Tags:
NOTE: This post is part of a series on building mature security awareness programs with a focus on Managing Human Risk. For this post we define the first and often most overlooked step: Identifying what exactly are your top human risks?
So how do you manage human risk? The first step is identifying exactly what risks you care about, as you can see in the visual below. Surprisingly, a large number of security awareness programs skip this step, jumping right into how to engage, train, and motivate their employees. While this is important, it is an indication that you have an immature program with primarily a compliance focus. If you are not focusing on the right human risks, you are not only wasting your workforce’s time but also your organization’s resources. To effectively manage human risk, you have to first know what risks your organization prioritizes.
So where do you start? One of the most common steps is to start with a human risk assessment. The concept of risk assessments are not new, there are numerous options and frameworks such as NIST SP800-30 and FAIR. For an awareness program, you leverage a similar approach but focus on identifying your top human risks. To be effective in any risk assessment, use data to drive your decisions as much as possible — far too often risk decisions are based too much on emotion. Some of the most effective sources for data on your top human risks can include:
- Past incidents / breaches
- Past assessments / audits
- Industry risk reports (my favorite is the VZ DBIR)
- Human risk / behavior assessments
- Cyber Threat Intelligence (CTI)
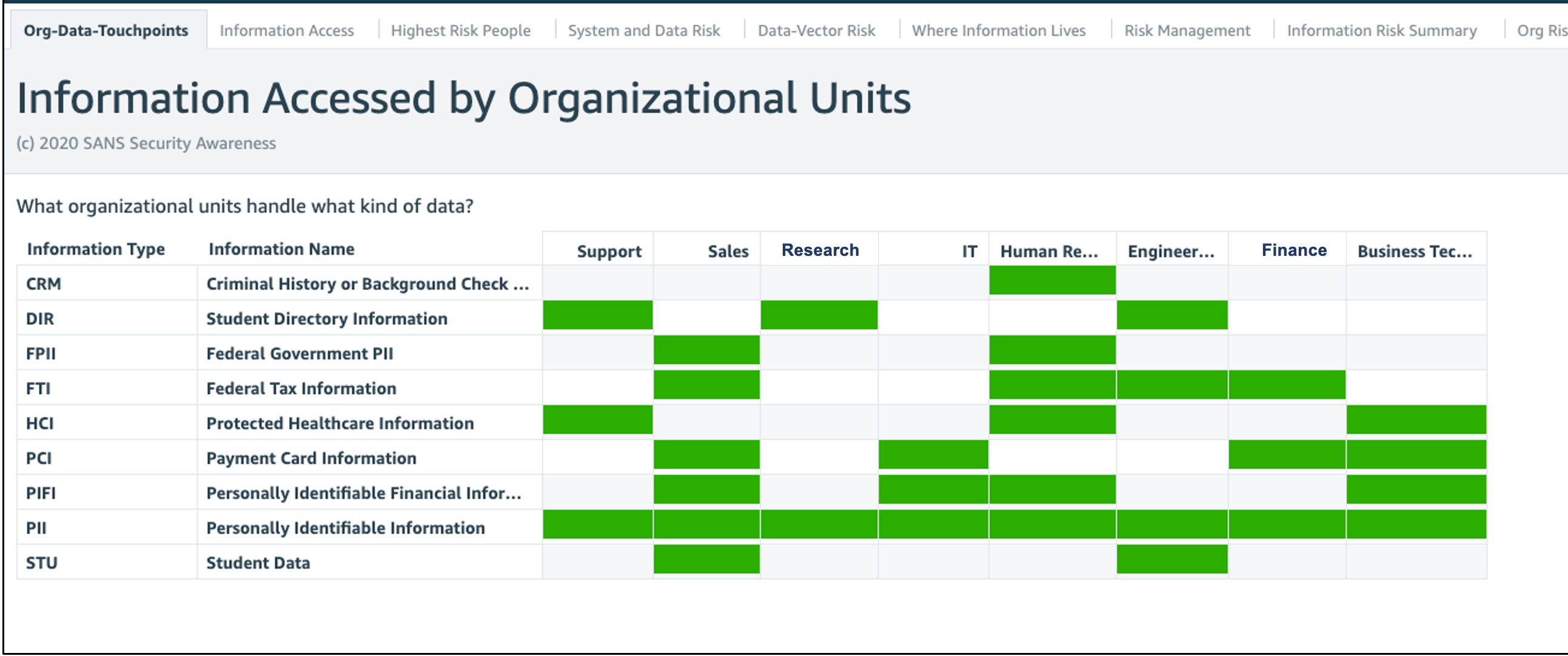
In this example, we show which departments are handling what data types. For example, if you are concerned about mitigating risk around payment card data, you could quickly identify you should focus on Sales, IT, Finance and Business Technology groups.
