ICS Connectivity: Business Benefits and Cyber Risk
Engineering systems: PLCs (programmable logic controllers), RTUs (remote terminal units), protection control relays, embedded HMIs (human machine interfaces), SIS (safety instrumented systems), DCS (distributed control systems), solenoids, meters, field bus communications, sensors, and actuators. These engineering devices and systems have been operating the critical infrastructure we rely on, for decades in their own engineering environments. Modern connectivity into ICS has led to increased data accessibility across traditional IT (information technology), OT (operational technology) environments and several benefits as we see here:
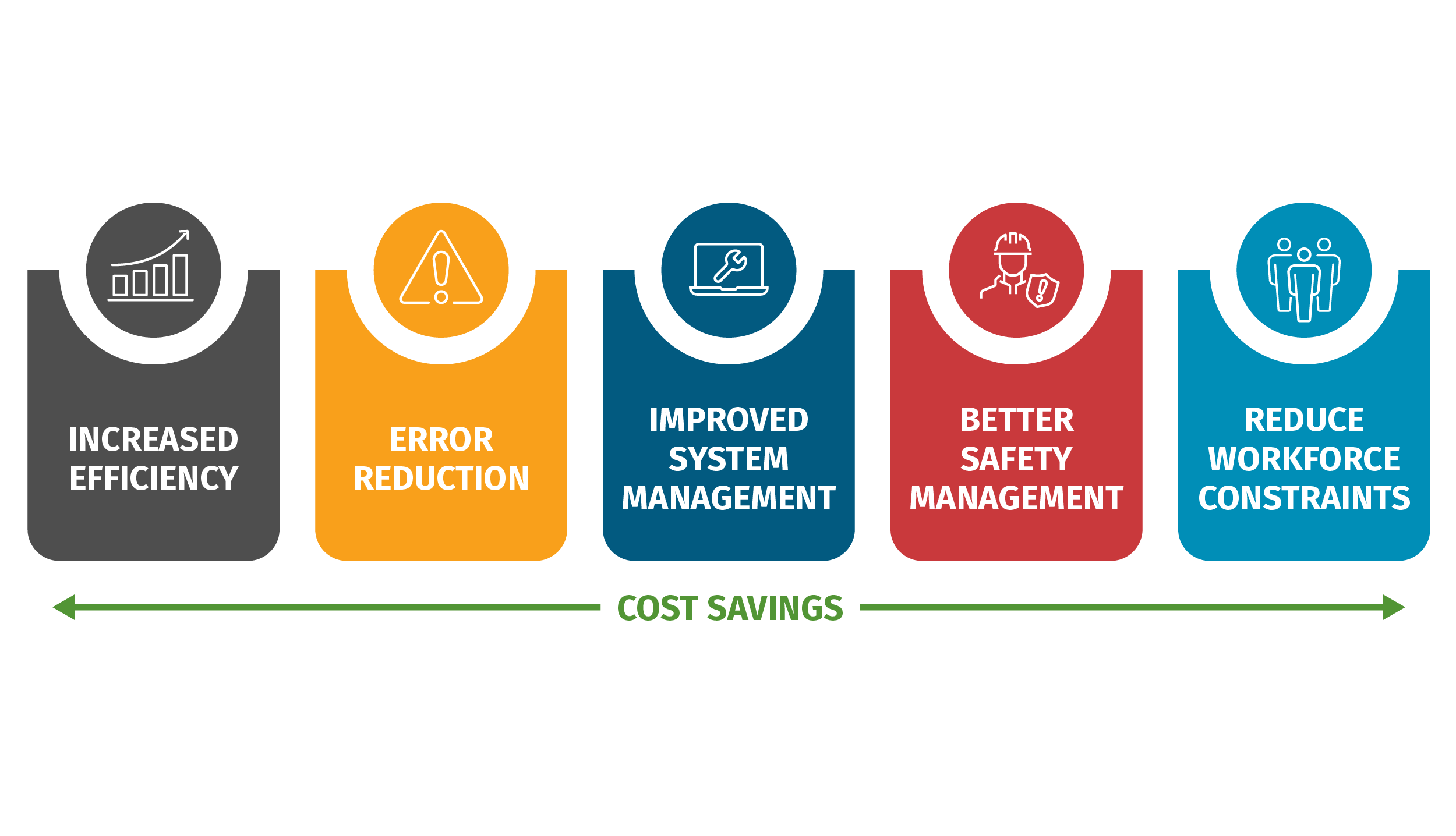
However, enabling connectivity to engineering environments that were originally designed to operate in isolation with an inherent trust inside their own networks results in these environments now being exposed. The increased targeting of control systems through impactful cyber-attacks in recent months has resulted in an attack surface more widely available and vulnerable to cyber-attacks. These attacks are created and deployed by adversaries-for-hire and rogue nation-states which have the means and motivation to disrupt operations and cause safety impacts. The good news - ICS/OT cyber security defense is totally doable - with an effective team and approach to risk management!
