Autoruns from Sysinternals is one of my favorite (free) tools. It has a myriad of uses, from optimizing the boot process to rooting out persistence mechanisms commonly used by malware. It is essentially a targeted registry dump, peering into at least a hundred different Windows Registry keys that the boot and logon processes rely upon. It very quickly shows what executables are set to run during boot or login, as well as enumerating many other interesting locations like Explorer shell extensions, browser helper objects, and toolbars. Over the years it has added some very useful features, including digital signature checks and the ability to ignore signed (and verified) Microsoft executables.
Until recently Autoruns had one big limitation: it had to be run on a live system. This is perfectly fine in a live response scenario when you are primarily working with systems that are up and running. However, in a dead computer forensics environment, its usefulness was hampered by this limitation. The painful workaround was to boot the forensic image using something like Live View or Guidance's Physical Disk Emulator, and run Autoruns on the booted system.
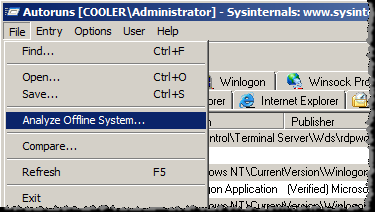
In version 10 of Autoruns, there is now an option to "Analyze Offline System". This is exactly the feature needed to leverage Autoruns with forensic images. It also provides a better ability to detect rootkits since the target system is offline and hence not protected by any malware hiding mechanisms.
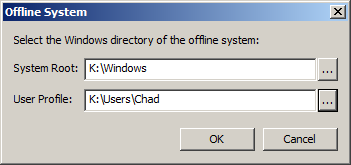
The first step is to mount your drive or image on your local system. This is very easy if you are lucky enough to be working with Microsoft VHD files, or more commonly will be accomplished using a third party tool like IMDisk to mount a forensic image. Once you have a drive letter for your image, you simply point Autoruns to the System Root and User Profile (location of NTUSER.DAT) that you wish to interrogate. All of the existing Autoruns functionality that you know and love will now work on the mounted image.
As excited as I am with this new addition, I unfortunately uncovered several significant issues during testing of the Autoruns v10.01 release:
- Autorunsc.exe, the command line version, appears to have a bug which precludes its offline capability. The switch should be ?—z <systemroot> <userprofile>', but I have had no luck in getting it to work. This is a bit unfortunate, because I prefer the .csv output and scripting capabilities.
- Regardless of the mount point your image is using, the tool reports the Image Path using C:\. Not a huge problem, but it tends to exacerbate some of the other issues documented below.
- I found several instances when Autoruns would fail to run on a particular mounted image. I eventually was able to get all of my test images to be recognized using the offline feature, but it required multiple tries and reloads of the application. Be careful here, because Autoruns will sometimes silently fail and load the results from your local forensic workstation instead.
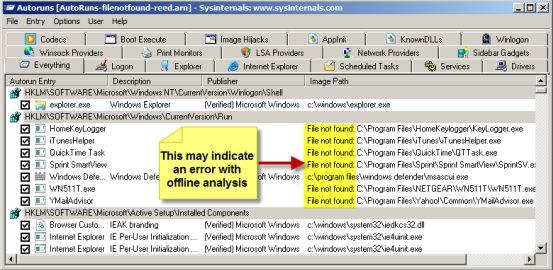
- In addition to outright failures, I also encountered partial loads, sometimes seeing results intermingled between the offline image and the local system values. A good indicator that something may be amiss is if you see large numbers of "File not found" entries in the Image Path column (see screenshot below). In these instances, I was also able to determine that some of the digital signature verification was taking place on the similarly named dlls and executables on the local system as opposed to the offline system image. Needless to say, this is a big problem.
While Autoruns has made a big step forward as a dead forensics tool, I encountered too many problems to recommend it as anything other than a "beta" product. That being said, I have the utmost respect for the Sysinternals Team and I am confident that these bugs will be fixed in an upcoming release. Maybe they will even add column sorting for the GUI interface (hint-hint). I'll make a point to update this post when the bug fixes occur.
Chad Tilbury, GCFA, has spent over ten years conducting computer crime investigations ranging from hacking to espionage to multi-million dollar fraud cases. He teaches FOR408 Windows Forensics and FOR508 Advanced Computer Forensic Analysis and Incident Response for the SANS Institute. Find him on Twitter @chadtilbury or at http://ForensicMethods.com.





