SEC595: Applied Data Science and AI/Machine Learning for Cybersecurity Professionals


Experience SANS training through course previews.
Learn MoreLet us help.
Contact usBecome a member for instant access to our free resources.
Sign UpWe're here to help.
Contact UsExplore the mission of the newly renamed SEC510: Cloud Security Controls and Mitigations.

Watch the Webcast | Prevent Cloud Incidents from Becoming Cloud Breaches
The number of cloud security breaches in the headlines have been staggering lately. It seems like a week cannot go by without a massive amount of sensitive data being leaked from either AWS, Azure, or Google Cloud. One example that would be funny if it were not so sad is the September 2023 incident where the Microsoft AI team leaked 38TB of sensitive data, including employee workstation backups and 30,000 internal Teams messages, due to a misconfigured storage configuration. How is the industry failing to use the clouds properly, let alone Microsoft, the extremely mature company who created Azure in the first place?
This is the question we answer in SEC510: Cloud Security Engineering and Controls. Here are some of the course’s findings:
The public cloud is the new norm. Thales Group reported that the percentage of corporate data stored in the cloud has doubled from 2015 (30%) to 2022 (60%). Meanwhile, the 2023 Unit 42 Attack Surface Threat Report, published by a threat research branch of Palo Alto Networks, reported that “80% of security exposures were observed in cloud environments.” Because this percentage is significantly larger than the percentage of data in the cloud, this implies that the cloud is somehow uniquely vulnerable.
.png)
The cloud providers are here to help you with security, but only to a point. Their ultimate goal is to increase profits. Each cloud provider wants to appear as if they care about security, but this is often outweighed by usability. If a cloud provider is hard to use, it is less likely to be adopted.
For example, the first thing an aspiring cloud administrator will try to do is launch a virtual machine, connect to it over SSH, and run some commands like they would on-premises. If the cloud provider prioritized security over everything else, they would block SSH access by default. However, if they did that, it would frustrate the administrator, require them to read documentation, and potentially discourage them from further exploring the cloud. Instead, when you launch a VM in AWS or Azure, the launch wizard will automatically allow SSH from the internet. Funnily enough, they will display a warning saying how dangerous the rule they suggested is. Google Cloud does the same thing, but they fail to even provide a warning.
Insecure defaults are addressed by the “Shared Responsibility Model.” The cloud provider is responsible for the security of the cloud, while the customer is responsible for the security of what is in the cloud. This includes configurations. Regardless of the default, the customer is ultimately responsible for configuring the services they use to meet their organization’s needs.
It is so much harder for security professionals to support multiple cloud providers than it is to support one. Exactly how much harder? Let us try to quantify the effort. If we were using three, completely different providers, it would require three times the effort.
Thankfully, there is some overlap between the different cloud providers. Emphasis on “some”. Shai Morag of the Forbes Technology Council stated that “AWS, Azure and GCP don't handle basic security functions...in exactly the same way. There are nuances that must be taken into account in order for security measures to work properly...The professionals who understand these nuances are not easy to find.”
What about the effort to securely integrate these cloud providers together? Odds are, your organization will need its systems to interact with one another regardless of the clouds in which they reside. Enabling this correctly is simply a nightmare. Learn more about why in my webcast with Eric Johnson, Securely Integrate Multicloud Environments with Workload Identity Federation. We also argue that cloud agnosticism alone will not solve this problem.
.png)