IT Security Is Not ICS/OT Security
Traditional IT security focuses on moving and securing data at rest or data in transit, and the traditional security pillars of C.I.A. (Confidentiality, Integrity, and Availability). Operating technology/industrial control systems (OT/ICS) manage, monitor, and control real-time engineering systems for physical input values and control output for physical actions in the real world. The main priority in OT/ICS is safety and reliability of operations. As ICS/OT security managers we should never just “copy” & “paste” IT security controls into ICS/OT environments. As the US Department of Homeland Security says, “…incident response deployed in IT business systems may result in ineffective and even disastrous results when applied to ICS cyber incidents.”
ICS Incident Response Objectives
The objectives for industrial control system incident response are to adapt traditional incident response steps to suit engineering environments, which prioritize safety at every single step. This involves a specific ICS incident response plan with several teams beyond that in a traditional incident response. These may include engineering operators, external control system support vendors, government agencies, physical safety teams, physical security teams, etc., with instruction from owner/operators of facilities and the engineering processes.
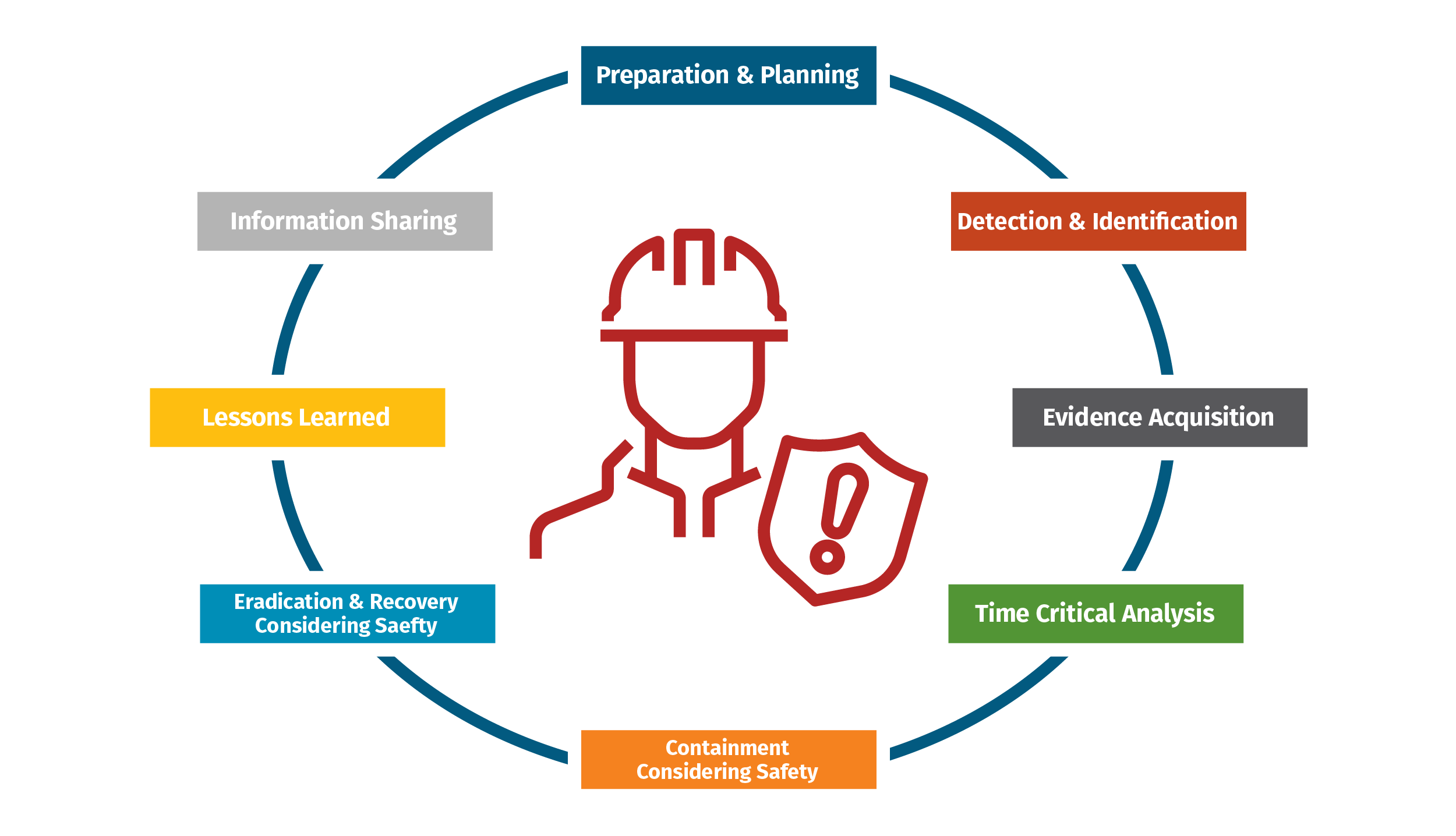
Main objectives for each phase of an ICS-specific incident response engagement:
Preparation - Have well-defined, well-communicated roles and responsibilities, trained ICS-specific security defenders who understand engineering and can investigate cyber events related to control systems. A cyber defensible position should be part of a well-tested and regularly updated ICS-specific incident response plan.
