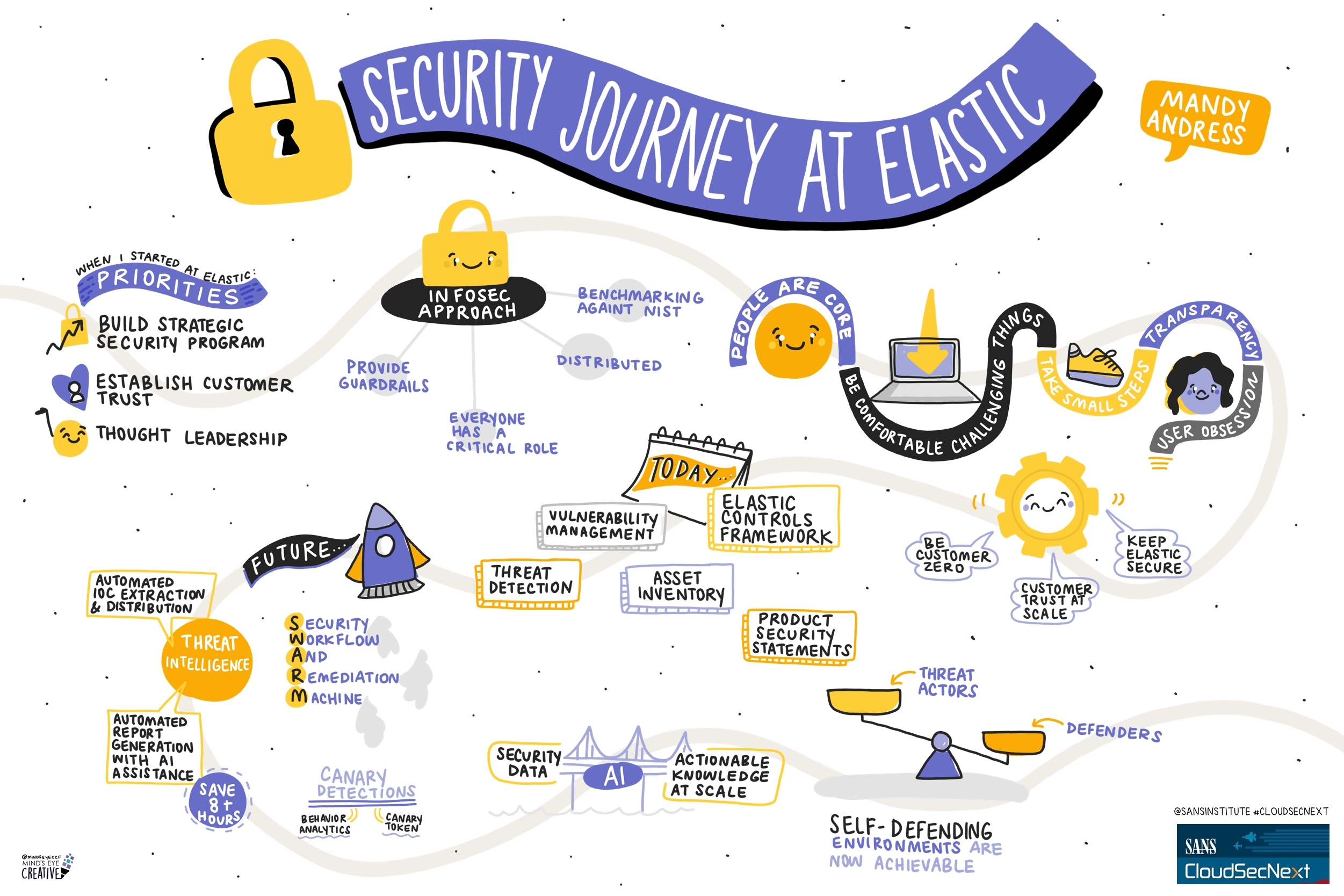
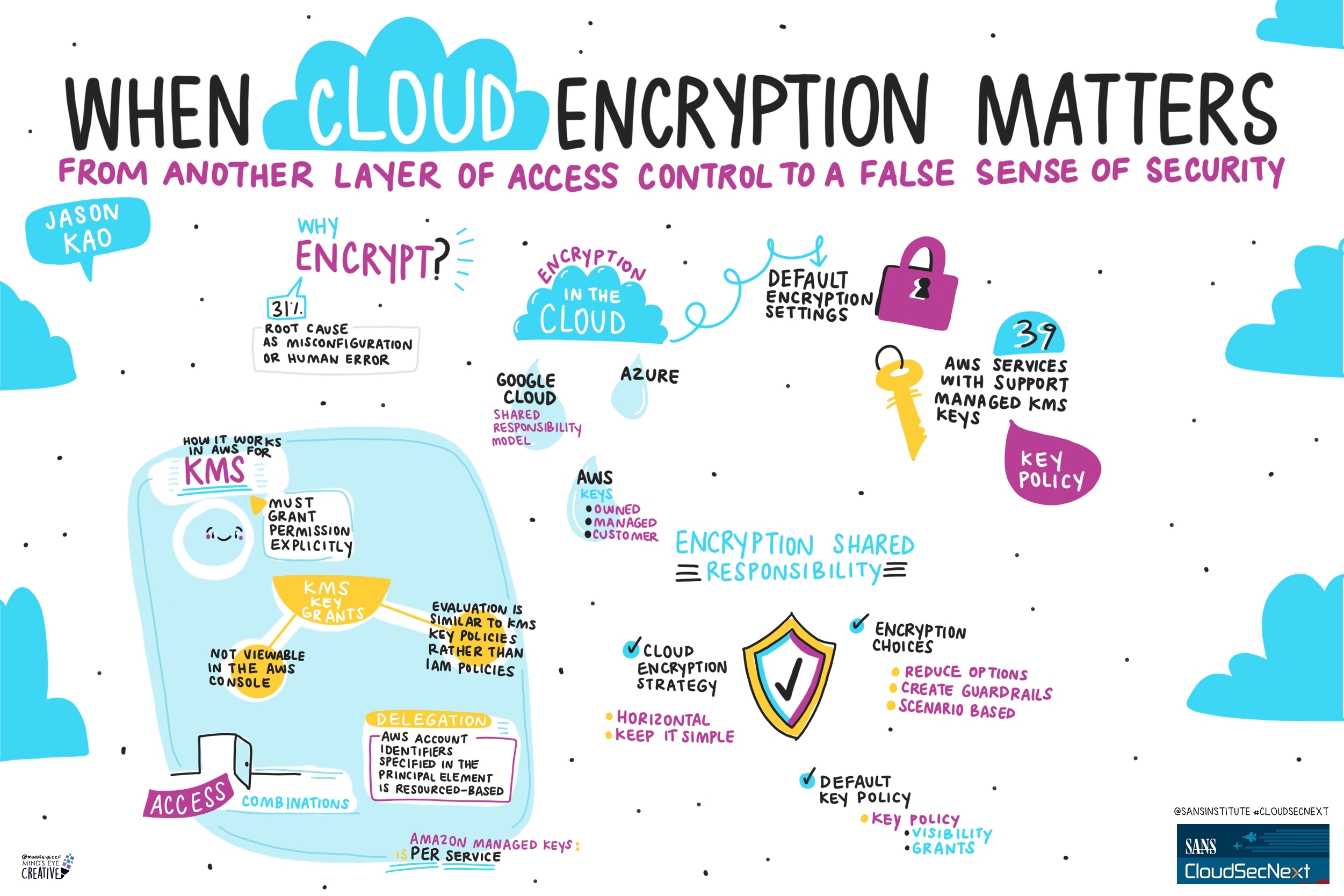
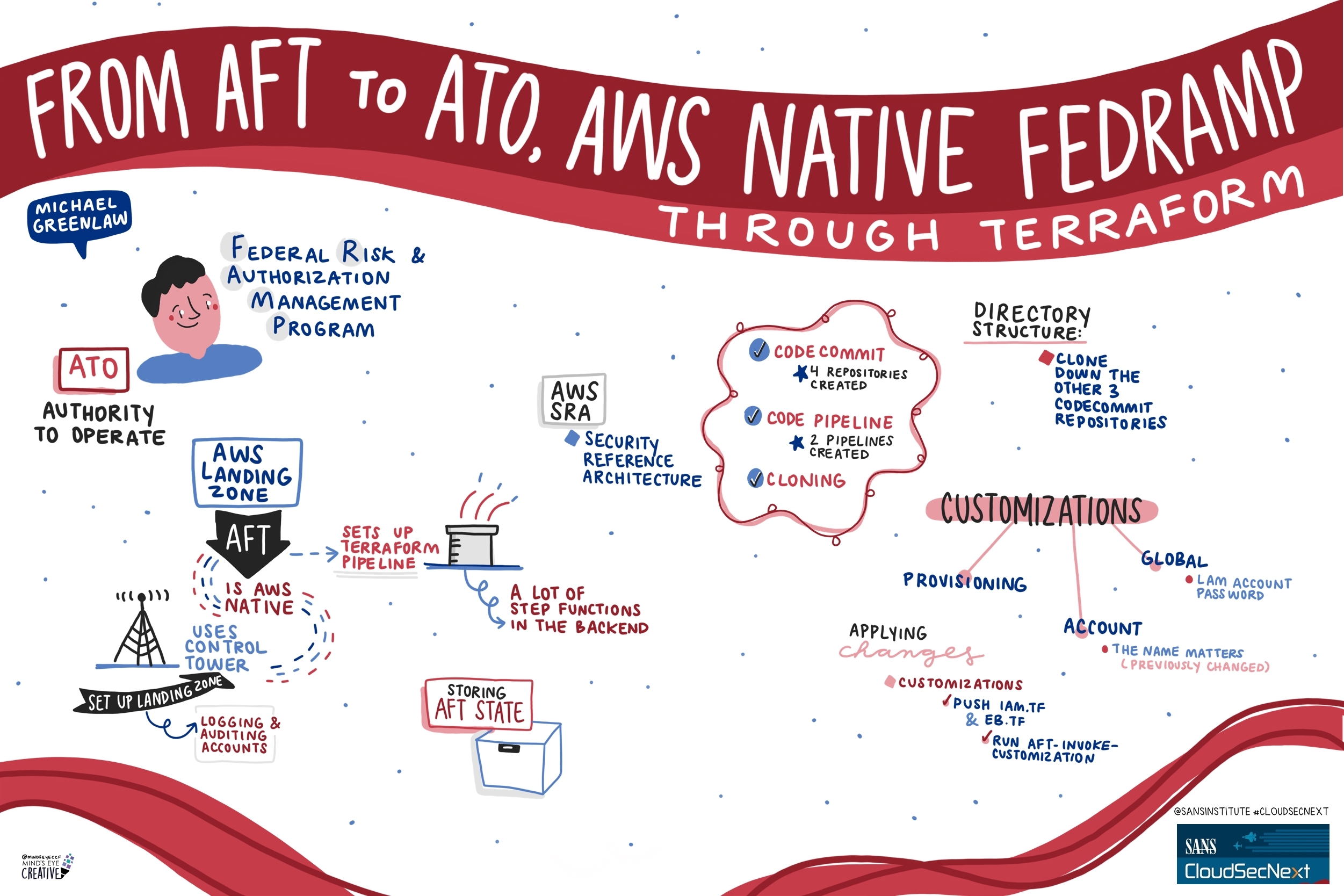
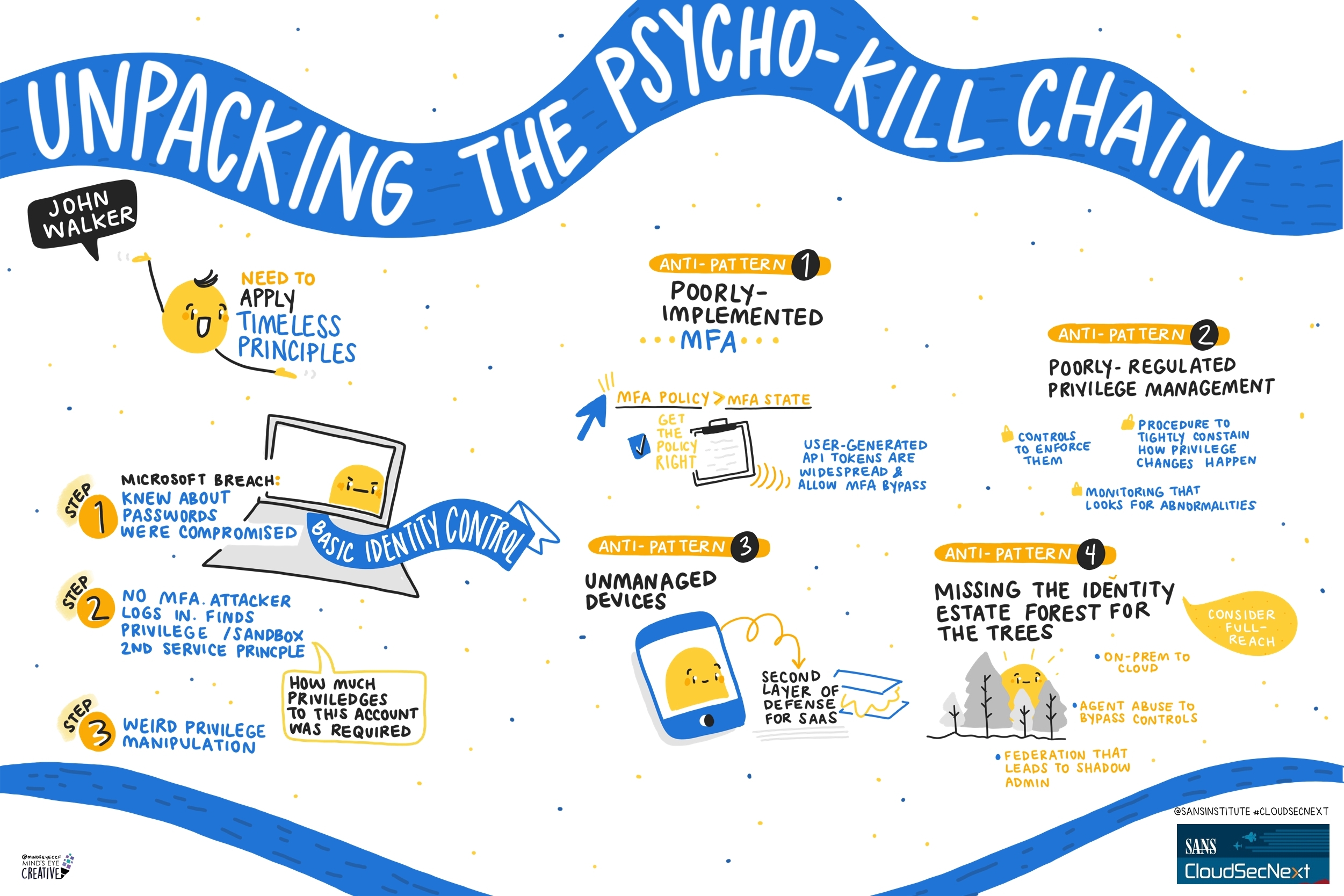
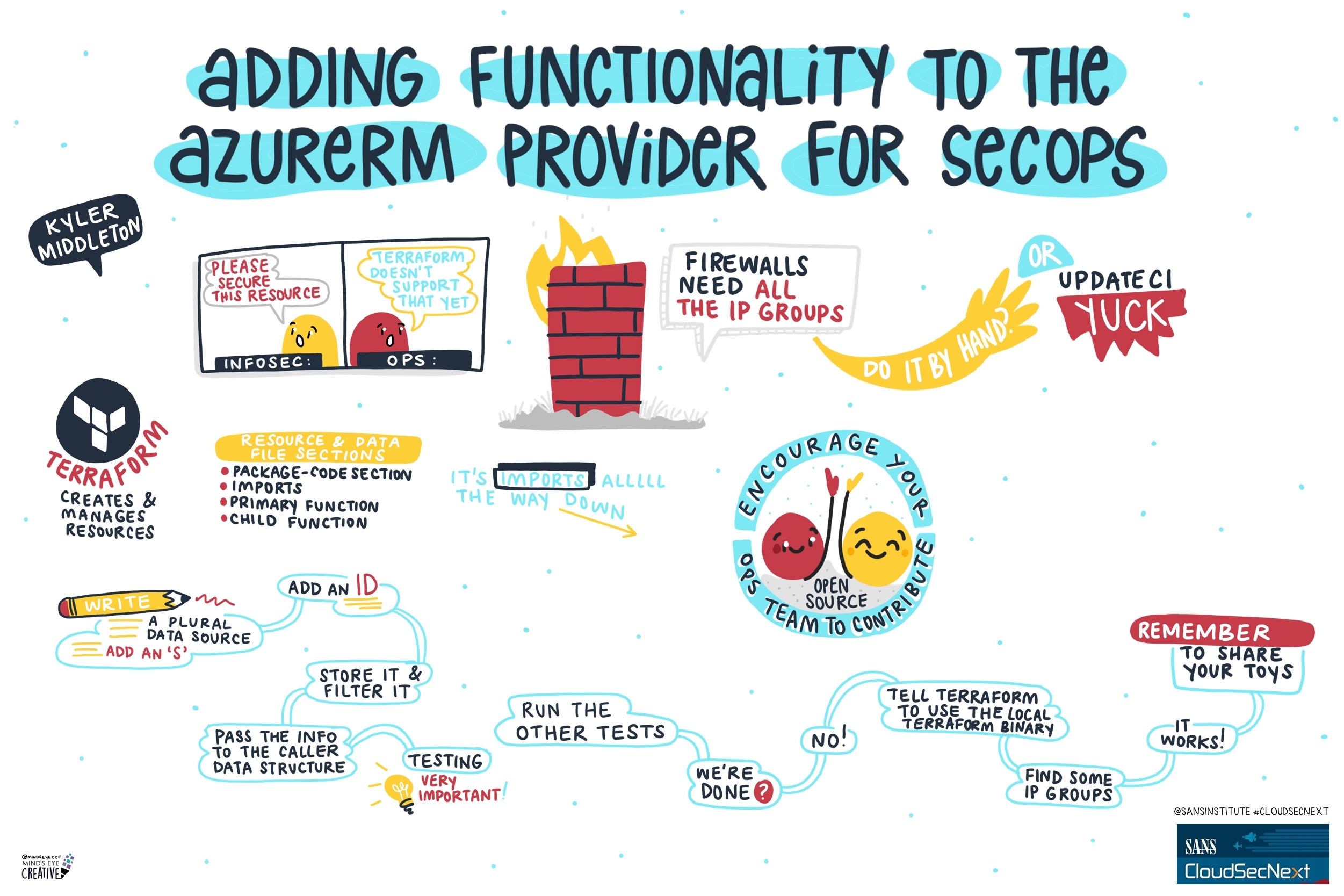
