SEC595: Applied Data Science and AI/Machine Learning for Cybersecurity Professionals


Experience SANS training through course previews.
Learn MoreLet us help.
Contact usBecome a member for instant access to our free resources.
Sign UpWe're here to help.
Contact UsWelcome to the first part of a multi-part series on threat hunting for industrial control system (ICS) environments.



The title of this ICS blog series, “They're Shootin’ at the Lights!”, is a reference to the 1988 film, Die Hard. Don’t worry, no major spoilers. In one scene in the film, several police officers and federal agents are at the site at night of a building taken over by criminals. Large police spotlights are pointed at the building to detect the movements inside. The criminals get spooked and start shooting. Deputy Police Chief Dwayne T. Robinson, who we might describe as a “non-threat hunter,” says It’s panic fire, suggesting that the adversaries are unsophisticated. But a lone police officer, Sgt. Al Powell (an actual threat hunter!) notes that “they’re shootin’ at the lights!” – a technique to evade detection and prolong the intrusion and impact. Clearly, Sgt. Powell has seen these types of tactics before and has high confidence the criminals are skilled.
Sgt. Al Powell is a great example of a threat hunter. He assumes passive defenses will fail, knows the likely tactics of the adversaries based on prior knowledge observing or tracking such attacks by using threat intelligence, and is able to suggest active defense steps. Hypothesizing an adversary’s next move provides the opportunity to proactively detect threats and adapt your defensive tactics instead of passively waiting for security tools to alert.
Translated into today’s world of cyber threats, threat hunting is a proactive process performed at a regular cadence by human defenders. Threat hunters use Cyber Threat Intelligence (CTI) to create CTI-driven attack hypotheses, then sift through available security event data to stop an attack in progress or identify ways to strengthen a security program before incidents actually occur.
Threat hunting is applicable to Information Technology (IT) and ICS environments, but it employs a different approach for ICS than for traditional IT. Threat hunting in ICS environments must take into account safety, different targeted assets, different logging capabilities (or lack thereof), legacy devices, embedded operating systems, and engineering devices speaking non-traditional industrial protocols. In addition, IT and ICS systems have different missions, objectives, and impacts during an incident. Finally, in ICS environments the adversaries must use different attack tactics and techniques for access, execution, collection, and persistence in order to degrade safety, manipulate control, damage physical engineering assets or property, etc.
