Tags:

John Pescatore - SANS Director of Emerging Security Trends
Preventing 999 out of 1,000 phishing attacks today is better than waiting for perfection.
This week’s Drilldown will focus on one item (included below) from NewsBites Issue 90 that reported on a blog posting by Microsoft Director of Identity Security Alex Weinert, which stated:
“Today, I want to do what I can to convince you that it’s time to start your move away from the SMS and voice Multi-Factor Authentication (MFA) mechanisms. These mechanisms are based on publicly switched telephone networks (PSTN), and I believe they’re the least secure of the MFA methods available today. That gap will only widen as MFA adoption increases attackers’ interest in breaking these methods and purpose-built authenticators extend their security and usability advantages. Plan your move to passwordless strong auth now -- the authenticator app provides an immediate and evolving option.
“It bears repeating, however, that MFA is essential -- we are discussing which MFA method to use, not whether to use MFA. Quoting an earlier blog, ‘Multi-factor Authentication (MFA) is the least you can do if you are at all serious about protecting your accounts. Use of anything beyond the password significantly increases the costs for attackers, which is why the rate of compromise of accounts using any type of MFA is less than 0.1% of the general population.’”
The coverage focused on the “move away from SMS and voice MFA,” but the most important part of this is the last sentence: “...the rate of compromise of accounts using any type of MFA is less than 0.1% of the general population.”
A major problem in security is what I call “The Cult of the Impossible Problem”--the tendency to look for the perfect security solution that solves all threats, which, of course, never arrives. This always provides a convenient excuse for inaction: “Well, it won’t solve everything.”
But if the business goal were to add $10 million in revenue and the BU manager presented a strategy that would bring in $9.99 million, do you think the CEO and Board would say, “No, let’s wait to get that last 0.1%”?
So, to repeat, Microsoft’s Director of Identity Security says, “...the rate of compromise of accounts using any type of MFA is less than 0.1% of the general population.”
You should read that as, “Let’s implement any type of MFA wherever possible.”
The starting point should be all sys admin privileged accounts. Not only are those accounts the prime targets of phishing attacks, but also most sys admins work within the IT organization--the perfect place to work out the obstacles to using MFA.
Users are starting to become extremely familiar with MFA. Duo’s 2019 “State of the Auth” report shows that 53% of respondents have used MFA, compared with only 28% in 2017, which is nearly 100% growth. And here’s an interesting graphic:
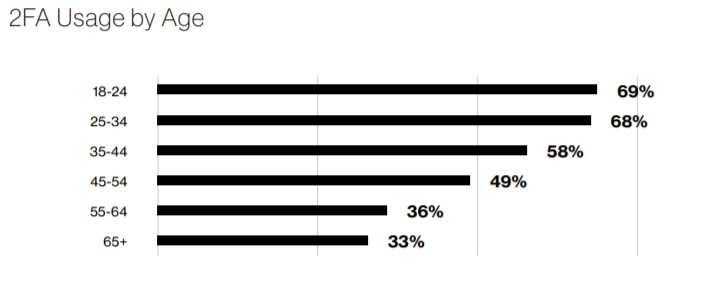
The under 34 crowd is leading the way in already using two-factor authentications (2FA). They are used to SMS message 2FA and biometrics on their phones, yet at work all they see is reusable passwords!
MFA is not penicillin--there are techniques, such as SIM swapping, that enable bypassing it. The authenticator apps have their own issued, both security and single vendor lock-in. But remember the bottom line:
Bottom line: Microsoft’s Director of Identity Security says, “...the rate of compromise of accounts using any type of MFA is less than 0.1% of the general population.”
______________________________________________________________________________
Microsoft: Use MFA That Doesn’t Use Publicly Switched Phone Networks
(November 10, 11 and 12, 2020)
Microsoft is urging organizations to use MFA that does not rely on publicly switched telephone networks. SMS and voice protocols were designed without encryption; one-time passcodes sent via SMS or voice can be intercepted. Encrypted authentication apps, such as Microsoft Authenticator, Google Authenticator and Cisco Duo Mobile, provide better security.
[Editor Comments]
[Pescatore] The most important quote from the Microsoft blog post is that the rate of compromise of accounts using any type of MFA is less than 0.1% of the general population. Using the widely offered SMS-based 2FA options means that a user is 1,000 times less likely to have their credentials compromised. Before we start talking about more secure, but often single vendor-controlled alternatives, let’s get that 1,000 times improvement in protection from phishing. If the apps (which are software written by vendors that are often issuing dozens of, often more than 100, applications patches per month) really do prove to be more secure, then the world can migrate to something more secure. I cannot emphasize this enough: The most important step is getting users away from reusable passwords.
[Neely] Implementing any form of MFA is a major improvement over a reusable password. Because users are able to forward SMS messages to their computer or other devices, using tools like Apple iMessage and Google Messages, interception is possible. Also, in the current environment, PSTN calls are also forwarded or otherwise rerouted, potentially exposing their data as well, because they are not encrypted end to end. Choose stronger authentication options, such as Microsoft Authenticator and Google Authenticator, prior to enabling SMS or voice verification options. Use a risk-based approach when selecting the authenticator strength for enterprise applications, which may lead you to require hard tokens for more sensitive data access, particularly when internet accessible. NIST SP 800-63 provides guidance for selecting authenticator strength.
[Honan] MFA, without doubt, is a key layer of protection against accounts being hijacked. While the use of authentication apps is the preferred method, as recommended by Microsoft, it is important to consider the challenge of rolling out such apps across your user base, in particular for those users who don’t have corporate devices and may be resistant to installing a corporate app onto personal devices. You should look not just at MFA to defend your systems, but also include other elements in a zero-trust model.
[Murray] Courtney’s First Law: "Nothing useful can be said about the security of a mechanism except in the context of a specific application and environment."
Read more in:
ZDNet: Microsoft urges users to stop using phone-based multi-factor authentication
www.zdnet.com/article/microsoft-urges-users-to-stop-using-phone-based-multi-factor-authentication/
The Register: Microsoft warns against SMS, voice calls for multi-factor authentication: Try something that can't be SIM swapped
www.theregister.com/2020/11/11/microsoft_mfa_warning/
Tech Community: It's Time to Hang Up on Phone Transports for Authentication