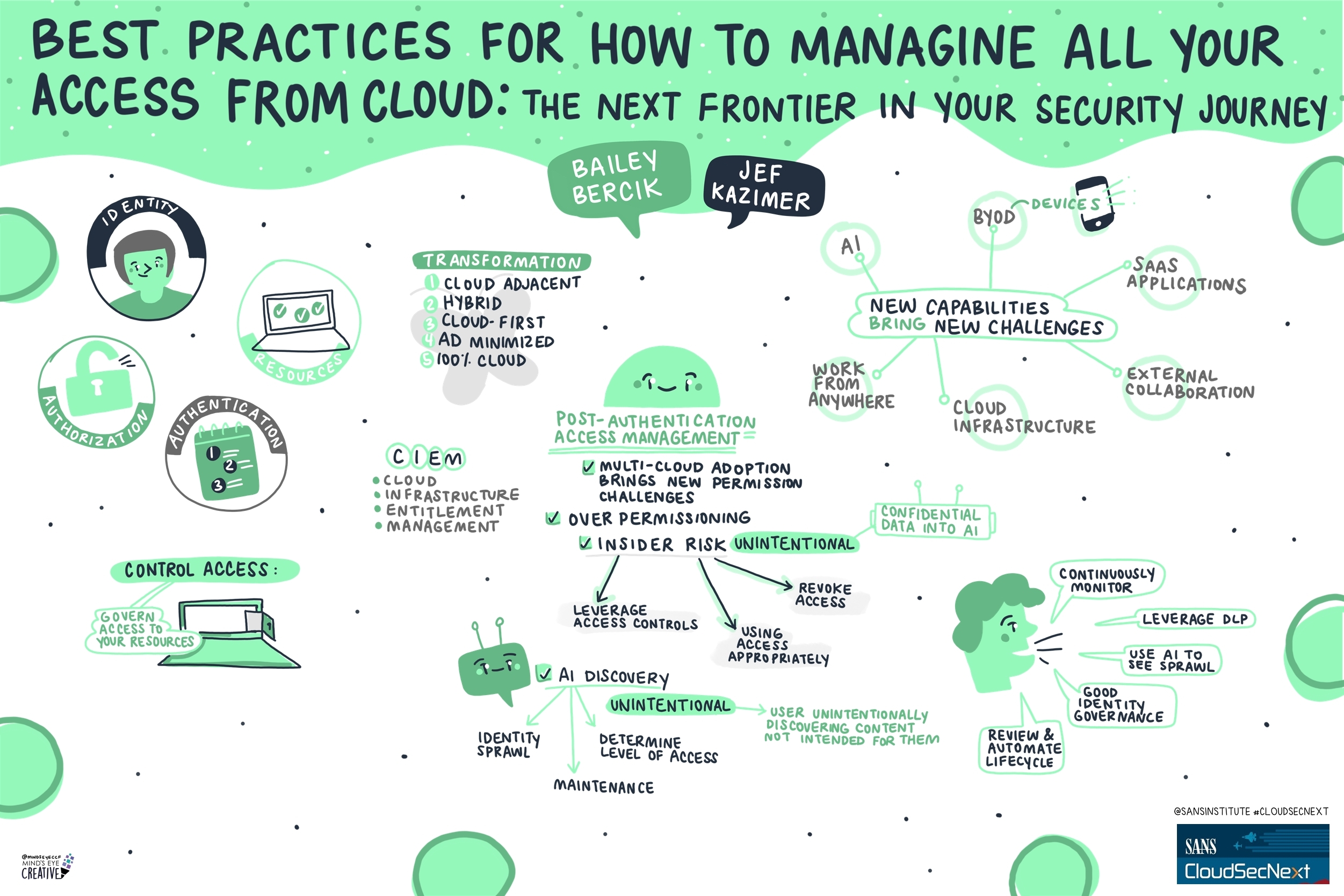
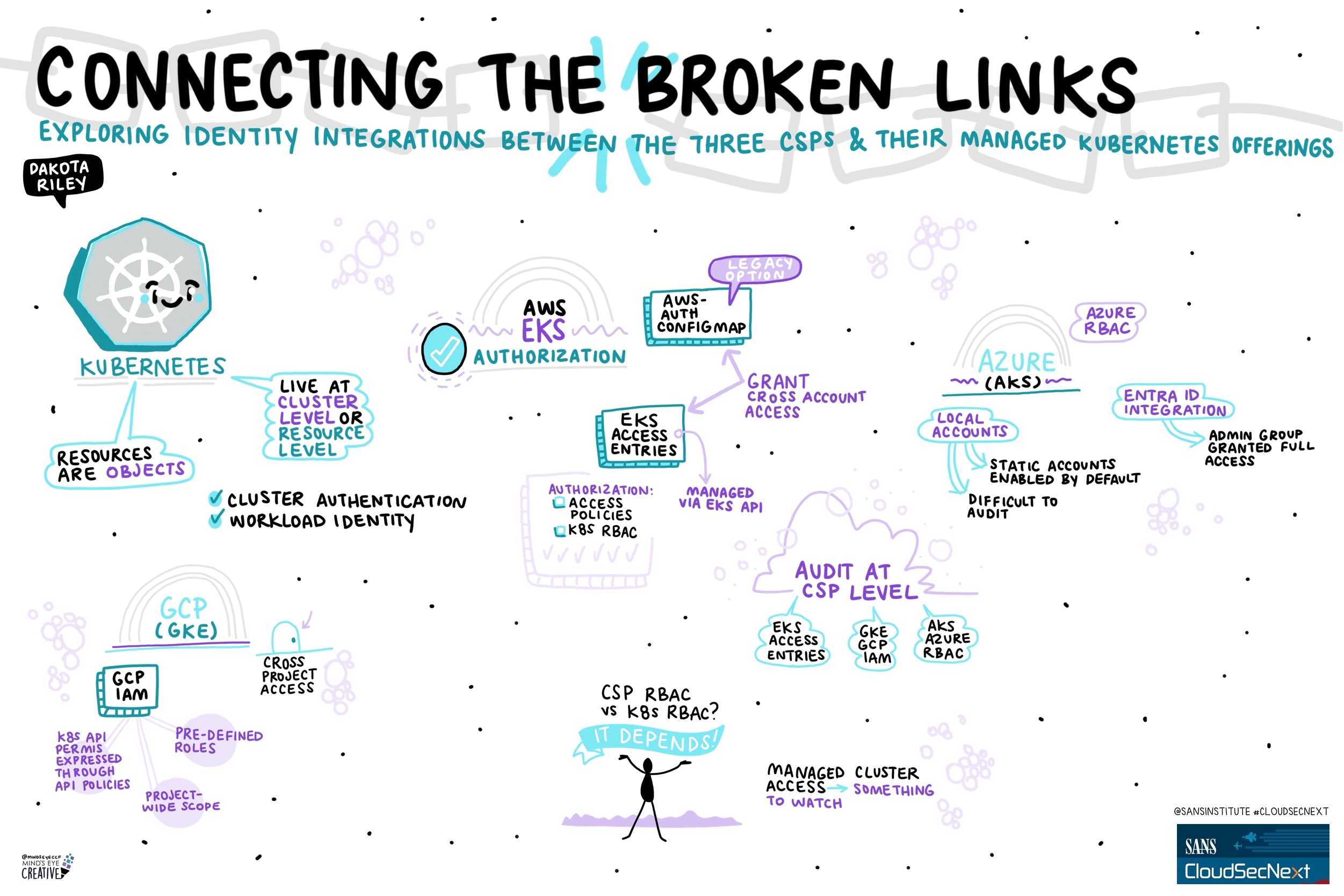
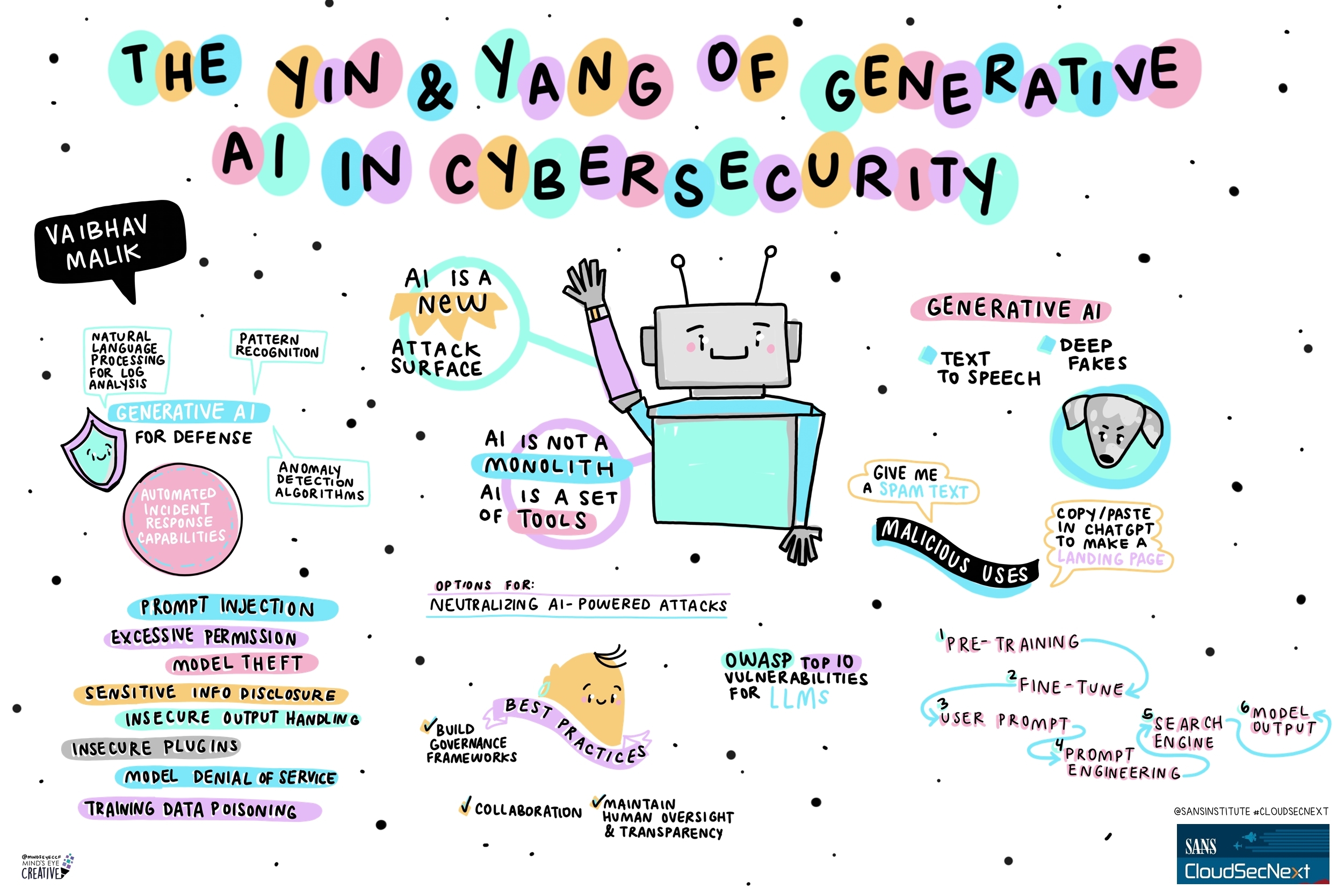
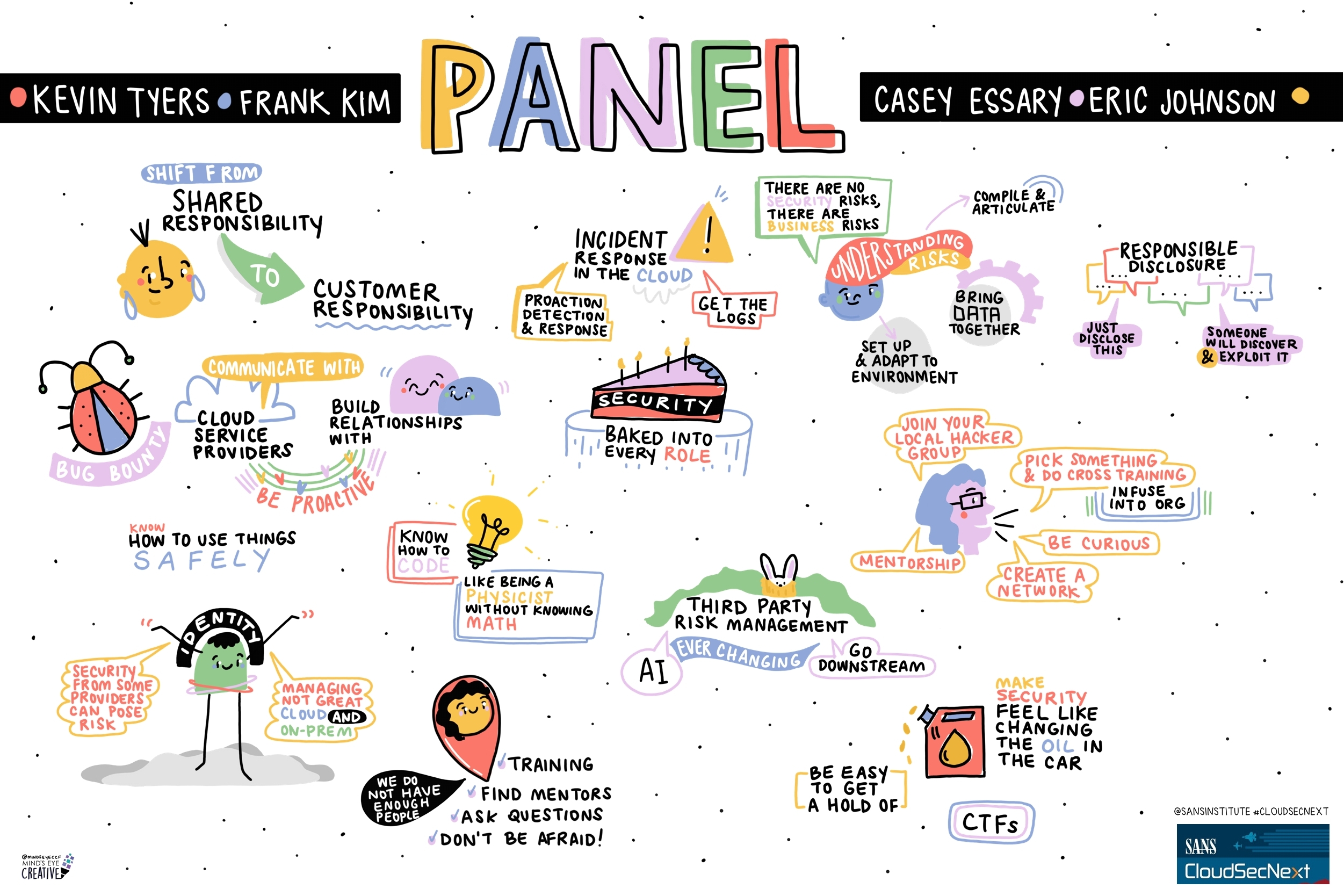
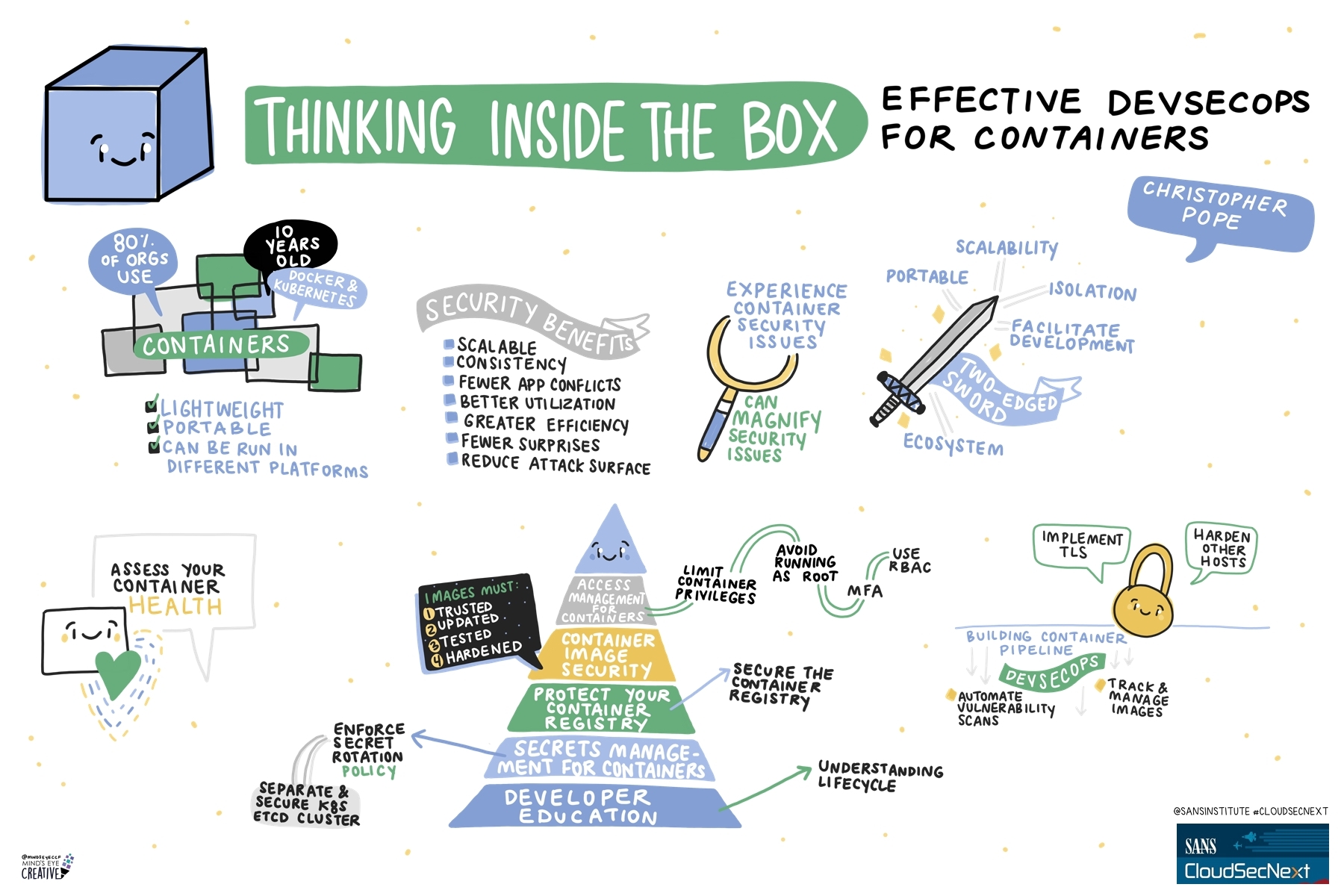