Threat hunting does not replace traditional ICS security defenses such as the Purdue network architecture, whitelisting anti-malware solutions on critical ICS endpoints, Network Security Monitoring, or hashing and comparing engineering logic files on a regular basis to find signs of tampering in Programmable Logic Controllers (PLCs) or Remote Terminal Units (RTUs). Threat hunting is built on top of these security layers, leveraging their data sources.
While there are many benefits from threat hunting at any maturity level of an ICS security program, it is most effective when the Active Defense maturity phase has been reached and architecture and passive defenses are in place. In addition, ICS threat hunting is most effective when:
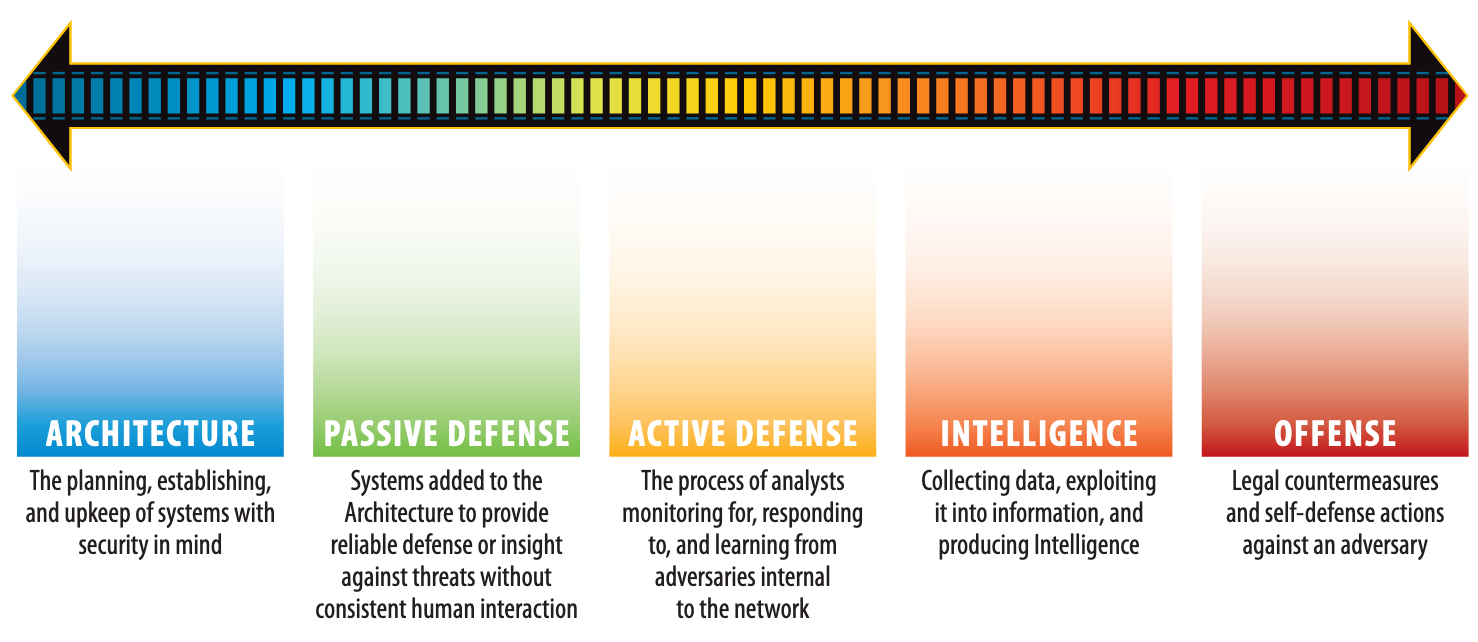
Source: https://www.sans.org/white-papers/36240/
People are the priority of this security pillar here:
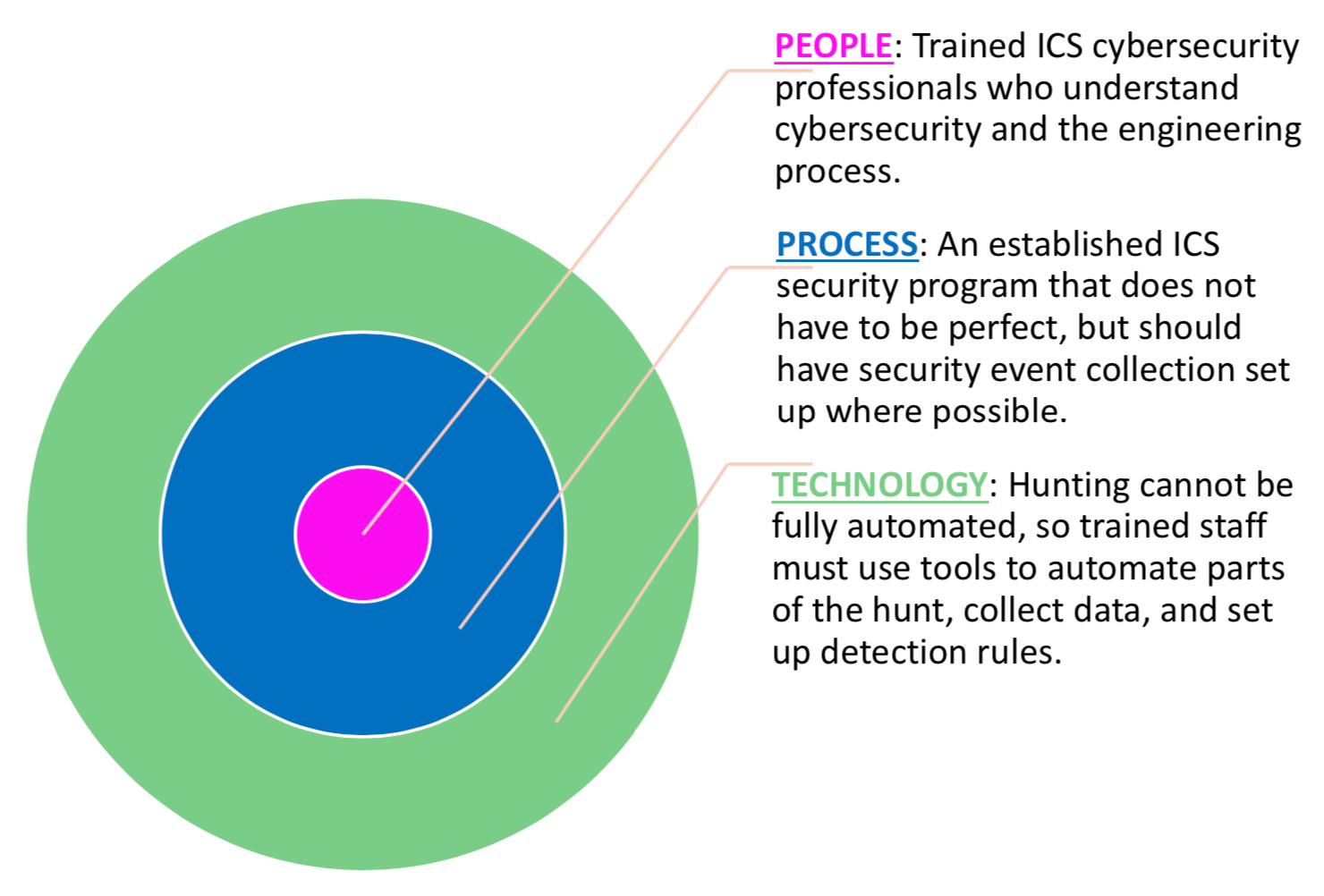
ICS threat hunters should have knowledge of the engineering process, the industrial protocols in use, what normal traffic patterns look like, which assets are critical for safety and operations, how to use technology to centrally log and correlate security events, and cyber defense skills, while at the same time regularly consuming threat intelligence for their sector.
Ideally, security event collection should be happening across both IT and ICS environments to allow a full view of an attack across Stages 1 and 2 of the ICS Cyber Attack Kill Chain (see https://www.sans.org/white-papers/36297/).
While it makes sense to use automation in the form of scripting for data collection and correlating to streamline elements of the hunting process, threat hunting cannot be fully automated.
The focus should not be on metrics such as “how many pieces of ICS malware did we find this week?” or “how many adversaries did we stop this month?”