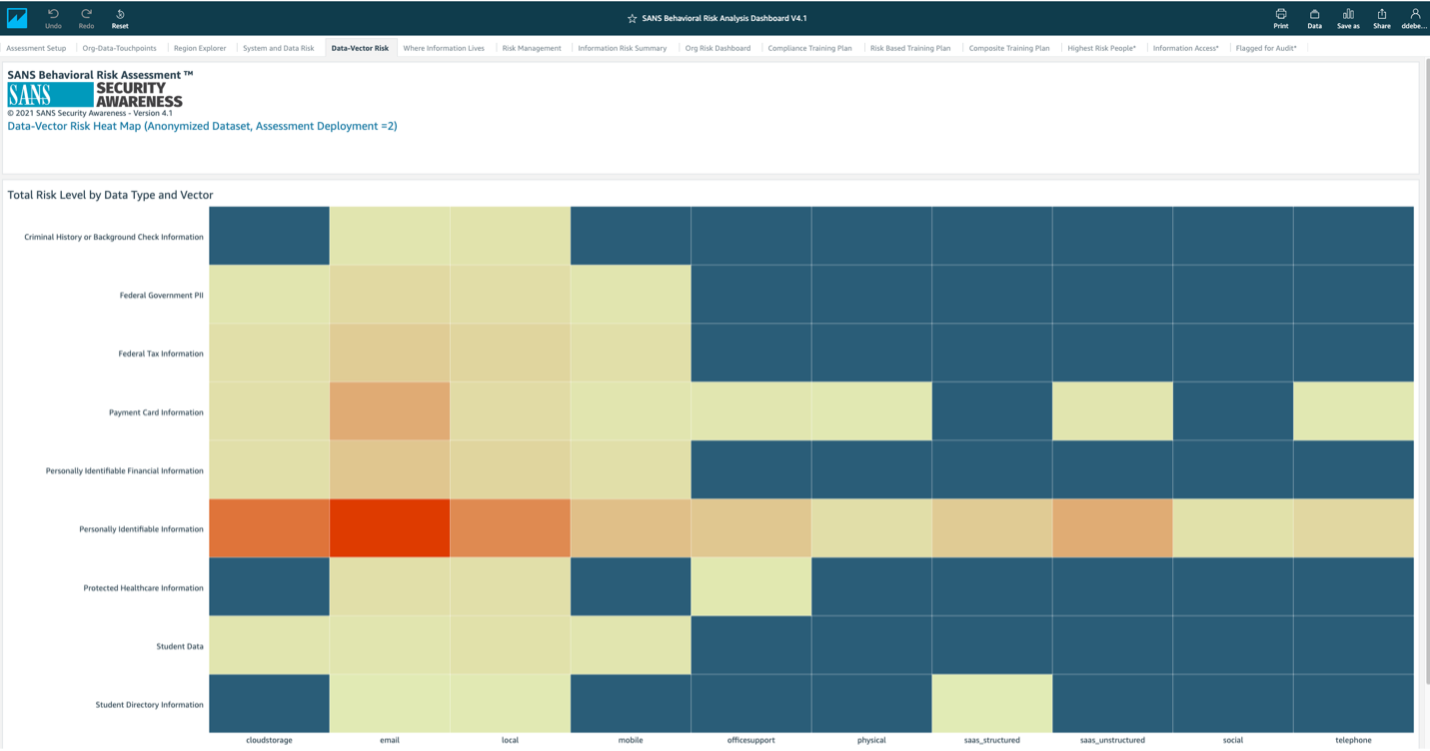
In this heat map, you can quickly identify what are the riskiest methods of how people are handling data. In reference to personally identifiable information (PII), the riskiest handling method would be email, which is red. Is this allowed in your policies? If so, how can we better secure these target groups behaviors?
These types of reports are extremely powerful in helping you identify not only who is handling your most sensitive data but how they are handling it, and which methods may be the riskiest. This ensures you provide the right training to the right people and nothing more, ultimately reducing program costs and unneeded training. The bonus with such an approach is you can also leverage this data for compliance purposes as compliance is often driven by the type of data people handle. If interested, you can learn more about our Cyber Risk Insight Suite™ and the Behavioral Risk Assessment™ here.
To learn more about human risk and security culture, consider the two-day SANS course MGT433: Managing Human Risk or the more advanced five-day SANS course MGT521: Leading a Strong Security Culture.