Threat Detection & Identification – Here, the objective is ICS-specific network visibility and threat identification based on consuming and applying sector-specific threat intelligence.
ICS Incident Response Evidence Acquisition – At this stage, the goal is to attain the ability to fight through the attack while maintaining safety and acquiring key evidence for meaningful and timely forensics analysis.
ICS Time Critical Analysis – In this area, we want to continue to fight through attacks, maintaining safety while conducting time critical analysis. (Traditional IT Containment & Eradication may cause more damage to ICS than the threats themselves.)
ICS Incident Response Containment – The focus is on the preservation of operations through logical or physical changes in the control environment to further reduce safety and control system impacts. ICS Security, Engineers, and Operator teams fight through the attack, and Evidence & Intel could be shared for reporting, compliance, legal, etc.
Eradication & Recovery – Eliminate the threat(s) from the environment(s) when it is safe to according to engineering. Restore engineering systems to normal operational state, full production of engineering operations.
Lessons Learned - Apply knowledge to improve response and restoration efforts for future incidents in the engineering environment.
ICS Incident Response Information Sharing - Share relevant tactical, strategic, and operational threat intelligence, and cyber security lessons learned which might be of use for defense in the larger ICS and critical infrastructure community.
ICS security managers would do well to host a practical, sector-specific, threat-intelligence-driven, ICS incident response tabletop exercise with applicable ICS security, engineering, safety teams, and ICS owners/operators, who will be critical to be attendance during the exercise and for the follow-up actions. For reference, the top ICS tabletops have been outlined in this blog here: Top 5 ICS Incident Response Tabletops and How To Run Them.
Risk Management Tracking - HILF in Critical Infrastructure
Tabletop metrics should be captured where HILF (high impact low frequency) events are brought forth and tracked through the organizations’ risk department for senior leadership discussions on business risk. They should be considered to pose risk like that of other engineering related risks where cyber to physical impacts in control environments are possible.
One of the principal types of HILF events is a well-planned cyber, physical, or blended attack conducted by an active adversary against multiple points on the system. Attacks such as damaging or destroying key system components of critical infrastructure like the power system could result in prolonged outages to large parts of the system.
Take, for example, the rapid convergence of the electric power systems infrastructure with traditional information and communications technologies. When combined with a new awareness of the sophistication of adversary capabilities in attacking control systems, improving the protection, resilience, and response capabilities of the bulk power system requires a fresh understanding of the risk and well-coordinated steps. Mapped here are some of the historic and recent ICS events.
