On Tuesday, August 11, 2020, SANS disclosed a security breach which was the result of a successful phishing campaign. As described in the disclosure found at https://www.sans.org/dataincident2020, the phishing email enticed a single user to install a malicious Office 365 add-in for their account. The O365 add-in caused a forwarding rule to be configured on the victim’s account, which resulted in 513 emails being forwarded to an unknown external email address. In this article, we are publishing specific details and indicators of compromise associated with this attack in the hope that it will help the community detect and respond to any similar attacks.
WARNING: The following information contains links that can be used as Indicators of Compromise for scanning for similar attacks in your own organizations. Do not copy/paste the link into your browser and remove the brackets as that would enable the link. These links might become active again if the attacker realizes individuals are opening their browsers to these sites.
On July 24, 2020, several employees from various parts of the business received an email with the subject:
File “Copy of sans July Bonus 24JUL2020.xls” has been shared with <recipient>
The sender name appeared to come from an Office 365 asset with the name:
no-reply@sharepointonline.com
Here is a screenshot of the redacted phishing email:
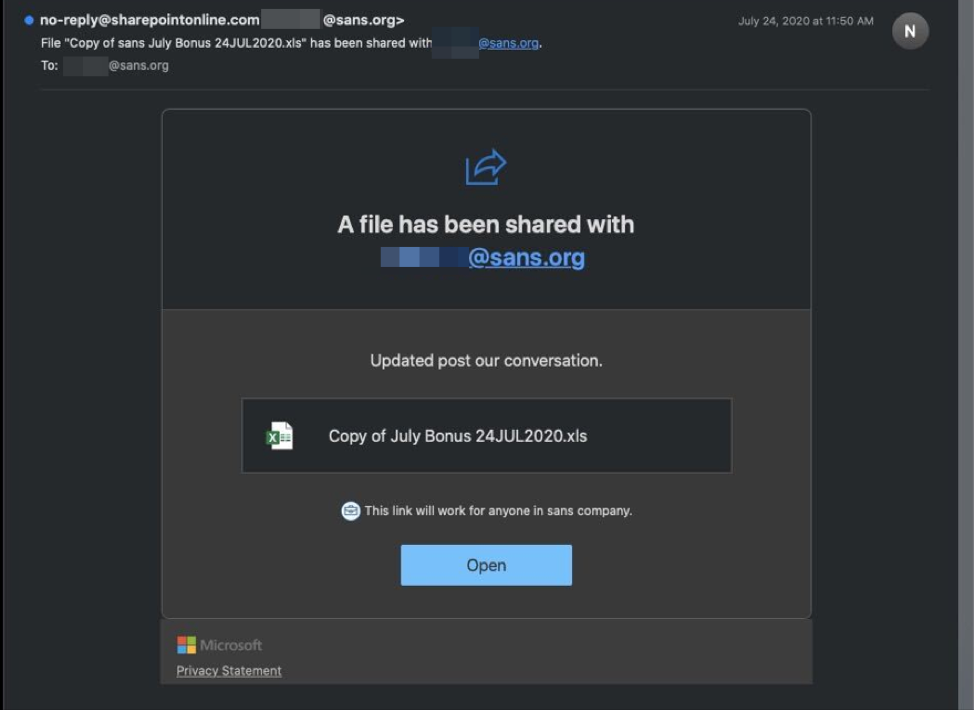
The recipient is enticed to click the “Open” button, which initiates the installation of a malicious Office 365 app. Once installed, the app configures an email forwarding rule with numerous keywords associated with financial data. The following are additional IOCs associated with this compromise:
- Link from phishing email that recipients were enticed to click:
https: // officei6zq49rv2p5a4xbq8ge41f1enjjczo[.]s3[.]us-east-2[.]amazonaws [.]com / index[.]html
- Phishing email header's "Return-Path":
root[@]hwsrv-750360[.]hostwindsdns[.]com
- Name of the malicious O365 add-in:
Enable4Excel
(note that this is very similar to a legitimate Salesforce add-in named Enabler4Excel)
- Link contained in the malicious O365 add-in:
https: // iwljzmwhres67fh[.]com / office
- Keywords to invoke forwarding rule:
agreement
Bank
bic
capital call
cash
Contribution
dividend
fund
iban
Payment
purchase
shares
swift
transfer
Wire
wiring info - External forwarding address:
daemon [@] daemongr5yenh53ci0w6cjbbh1gy1l61fxpd.com
- Forwarding rule name:
Anti Spam Rule