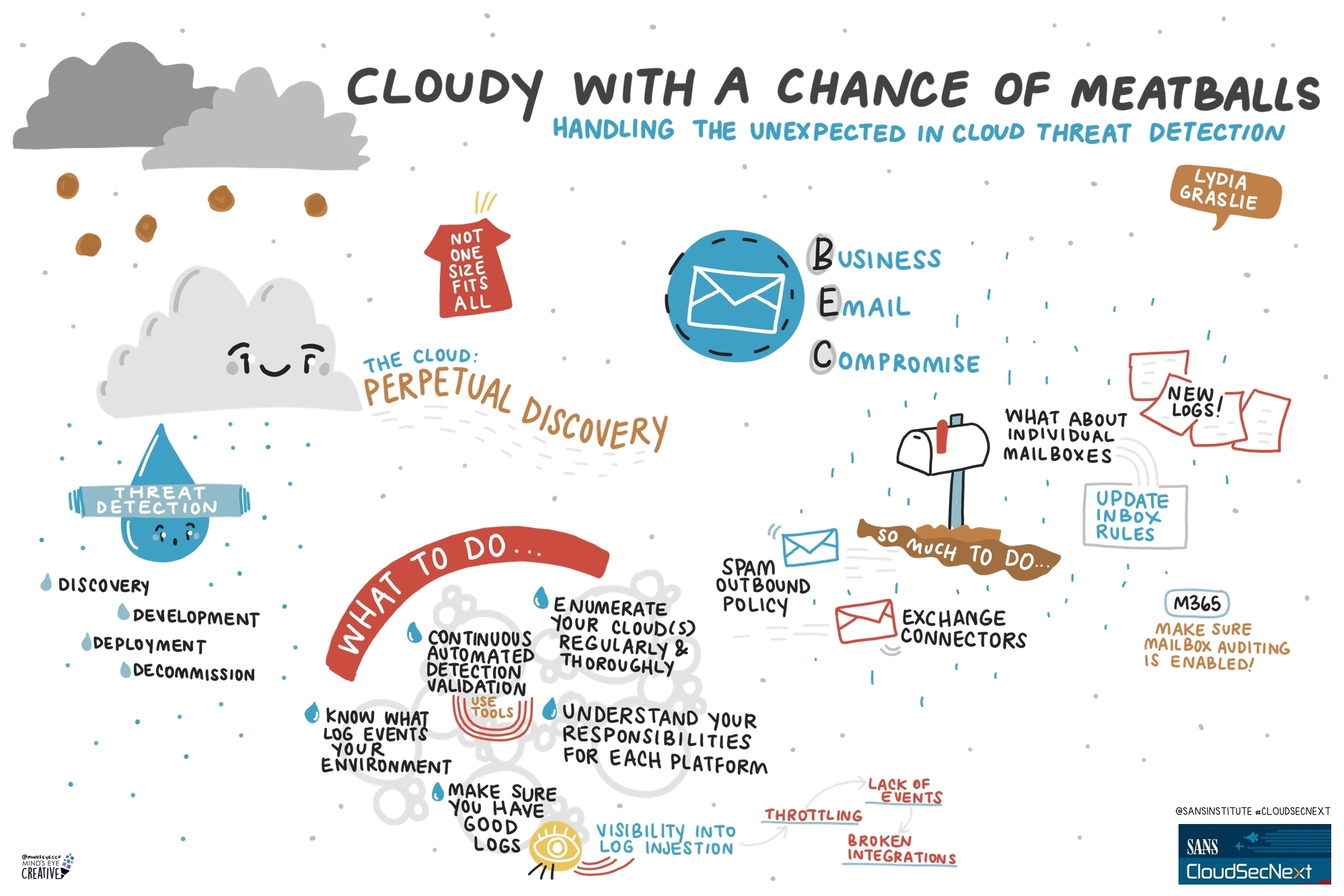
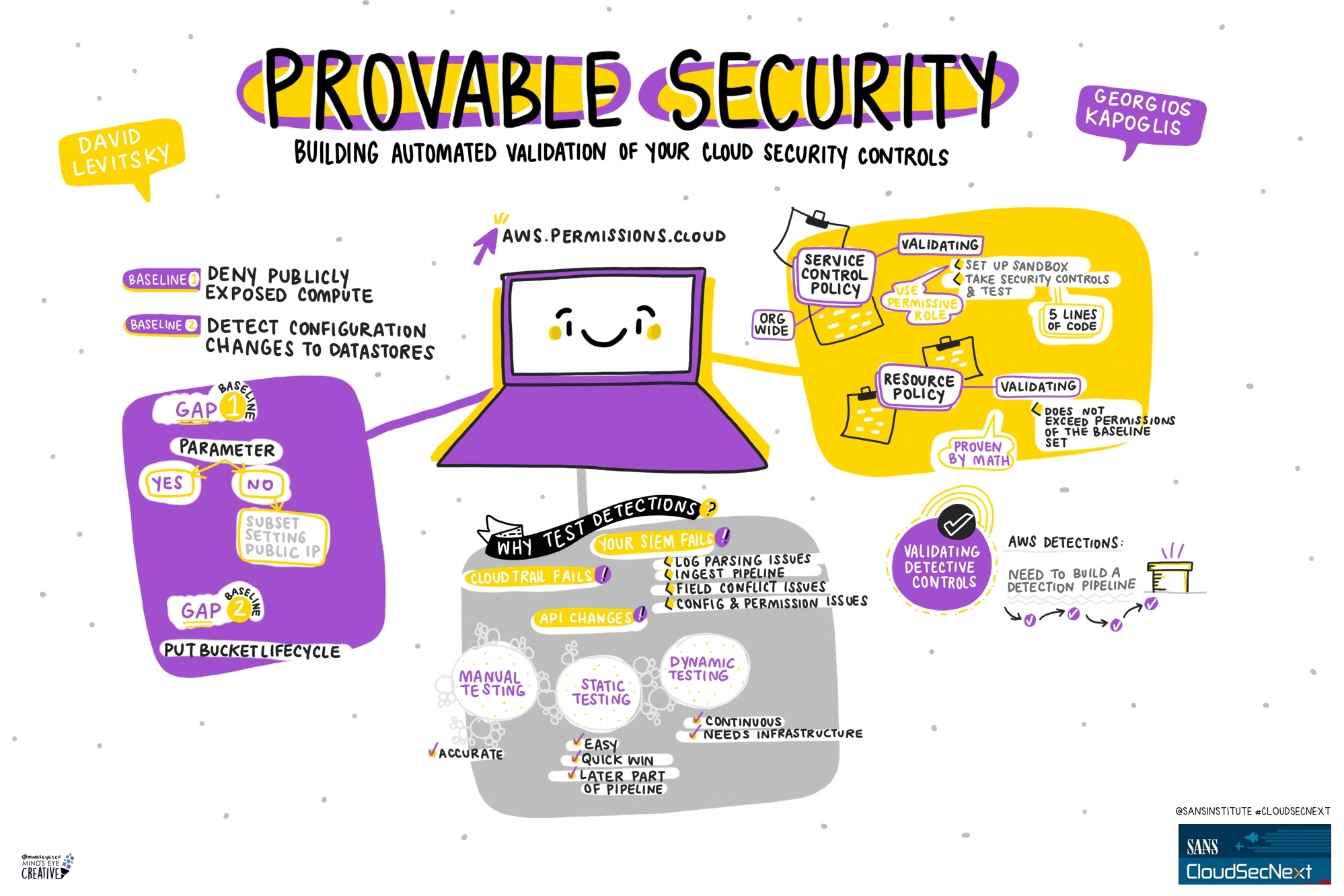
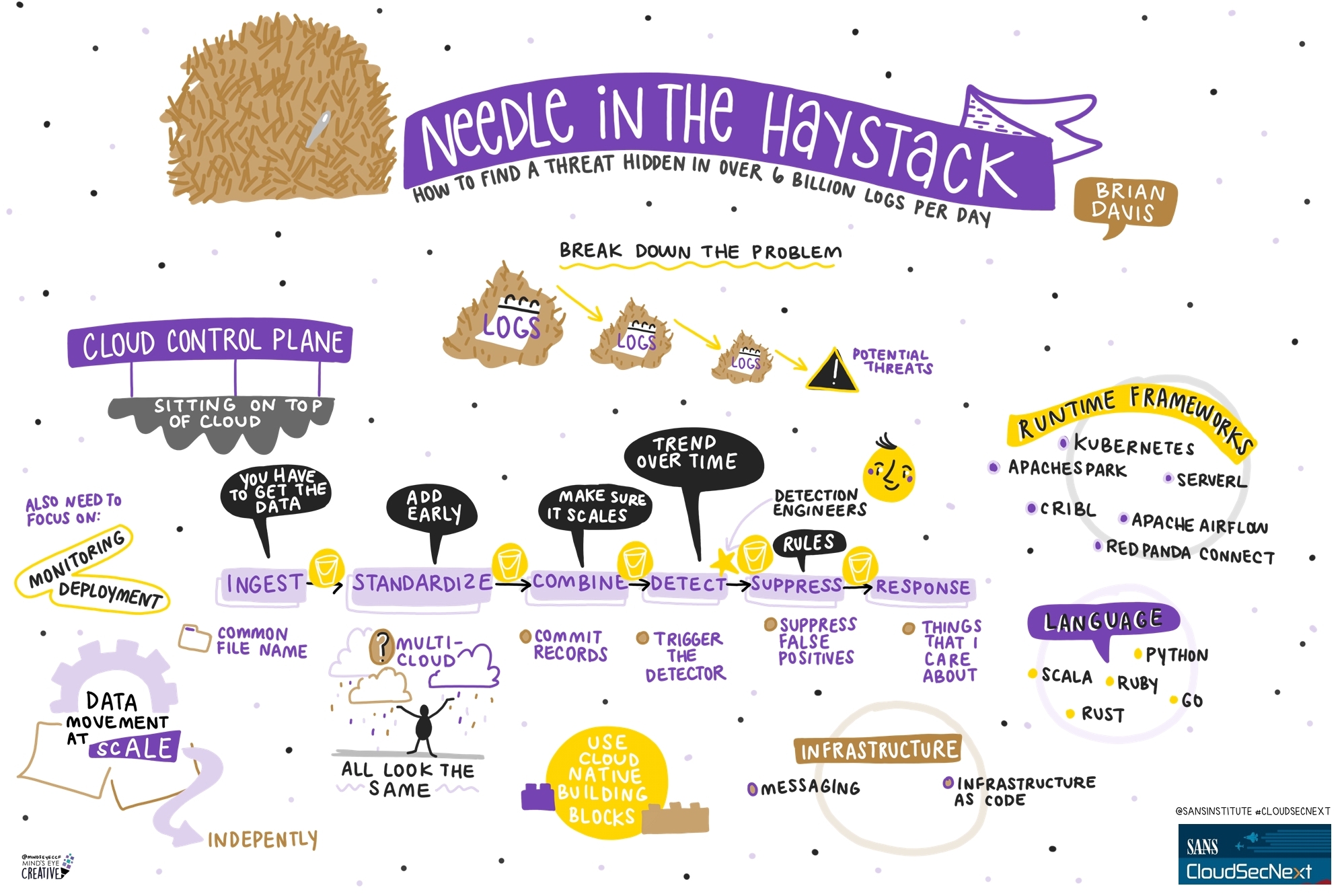
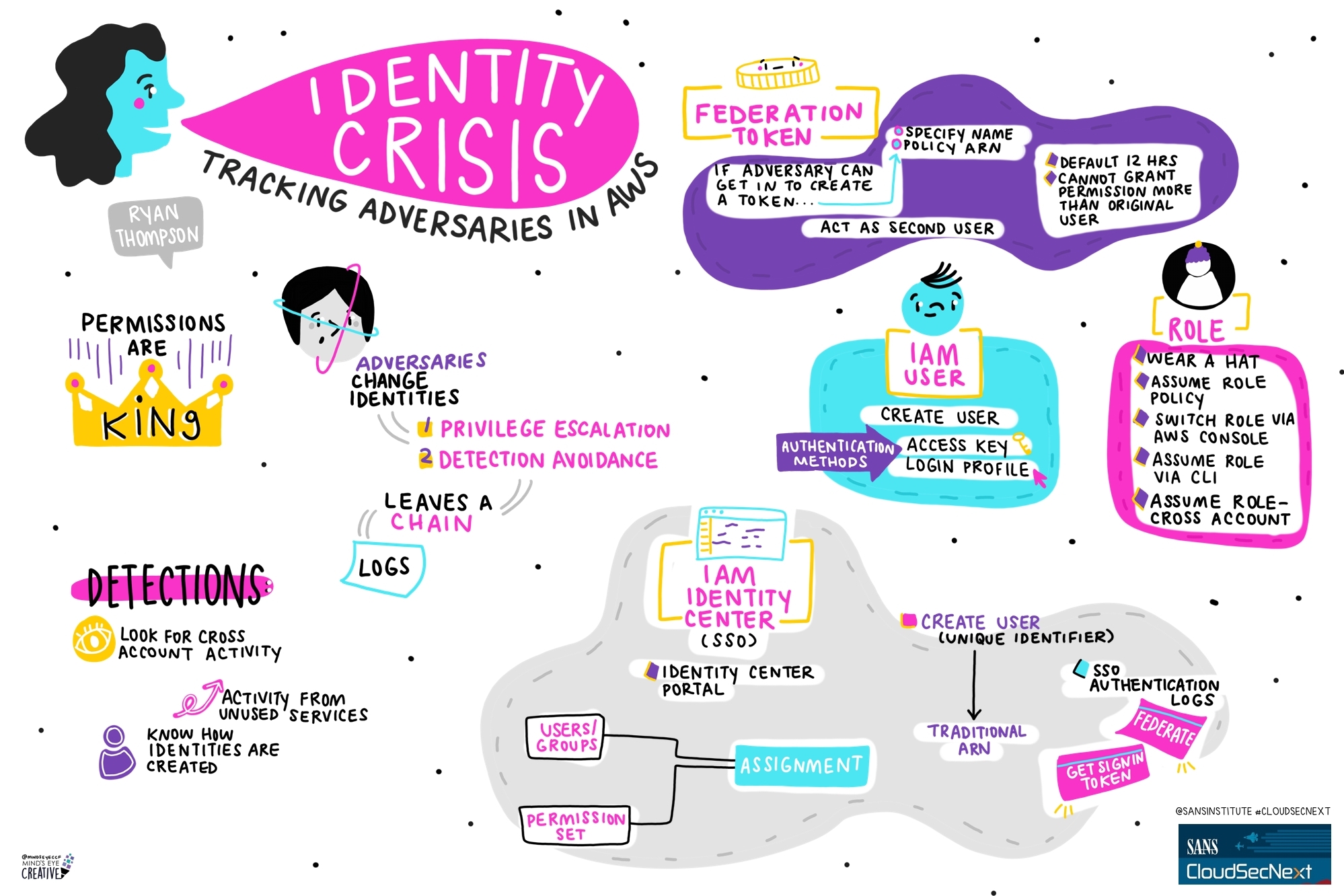
Contact UsCheck out these graphic recordings created in real-time throughout the event for SANS CloudSecNext Summit 2024

On September 30 - October 1, attendees in Denver, CO and thousands from around the globe tuned in for the SANS CloudSecNext Summit. Top practitioners and global experts shared actionable ideas, methods, and techniques to overcome obstacles, and connect with leading professionals.
We invited Ashton Rodenhiser of Mind's Eye Creative to create graphic recordings of our Summit presentations. If you missed a talk or are looking to view the talks through a visual lens, take a look at the recordings below.
*If you registered for the Summit, video recordings will be available on your Summit Access page in your SANS Portal next week!


Launched in 1989 as a cooperative for information security thought leadership, it is SANS’ ongoing mission to empower cybersecurity professionals with the practical skills and knowledge they need to make our world a safer place.
Read more about SANS Institute