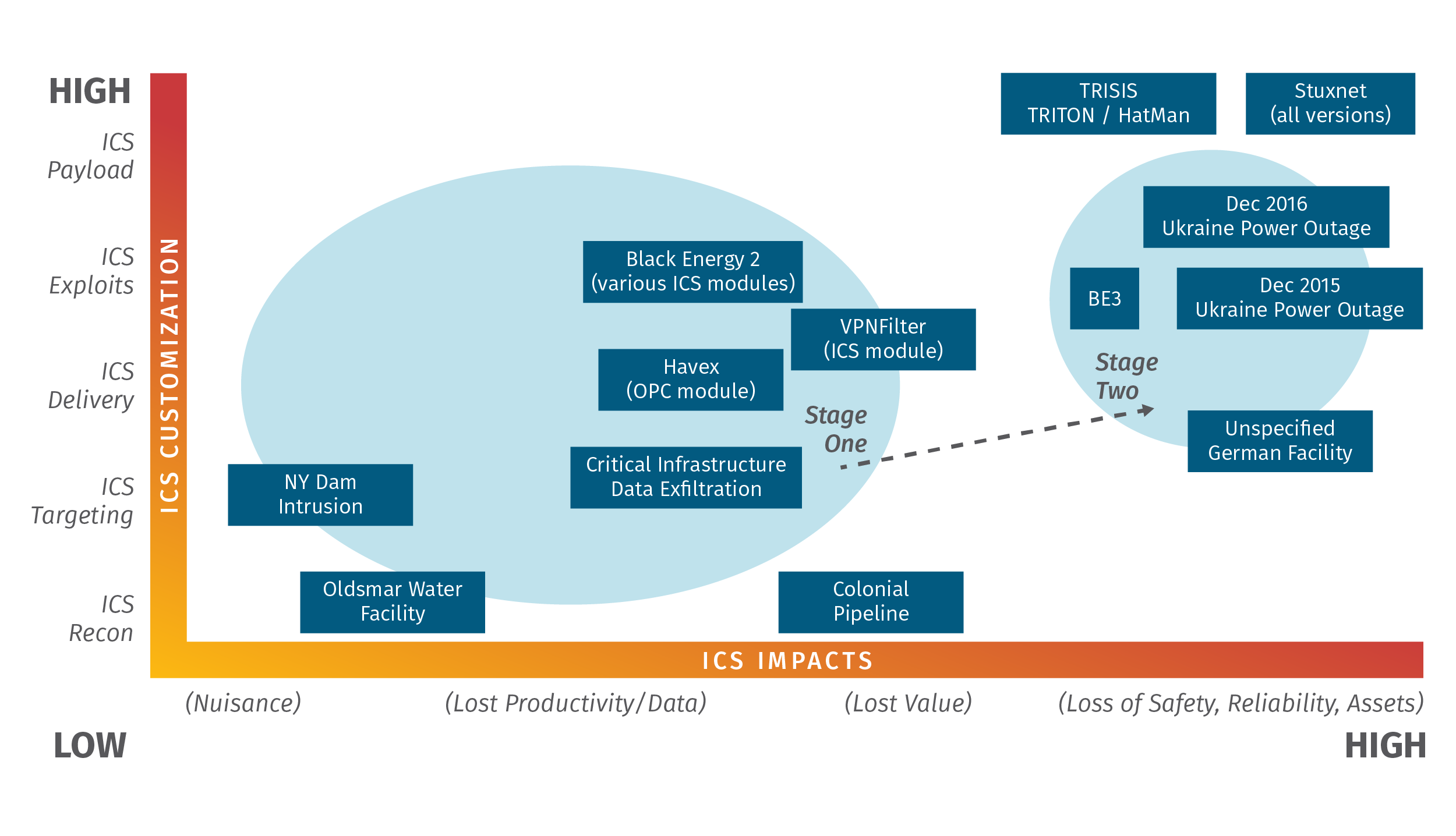
ICS Security Management Choices VS. ICS Attack Group Targeting
There is a common misconception in control system security whereby a utility may think they are too small to be a target of an ICS cyber-attack or impactful cyber event. The reality is, adversaries likely develop and test capabilities in smaller facilities in preparation for the final attack in their ultimate target environment. As managers and tactical cyber defenders in ICS/OT, we get to choose many things about our control system security program—one of which is not whether we are a target. Only the adversary has complete control over that.
The ICS418: ICS Security Essentials for Managers course empowers leaders responsible for securing critical infrastructure and operational technology environments. The course addresses the need for dedicated ICS security programs, the teams that run them, and the skills required to map industrial cyber risk to business objectives to prioritize safety. The course effectively addresses today’s challenges and shows how to reduce cyber risk in ICS, covering the needs of the full range of managers, including:
- Managers asked to "Step-Over"
- Traditional IT security managers who must create, lead, or refine an ICS security program
- Traditional IT security managers who must create, lead, or refine an ICS security program
- Practitioner to Manager "Step-Up"
- Industrial engineers, operators, or ICS security practitioners promoted to a manager position to create, lead, or refine an ICS security program
- "In-Place" Managers
- Existing ICS security managers who need to further develop their leadership skills specific to industrial security
- Existing ICS security managers who need to further develop their leadership skills specific to industrial security
In-Class Industrial Management Simulation
Those familiar with the Cyber42 cybersecurity leadership simulation game may have learned about it when taking SANS Management courses. SANS has extended this awesome tool for ICS418 by introducing Cyber42: Industrial Edition, which borrows many features from the traditional Cyber42 game. The scenarios are specific to industrial control systems, and of course, safety is added to the mix of industrial cyber incidents. In Industrial Cyber42, the object of the game is to finish with the highest safety culture.
Take ICS418 with Dean and get to know him!
For an in-depth exploration of ICS security management strategies and how to defend against targeted attacks, download the SANS Strategy Guide: ICS Is the Business.




