Several times over the past year it has come up in a discussion about the key differences between examining USB Key/Thumbdrives on XP, VISTA, and Windows 7. We did an initial post several weeks ago, but found some new information and have updated our guides as a result. Thanks to SANS Digital Forensic Instructor Colin Cree for the wonderful feedback.
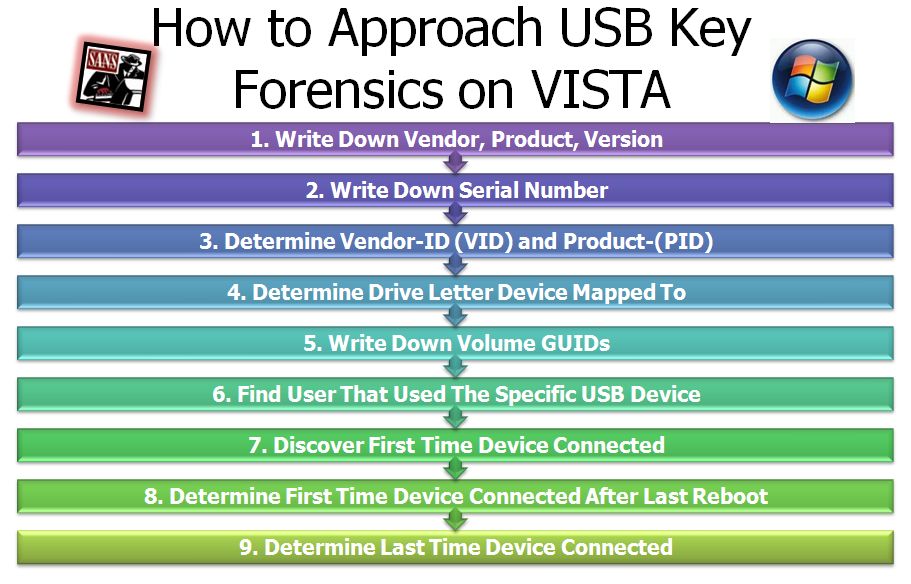
As a part of the SEC408: Computer Forensic Essentials course, we have an extensive section on residue left by USB Devices. I am providing a single guides to help you answer the key USB Key/Thumbdrive questions for your case covering XP, VISTA, and Win7.

How would you examine these keys? We recommend Access Data's Registry Viewer and Regripper. Even though you can get access to the data, there is not a tool that has this process automated yet. The guides will help you step through the keys/values in addition to the files you will need to correctly parse the data.
USB Device Forensics for Windows XP: DOWNLOAD

USB Device Forensics for Windows VISTA/WIN7: DOWNLOAD
Rob Lee is a Director for MANDIANT, a leading provider of information security consulting services and software to Fortune 500 organizations and the U.S. Government. Rob has over 13 years experience in computer forensics, vulnerability discovery, intrusion detection and incident response. Rob is the lead course author and faculty fellow for the computer forensic courses at the SANS Institute.