. Rather, the output from ICS threat hunting needs to be understanding at what scale the ICS changed to reduce the habitable nature of the environment for adversaries, mapped to the MITRE ATT&CK Threat Groups. Or, is the ICS aligned with defenses to protect against the latest cyber intrusions seen in the sector? Were changes made that strengthens safety and reliability or increase threat detection coverage in the environment? How many additional resources have been trained to better understand the control system and how to defend it the control system? In many cases, even if a hunt does not find an adversary mid-attack, it does identify specific areas to improve tied to likely attack techniques that adversaries in your sector have been observed using. This is a win! With these types of outputs in mind, every hunt can:

It's advantageous to start ICS threat hunting with CTI feeds or even recent attack reports from your sector. CTI can come in many forms, including hardware or software vulnerability advisories, technical indicator feeds via STIX/TAXII, strategic cyber threat reports, malware analysis reports, and open-source technical maps of tactics and techniques observed in the wild (e.g., MITRE ATT&CK for ICS). CTI should include sector-specific details and beyond just Indicators of Compromise, to include Tactics, Techniques and Procedures – that is, tradecraft of how the adversary executes an attack, which assets are commonly targeted, and which tools the adversary used to attain adversary persistence, lateral movement, data exfiltration, remote access, etc.
There are paid and non-paid CTI sources. Some are specific to ICS. Free or low-cost CTI can be obtained through some Information Sharing and Analysis Centers (ISACs) and other government sharing programs. While ISACs provide a great CTI foundation for a threat hunting program, commercial ICS CTI services excel in providing timely reporting and specific control system detail. Many ICS-specific vendors conduct their own in-depth industrial incident response across multiple ICS sectors. The observations from their work in the field feed their CTI report generation for paying clients. To start, review these low/no-cost sources to find out how you can best consume, generate, and share ICS-specific CTI in order to kick-start your ICS threat hunting program.
In the upcoming entries in this ICS blog series, we will walk through building and performing hunts, and highlight takeaways for proactive changes in control system environments.


Dean Parsons, CEO of ICS Defense Force, teaches ICS515 and co-authors ICS418, emphasizing ICS-specific detection, incident response, and security programs that support OT operations—aligning practitioners and leaders on clear, defensible action.
Read more about Dean Parsons