Device acquisition may not be the sexiest phase of digital forensics, but it has the most number of pitfalls and can result in catastrophic loss. If a practitioner makes a mistake during acquisition, the investigation may simply be over, with nothing left to examine. Establishing an acquisition process is important, and a critical part of your process should be checking for the presence of full disk and volume-based encryption. Disk encryption is more prevalent than many believe — I am anecdotally seeing it in use on nearly thirty percent of the computers I encounter. If a system is running, the examiner often has a one-time shot to capture any mounted volumes in their decrypted state.
The inherent challenge is how to determine if an encrypted disk or volume exists. From the perspective of the operating system, data on a mounted volume is available in unencrypted form. A separate abstraction layer takes care of encrypting write operations and decrypting data for read operations. Thus when encountering a live system, investigators are often left with ad-hoc tests to try and make a determination. They can look for telltale installed software, or particular icons present on the system, but there are few reliable ways to get a confident answer whether encryption does or does not exist.
See any evidence of encryption products?
Encrypted Disk Detector
Jad Saliba of Magnet Forensics encountered this dilemma and wrote a tool that takes the guesswork out of the decision to perform a live acquisition or shut the system down and pull the drive. His free tool, Encrypted Disk Detector (EDD) has been available for a couple of years, and has been a staple of our forensic acquisition curriculum in the SANS FOR408 Windows Forensics In-Depth course. It does an excellent job of recognizing disks and volumes encrypted by Symantec PGP, TrueCrypt, Microsoft Bitlocker, and most recently, McAfee SafeBoot. Here are two examples of the tool in action:
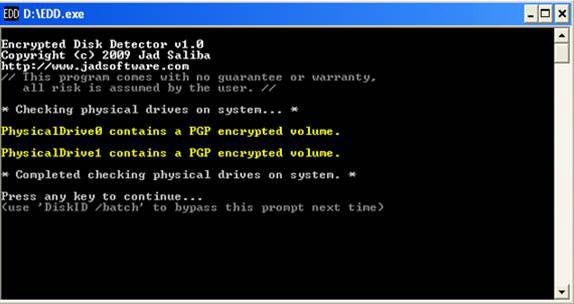
Figure 1 shows EDD identifying two physical disks on the live system, with both being encrypted by PGP full disk encryption (FDE).
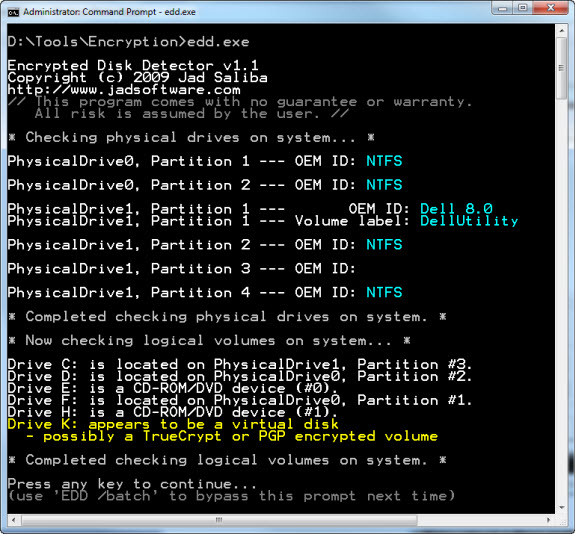
Figure 2 is a little more interesting. It shows a nice side-benefit of the tool: EDD lists all of the current physical and logical drives it finds on the live system. Solid state drives are getting smaller and hence it is very common to now find two (or more) drives even in laptops. Knowing up front how many drives and mounted partitions you may be dealing with can save a lot of time. In addition to seeing two physical drives and six mounted partitions on this system, note the alert for "Drive K:". Students often ask if EDD can detect the special "hidden" volumes that TrueCrypt is famous for. "Drive K:" happens to be such a volume. Keep in mind that the volume can only hide until the user mounts it to use the files within. EDD finds the TrueCrypt volume because it was mounted when the system was examined. This illustrates why checking for encryption is so important when responding to live systems. Once this system is shutdown, that hidden volume is likely gone for good.
How it Works
EDD requires Administrator permissions, and is simple enough for any first responder to use. Simply run edd.exe from an elevated command prompt and it will search the Master Boot Record and Volume Boot Records for signatures indicative of encryption products. Which leads me to its biggest weakness — EDD relies on signature based detection and hence can only recognize a finite number of encryption products. While it can easily detect PGP full disk encryption and Bitlocker volumes, it would provide no information if the system is protected with Utimaco SafeGuard. Thus the more products EDD can identify, the higher our level of confidence can be that encryption does or does not exist on a system.
How You Can Help
One of the great parts of being a SANS instructor is I get to spend time doing research, often leading to interactions with tool authors and others in the forensics community. In this case, I spoke to Jad about his plans for EDD. Like most free tool developers, he wants EDD to be relevant, but does not receive a lot of feedback. For instance, what are the most important encryption products that EDD should support? To answer that question, we put together a brief survey and decided to crowd source the future development of EDD with your vote. Jad has pledged resources to implement signature detection within EDD for the three most popular products as picked by YOU. Further, the breakdown of product usage/demand will be used to guide the future roadmap for EDD and will be shared with the community.
If you have made it this far, please take thirty seconds to fill out the survey. [Survey Closed]
Stay tuned: in a future post we will cover the survey results and the release of an updated version of Encrypted Disk Detector.
Chad Tilbury, GCFA, has spent over twelve years conducting computer crime investigations ranging from hacking to espionage to multi-million dollar fraud cases. He teaches FOR408 Windows Forensics and FOR508 Advanced Computer Forensic Analysis and Incident Response for the SANS Institute. Find him on Twitter @chadtilbury or at http://forensicmethods.com.





