Tags:
Early in 2016, I had a conversation with a colleague about the very, very limited free and open-source .NET security static analysis options. We discussed CAT.NET, which released back in 2009 and hasn't been updated since. Next came FxCop, which has a few security rules looking for SQL Injection and Cross-Site Scripting included in the Visual Studio Code Analysis Microsoft Security Rules. Plus, the various configuration analyzer tools that run checks against web.config files, such as the Web Configuration Security Analyzer (WCSA) tools written by Troy Hunt and James Jardine.
Combining these scans all together leaves .NET development teams with a few glaring problems:
- From past experience, I know that CAT.NET and FxCop have very poor coverage of secure coding issues covered by OWASP, SANS / CWE Top 25, etc. See the presentation slides below for stats from CAT.NET and FxCop scans against a vulnerable .NET target app. The results are very concerning.
- Aside from the Visual Studio Code Analysis rules, none of the tools actually run inside Visual Studio where engineers are actually writing code. This means more add-on tools that need to be run by the security / development leads, resulting in more reports to manage and import into bug tracking systems. For this reason, it is very unlikely these scans are actually run before committing code, which in my opinion is too late in the development process.
There has to be a better way, right?
Roslyn - The .NET Complier Platform
At the end of the conversation, my colleague asked me if I had tried writing any Roslyn rules yet? Wait, what's Roslyn? After some quick searching, I discovered that Roslyn, aka the .NET Compiler Platform, is a set of code analysis APIs for the C# and Visual Basic compilers. Using Roslyn, Microsoft provides a way to query and report diagnostics on just about any piece of code. These diagnostic warnings are displayed in two different places:
- Inside a code document, diagnostic warnings show as spell check style squiggles as code is being written! See the following screenshot for an example:
.png)
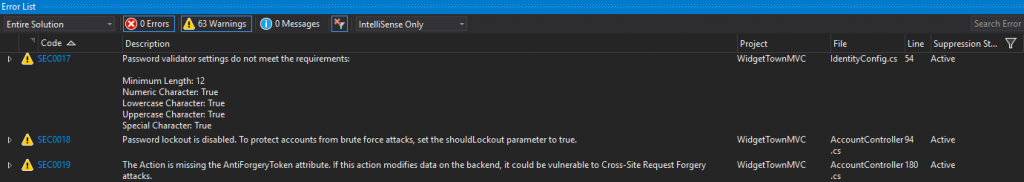
- In the Error List, diagnostic warnings are added to the standard list of compiler errors. Roslyn provides rule authors the ability to create custom warnings (or errors if you want to be THAT disruptive security team that slows down dev teams) in the list. See the following screenshot for an example:
After reading Alex Turner's MSDN Magazine article, I realized that the Roslyn team at Microsoft had provided me exactly what I needed to build a powerful, accurate secure coding engine that runs inside of Visual Studio. During development. As code is written. Before code enters the repository. Bingo!
With that, I decided to help address the gap in the lack of free .NET static analysis tools.
The Puma Scanner
Once we figured out the Roslyn basics, my team and I spent a small part of our consulting hours over the past 4 months learning about the various types of analyzers and building security rules. Of course we had some help, as the folks on the Roslyn team at Microsoft and the Roslyn Gitter channel are very helpful with newbie questions.
Last week, I had the pleasure of presenting our progress at the OWASP AppSec USA conference in Washington, DC. While there is a lot of work left to be done, we are happy to say that Puma Scan has roughly 40 different rules looking for insecure configuration, cross-site scripting, SQL injection, unvalidated redirects, password management, and cross-site request forgery. At this point, I am confident it is worthwhile running the scanner in your development environment and MSBuild pipeline to gain more advanced static analysis compared the free options that exist today.
If you were unable to attend AppSec USA 2016, don't worry. The hard working volunteers at OWASP record all of the sessions, which are posted on the OWASP YouTube channel. You can watch the presentation here: Continuous Integration: Live Static Analysis using Visual Studio & the Roslyn API session.
For now, as I promised those that attended the presentation, the presentation slides are available on Slideshare. Additionally, links to the Puma Scan web site, installation instructions, rules documentation, and github repository are available below. Let me know if you're interested in contributing to the project!
To learn more about securing your .NET applications, sign up for DEV544: Secure Coding in .NET!
References
- Puma Scan Web Site: https://www.pumascan.com/
- AppSec USA Presentation: Continuous Integration: Live Static Analysis using Visual Studio & the Roslyn API
- Github Repository: https://github.com/pumasecurity
- Visual Studio Extension: https://visualstudiogallery.msdn.microsoft.com/80206c43-348b-4a21-9f84-a4d4f0d85007
- NuGet Package: https://www.nuget.org/packages/Puma.Security.Rules/
Eric Johnson is a Senior Security Consultant at Cypress Data Defense, Application Security Curriculum Product Manager at SANS, and a certified SANS instructor. He is an author for DEV544 Secure Coding in .NET and DEV531 Defending Mobile App Security Essentials, as well as an instructor for DEV541 Secure Coding in Java/JEE and DEV534: Secure DevOps. Eric's experience includes web and mobile application penetration testing, secure code review, risk assessment, static source code analysis, security research, and developing security tools. He completed a bachelor of science in computer engineering and a master of science in information assurance at Iowa State University, and currently holds the CISSP, GWAPT, GSSP-.NET, and GSSP-Java certifications.