There is a deep link between software security and cloud security. The 2023 Verizon Data Breach Investigations Report (DBIR) showed that “Basic Web Application Attacks” were still among the ”top attack patterns.” Vulnerable applications are more susceptible to these basic attacks. The risk posed by these attacks is enhanced or mitigated by how the cloud provider hosting these apps is configured. Without the proper controls, an attacker can pivot to these cloud-managed services and potentially compromise the entire cloud account.
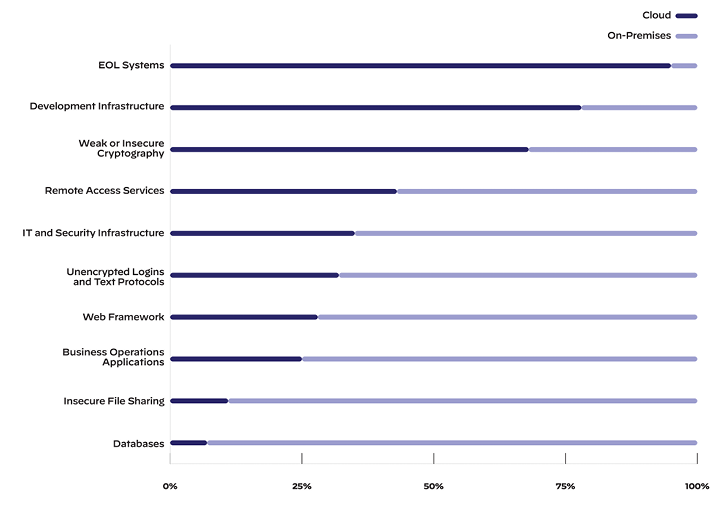
The cloud also enables the fast deployment of publicly accessible vulnerable software. The Unit 42 report cited above argued that “it is comparatively easier for developers to create and deploy…substantially outdated software in the cloud” when compared to on-premises. In fact, they reported that “95% of EoL [end-of-life] software systems exposed on the public internet…were found in cloud environments.” This is surprising because most organizations with on-prem and cloud assets start on-prem, so their oldest assets would presumably live there. Perhaps this is because it is much easier to accidentally expose resources on the cloud than on-premises.
Vulnerable applications, both those developed in-house and by a third-party, are inevitable. Not many cybersecurity professionals can fix vulnerable application code alone. Learning how to code is considered optional for many cybersecurity roles. Thankfully, it is usually much easier to apply secure cloud configuration to mitigate the impact of these vulnerabilities. SEC510 is not an application security course, and it will not teach you how to fix vulnerable application code.
Instead, SEC510 teaches you practical controls and mitigations that you can use to prevent AppSec incidents from becoming breaches. While we leverage material from resources like the CIS Benchmarks, these often focus on compliance. Instead, we put attack-driven controls front and center because they are the most effective to protect your organization’s most important cloud-based assets.
We cover many attack case studies, including the Capital One breach, the Azure SQL lateral movement campaign disclosed in October of 2023, and much more. In all of these case studies, even when the attack involved the complete takeover of a software system, the right cloud-level controls could have dramatically reduced the scope of the incident. Instead of waiting for developers to fix every issue they report, security teams should control what they can by implementing these types of mitigations.
SEC510 is a flagship course in the SANS Cloud Curriculum. Over the past four years, thousands of students have taken it to learn the nuanced security differences between the Big 3 cloud providers and how to securely configure their Platform as a Service (PaaS)/Infrastructure as a Service (IaaS) offerings. The value it has provided is immense, with Sean Ayres of UPS stating, “If you Cloud, you need this course - <period>.”
Multicloud security has become harder, not easier. The SANS 2023 Multicloud Survey demonstrated that the majority of organizations use multiple cloud providers. This trend has resulted in all SANS Cloud Security training courses covering at least 2 of the Big 3 CSPs.
The new SEC510 still supports all Big 3 cloud providers (AWS, Azure, and Google Cloud) equally, with roughly a 33% / 33% / 33% coverage split. It contains all the great content past students have received, while updated to current day, and more. The new name simply highlights the mission SEC510 has had all these years: to mitigate security vulnerabilities in the Big 3 cloud providers with controls and configurations that can block real attacks. SEC510's primary focus is on prevention. If we can prevent security incidents from happening in the first place, or at least mitigate their risk so that they do not become breaches, we can safeguard the confidentiality and integrity of our data, keep our critical systems operational, and lighten the load for our teammates working in other cloud security disciplines.
To learn more, please visit sans.org/sec510. Make sure to click the “Course Demo” button to receive nearly an hour of content from the course for free!


Brandon is a Partner at Cyverity and SANS Senior Instructor at the SANS Institute. He is lead author for SEC510: Cloud Security Engineering and Controls; GPCS holder #1, multi-year RSA Conference presenter, and cloud Bug Bounty collector.
Read more about Brandon Evans